For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.

Lifehacker provides a helpful guide for Facebook addicts everywhere. How does one get around an employer's website blocker? The trick is to set up a local web server running from home, from which you can use a proxy to access any site you please.
I assume you are on the same network with your router 1 - open a terminal window

Hi there, nullbytes! I've been recently using NullByte as my only source of learning (almost) and it has proven to be really good to me.
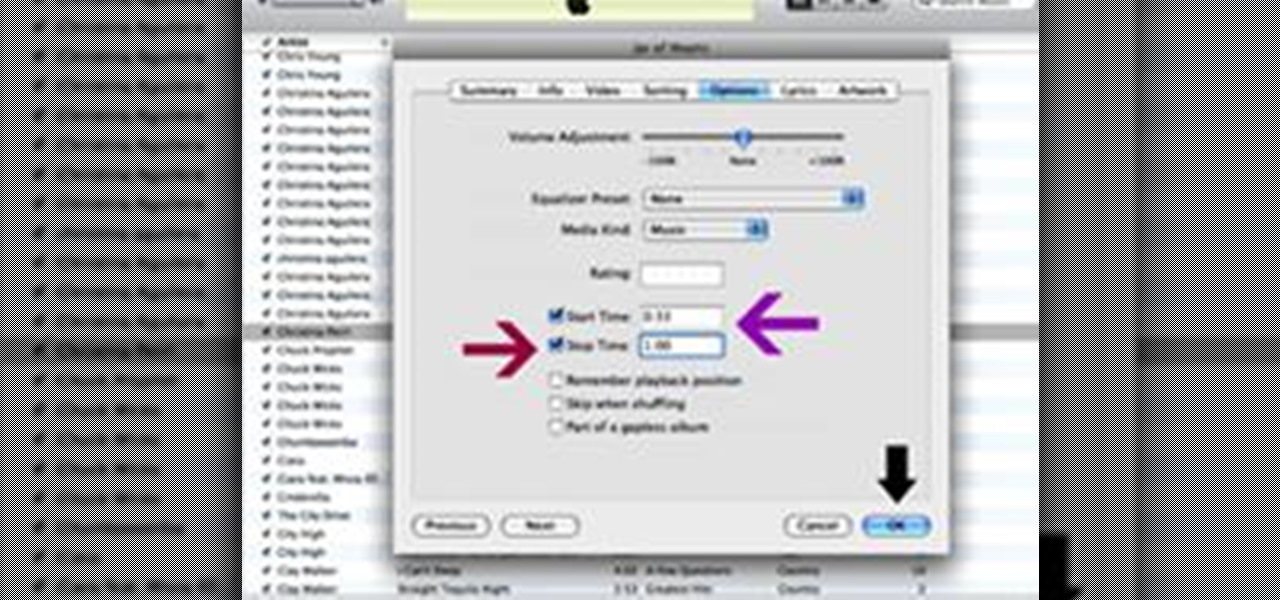
Granted the iPhone is an awesome phone... but their choice for default ringtones kind of, well, stinks. They have plenty of apps you can BUY to PURCHASE ringtones... but why waste money when you can make an unlimited amount of ringtones yourself forFREE? At first glance, it looks complicated and confusing, but I'll break it down so simply, you'll be making ringtones for everyone in iTunes.

Simple test of endurance: light off several fireworks placed in your pants pocket, belt, socks, and in close vicinity.

A lot of different places have computers with controls on them for several things; some have controls for installing software, some for running software, blocking websites, opening certain file formats, etc.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

This tutorial shows you how to download bittorents with uTorrent without risking having your IP address get exposed or traced. You will need to find a proxy server for this to work. Download torrents safely.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

To those who may not know about this, the UK high court has ruled that all UK based ISP's are to begin blocking Piratebay. This comes in retaliation to Piratebay's action to take down all torrents and provide only magnet links to the pirated content - a move which releases TPB from liability should they be once more accused of hosting the actual content.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

How many people use the big search engines here? I'm going to estimate 90% of everyone on WonderHowto uses one of the following on a regular basis: Google, Bing or Yahoo! Search. The question is: are you in that 10%? You should seriously consider dumping Google search for DuckDuckGo. Why? DuckDuckGo does not track you.

Hello everyone and welcome to Part II - The Ultimate Guide: Diagnosing & Fixing Connection Issues. In this tutorial we will discuss more advanced methods that I took in order to fix our home network. I have also attached a link to download the FREE eBook - so feel free to download it to you can refer to this manual when you are experiencing connection issues. I would also like to note that the manual has been loaded onto a free server - it will remain on the server until people stop downloadi...

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

The internet is a scary place, and if you're like me, you don't want anyone tracking you or learning your search habits. It's a blatant invasion of privacy for companies to do this, but at least we have methods of fighting back—one of which is Tor.

This Week's Workshop: Music To My Ears The heart of WonderHowTo's Minecraft World is, naturally, “How-To” and so in the spirit of all things tutorial and DIY we will be hosting a weekly workshop showcasing the best and newest tutorials, builds, and inspiring ideas. We hope to inspire creativity and create a place where the community can share ideas and practice skills, right here on our server.

Shoot-em-up games, or shmups, consist of lone or small groups of players shooting at and being shot at by hordes of colorful enemies. The genre is thought to have peaked in the mid-'90s, but recent games in the indie world may be saying otherwise. Geometry Wars and other twin-stick games kicked off the trend, but newbies Trouble Witches NEO, Outland and just-released Gatling Gears have brought some much needed originality into the modern shmup scene—making it something worth exploring again. ...

The Fake Adult Website Prank is an incredible trick if you happen to have the necessary access and work in the internet industry. Luckily, I had both.

The only thing better than successfully pulling off a new experiment is doing it with household materials. You get to laugh in conceit as professional scientists everywhere spend all their grant money on the same project you just accomplished with some under-the-sink chemicals! However, there are times when DIY gets dangerous. Some household chemicals are not pure enough to use and some are just pure dangerous. Let's take a look at two problems I have encountered in the course of mad sciencing.

If you're hungry, eat now, because this list is probably going to put you off consuming vittles for so long that you'll end up looking like the love child of Nicole Richie and Skeletor. Now that you've been officially warned, help me count down the ten most WTF food items on this beautiful blue marble we call Earth.

Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.
Our class had been assigned interviews with political representatives from different branches. In these interviews we asked questions that we had generated about their career position, advice to young activists, our government system, getting involved, and their opinion on certain laws. Here are the results from the two interviews that were done.

Anonymity is something that doesn't exist today. Everything you do in the world is tracked, from the purchases you make to surfing the internet—even taking pictures on your iPhone. Everything you have ever said and done on the internet is still there—somewhere. This is called caching. For example, when a site is down, you can view its cached page on Google.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

Here, ladies and gentlemen, is my main deck. The youngest card in it was printed in 2000. It makes me feel a little crusty and old for one of the first times in my life. But it does mob pretty well against all of the mostly pre-2000 decks I've played it against (none of my friends really have new cards either) and I'll tell you why:

disguise yourself however you like Go to an airport. have a suitcase full of fake illegal items such as powder (cocaine), crushed leaves (weed), guns, knives and dynamite . make sure it all looks real and also something metal to set off the detector so the search your bags.

Disguise yourself how ever you like. Go to an airport. Have your suitcase full of fake illegal items such as powder (drugs), crushed up leaves (weed), guns and Knives dynamite make sure everything looks as real as possible and also something metal to set off the detector (so they search your bag).

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

How to Make the Internet Faster in Windows 7 Go to Control Panel.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

If you've read my darknet series, you've probably got a pretty good idea of what I2P actually is and is capable of. One of the features of I2P is that it's designed with P2P file sharing in mind. Using a built-in service called I2PSnark, you can host and seed torrents quickly and easily!

In the last article, we left off with the Tor network and its hidden services. As I mentioned, Tor is not the only option in the game, and I want to offer a general introduction to I2P.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

VNC is a great protocol that you can use on Windows and Linux machines to remotely control computers. This is useful if you need to control your computer when away from home, help your grandma check her email, or help a client with a disk cleanup. VNC is secure in the sense that it requires authentication in order to make the connection, but after that, the data is sent over the internet unencrypted. This means that an attacker could sniff your traffic and snoop everything that's going on. Th...