My autistic son loves music. One afternoon, when he was nine, I downloaded GarageBand to his iPhone to help with the boredom of a long wait at a doctor's office. Instead of pacing or escalating into a meltdown, he spent the entire hour and a half practicing, learning, and composing. When we finally left that day, the rest of us exhausted and irritated, he shared his first composition with a big smile.

You've probably heard of RCS messaging. The new standard has been promoted by Google as their answer to iMessage and is the backbone behind the new "Chat" features in Android Messages. With RCS, Android phones will now enjoy enhanced messaging like iPhone users have had for years — but is it really the same?
Once again, LG is mixing up its launch. Instead of the announcing the latest entry in G series later in the year, the LG G8 ThinQ was announced at Mobile World Congress 2019, shortly after Samsung's Galaxy S10 event. And instead of trying to match what other OEMs are doing, LG is once again trying to be different.

A rainbow table can be thought of like a dictionary, except instead of words and their definitions, it holds combinations of characters on one side and their hashed form on the other. What is a hash and why would you want to know what random combinations of characters are hashed into?

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.
Since its humble beginnings on the iPhone 4S, Siri has come a long way. While each iteration of iOS sees new features for the iPhone assistant, iOS 12 offers users some of the best advancements in Siri we've seen in a long time, not the least of which is support for Shortcuts, Apple's replacement to the Workflow app.

Think back to when you last wanted to transfer some music or videos to your friend's smartphone and how difficult and slow it was. As powerful as our phones are, the default file sharing options are limited. There are, fortunately, some better options which make moving files easy, secure, and painless.

After getting confirmation from Tim Sweeney, CEO of Epic Games, we now know Fortnite Battle Royale will not be available on the Play Store when it's finally released for Android. Instead, users will have to download the APK directly from Epic Games' website — and quite frankly, this is a bad idea.

Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

2017 was a down year for HTC. First, the U11 and U Ultra were widely criticized. Later, Google purchased a large chunk of HTC's manufacturing division, leaving the Taiwanese company running with a skeleton crew after losing 2,000 key employees. But that's not stopping HTC — their flagship U12+ was just announced, and it's quite impressive.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Introduced on the iPhone 6s, 3D Touch is just about the closest thing to a "right-click" that we have on iOS. Apple and app developers utilize this feature to give us helpful options that might otherwise clutter the overall app experience, as well as opportunities to "peek" into an action without committing to it. Safari on iPhone is no exception.

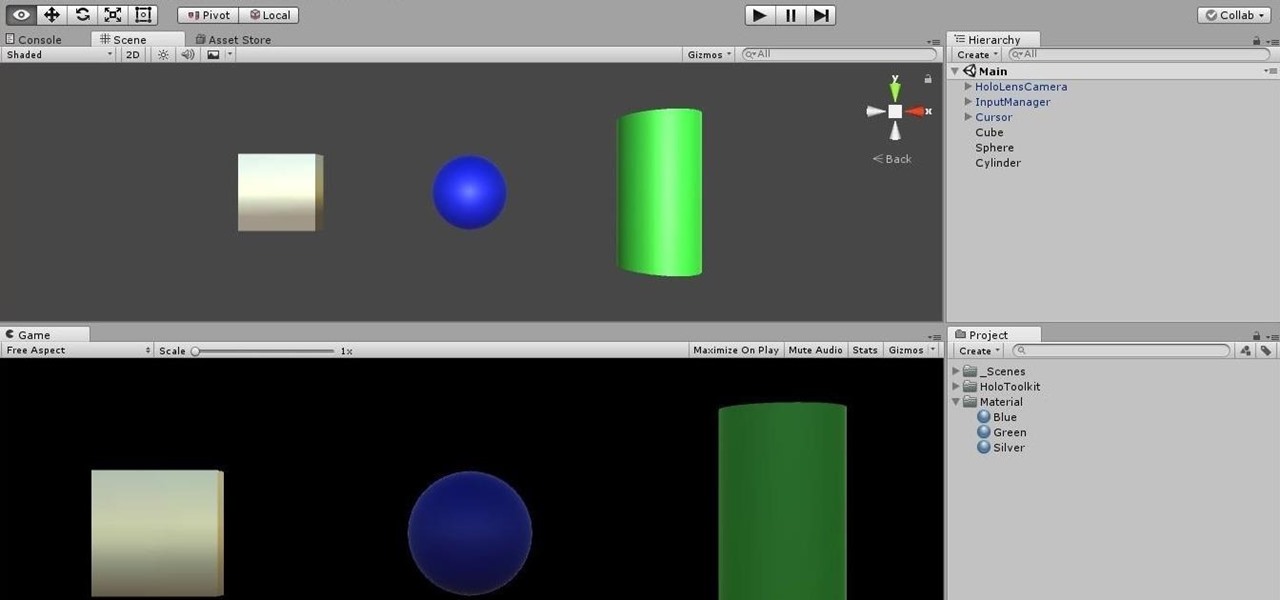
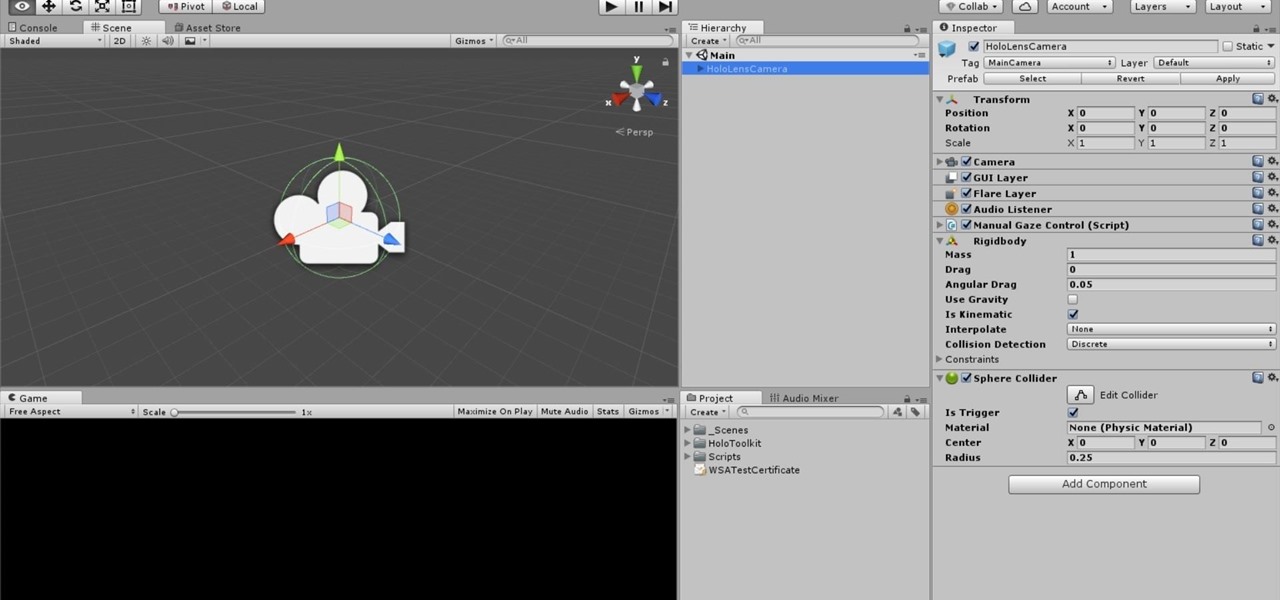
An incorrectly scaled object in your HoloLens app can make or break your project, so it's important to get scaling in Unity down, such as working with uniform and non-uniform factors, before moving onto to other aspects of your app.

While the Twitch app for iOS came out way back in 2011, livestreaming iPhone games was a rarity until Apple recently updated its ReplayKit in iOS 11. However, Twitch hasn't jumped on the bandwagon yet, but that doesn't mean you can't livestream your iPhone games to Twitch right now.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

Apple has been in hot water ever since the news that the company slows down iPhones with older batteries. The iPhone maker is now in damage control, offering customers a large, $50 discount on battery replacements. The question for you, though, is does your iPhone need a battery replacement in the first place?

As smartphones become more accessible, billions of people have come to depend on their features for daily life. One of the most important aspects these days is the camera. OEMs have been working for years to improve camera quality, and they seem to have finally figured it out — the best way to achieve DSLR-quality photos wasn't just with better sensors, but with better intelligence.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

The LG V30 is an amazing device that will contend for best smartphone of 2017. It has all the major features you'd expect from a high-end flagship, and it even includes what's become a rare commodity these days — a headphone jack. However, for the purists out there, the LG UX skin strays too far away from stock Android. Have no fear, for with the LG V30, you can have your cake and eat it, too.

In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

Being part of the wild frontier is amazing. It doesn't take much to blow minds of first time mixed reality users — merely placing a canned hologram in the room is enough. However, once that childlike wonder fades, we need to add more substance to create lasting impressions.

One of the truly beautiful things about the HoloLens is its completely untethered, the-world-is-your-oyster freedom. This, paired with the ability to view your real surroundings while wearing the device, allows for some incredibly interesting uses. One particular use is triggering events when a user enters a specific location in a physical space. Think of it as a futuristic automatic door.

New releases of iOS are always pretty exciting. I remember the anticipation buildup of iOS 7 before it was announced at WWDC 2013, as it was expected to be a complete game changer compared to previous versions—and it was.

I'm an Android user. Over the course of the past seven years, I've owned ten different smartphones—all of them powered by Android. This isn't due to some blind trust in Google or some unfounded hate for Apple, either, because I've always made sure to get my hands on each iPhone iteration along the way to see what it had to offer.

Knowing if your meat is cooked properly is both the difference between a delicious meal and an inedible one... and the difference between making your guests sick and keeping them safe.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.
Welcome back Hackers\Newbies!

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!