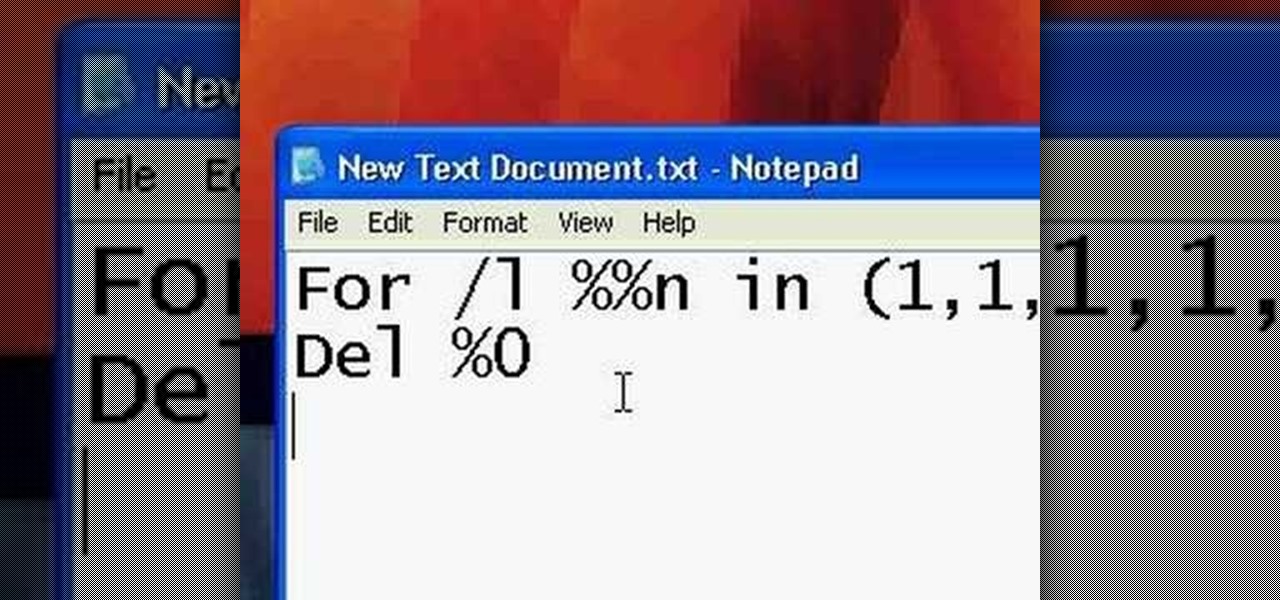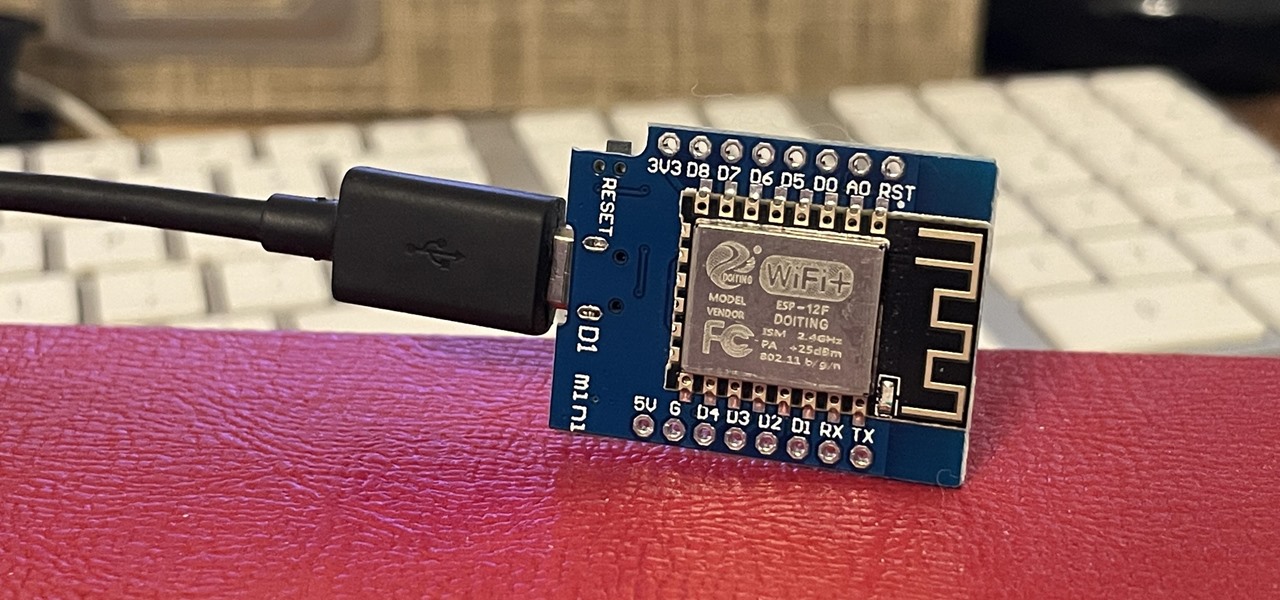
If you've wanted to get into Wi-Fi hacking, you might have noticed that it can be pretty challenging to find a safe and legal target to hack. But you can easily create your own test network using a single ESP8266-based microcontroller like the D1 Mini.
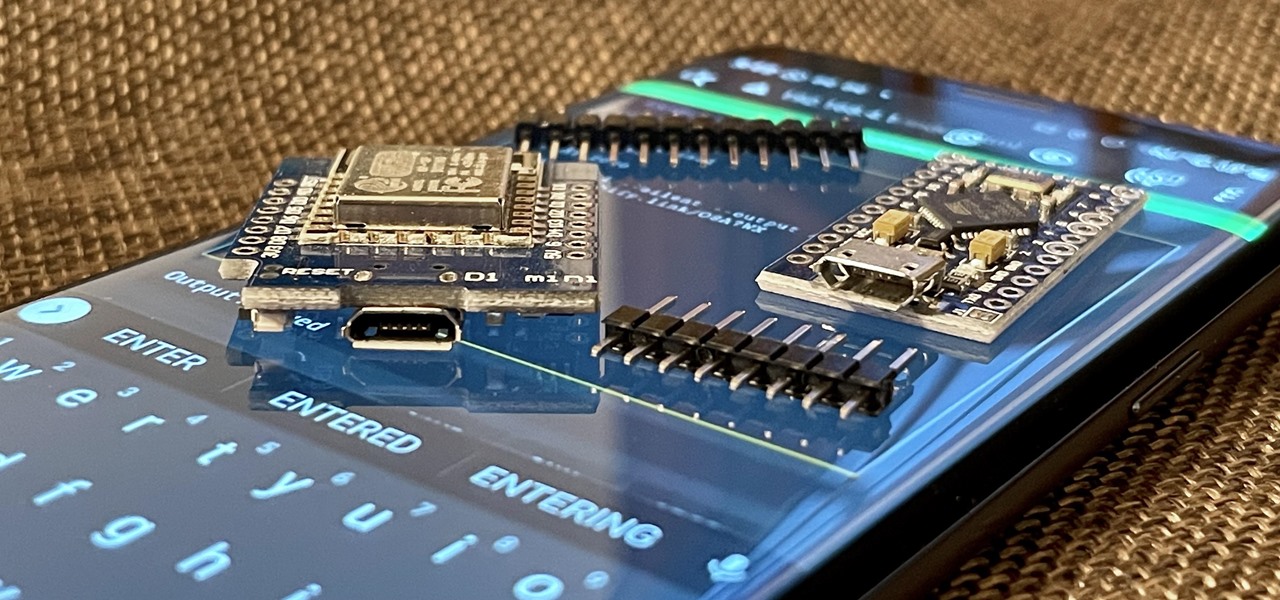
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.
Your iPhone and Mac can speak to each other in many ways, allowing you to start work on one device and seamlessly switch to the other, share clipboards between the two, and pick up phone calls and answer text messages on both. The compatibility is incredible, but there's even more you can do by incorporating third-party software into the mix.

If you've spotted an unintended Ethernet connection and wondered what you could do with all of the information coursing through those wires, there's an easy way to hack into it and find out.

Everybody knows not to store sensitive information in unencrypted files, right? PDFs and ZIP files can often contain a treasure trove of information, such as network diagrams, IP addresses, and login credentials. Sometimes, even certain files that are encrypted aren't safe from attackers. That's where Zydra comes in — a tool for cracking RAR files, ZIP files, PDF files, and Linux shadow files.

In a time where we're more connected than ever, privacy and security have never been more important. Maybe you're not concerned, but I'm sure there's someone in your life who is, and shopping for them can be daunting. However, with these gifts, you can provide them the tools they need to enhance their protection.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Besside-ng is the hidden gem of the Aircrack-ng suite of Wi-Fi hacking tools. When run with a wireless network adapter capable of packet injection, Besside-ng can harvest WPA handshakes from any network with an active user — and crack WEP passwords outright. Unlike many tools, it requires no special dependencies and can be run via SSH, making it easy to deploy remotely.

Apple has revolutionized how we write with the introduction of its new Writing Tools, powered by Apple Intelligence. In beta on iPhone, iPad, and Mac, these tools allow you to select text and use intelligent features to summarize, proofread, or rewrite it until the tone and wording are just right. In a future beta, Writing Tools can even write original content for you.

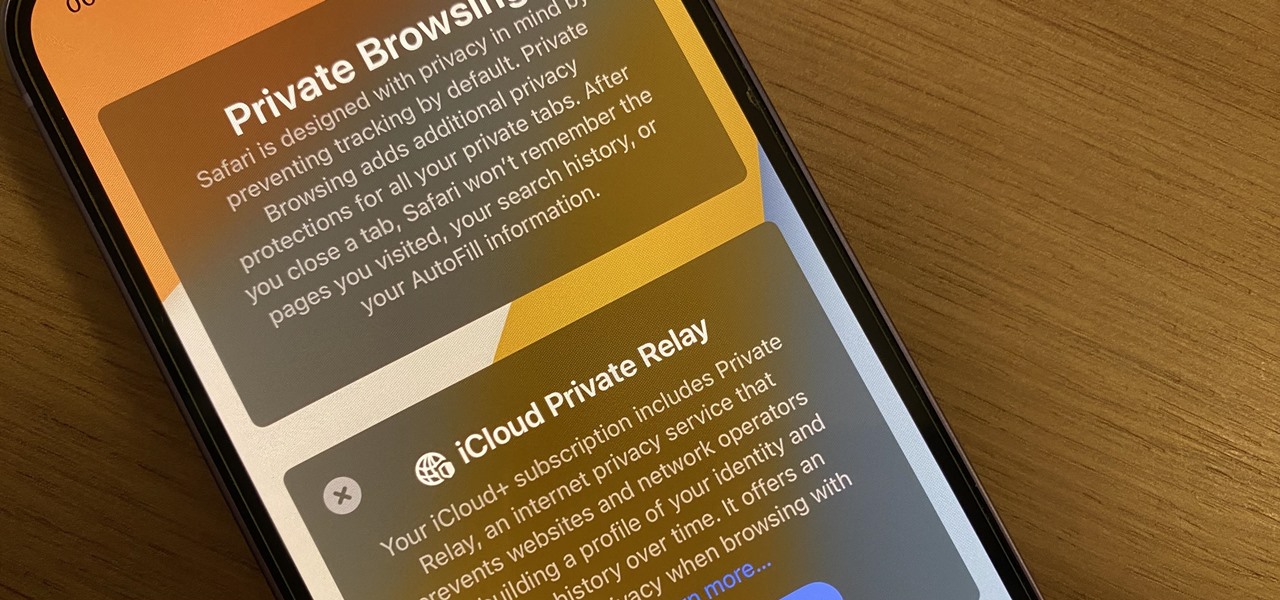
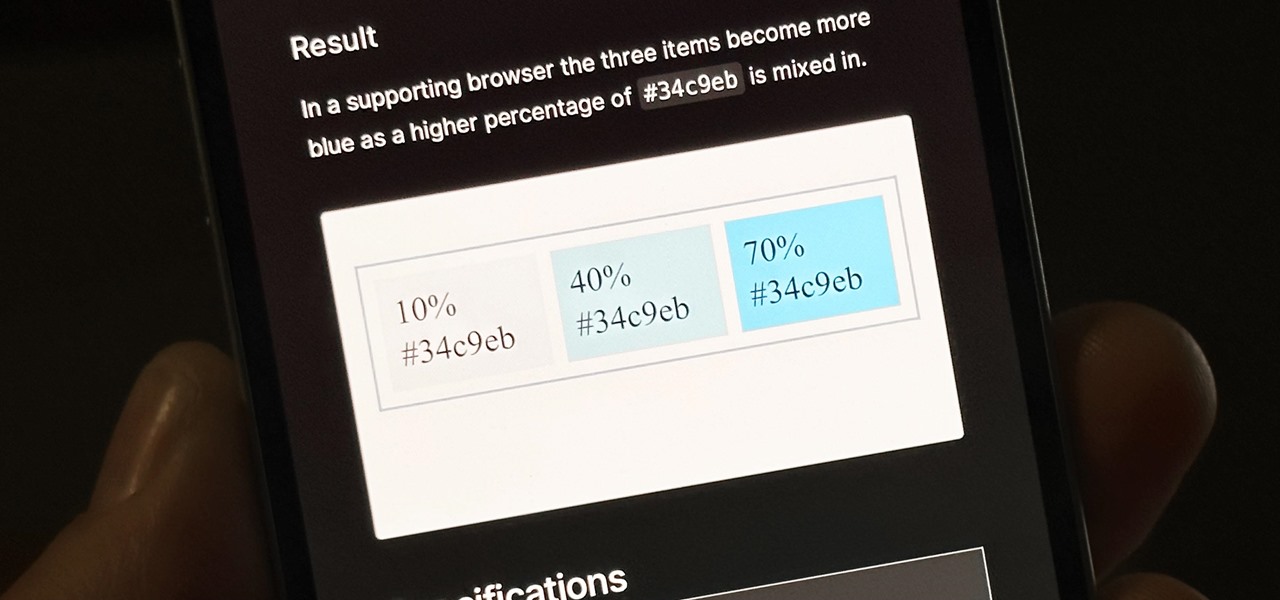
Safari's massive upgrade in Apple's latest iPhone software update includes new features you won't find in any other web browsers on iOS, from better ways to stay organized to enhanced security and further privacy protections.

Apple's latest big software update includes an entirely new Apple app, a controversial change in the TV app, better Siri control, an improved Shortcuts app, interesting Safari upgrades, Apple Music Sing, and more. Keep reading to see what iOS 16.2 has to offer your iPhone.

It hasn't been long since Apple released iOS 16.0 with over 350 new features, but iOS 16.1 just came out with even more cool updates for your iPhone. While some of the recent upgrades were expected, others are somewhat surprising — and there's even one that you may not even think was possible.

Apple officially announced iOS 15 at WWDC Monday, June 7. With that announcement, we got our first look at brand new features like redesigned notifications, FaceTime screen and music sharing, and Focus modes in Do Not Disturb. All of these new iPhone features are available to test out today, thanks to the iOS 15 beta.

Android comprises an entire ecosystem of apps, games, functions, and features, so it would only make sense that it has its own lexicon. Words, phrases, and acronyms that didn't exist ten years ago are now used in an off-the-cuff style by developers and support technicians across the web.

What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to access a blocked website... it's possible! As a matter of fact, it's quite easy.

In this article I'll show you how to make a simple IP address notifier. The program will text you your new IP address, in the event that it changes. For those of you with dynamic IPs, this is very useful. I'm constantly frustrated when my IP changes, and it's handy to be notified via text when it happens. To use the program, you'll need Python 2.7 or later, urllib2, and a program called "text" (see this article here to get it).

The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel today's lesson.

In this tutorial, we learn how to find an external IP address on your PC using different websites. First, find a website that will let you find your IP address for free. Once you find this site, it will not only give you your IP address, it will show you where you are in the world. Not only will it tell you where you are in the United States, it will tell you your exact coordinates and pin point your location on a map. There are many sites available online that will do this, a great site is I...

Tutorial showing how to trace and locate any IP using tracert. Trace any IP address with tracert.

Ever wondered where someone was located? Check this out to find out where in the world someone is located by using their IP address. Trace any IP address in the world and see location.

IP Hider masks the real IP of a user, allowing him to browse all kind of pages without ever worrying that the ISPs or any other marketing tool is monitoring your surfing habits or spammers are attacking your computer. The simplest way to do this is to have traffic redirected through anonymous proxies.

In this tutorial, we learn how to find an IP address in Hotmail. First, open up your Hotmail in box and right click on the email you want the IP address of. Now, select "view source" and find where it says "received: from" or "X-Originating IP". This will give you the exact IP of where this email was sent from. You can use this for any email you receive and the best part is that it only takes a few simple clicks of the mouse and a few seconds out of your day! This can help you bump up securit...

In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP addresses should be returned. Then in the command prompt type "shutdown-i" and hit enter, this opens the remote shutdown dialogue. In this dialogue you can add the IP addresses and adjust the various other options then c...
On 2 October 2010 Univision held the first Spanish-English debate in the state, which was hosted by CSU Fresno.

In this Computers & Programming video tutorial you will learn how to establish a Remote Desktop connection in Windows XP. 1st you got to enable remote desktop. To do this go to start, right click on My Computer and click on properties. Then click on the remote tab and click on ‘allow users to remotely etc’ and click on ‘select remote users’. Click add and add your account. Click OK, apply and again OK. Now get your IP. Click start > run and type cmd. In the cmd prompt type ‘ip config’ and not...

Paparazzi are very annoying for the stars but with these sunglasses, paparazzi can't take you in picture .Why ? Because with this sunglasses your face will be invisible to the camera . Disclaimer: CAUTION! . Never use them for illegal act. Make anti paparazzi infrared invisibility sunglasses.

This article will be about setting up a static IP (Internet Protocol) address in Windows Seven. To see whether you should set one up, ask yourself the following: Do I have many computers in the house hold? Do I get connection issues often? Did you answer yes to both? Then you should set one up.

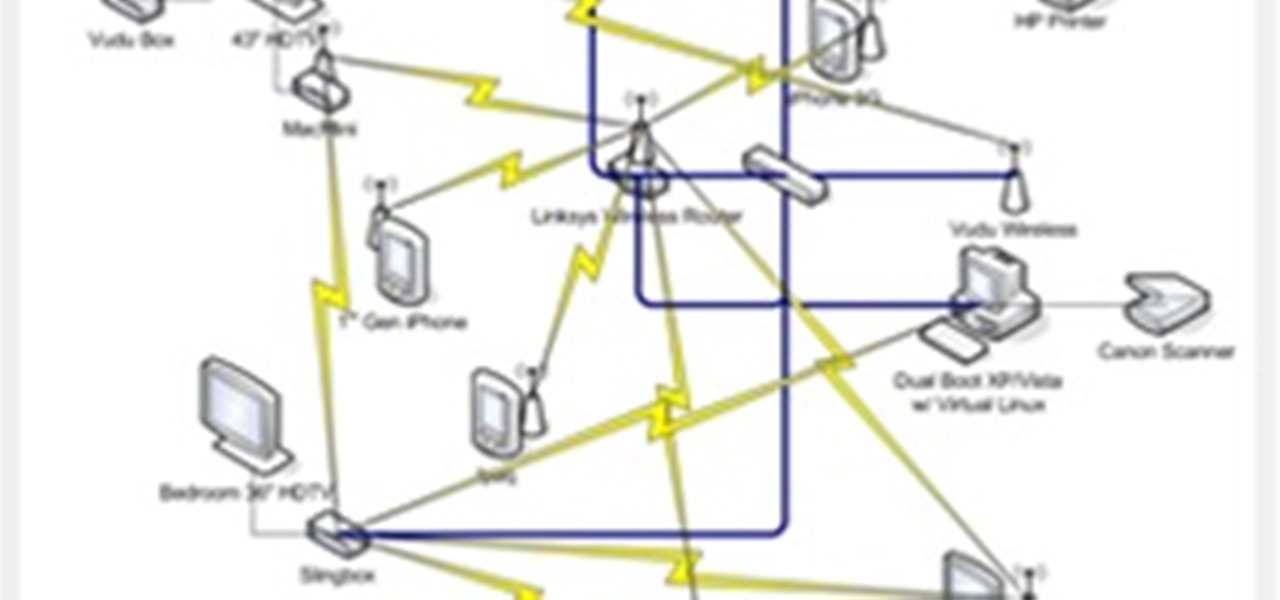
Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.

A proxy is a server that lets a client to connect to it and forward its traffic. This enables a certain "layer" of protection by masking your IP. An IP address can be used to learn your location and track you on the Internet, thus eliminating any form of anonymity that you may have.

Immigration is a serious political issue in the United States, and those who oppose or support stricter immigration laws are often outspoken and candid about their beliefs, imposing their will on future legislation to not only politicians, but the general public—the voters. And what's the best way to reach the public? Entertainment.

.bat files can be quite dangerous to any machine. Creating and opening these files should be done at your own risk. Sending malicious .bat files over the internet is illegal. This video will show you how to make and use a .bat file to prank your friends. Create an annoying batch file to fool your friends.

Imagine you're in Paris and you need to get to Versailles. Looking around for directions, you come to a cold realization—you do not speak a lick of French! How are you going to get to Versailles and what happens if there is a detour? It will be a difficult struggle, and you'd probably get lost and eventually fail. This is why it's important to know some of the country's language before taking that trip in the first place.

Here is the movie trailer for the feature film IP MAN 2 coming out in January 2011.

It works. Very cool. Thanks, Kip. You will get to the nearest subnet of the ISP. You will not get to the actual street address.

Welcome everyone Today i will show you a simple but very useful way to stop your ip leaks . In order to stay anonymous on the web you HAVE to do this.

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!