How To: Perl for the Aspiring Hacker (Control Statements)
In this tutorial we will be go over how we can make use of conditionals. In Perl the main conditional is the if statement. The if statement in

In this tutorial we will be go over how we can make use of conditionals. In Perl the main conditional is the if statement. The if statement in
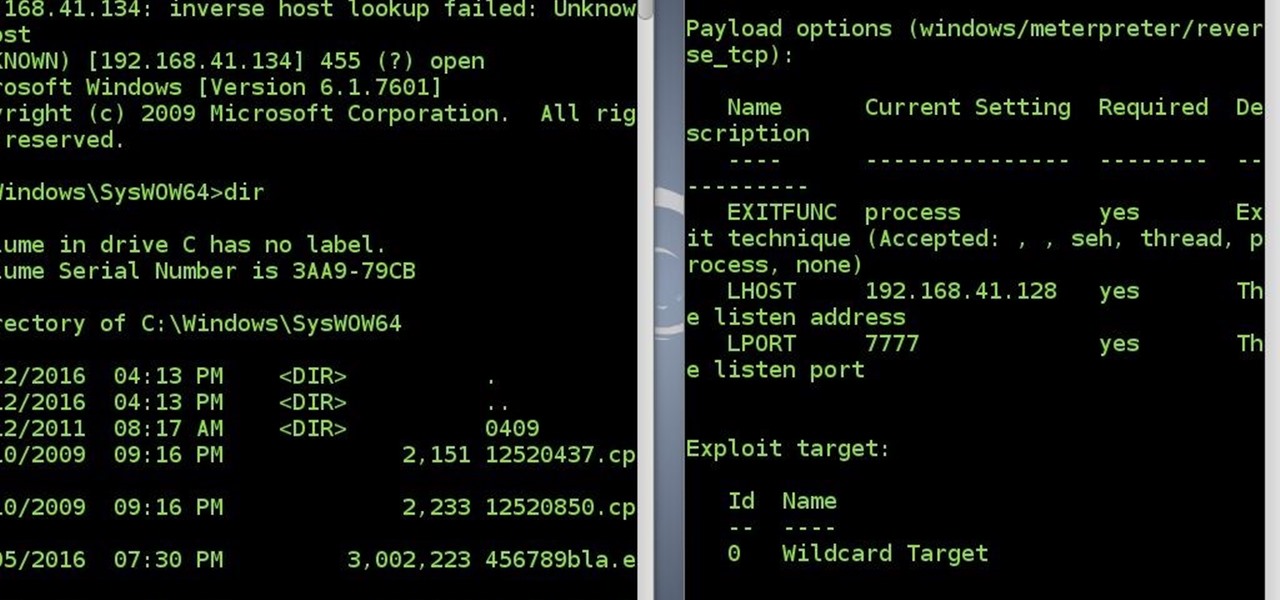
After a long time I succeed to reconnect to victim's system without a touch(the victim did not click the app again)
So, at first, I miss everyone :( and i missed playing minecraft a bit... sooo i found inspiration and i went on for the search for a server as amazing as wonderhowto... OFCOURSE i did not found one wich was better, or wich could even get close to what he had... But i found one, wich allows you to build, rank and have fun... You get a world ( well, 320x320) and how much you rank, how bigger your "world" gets.. you get 100.000 blocks of WE from the very start and you get voxelsniper... wich is ...

First you need to sign in or make a account with facebook or with your mail. The comment on the post. Write like this:

Your IP address or Internet Protocol address is your computer's unique identifier. Here is our quick guide on how to change your IP address when using Windows. Change your IP address when using Windows.

Someone got a hold of your IP address and you need to change it? Find out how to use Windows command prompt to change your IP address. Change your IP address.

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.

Surveillance expert Julia Adams offers the different ways to secretly record a conversation in this how-to video.

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

In this article, I'll show you how to prank your friends on April Fool's Day with the very popular Google Voice, a computer to land/mobile calling feature. Basically, Google allows you to play whatever you like through the microphone port on your computer, and play it right through to your victim's phone. Whether it's Rick Astley ("Never Gonna Give You Up") or a text-to-speech application, general hilarity always follows.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

The Armadillo For Robert Lowell

This weekend in a jungle estuary, the DEA and local Ecuadorian police seized a prototype narco sub that may be the most sophisticated one yet. Complete with air conditioning and periscope, this 100 foot creation would have carried a more cocaine tonnage than any previously captured narco sub. To give you a perspective on the resourcefulness of these outlaws, consider this. A U.S. Navy Virginia Class attack submarine will run around $2.8 billion. But a drug lord in Cartagena would make you one...

If you happened to be watching Brazil vs. Portugal, you might have noticed something weird in keeper Julio Cesar's back after he and Meirelles collided. It was some kind of steel rod support for his injured back. According to FIFA article 4, it's illegal for players to wear any kind of equipment that can be dangerous to the player wearing it or to others. This is the reason players can't wear chains around their necks, or rings in their fingers, since these things can get caught with other pl...

Do you have AMNESIA? How about SYPHILIS? Or have you gotten SODOMIZED? Well, the people pictured below do, and I don't feel sorry for them, not at all——those words would kill on the SCRABBLE board!

3D Dot Heroes Preview Release Date: May 11th, 2010 for the PS3

Do you know your constitutional rights if stopped by the police? Washington Post recently ran an interesting article on "10 Rules", a docudrama produced by the D.C. nonprofit Flex Your Rights.

In a move that seemingly surprised everyone—including Samsung—Korean carriers have released the Galaxy S5 a full two weeks early to avoid being caught up in an about-to-be-imposed ban.

Have you ever fallen asleep watching television only to be rudely awoken by one of those obnoxious commercials that randomly play three times as loud as everything else? While the FCC actually made excessively loud commercials illegal as of last December, it's up to providers to comply, so the problem will probably take a while to go away.

Need to find some directions? No problem, use Google Maps. Want to find some spy photos of yourself? No problem, use Google Street View.

Monserrat Morilles sure shook up Chile. She brought a whole new brand of street performance to the city's commuter trains. Her act: strip to a bikini and poledance in the middle of rush hour. Morilles, 26, was protesting the 'prudishness' of Chilean society.

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

You've probably seen those deep-web images floating around on the Internet. Usually, it goes something like this: There is a towering iceberg and the deeper the underwater portion extends, the more “hidden” and “exotic” the content is described to be. Sometimes these images are accurate to a point, but most are just making things up.

The dreaded moment you hope never happens—someone has stolen your laptop. You could have private information, pictures, or even private information belonging to the company you work for, all lost forever. It can cause you pain, money, or even a job.

Are you the expert hacker we're looking for? Do you have a great idea for an article on Null Byte? Do you have a passion to write, and more importantly... teach?

File Transfer Protocol, or FTP, is a network protocol made for transferring files in a client and host fashion over a Transmission Control Protocol (TCP) network, such as the internet. FTP is integrated into most browsers, and you have probably used it before. It is a common way to host files and transfer them easily. To access an FTP, a login is required, unless the server is configured to use anonymous logins (like the Arch Linux mirrors).

Big name individual hackers and hacker groups everywhere in the news are getting caught and thrown in jail. Everytime I see something like this happen, I won't lie, I get a little sad. Then I wonder, how are these guys getting caught? If a group like LulzSec, with all the fame and "1337-ness" can get caught, I think my hacker comrades are doing something wrong.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

Despite the recent problems with the 1.04 update for PlayStation 3 gamers, Call of Duty: Black Ops remains a juggernaut for Activision in the gaming community, and its sales alone prove it.

This video shows how to get your IP address from your computer. Get your IP address.

Over the next few months, I'll be focusing on building a fully functional, long range UAV. This series will consist of several in-depth articles on my progress and the steps involved, so you can follow along and build your own unmanned aerial vehicle!

Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...

Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.

This is the first of a multi-part series on steganography techniques. Steganography, the art of hiding things in plain sight, has existed for a long time, and in many forms. When you manipulate the alphabet to have your own cipher and decipher, this is considered steganography.

SSH is what is referred to as the Secure SHell protocol. SSH allows you to do a plethora of great things over a network, all while being heavily encrypted. You can make a remote accessible shell on your home computer that gives you access to all your files at home, and you can even tunnel all of your traffic to keep you anonymous and protected on public Wi-Fi. It has many great uses and is a must have tool for your arsenal. It was designed to replace the insecure Telnet protocol, which sends ...

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

The Australian government has a dysfunctional history with video games. Any regular Yahtzee Croshaw follower can attest to that. The Parliament has established a series of unfortuante regulations that make games both highly taxed and overregulated in price. Bringing any goods all the way to an island in the bottom of the world is expensive to begin with, and new games in Australia can tip the scales at $80 or more.
After a decent amount of downtime, one of the best indie game sites on the internet has finally relaunched! PixelProspector is a one-man gaming blog and YouTube channel devoted to the weird and beautiful world of indie games. In the first half of 2010, it received a huge boost in popularity from its video 235 Free Indie Games in 10 Minutes, a hypnotic montage of the best indie games the site had to offer at that point. And to celebrate the relaunch of the blog, which now has an improved desig...