
How To: Solve the Rubik's Cube like you never could
This is for everyone who has ever been frustrated by this mightiest of puzzles. Solving the Rubik's Cube.


This is for everyone who has ever been frustrated by this mightiest of puzzles. Solving the Rubik's Cube.

Autodesk Maya, affectionately known as just Maya to its users, is a 3D computer graphics software that makes it easy to create impressive, realistic models of real-life - or imagined - objects. Super useful for graphic designers, film makers and web designers, the program is one that you should study if you're looking to go into one of the fields above.

Pranks are the world's favorite pastime. Everyone loves a good prank, and there's nothing better than keeping someones stomach empty. Imagine the pain and suffering one would endure if he or she could not eat because the fridge will not open. Most refrigerators allow for reversing the door swing. Normally you also switch the handle. But not if you want to thoroughly confuse the victim of this practical joke.

The pen doesn't have to stop on the paper. Your art masterpiece doesn't have to stay on the canvas. You can share your favorite drawings with everyone, right on your own chest. Wear your art designs with pride by using a scanner/printer, a photo editing application, an iron, and Avery iron-on Dark Fabric Transfer paper. And don't forget your tee shirt.

Brooke Burke, a leader in the exercise industry shows us how to get a fabulous butt. These exercises takes fifteen minutes or less. Use a workout ball. Do these three times a week for best results.
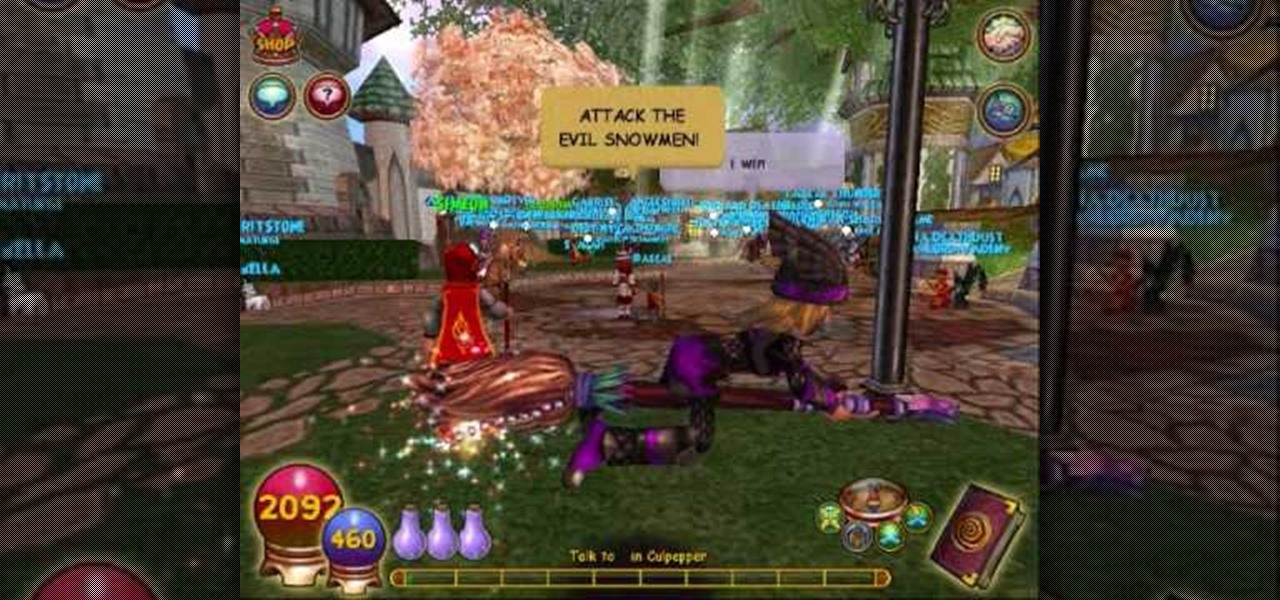
The Wizard101 Test Realm. You can play in it, but beware of scammers, beggars, and spammers! There's nothing worse than getting bombarded with these annoying requests.

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast. Search Systm on WonderHowTo for more DIY episodes from this Revision3 show.

Starcraft 2, like it's predecessor before it, has a very robust level editor that allows you, the DIY modder, to create nearly any scenario within the bounds of the Starcraft 2 engine that you could imagine. We have compiled videos on how to do all sorts of fun things with it, from making RPG's and Tower Defense games to just making you dream Starcraft 2 level. This video will teach you how to create some cool effects for your custom map in Starcraft 2, including a voting system and a creep t...

The lion's breath exercise can be used to get rid of sore throats. To perform this, get into a comfortable position. Inhale deeply. When you exhale, stick out your tongue, as far as it will go. Exhale, releasing all of the air from your lungs. Take in another cleansing breath, and repeat. This time, when you exhale, in addition to sticking out your tongue, you will need to roll your eyes back in your head. Try to make your eyes roll all the way back but slightly inward. Try to imagine that yo...

Can you imagine anybody who doesn't like coleslaw? In restaurants, it's one of the most popular sides to any meal. It's also the most popular salad topping. And it's not hard to make at all, especially with a food processor. You can prepare delicious slaw right at home, for the whole family. Check out this video recipe for creamy cole slaw from Chef Hubert Keller.

This video teaches how to use calculus find the position, velocity and acceleration of an object. Imagine an object moving on a straight line. It's position at any time (t) is given as s(t) pronounced "s of t". It's velocity is v(t)= s'(t) which is the derivative of s(t). It's acceleration a(t) is the derivative of its velocity v'(t). If we look at it from a different perspective we are differentiating. The derivative of the position is its velocity, the derivative of its velocity is it accel...

Changing a toilet is really not the dirty and difficult job that you would imagine. Start by turning the water off using the valve that is located on the wall. Empty the tank by flushing the toilet and holding up the drain valve. Soak up the excess water with a sponge. Disconnect the water line and loosen the bolts that hold the toilet down. Cut through the caulk seal at the bottom of the toilet. Remove the toilet and the wax ring that is around the opening of the drain. Remove the wax ring a...

The increasingly important world of white hat or "ethical" hacking is getting competitive. Thanks to growing salaries and opportunities for talented and trained coding pros who can infiltrate servers and safeguard networks against digital threats, demand for intrepid cyber warriors is through the roof, and it shows no signs of slowing down any time soon.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.
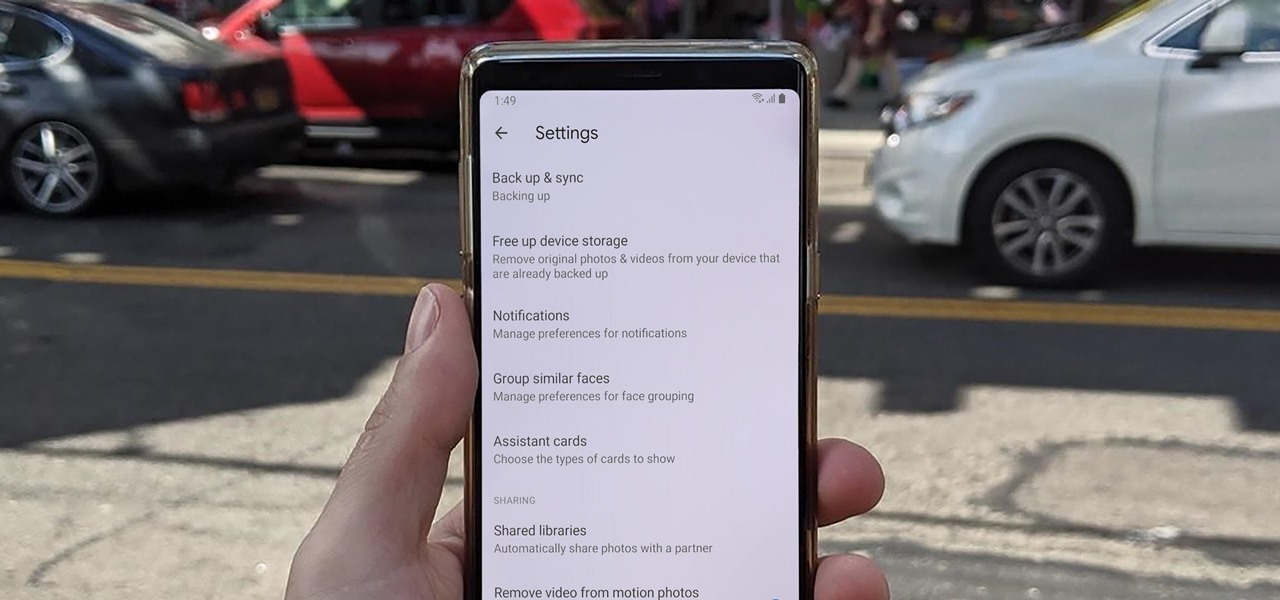
Sharing pictures from Google Photos by sending a link saves time because you don't have to download the image from Google, then reupload it somewhere else. But anyone who has your link can access your pictures, and baked into every file is metadata that you may not want prying eyes to know about.

Over the past two years, Apple's Worldwide Developers Conference (WWDC) has become a showcase for new ARKit capabilities. This year, it could offer more information related to Apple's long rumored augmented reality wearable.

Next to Game of Thrones, Harry Potter is one of the most beloved franchises in entertainment today, and now we have another peek at its dive into augmented reality.

Location services company Mapbox has added new capabilities to its location-based gaming tool to fend off Google's challenge for the same mobile app category.

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.
Apple announced upcoming changes today to prevent third-party tracking of users and prevent autoplay, on Safari. Safari will prevent the recording (by anyone other than Apple) of users' browsing behavior, and by doing so prevent advertisers from targeting ads based on individuals' history.

It wasn't too long ago that Uber threatened to fire star engineer Anthony Levandowski. Eleven days to be exact. If Levandowski didn't turn over the documentation he allegedly stole from Google's autonomous car division, Uber informed Levandowski that they would take "adverse employment action." Today, The New York Times reported the ride-sharing firm has delivered on that threat. In a memo sent to employees Tuesday morning, Uber announced Lewandowski's official departure from the company "eff...

Google Home now helps users to discover new music with an added "Listen" tab in the app. The feature offers suggestions based on the Cast-enabled apps on a phone, while offering other apps to download if you'd like to broaden your musical horizons. The playlists are curated to your individual taste and will adjust for different artists and activities, which is a pretty nifty feature. This means that Google Home can cater to your momentary mood change with music, which is a welcome addition to...

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

I don’t buy socks—I get a pack from my parents on Christmas Day, so I’ve got to make sure they last all year. Other than losing them mysteriously in the dryer, the biggest threat to my limited sock collection is a stretched out cuff. Nothing's more frustrating than a loose sock sliding down into your shoe.

Welcome back, my budding hackers! In previous tutorials, we've looked at some of the basic commands and concepts for using Linux. Along the way, I realized that I've failed to provide you with some basic background material on the stdin, stdout, and stderror.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

If you have a Mac running Mountain Lion, I'm sorry to tell you that all it takes to crash almost any app on it is eight little characters. This strange bug seems to only affect Mountain Lion and doesn't cause your computer any harm. Apparently, it even crashes the error reporter. On its own, the bug doesn't really pose a threat—just don't type it.
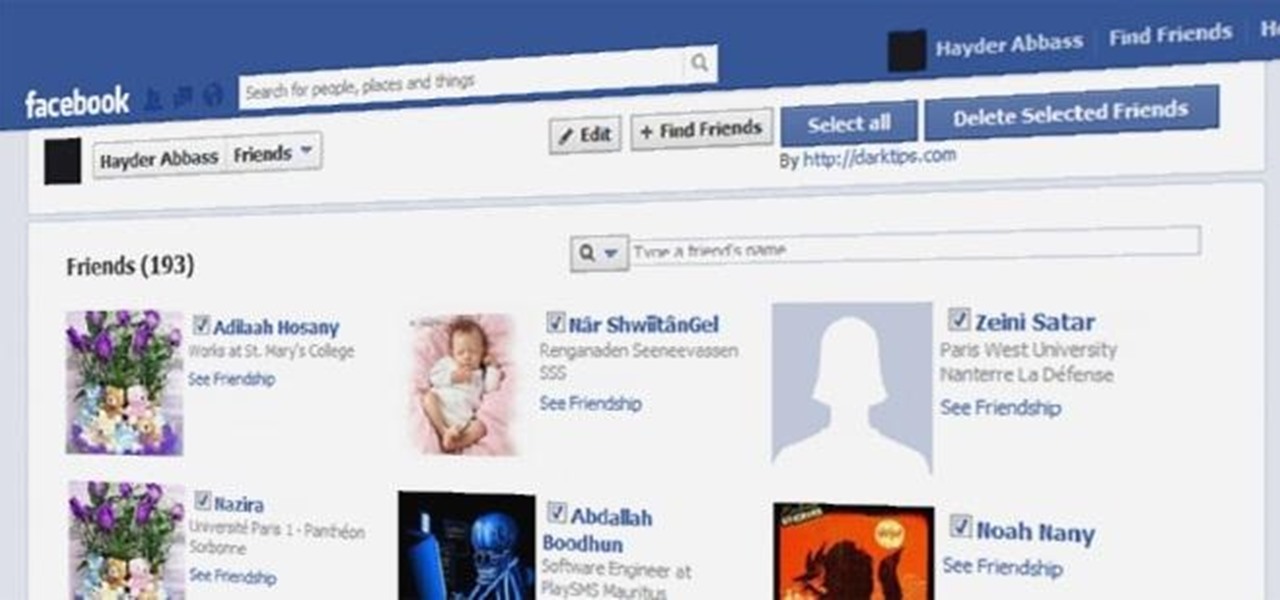
Facebook makes it extremely easy to keep in touch with family and friends, while maintaining those relationships with little to no face-to-face contact. It's the perfect tool for recluses.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

Some of us use our smartphones for almost everything. Manufacturers know this, so they try to make their devices as convenient as possible to use, but sometimes that convenience comes with a cost to security. The very same technology that allows you to easily share music with friends and make purchases can also put you at risk. Photo by sam_churchill

This is a video about how to create a simple water color painting. First we have to select the seen that we are going to paint on the paper. Next give a rough sketch on the paper about the scene that you have imagine or select to paint with a pencil. Next take the water proof marker give the outlines to that paint. Then you have to give two washes to your paint. First one is warm wash. For that you have to take yellow, orange, and red colors. First wet the paper with the water. Next splash on...

John Campbell shows you how to make an all natural bowl with spout using hot coals to burn the desired shape into a block of wood. First you'll need to make a straw from a cattail stock by burning through the center with a hot coat hanger. John next demonstrates how to use this straw and some hot coals placed on the wood to burn the shape of a bowl and spout into the block. Finally, John uses a stone to sand the bowl down and remove the charcoal leaving a clean wooden container. The final res...
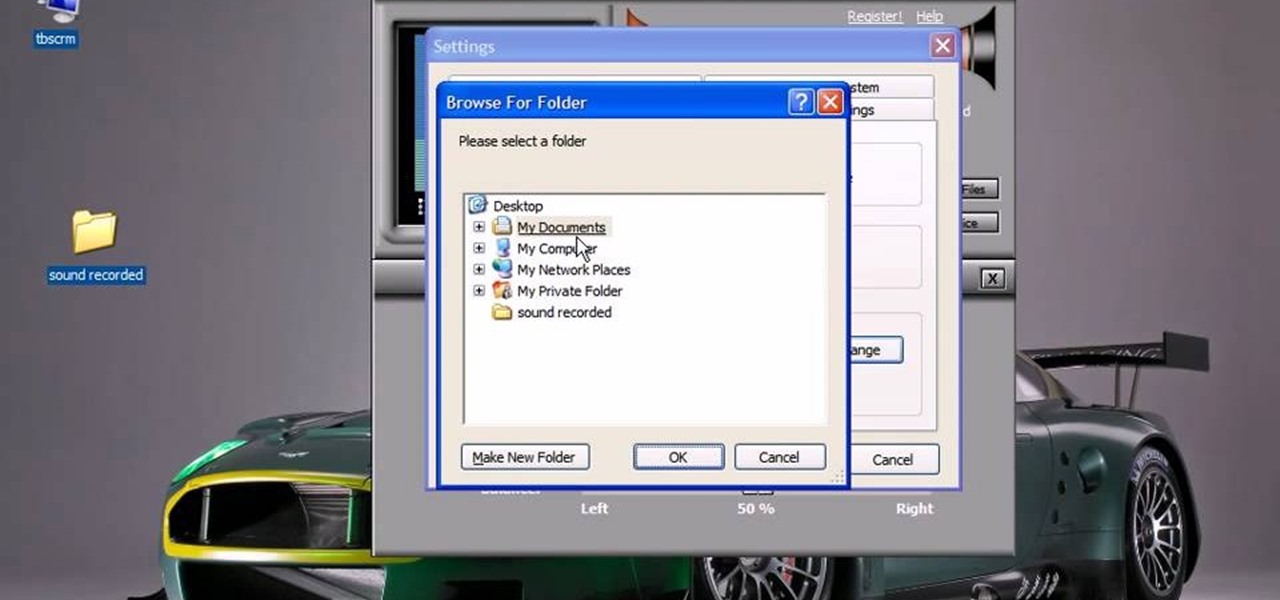
This video will show you how to record audio from the internet. Once you install this program, the video goes on to give you step by step instructions on all of the bells & whistles within the Free Sound Recorder. It will teach you how to work it according to your computer settings, and show you how to personalize and change the settings within the program. It gives you recommendations on the best options for the best audio. It also gives suggestions like choosing which folder to default all ...

Interested in chakras? Boost the seven energy centers from the base of your spine to the top of your head for optimum health and vitality. Learn how to awaken chakras with help from this video.

Worried about your or someone you love's relationship with alcohol? Not all alcoholics fit the stereotype of the down-and-out drunk. Learn to recognize the warning signs in yourself or a loved one.

If you have habits that are repetitive, time-consuming, and don't seem to make sense, and they interfere with daily functioning, you may have Obsessive-Compulsive Disorder.