
How To: All the Reasons You Should Root Your Phone
Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.


Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!
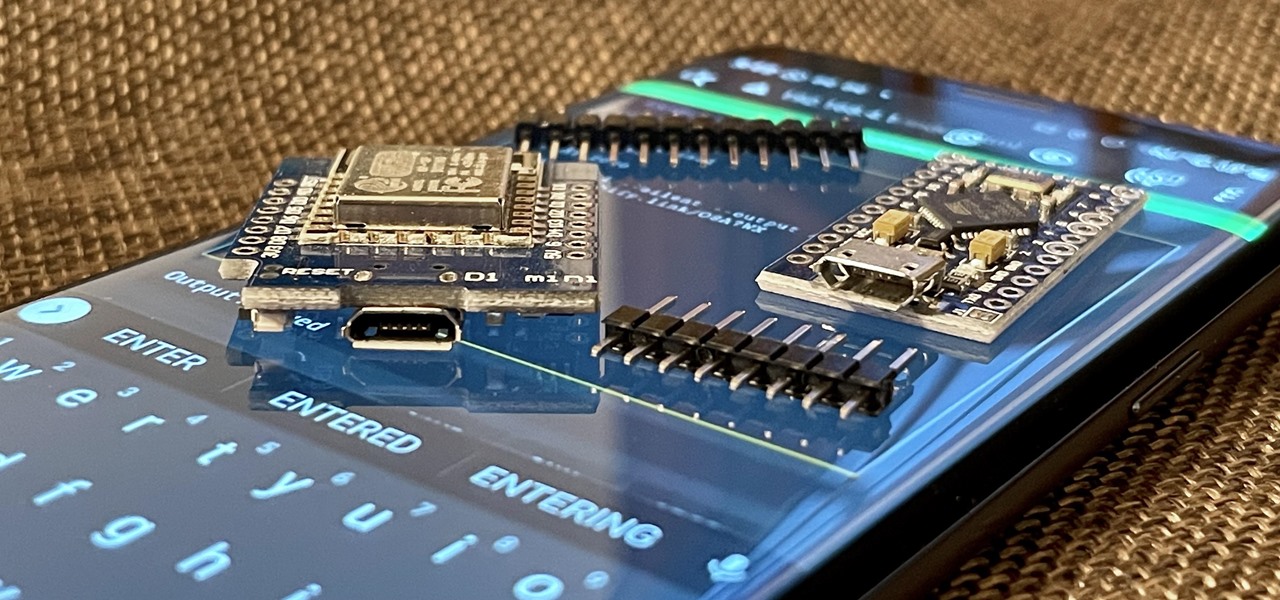
With just two microcontrollers soldered together, you can inject keystrokes into a computer from a smartphone. After building and programming the device, you plug it into a desktop or laptop, access it over a smartphone, and inject keystrokes as you would with a USB Rubber Ducky.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Flight disruptions can cost billions of dollars, but most modern commercial flights rely on air traffic control systems that harbor serious vulnerabilities. The Federal Aviation Administration uses an infrastructure called NextGen, which relies on Automatic Dependent Surveillance – Broadcast, or ADS-B for short.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

Using simply 2 bobby pins and a tension wrench, you should be able to open up a padlock without needing the key. When properly wiggling the pins around, with the right tension, you should be able to break right in. Remember, only pick locks that you own, otherwise it could be considered illegal.

Did you know that you can pick a padlock using simply a paperclip and bobby pin? All it takes is a little wiggling, tension, and precision, and you should be on your way to opening up a padlock. It's recommended that you only perform this on your own lock as attempting to break into other people's locks is illegal.
Learn how to download without using google or any torrents! Single Fish works. But don't do anything illegal now.

It's a trick that never fails to amaze. You're placed in handcuffs, but with a flick of the wrist, you're free! Kick off your career as a daring escape artist with these simple tips.
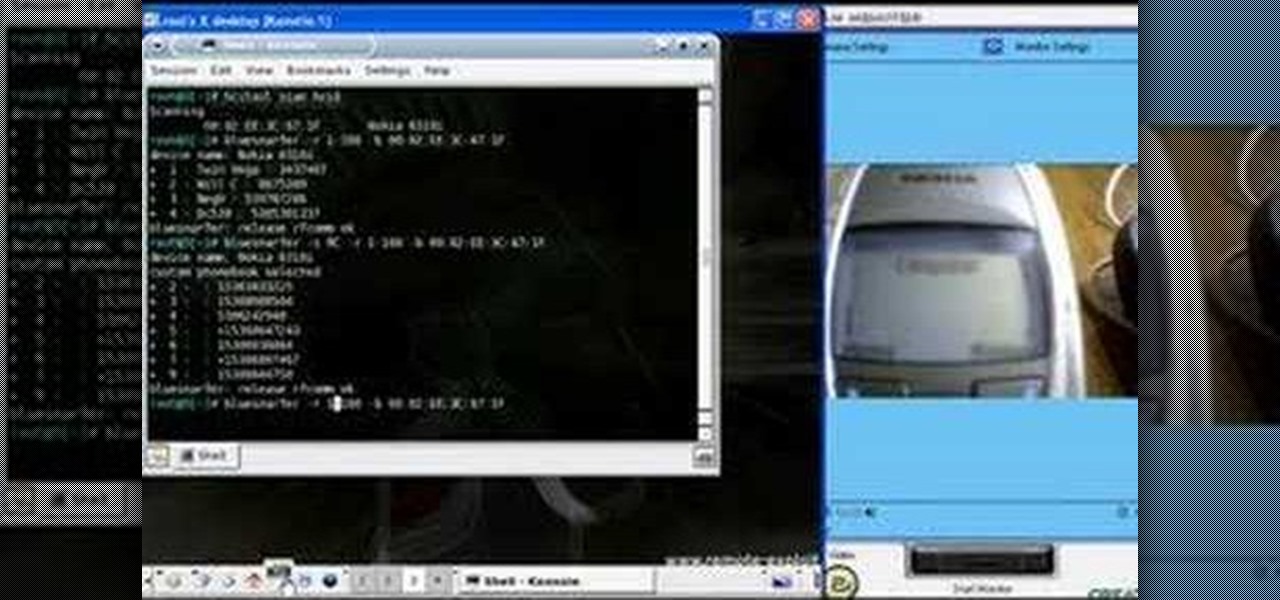
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

In most states, it's illegal to drive while talking on your mobile phone, but that is easily remedied with hands-free calling. If your cell phone comes equipped with Bluetooth, you can sync it right to your 2010 Lincoln MKZ using Ford SYNC. This video shows you the steps to connecting your phone up in your vehicle. Now you'll have more hands for coffee and cigarettes and donuts.
Granted the iPhone is an awesome phone... but their choice for default ringtones kind of, well, stinks. They have plenty of apps you can BUY to PURCHASE ringtones... but why waste money when you can make an unlimited amount of ringtones yourself forFREE? At first glance, it looks complicated and confusing, but I'll break it down so simply, you'll be making ringtones for everyone in iTunes.

What is DansGuardian? Schools, offices and universities often tend to use a software like DansGuardian to prevent people from accessing certain websites - websites like Youtube, Facebook, Myspace, and so on. However, if you ever find yourself in a situation where you need to access a blocked website... it's possible! As a matter of fact, it's quite easy.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Paparazzi are very annoying for the stars but with these sunglasses, paparazzi can't take you in picture .Why ? Because with this sunglasses your face will be invisible to the camera . Disclaimer: CAUTION! . Never use them for illegal act. Make anti paparazzi infrared invisibility sunglasses.
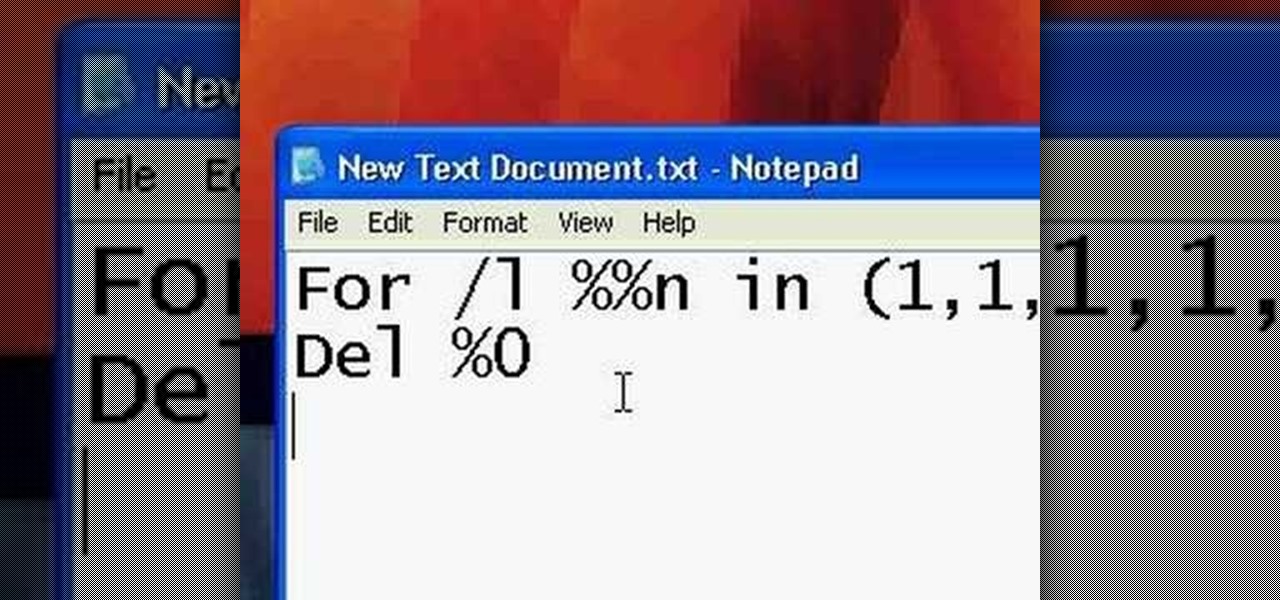
.bat files can be quite dangerous to any machine. Creating and opening these files should be done at your own risk. Sending malicious .bat files over the internet is illegal. This video will show you how to make and use a .bat file to prank your friends. Create an annoying batch file to fool your friends.
.bat files can be quite dangerous to any machine. Creating and opening these files should be done at your own risk. Sending malicious .bat files over the internet is illegal. This video will show you how to make a virus that crashes your computer.

Surveillance expert Julia Adams offers the different ways to secretly record a conversation in this how-to video.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?
On 2 October 2010 Univision held the first Spanish-English debate in the state, which was hosted by CSU Fresno.

From Boing Boing, a highly amusing photo gallery of illegal goods seized by airport customs officials in Australia. Some are fairly typical, but others really make you wonder... Yes, I'm most definitely talking about the tropical fish skirt lady.
Born in Sacramento, CA on January 1, 1958 and raised by two Mexican immigrant parents, Xavier Becerra was the only Hispanic on the House Ways and Means Committee. He was elected vice chair of the Democratic Caucus for 111th Congress and was a reprensentative from California's 31st district. From 1987-90, he was the California Deputy Attorney General. Xavier Becerra was part of the California State Assembly (1990-92) and has been a member of the U.S. State House since 1993.Xavier Becerra is a ...

It seems like the EU is currently in the works of making "the production or sale of devices such as computer programs designed for cyber-attacks" illegal. So, if you're a network admin that uses WireShark or Metasploit, you better watch out!
Many times throughout history companies have been hacked by so-called "grey-hatters": hackers who do ambiguously ethical things with their computer skills. Often enough, after being hacked the companies actually offer to hire the hacker, but not always (as you see in this case). Just a reminder that you need to watch what you are doing. Never do anything illegal unless you don't mind facing the consequences!

This shows how to collect rain water for future use from the roof of your house. Very cool setup, but be careful not to break the law while you're doing it. I know that here in Colorado, it is actually illegal to collect rain water without a permit. Scary, huh?

Immigration is a serious political issue in the United States, and those who oppose or support stricter immigration laws are often outspoken and candid about their beliefs, imposing their will on future legislation to not only politicians, but the general public—the voters. And what's the best way to reach the public? Entertainment.

Do you think that this controversy surrounding GOP nominie Meg Whitman's illegal immigrant housekeeper goingo to affect her votes in her political campaign?

Here is the trailer for the movie "Import Export" If you want to see a really disturbing twisted movie about illegal workers and deviant behavior, check this film out, it will not disappoint.

Acclaimed Cinematographer Adam Kimmel Arrested:

Lost the product key for your game? If you have to reinstall the game and don't have that key anymore, you're out of luck, especially if you didn't "buy" the game. But never be in fear of losing product keys again with today's Null Byte, where we'll be practicing a little bit of mind-kung fu.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.

This Null Byte is the first part in a mini-series on the art of Social Engineering. I will be teaching you how to effectively defend yourself against it.

Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject.

She is kind of cute, in that fetching, illegal is-she-under-18 kind of way. A model from Paraguay. There is a 'green' undercurrent to the headline, in addition to an accomplished arts and crafts sensibility. It is a sweet domesticated how-to.

In this article, I'll show you how to easily "hack" Facebook, Twitter, YouTube, and any number of similar account types with an Android app called FaceNiff.

In this article, I'll show you how to prank your friends on April Fool's Day with the very popular Google Voice, a computer to land/mobile calling feature. Basically, Google allows you to play whatever you like through the microphone port on your computer, and play it right through to your victim's phone. Whether it's Rick Astley ("Never Gonna Give You Up") or a text-to-speech application, general hilarity always follows.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."

Have you ever been away from home or on holiday and noticed an open network connection? FREE INTERNET! But then you find out that every search or page redirects you to an "enter password" or "signup here" page. Well, there are ways around this.