Many times throughout history companies have been hacked by so-called "grey-hatters": hackers who do ambiguously ethical things with their computer skills. Often enough, after being hacked the companies actually offer to hire the hacker, but not always (as you see in this case). Just a reminder that you need to watch what you are doing. Never do anything illegal unless you don't mind facing the consequences!

This shows how to collect rain water for future use from the roof of your house. Very cool setup, but be careful not to break the law while you're doing it. I know that here in Colorado, it is actually illegal to collect rain water without a permit. Scary, huh?

Do you think that this controversy surrounding GOP nominie Meg Whitman's illegal immigrant housekeeper goingo to affect her votes in her political campaign?

Here is the trailer for the movie "Import Export" If you want to see a really disturbing twisted movie about illegal workers and deviant behavior, check this film out, it will not disappoint.

Acclaimed Cinematographer Adam Kimmel Arrested:
In this video, Sky Van Iderstine will tell you how to get your IP address e-mailed to you every time it changes by using a freeware program, Wimp. With this information, you can then track your stolen Mac laptop or even desktop's location using www.ip-adress.com (the "adress" is not a typo.) Imagine the look of the police officers when you show them the satellite picture of your suspects location! Locate your stolen Mac laptop using Wimp.

She is kind of cute, in that fetching, illegal is-she-under-18 kind of way. A model from Paraguay. There is a 'green' undercurrent to the headline, in addition to an accomplished arts and crafts sensibility. It is a sweet domesticated how-to.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

Hello people. We just wanted to let you know that the server is live now and you can come and play with us!

.bat files can be quite dangerous to any machine. Creating and opening these files should be done at your own risk. Sending malicious .bat files over the internet is illegal. This video will show you how to make a virus that crashes your computer.

Only so much data can be passed through the network and to your computer's networking interfaces. This is limited by the amount of bandwidth you have. The more bandwidth you have, the faster your network connections will be. Not only this, but your transfers will be more parallel and distributed so that all of your speed isn't taken up by one transfer. When all of your bandwidth is sapped and unable to be used, this is called a denial of service, or a DOS.

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

For more than a decade, Interplay was arguably the best video game publisher in America. Their list of games is a who's-who of the most creative and forward thinking games of the '90s, including everything fromOut of This World to Alone in the Dark to Earthworm Jim to Descent. They've been around since 1983, but have fallen on hard times since 1997, when they became a public company. They were acquired by a French publisher who then went bankrupt. They were forced to close their internal deve...

Have you been sharing your Netflix password with your friends? How about Rhapsody or Hulu Plus? If you get caught sharing your online subscription accounts, you could be slapped with a fine and even imprisoned.

From Boing Boing, a highly amusing photo gallery of illegal goods seized by airport customs officials in Australia. Some are fairly typical, but others really make you wonder... Yes, I'm most definitely talking about the tropical fish skirt lady.
Born in Sacramento, CA on January 1, 1958 and raised by two Mexican immigrant parents, Xavier Becerra was the only Hispanic on the House Ways and Means Committee. He was elected vice chair of the Democratic Caucus for 111th Congress and was a reprensentative from California's 31st district. From 1987-90, he was the California Deputy Attorney General. Xavier Becerra was part of the California State Assembly (1990-92) and has been a member of the U.S. State House since 1993.Xavier Becerra is a ...

Sharing a laptop's wireless Internet connection with other computers connected to its Ethernet port is a great skill to know. It can be good for a number of reasons; Your computer may not have proper hardware to have a standard setup, or you may have an awkward network topology where sharing your wireless Internet via Ethernet would just be a better option.

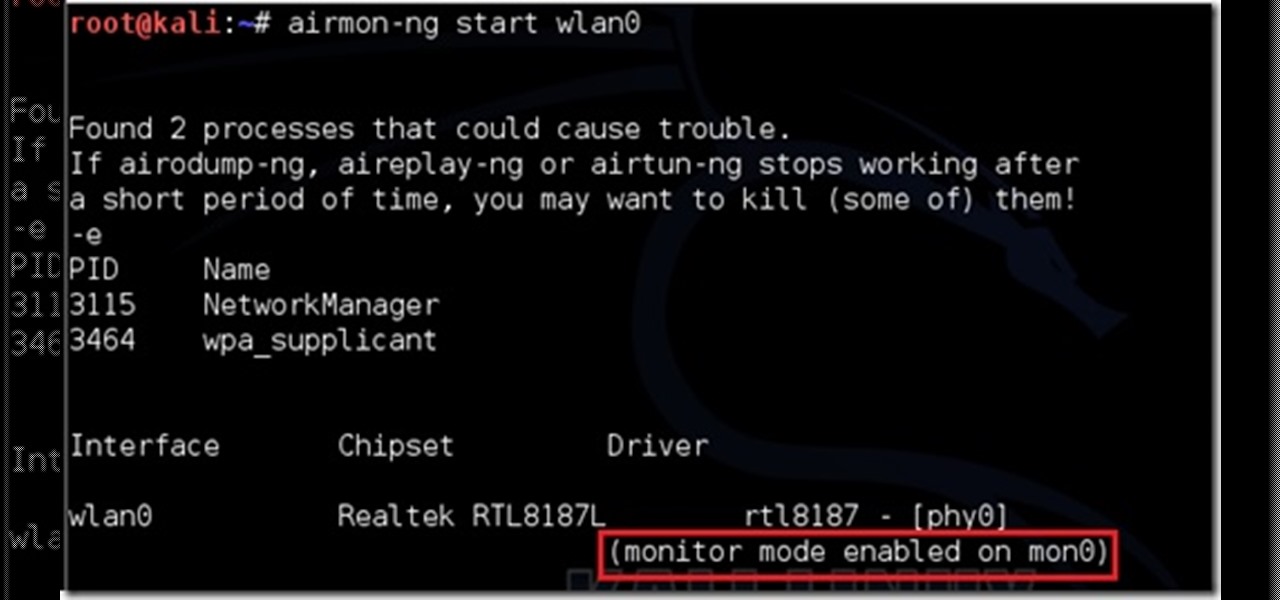
This is my first post please tell me what I can improve. (I don't claim any of the images. I tried taking screen shots but it froze my computer. ) I will be using wlan0 because thats my wireless but use yours.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

When you're out and about in the dangerous world of Wi-Fi, it's hard for the average computer user to stay protected, or even know what being protected entails. Little do most people know, Windows 7 has a built-in security that few people take advantage of: a VPN (Virtual Private Network) server and client.

Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject.

These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brother or otherwise.

Fist full of pennies weighing you down? This will certainly make your pockets lighter.

Learn how to use a proxy when surfing the Internet to hide your IP address. Use a proxy server.

Have you ever wanted to make your own Minecraft server on Windows? This tutorial will teach you how, without having to download Hamachi.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.

Reverse shells are useful for issuing commands to a remote client when the client is behind something such as a NAT. You might say, "But can't a normal shell or simple SSH tunnel do the same thing?". No, it can't. All over the internet I see a lot of confusion regarding the difference between a normal shell and a reverse shell. Let's clear this up before we get started.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

A network Tarpit, sometimes know by the German word Teergrube, is a service or set of hosts that deliberately try to slow malicious network connections down to a crawl. The idea is to put up unused hosts or services on the network that respond to an attacker, but do things to waste their time and greatly slow their scanning (or spreading in the case of Worms). To follow along with this video tutorial, you'll need a package called LaBrea by Tom Liston and an unused IP address to tarpit. Set up...

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.

Haven't you ever wanted to live in a futuristic home? I think that homes are headed towards an era where they will be controlled by our computers and smartphones. No longer will you have to find your keys to unlock your door, or wait until you get home to monitor your security, because X10 is here.

Encryped traffic and tunneling is a must when away from home to keep you and your information safe. SSH tunnels can be slow, and are heavily encrypted. VPNs are an all port solution, and proxies are just not what we need in most cases. Then, there is Tor.

OpenVPN is the open-source VPN (Virtual Private Network) client, used over the PPTP (Point to Point Tunneling Protocol). It allows you to connect to a remote network over a secure, encrypted connection and mask your IP addresses over all ports. Since there is only one "hop," the network speeds are barely effected and are far more secure.

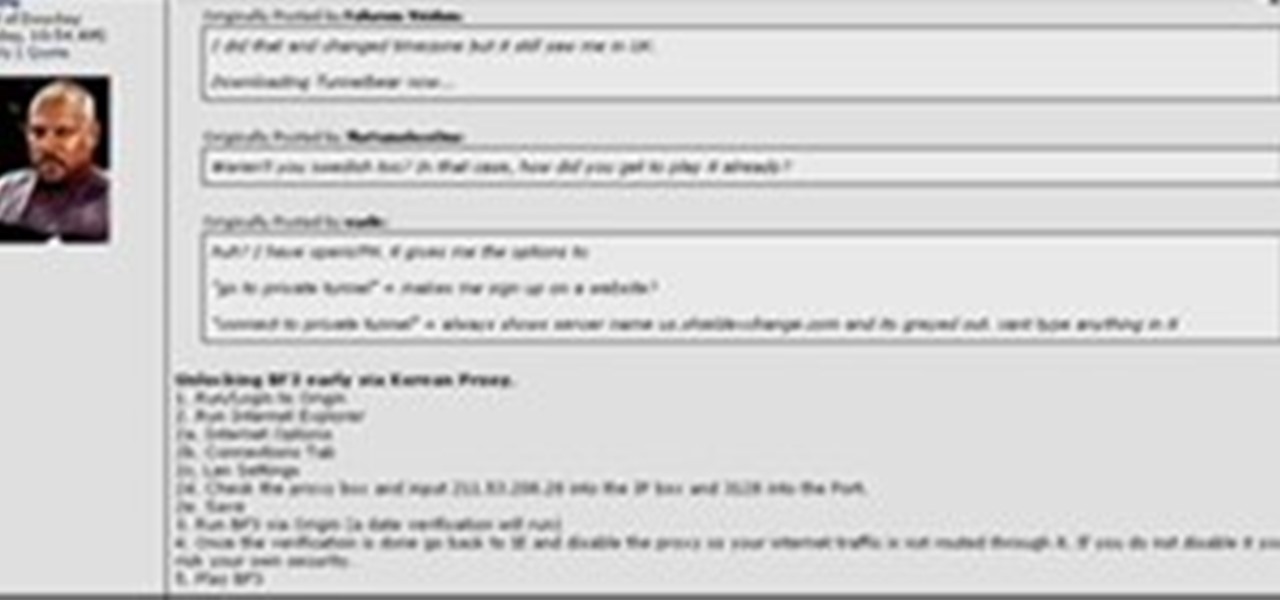
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

People have asked: "Here is an IP address. Can you hack this? Can you hack me right now?" Hacking takes time and skill. You can't just get an IP or an email and hack it in ten minutes unless the password is 1234.

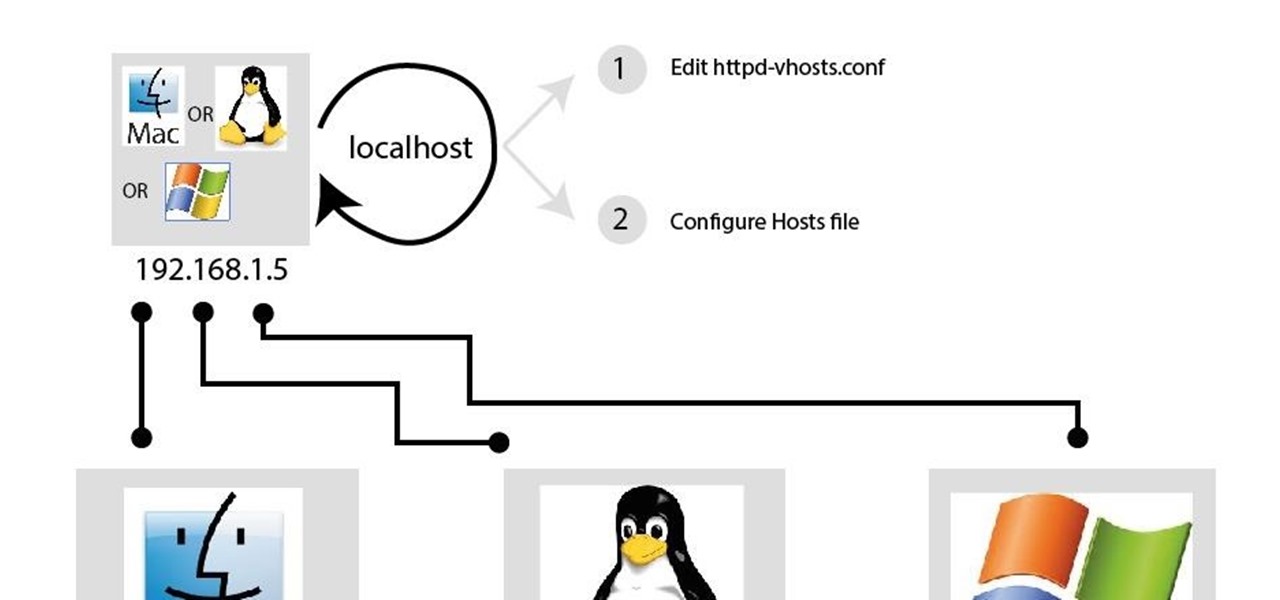
In my last article, I discussed: How to install xampp