
News: Poem of The Day
The Armadillo For Robert Lowell


The Armadillo For Robert Lowell

This weekend in a jungle estuary, the DEA and local Ecuadorian police seized a prototype narco sub that may be the most sophisticated one yet. Complete with air conditioning and periscope, this 100 foot creation would have carried a more cocaine tonnage than any previously captured narco sub. To give you a perspective on the resourcefulness of these outlaws, consider this. A U.S. Navy Virginia Class attack submarine will run around $2.8 billion. But a drug lord in Cartagena would make you one...

If you happened to be watching Brazil vs. Portugal, you might have noticed something weird in keeper Julio Cesar's back after he and Meirelles collided. It was some kind of steel rod support for his injured back. According to FIFA article 4, it's illegal for players to wear any kind of equipment that can be dangerous to the player wearing it or to others. This is the reason players can't wear chains around their necks, or rings in their fingers, since these things can get caught with other pl...

Do you have AMNESIA? How about SYPHILIS? Or have you gotten SODOMIZED? Well, the people pictured below do, and I don't feel sorry for them, not at all——those words would kill on the SCRABBLE board!

3D Dot Heroes Preview Release Date: May 11th, 2010 for the PS3

Do you know your constitutional rights if stopped by the police? Washington Post recently ran an interesting article on "10 Rules", a docudrama produced by the D.C. nonprofit Flex Your Rights.
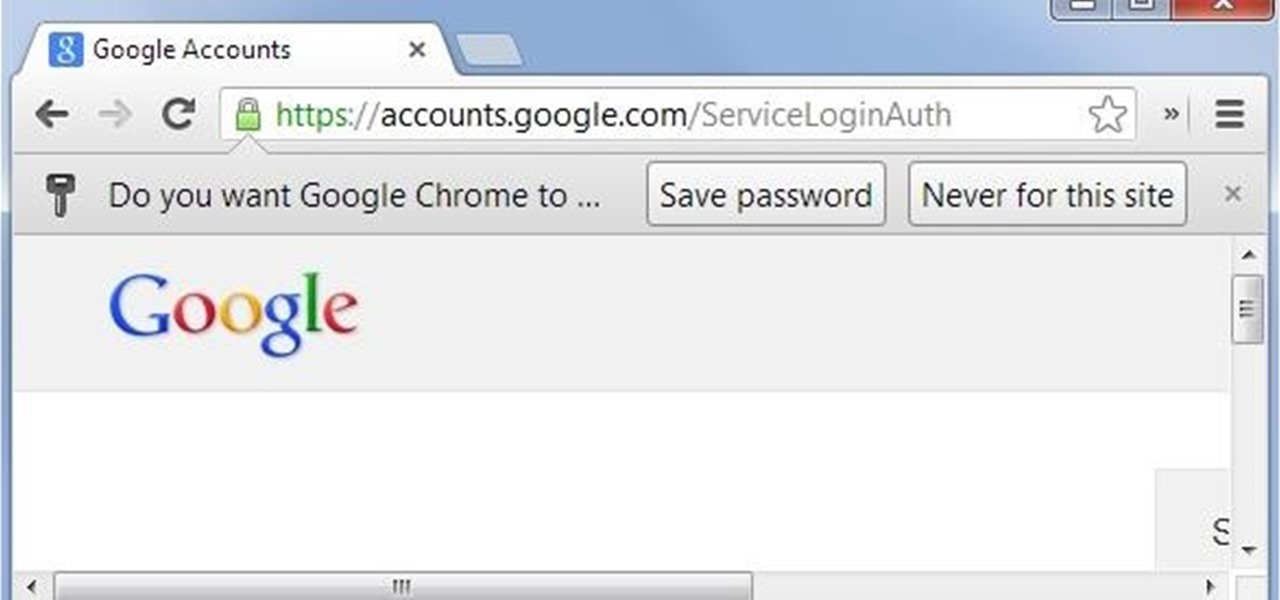
These days I found a very beautifull python script that just prints the google chrome usernames and passwords that are stored on your machine.

Need to be undercover? Well, make yourself impossible to photograph. Get some infrared LEDs. They're undetectable to the human eye, but that's not the case with cameras. Wire them to the brim of your hat and you've got instant invisibility to any camera -- paparazzi, Big Brother or otherwise.

Fist full of pennies weighing you down? This will certainly make your pockets lighter.

Over the next few months, I'll be focusing on building a fully functional, long range UAV. This series will consist of several in-depth articles on my progress and the steps involved, so you can follow along and build your own unmanned aerial vehicle!

Cell phone jammers, a DIY endeavor for the darker crowd. I'm pretty sure we've all considered having one at some point: whether the obnoxiously loud woman next to you is announcing private bedroom stories to a crowd on the subway, or your kids are grounded from using the phone (and consequently snagged a hidden prepaid phone), sometimes having a cell phone jammer comes in handy.

The already robust and ingenious Nmap tool has received a whole slew of new scanning scripts that can be used to do all sorts of naughty endeavors. Notably, the SQLi module, since it is a necessary evil that we must cover here at Null Byte. This major update is going to fuel today's lesson.

With the rather large success of the Community Byte activities, both programming and HackThisSite, I have decided to continue to do both activities every session! With that said, when programming sessions occur, they will be lead by Sol Gates in Gobby. Also, the programming mission will no longer be to code a tool, we have changed it to be even more "noob friendly". This means that instead of coding a tool, you will be walked through puzzles and challenges that must be solved by coding a scri...

Welcome to another Community Byte announcement! For the past few Community Bytes, we coded an IRC bot, and hacked it. Then, we created a web-based login bruteforcer! This week we are going to start something a bit different. We are going to start going through the missions at HackThisSite one-by-one each week, starting with the basic missions.

This is the first of a multi-part series on steganography techniques. Steganography, the art of hiding things in plain sight, has existed for a long time, and in many forms. When you manipulate the alphabet to have your own cipher and decipher, this is considered steganography.

The Australian government has a dysfunctional history with video games. Any regular Yahtzee Croshaw follower can attest to that. The Parliament has established a series of unfortuante regulations that make games both highly taxed and overregulated in price. Bringing any goods all the way to an island in the bottom of the world is expensive to begin with, and new games in Australia can tip the scales at $80 or more.
After a decent amount of downtime, one of the best indie game sites on the internet has finally relaunched! PixelProspector is a one-man gaming blog and YouTube channel devoted to the weird and beautiful world of indie games. In the first half of 2010, it received a huge boost in popularity from its video 235 Free Indie Games in 10 Minutes, a hypnotic montage of the best indie games the site had to offer at that point. And to celebrate the relaunch of the blog, which now has an improved desig...

For most street artists, it takes a considerable amount of time to paint large art installments on the walls of urban structures. The more time it takes, the better chance there is of getting caught, since nearly all of the rogue artwork is slapped on the sides of city and privately owned buildings.

The only thing better than successfully pulling off a new experiment is doing it with household materials. You get to laugh in conceit as professional scientists everywhere spend all their grant money on the same project you just accomplished with some under-the-sink chemicals! However, there are times when DIY gets dangerous. Some household chemicals are not pure enough to use and some are just pure dangerous. Let's take a look at two problems I have encountered in the course of mad sciencing.

If you're hungry, eat now, because this list is probably going to put you off consuming vittles for so long that you'll end up looking like the love child of Nicole Richie and Skeletor. Now that you've been officially warned, help me count down the ten most WTF food items on this beautiful blue marble we call Earth.

Law enforcement can make a lot of folks cringe. Too often do we hear on the news, and even experience in our own lives, the unjust way that an unacceptable portion of law enforcement treat the very citizens they are supposed to protect. People's rights are violate each and every day by law enforcement, simply because they are timid and uneducated with the laws of society. This dirty trickery shouldn't be played on harmless citizens under any circumstances.
Our class had been assigned interviews with political representatives from different branches. In these interviews we asked questions that we had generated about their career position, advice to young activists, our government system, getting involved, and their opinion on certain laws. Here are the results from the two interviews that were done.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Some cops already have the ability to extract data from your cell phone using handheld forensic devices, but soon police officers will have a new mobile data collection toy to play with—an Apple iPhone. Actually, it's an iPhone-based device that connects directly to the back of an iPhone, which is designed to give law enforcement an accurate and immediate identification of a suspect based on their facial features, fingerprints and even their eyes.

Here, ladies and gentlemen, is my main deck. The youngest card in it was printed in 2000. It makes me feel a little crusty and old for one of the first times in my life. But it does mob pretty well against all of the mostly pre-2000 decks I've played it against (none of my friends really have new cards either) and I'll tell you why:

Professionally and academically speaking, I am a computer scientist, but I also enjoy lock picking as a hobby, so I thought I would share what knowledge I have with this. Before we start doing anything, first we need to understand the fundamentals of how locks work and then acquire and familiarize ourselves with basic lock-picking tools.

Everyone's been in the following situation. You're sitting there at a nice bar, chatting up a smoking hot member of the opposite sex when all of a sudden they drop this bomb: "Can you engrave on wood in Photoshop?" The next thing you know, the night spirals into blackness and you wake up in a puddle of your own tears with some half-eaten beef jerky hanging out of your mouth.

How many of you know all the amendments of the Constitution? Do you even know how many there are?? Well, many of the people I speak to don't. And let me tell you, that's a bad thing. Knowing even the basics of the Amendments can have a profound effect in your lives. Ever got pulled over by a cop? Did you know you can deny his request to search your car (unless he sees something 'suspicious')? If you own a gun, you sure know about the Second Amendment. Here's a neat one: a public phone booth i...

Hello and welcome to another InfoSecurity World tutorial. The intent of this article is to teach one how to encrypt sensitive files. When set up correctly with a strong password, it would be almost impossible to hack. Even the FBI have had issues decrypting this software. I'm here to teach you how to create a general encrypted container—not the complex hidden TrueCrypt volume.

In a move that seemingly surprised everyone—including Samsung—Korean carriers have released the Galaxy S5 a full two weeks early to avoid being caught up in an about-to-be-imposed ban.

Have you ever fallen asleep watching television only to be rudely awoken by one of those obnoxious commercials that randomly play three times as loud as everything else? While the FCC actually made excessively loud commercials illegal as of last December, it's up to providers to comply, so the problem will probably take a while to go away.

Need to find some directions? No problem, use Google Maps. Want to find some spy photos of yourself? No problem, use Google Street View.

Monserrat Morilles sure shook up Chile. She brought a whole new brand of street performance to the city's commuter trains. Her act: strip to a bikini and poledance in the middle of rush hour. Morilles, 26, was protesting the 'prudishness' of Chilean society.

Industrial espionage, social engineering and no-tech hacking are all very real and there are simple precautions that you can take to protect yourself, which this article will discuss. Whether you are a high-profile businessman or a housewife (or husband), keeping information you want to keep private, private, should be important to you.

Remember that scene in The Matrix when Trinity uses a realistic Nmap port scan, followed by an actual SSH exploit (long since patched) to break into a power company? Well, believe it or not, but that scene is not far fetched at all. If you want to exploit vulnerabilities and root boxes, you'll need to learn how to perform the necessary reconnaissance first. In fact, you will spend far more time researching your target then you will exploiting it. In this article, I am going to show you the fi...

Before you start snapping away and submitting your photos, please take some time to read the official rules below!

Let's face it, not every logophile is addicted to Scrabble. Without the use of a timer, Scrabble can be a pretty slow game. Even in clubs and tournaments where the standard time limit is 25 minutes per person for a two-player game. Now, take away time restrictions and add two other players and you've got a game that could take up to 2 hours! It all really depends on who the competition is.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

Perhaps one of the greatest embodiments of urban exploration lies in a disturbing and volatile mental health facility in Massachusetts, and its story starts with...

So, you scratched up your $500 Adobe CD and now it's unreadable. You could go buy a new one, but you already purchased it! Searching The Pirate Bay and downloading some Adobe software can usually be easy enough, but what should you watch out for?