User interfaces for computers have evolved over the years, from the introduction of the keyboard and mouse on the personal computer, to touchscreens on mobile devices, to natural voice recognition. However, the same cannot be said for robots or drones—until now.

Hey guys, in this tutorial, we are going to learn about the heap segment and how to use it for storing data in our programs. We will also go into the details of its use in conjunction with the char pointer and struct data types.

Welcome back, my hacker novitiates!

Sometimes you need more than just your brain to split the bill at a restaurant or to calculate how much your cable company is ripping you off.

If you have friends or relatives living or traveling in another country, you may need to call them internationally. Check out this tutorial and learn how to dial a far away land just as easily as you would dial one close to home.

If you have just purchased a new Ford Taurus, you may have noticed the new SYNC feature. SYNC is a GPS built right into your dashboard. If this is your first time using a global positioning system, you may need a few pointers. Check out this video and learn how to access step by step directions and get where you need to go.

Choosing which programming language to learn next can seem like a nearly impossible task, regardless of whether you're a novice developer or a seasoned coding pro with years of experience creating apps and websites. But if you haven't already learned Python, look no further.

Kings Dominion, an amusement park located in Doswell, Virginia, just announced a mobile augmented reality game for park visitors. Gameplay in The Battle for Kings Dominion — available on May 19 for iOS and Android devices — follows the playbook designed by Niantic through Ingress and Pokémon GO.

Here on nullbyte we always hear mention of hacking being used to shut down power grids or attacking SCADA and other such cyber warlord activities, but ive never seen a TDos post come up.

In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

Want the best view of Los Santos in Grand Theft Auto 5 without having to purchase a plane or steal a chopper? You can enjoy the sights of the Los Angeles replica by hopping on one of the trains rolling around the city—and forget about riding in one of the cars, we're going straight into the cockpit.

When you're capturing video with a DSLR, not having some type of stabilization system can lead to some pretty awful and shaky scenes. Camera instability is not only painful to watch, but breaks the fourth wall. Once that the invisible barrier between filmmaker and audience is apparent, it may break down that magical relationship between the two.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

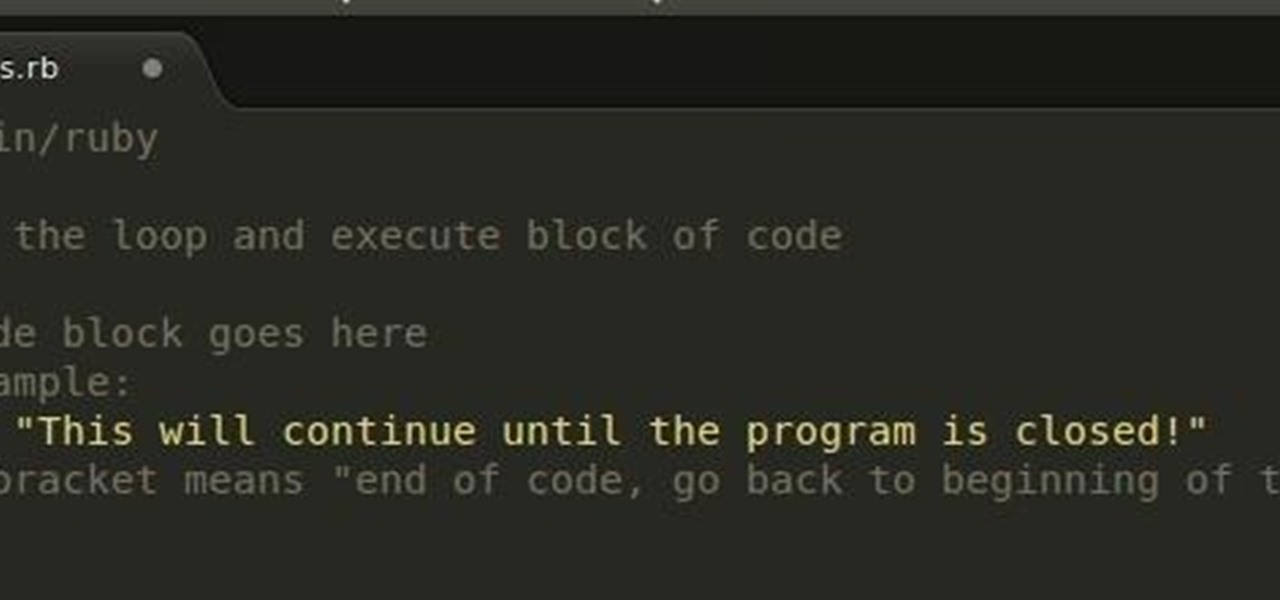
Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

Hello everyone. It's been a while since I've posted anything (with good reason). But, now that the digital dust has settled, it's time to be an adult about this. I will be continuing to post to Null Byte on a smaller scale, and will also fully participate in whatever communities Null Byte members branch into.

Welcome back, my aspiring hackers! One of those areas of Linux that Windows users invariably struggle with is the concept of "mounting" devices and drives. In the Windows world, drives and devices are automatically "mounted" without any user effort or knowledge. Well, maybe a bit of knowledge. Most Windows users know to unmount their flash drive before removing it, but they usually think of it as "ejecting" it.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

The wildfires that spread across Northern California for two weeks in November were among the deadliest and most destructive in the state's history. Ultimately, the incident claimed 85 lives, and hundreds of people are still missing in the wake of the disaster, which impacted over 154,000 acres of land.

Augmented reality and drones already go together like turkey and stuffing, but a new iOS app adds some spice to the combination with a new kind of flight path automation.

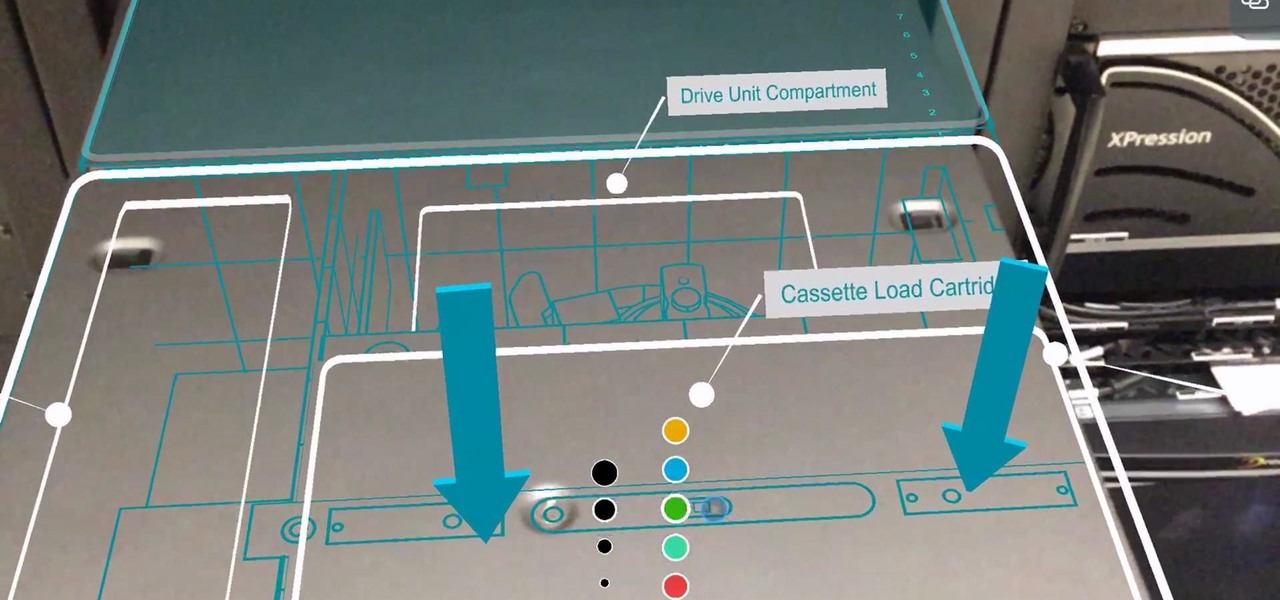
Germany-based Augmented reality software maker Re'flekt has added a new tool to its enterprise app development platform that makes it simpler to link AR content to physical objects.

Enterprise augmented reality software maker Scope AR is bringing the powers of its two productivity apps together like the Wonder Twins into the form of a single app.

Texas has become the 18th state to pass a bill into law regarding autonomous vehicles, the third this month to do so.

Mercedes-Benz's parent company, Daimler, announced their intention today to put self-driving taxis on the road in three years or less in a partnership with Bosch.

Greetings, hackers and friends! I know it has been a while since I posted a tutorial, and hopefully I can make up for that by posting a series.

Rumors have had Google making a foray into the mobile carrier world for quite some time, but today, the Mountain View tech giant finally made things official. The new service, dubbed Project Fi, will be a Mobile Virtual Network Operator, or MVNO, that uses existing Sprint and T-Mobile cell towers.

In college, I enjoyed eating, sleeping and making my roommate's life a living hell. My most satisfying prank involved 500 red cups stapled together, filled with water, and strewn across his bedroom floor. He was not happy. To clean up, he had to unstaple each cup, carry it to the bathroom, and dump the water. He was furious, but I was okay with sacrificing our friendship in exchange for a fantastic story that I'll probably tell my grandkids one day. If you're not as cruel as me, there are oth...

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

So you've been playing Call of Duty Mobile for some time but can't seem to get MVP at the end of the battle. Well, since the game is a competition of players and bots, you're in an uphill battle. But you don't have to languish at the bottom. With the help of these tips, you might just nab your first MVP.

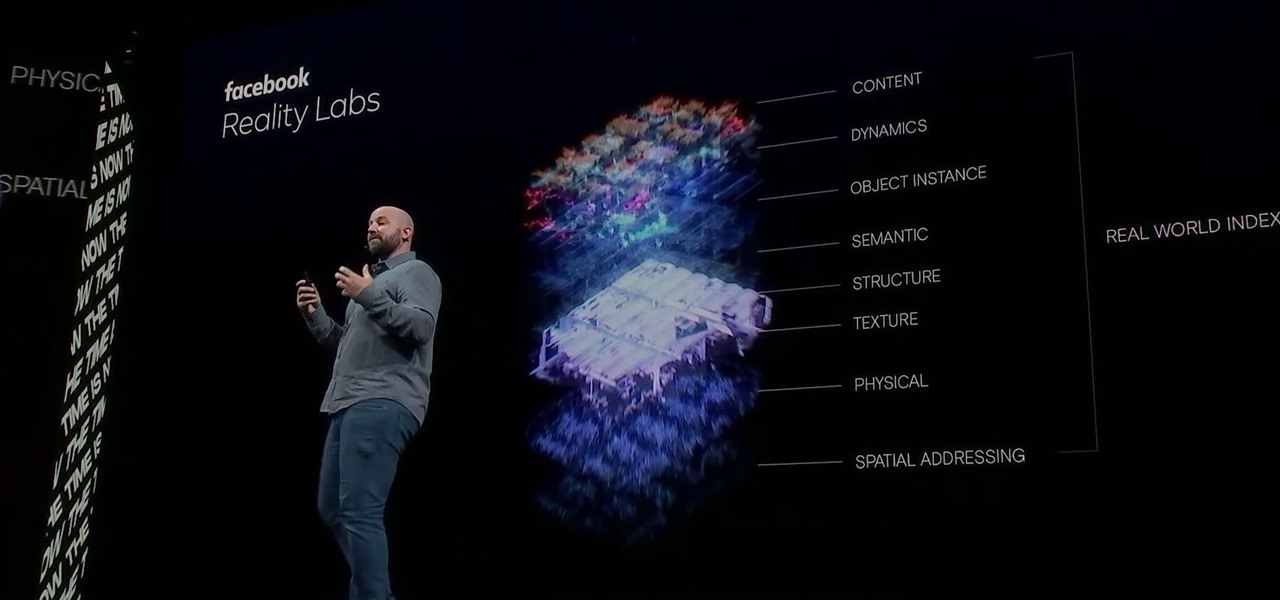
Facebook had a pretty big week in terms of augmented reality, with much of its news coming from the Oculus 6 keynote presentation. But Mark Zuckerberg's social media company found other areas of impact outside of Oculus 6 as well.

Until Star Wars-style 3D hologram projection technology becomes commonplace, the near future of certain kinds of remote work is in robotics. Now, a new dynamic is using augmented reality to give this kind of telepresence a kind of superpower.

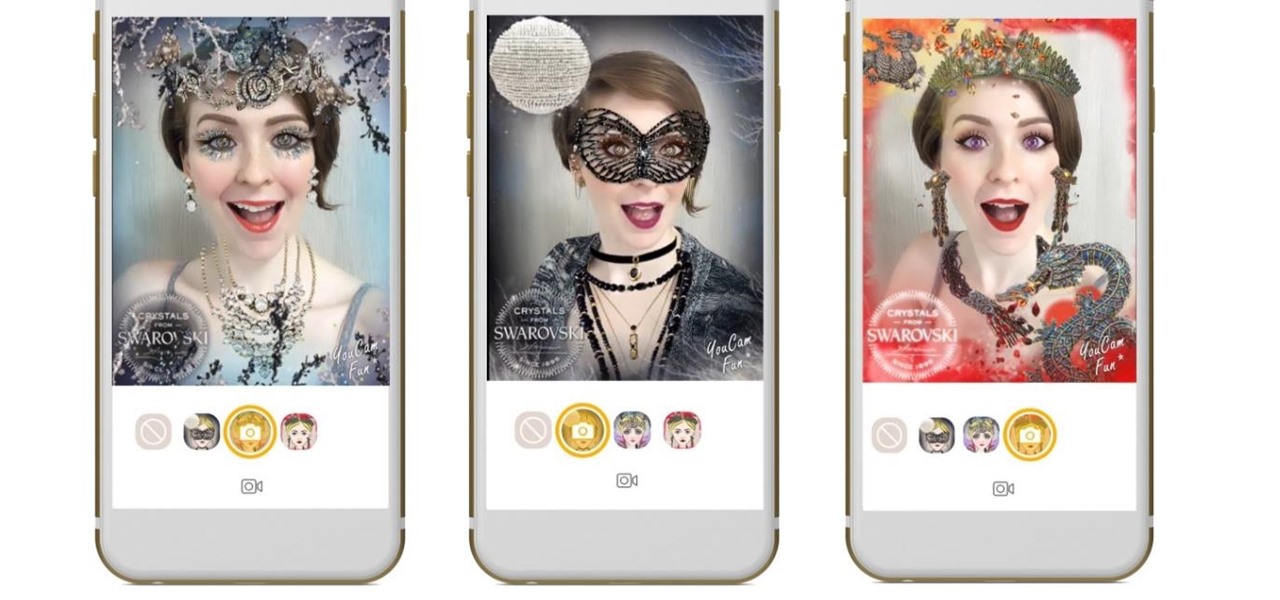
Nowadays, with the convenience of online shopping, brick-and-mortar retailers and malls have to work harder to draw shoppers to stores. This year, many of them are turning to augmented reality for assistance.

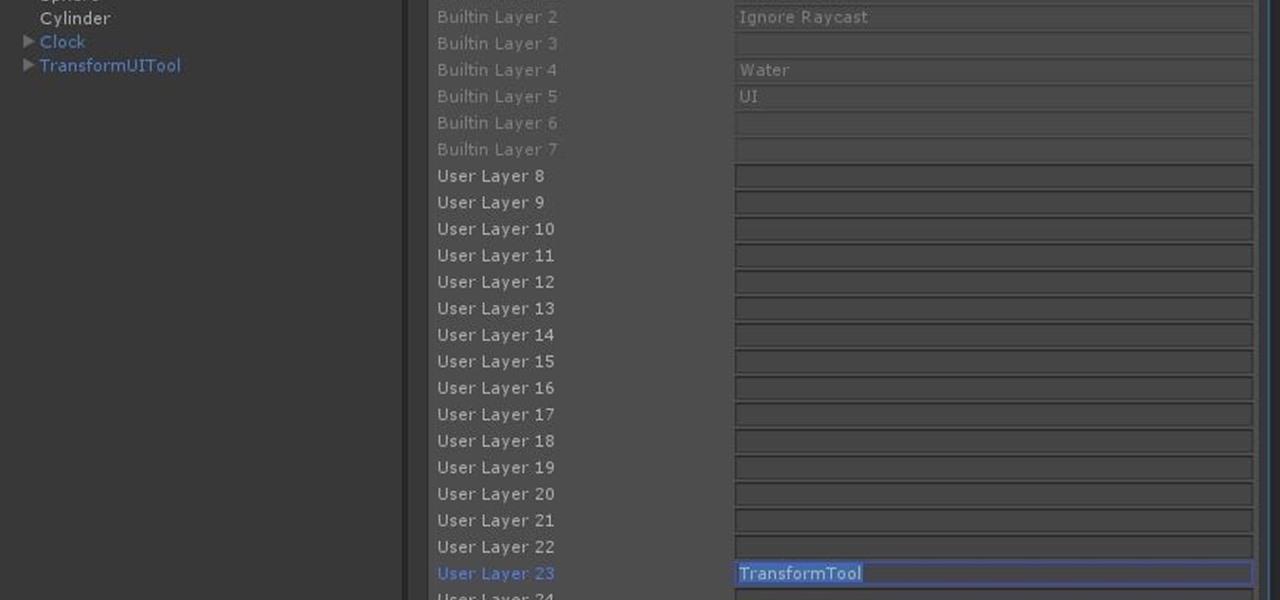
Now that we have unlocked the menu movement — which is working very smoothly — we now have to get to work on the gaze manager, but first, we have to make a course correction.

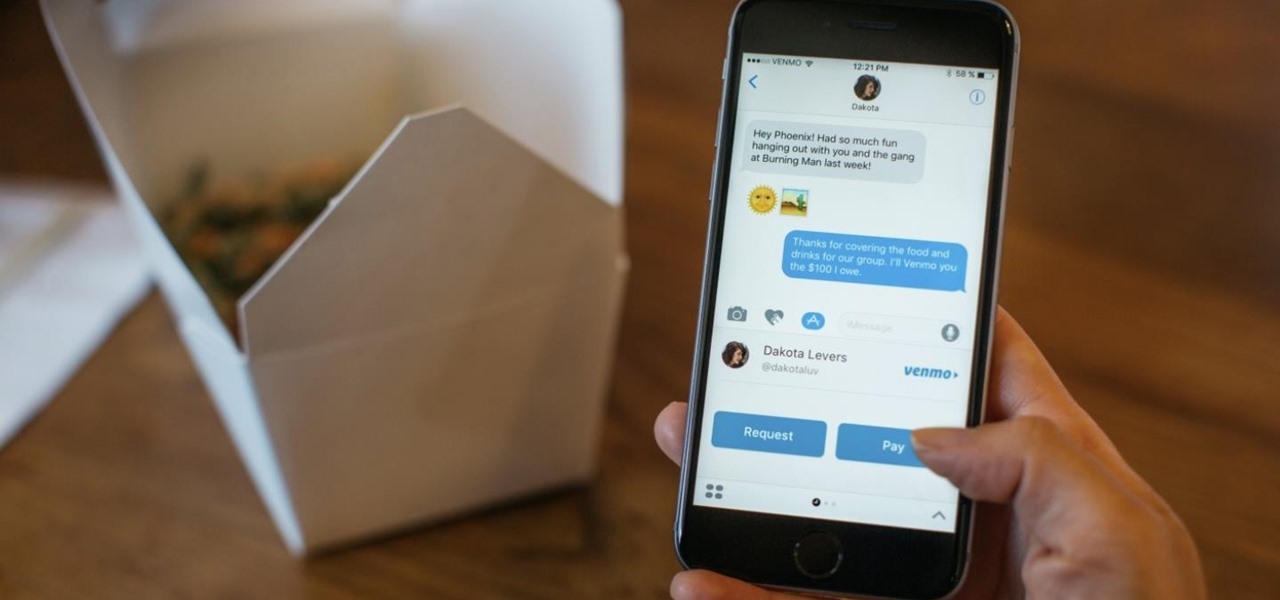
For $0.25 per transaction, PayPal will soon be allowing you to transfer money through their app that will get delivered within seconds rather than days.

A couple weeks ago, GM's Cruise Automation released a remarkable self-driving video from the streets of San Fransisco that Driverless analyzed in detail. And now they've just released a new one giving more insight into their growing mastery of the complex roads in San Francisco, specifically, the Potrero Hill and Mission Dolores neighborhoods.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

As a commercial and potentially consumer product, one might assume it very unlikely to see the Microsoft HoloLens in the military marketplace. And that assumption would be completely wrong. One company from the Ukraine is currently working on using the mixed reality head-mounted computer for 360-degree vision inside armored tanks. If a tank crew could see the entire battlefield there are in, they would likely have a better chance of accomplishing their mission and avoiding damage. Tanks are l...

Making international calls have always been tricky and confusing. There's access codes, different digit formats, and unsupportive telephone operators. But in all actuality, making an worldwide phone call is relatively simple, but there are some numbers that you need to know. The access code, country code, city codes, and the telephone number. Once you have this down, you'll have more successful connections abroad.

In this emergency preparedness video series, learn what to do when you need to call 911, or even if you call by accident. Our expert, an experienced 911 dispatch operator, Jill Maglione, will tell you what the most important information you need to give is, why you need to give your address, why you may be asked to stay on the line, how to get to the point about what type of emergency you have, how to teach kids to use 911, how to report a car accident, and more tips you need for emergency pr...