Traditionally, if you were looking for end-to-end encrypted messaging, you'd stick with something like iMessage, WhatsApp, or Signal. However, if you already use Facebook Messenger, you have all you need for truly private chats with its built-in E2E encryption. It's available to all users, on Android and iOS — you just need to know where to look.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Texting has become the king of communication—gone are the days where everyone called each other. These days, it's down-right weird when someone calls first. Whether it be on a phone or on a computer, SMS and MMS messages are the most common way people keep in contact, so why not make sure your app of choice is the best possible one out there?

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

As you know, it's impossible to be a Steampunk without a pair of goggles. In fact, there are entire communities dedicated to judging other Steampunks based solely on their goggles. A Steampunk without goggles is like Samson without his hair, or a duck without a beak—totally powerless. As I'm sure you also know, the right pair of goggles can instantly render any outfit Steampunk, no matter what it looks like.

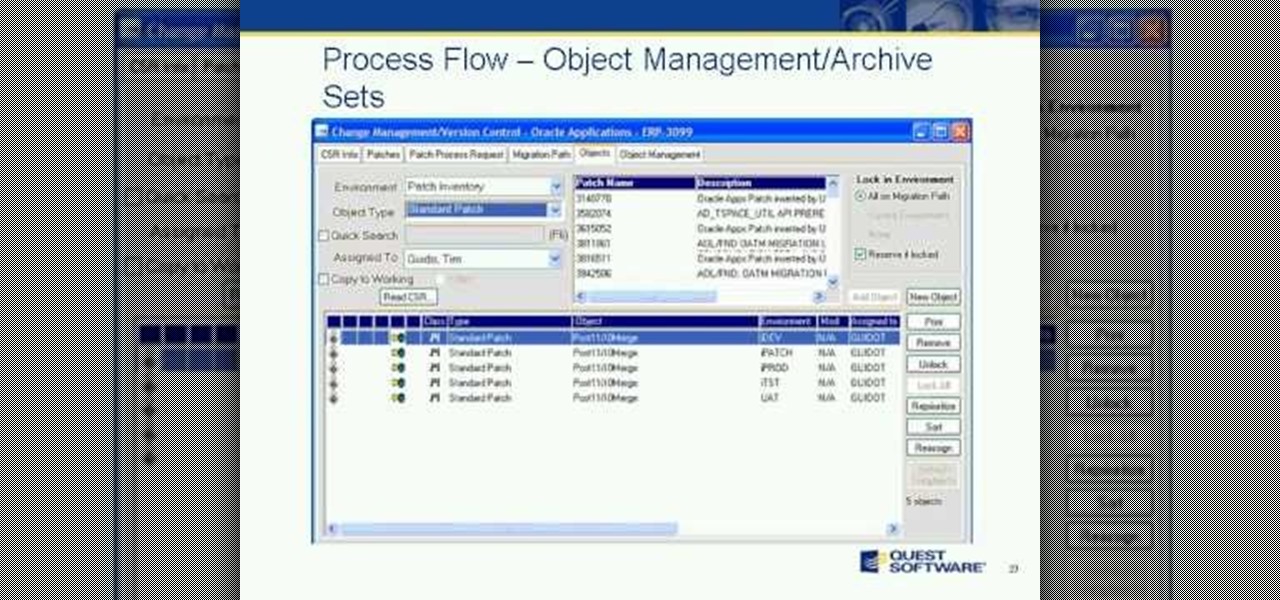
Join us and guest speaker, Cary Pochek - ERP Project Manager at Curtiss-Wright Corporation, as we discuss the importance of change lifecycle management when dealing with Oracle E-Business Suite implementations and upgrades. We will focus on best practices around:

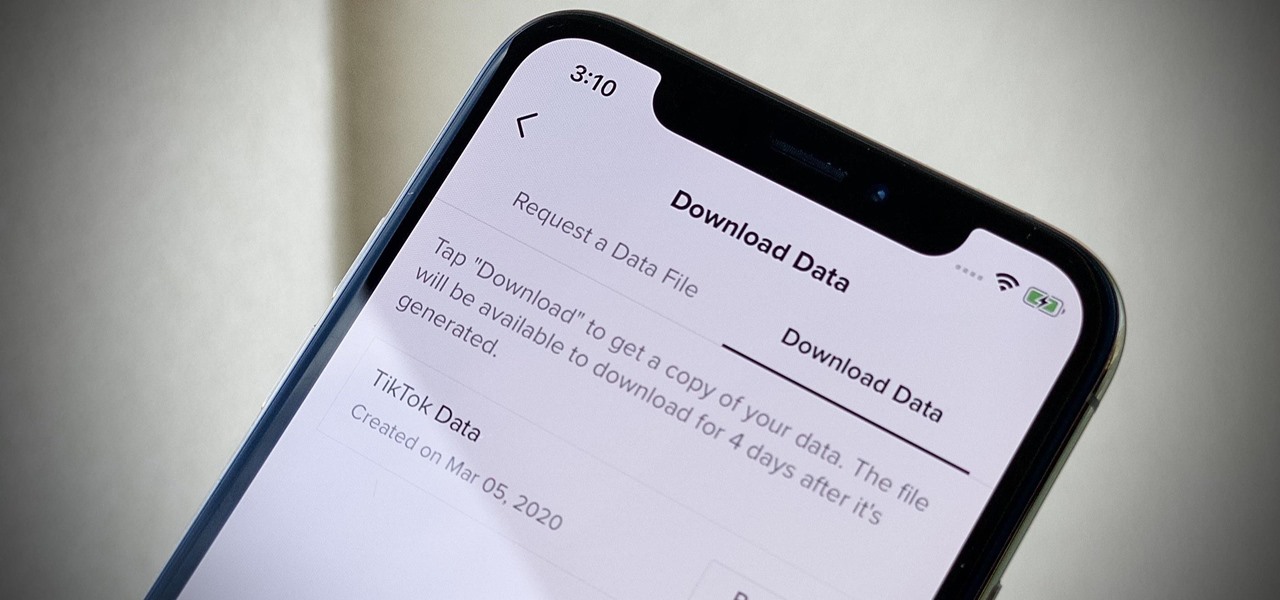
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Alongside Sesame Street, the Dr. Seuss universe has been a constant presence in the formative years of several generations of children in the US.

The Unity 3D engine is not only responsible for facilitating the creation of 60% of AR and VR content but it also plays a significant role in producing the immersive stories that increasingly push the boundaries of cinema.

After opening up its Spark AR platform on Instagram for all creators, Facebook is already expanding the platform's capabilities on its Snapchat killer.

The iPhone's home screen gets its signature aesthetic from a grid of icons that seamlessly blend in to almost any background. It's a somewhat minimalistic look, but that's interrupted by cluttery text labels for apps and folders. Fortunately, there's a way to remove these labels, but you'll have to be jailbroken to pull it off.

With Android 10 hitting the streets (at least for those mobile devices that get quick updates) and the public release of iOS 13 dropping on Sept. 19, Google is releasing an update on Thursday to ARCore that adds some fantastic new benefits to its cross-platform capabilities.

Although early attempts at consumer smartglasses have employed trackpads and handheld or wearable controllers for user input, its the gesture control interfaces of the HoloLens 2 and the Magic Leap One that represent the future of smartglasses input.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

If online retail is war (and who says it isn't), then CGTrader is prepared to arm its allies with augmented reality ammunition.

When you think of companies that represent pillars like "privacy" or "security," Facebook is pretty far from the top of that list. However, the social media empire is making strides — small strides — to win trust with how it handles your user data. One of those efforts involves a way to prevent Facebook from tracking your iPhone or Android phone's location when you're not using the app.

Your Instagram feed is jam-packed with interesting and lively photos, videos, and stories that largely offset the iOS app's comparatively bland user interface. If the interface's dull colors have always bothered you, you can splash on some much-needed color to better reflect your personality and tastes.

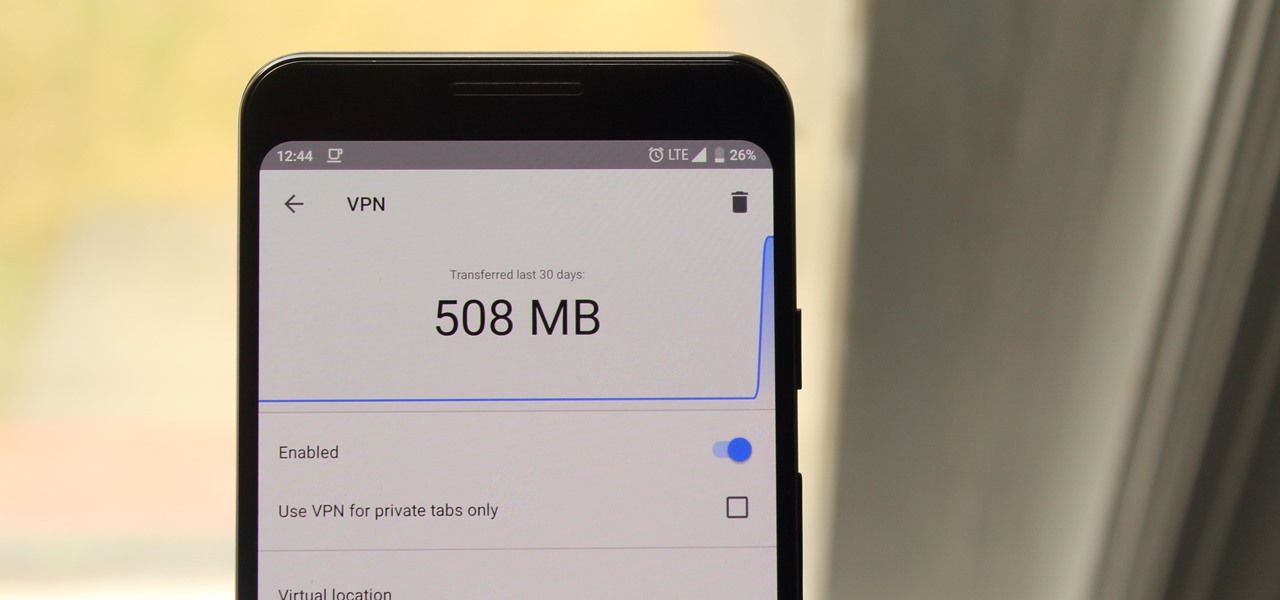
Browsing the web can be dangerous. With all of the various threats out there, it isn't enough to just avoid bad links and visit only HTTPS websites. You need to take advantage of the tools available to you so you don't end up the victim of some scam. Fortunately, Opera is making this a bit easier.

By default, there aren't many customization options for the notification badges on iPhones — you can either leave the numbered red bubbles there, or turn them off. But thanks to a new jailbreak tweak, you can now give your badges a unique look with new functionality.

Augmented reality gaming company Niantic Labs is now instigating conflicts between Pokémon GO players, but it's not as bad as it sounds.

When I review apps, I'll oftentimes end up downloading at least one or two "bad" apps that either lied about their functionality or were riddled with ads. These apps, while not as harmful as malware, can still be a major headache. This got me thinking about the other bad apps on the Play Store and how to avoid them.

Automotive augmented reality company WayRay has set its destination for a $1 billion valuation with an estimated time of arrival of 2019, and it has just passed a major milestone towards that goal.

Samsung makes more than just the Galaxy S and Note series. With a large portion of the world not able to afford phones with flagship specs, Samsung makes several different series that focus on price. The latest is the Galaxy A6, a budget option with a flagship feature.

Now that we've had a few days to recover from the VR geek versus augmented reality nerd battle between Oculus founder Palmer Luckey and Magic Leap founder Rony Abovitz, we can get back to taking a closer look at the Magic Leap One. This time, we take a very brief dip into the Abductor app.

If you're not impressed with the current crop of AR content, and you're worried this may put a damper on the industry's growth, these stories should give you cause for some optimism.

Project Fi, Google's MVNO, is running a new promotion on the latest and greatest from LG. From July 16 until the 29th, whenever you order and activate the LG G7 ThinQ or LG V35 ThinQ, you will receive a $300 service credit. When you do the numbers, that equals a minimum of three free months of service.

When you receive a photo or video from a contact in WhatsApp, after you load it, it's automatically saved to your phone's local storage. That means all received content from WhatsApp is visible to anyone who gains access to your default photo gallery. Luckily, there's a new feature available for the Android version of the app that can prevent this from happening.

For those of us who love to multitask, picture-in-picture mode is a godsend. The feature, introduced in Android 8.0 Oreo, lets you enjoy videos in a floating window overlaid on top of another app. However, while the OS does have native support, only a select number of apps support the feature.

While privacy and security are cornerstones of Apple's ecosystem, your iPhone isn't bulletproof. Creating a strong passcode will protect you from most threats, but there exist tools that can break through even the toughest passcodes via the Lightning port. Luckily, Apple has implemented a new security feature to disable your Lightning port and keep your data safe and secure.

This time last year, computer vision company uSens introduced a stereo camera module capable of hand tracking. Now, uSens can achieve the same thing with just a smartphone's camera.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

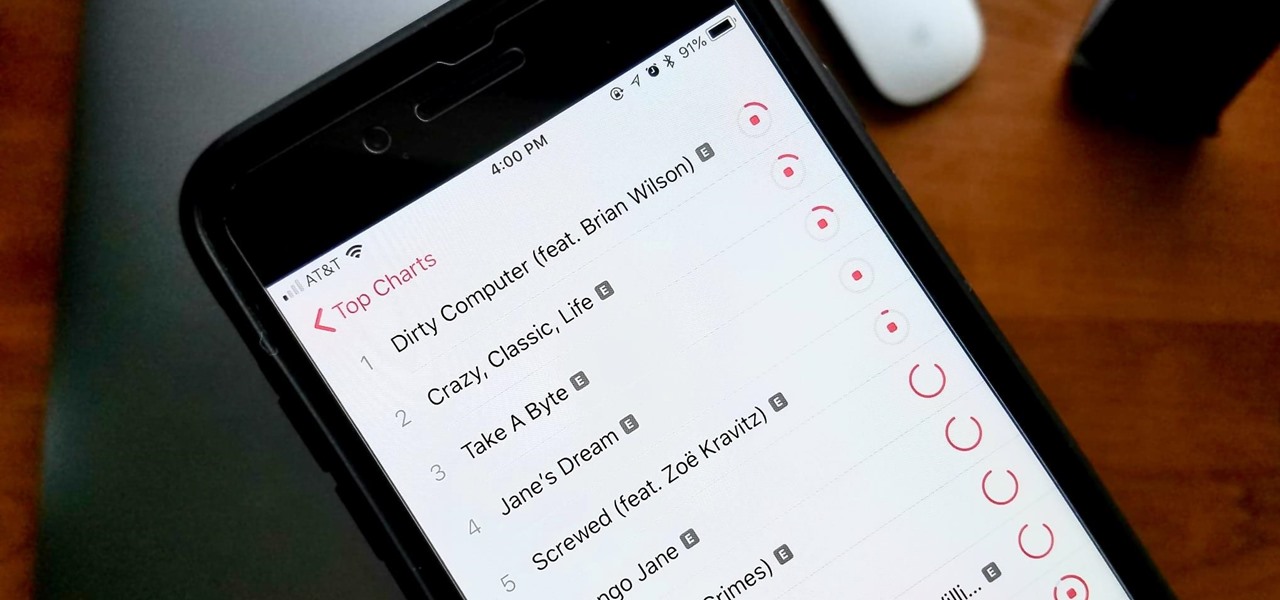
When you've exhausted your data plan, streaming isn't an option unless you want overcharges. While Apple Music makes it easy to download songs for offline listening, you need to add the music to your library first. This creates an extra step in downloading music, but it doesn't have to — Apple Music lets you automatically download any song, album, or playlist that you add to your library.