It's been over a year now since Google introduced a visual way to track down which tabs are playing audio in Chrome, something that was previously only available using third-party extensions. However, they still didn't give an easy option for shutting those tabs up without having to stop what you're doing.

Early last year, Google purchased Quest Visual, acquiring the immensely popular augmented reality translator app Word Lens in the process. While Google did put the feature on the Google Glass, they spoke more about implementing Word Lens into their Translate app sometime in the future.

Google+ doesn't have quite the user base of Facebook or Twitter, but for Android enthusiasts, it's definitely the place to be. All of the major developers—such as Chainfire and Koush—make their social media home on Google+, and the Android app sports one of the nicest interfaces of any comparable platform, chock-full of Google's Material Design.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.

In my opinion, the greatest food hacks are the ones that help you cut way, way down on dishwashing. That's especially true when it comes to baked goods, which usually involves dirtying up a couple of mixing bowls, measuring cups and spoons, some kind of stirring implement, and the baking pan itself.

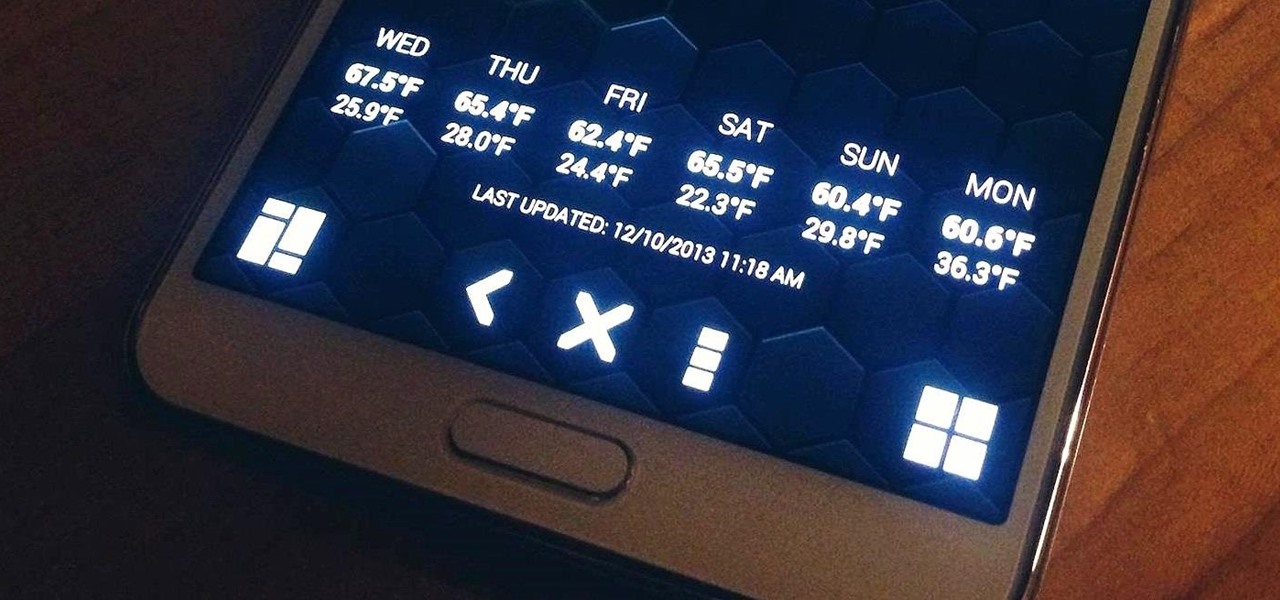
Your device has several volume levels that are regularly adjusted: the alarm, media, and ringer. Keeping track of the various volumes on a device can become an easy-to-forget task, potentially resulting in you not hearing an alarm in the morning, as you have to enter the sound options or trigger a volume change, then expand the dialog box that pops up.

Even with display sizes increasing by the year, smartphone screen real estate is still at a premium. We want the content we're viewing to take center stage, and this leaves little room for functionality beyond the focused app.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

When Google first introduced Android 4.4, the most glaring user-facing change was a new trend towards transparency. The stock launcher, originally exclusive to the Nexus 5, had transparent status and navigation bars and its app drawer added a touch of transparency.

Veering from common practice, XDA commenter, "the_commenter", discovered a changelog for the upcoming version of Android 4.4.3 tucked away on Google's servers.

Let's say you're watching a video and everything's going great, but you feel the need to raise the volume a tiny bit. You hit the volume button on your Nexus 5, and all of a sudden, a giant volume slider appears that obscures half of your video for 3 seconds.

When the Nexus 5 was released, a new version of Android came along with it called KitKat. In the 4.4 update were some fancy new UI elements, one of the most noticeable being the translucent decor. By that, I mean the status and navigation bars being semi-transparent.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

Android updates are a funny thing—they give us a host of new features and upgrades, but they can also change things that we're used to. And sometimes we prefer to have things the way they were.

Privacy features have become quite the hot commodity, emerging from the aftermath of the NSA scandals that rocked the United States this past year. While the NSA has the means to gather information on all of us (regardless of any security software we implement), it doesn't mean that they're the only ones looking.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

In a world where more features are king, sometimes it's a good thing to breathe, take a step backwards and keep it simple. With home launchers, this isn't often the case, as developers add a galore of features to their apps in order to be at the top of the game.

The new Samsung Galaxy S4 has something no other phone has ever had before—weather sensors. Older devices like the Galaxy Nexus, S3, Note, and Note 2 do have a atmospheric pressure sensor, aka a barometer. However, they do not have a thermometer or hygrometer like the GS4 does, which measures ambient temperature and humidity.

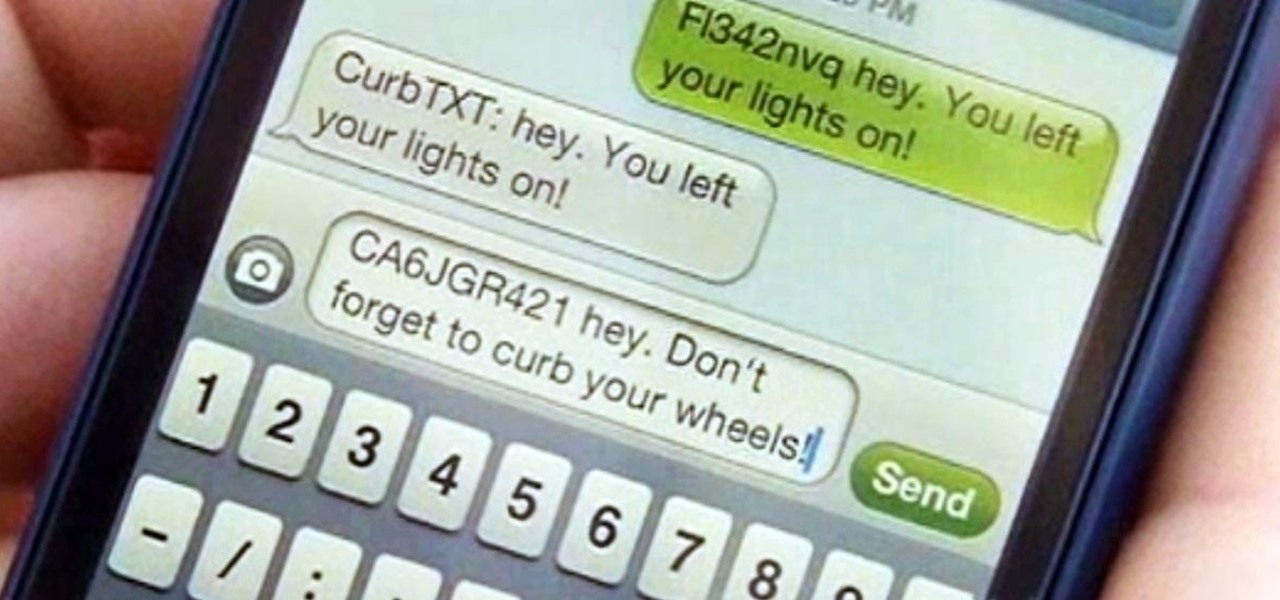
Last month, Alexander Heit drifted into oncoming traffic after being distracted from the road. His sudden correction forced his vehicle to roll and flip over. He was pronounced dead at a local hospital shortly thereafter. All because of a freaking text message. He was only 22 years old.
Your company is deciding on starting new projects but there is a lot you need to do to make sure these projects are right for your company and will be financially rewarding to the bottom line. Before you begin you and your project management team will need to go through a Project Evaluation Process.
Project management covers a lot of processes needed for project completion. Among the many functions in managing projects, one of the most important is resource management. It is an aspect of project management which deals with various project management resources like human, materials, equipment and costs.

A lot of people have problems with their cats urinating inside the house, leaving behind the retched odor of cat pee. Others get frustrated when feral or stray cats pee on their porch, patio, or anywhere else outside of their house, as it's not the most welcoming odor when guests arrive.

Parking. Ugh. Parking is about as fun as running through a swarm of bees while being chased by a pack of wolves from The Grey.

Have you ever found something in your suitcase that wasn't yours? Maybe it was, but you're almost certain it wasn't. Maybe a friend slipped something in your baggage before your departure flight? Maybe the TSA was playing a joke on you, since they have all the master keys for your approved travel locks?

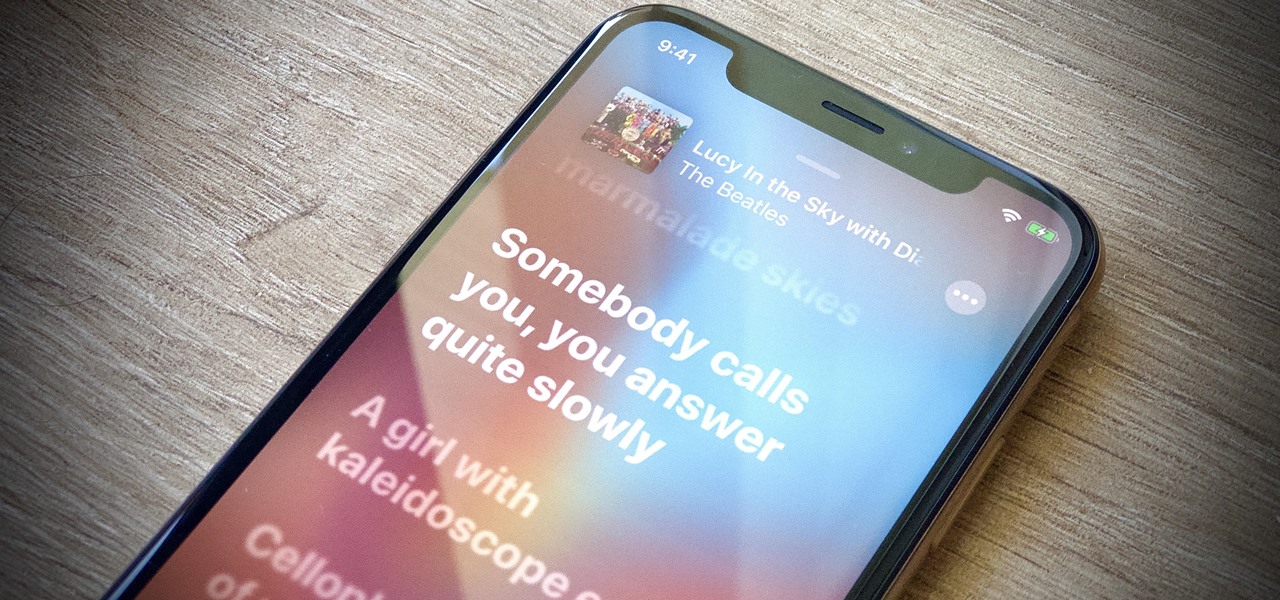
There are a lot of songs out there, so it's tough to remember all of the words to every song you like. If you're like me and have a less-than-perfect memory, visual aids will ensure your Apple Music jams aren't interrupted with incorrect or forgotten lyrics. That's why Apple's update with time-synced lyrics is so cool, essentially turning your iPhone into a portable karaoke machine.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

Because of quirks with cell radios and how Android was previously set up, custom ROM support for Galaxy S phones has been sparse these past few years. It's been almost nonexistent for US customers, while international users would see some ROMs. Thanks to Android Oreo's Project Treble, this will all be changing soon.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

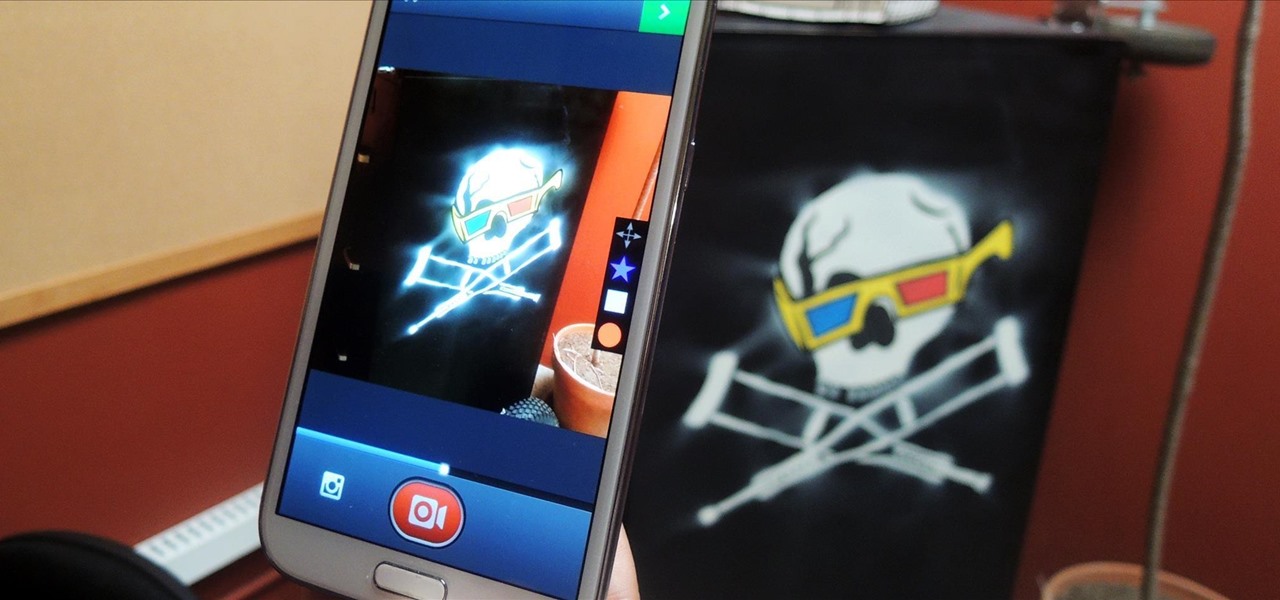
With the introduction of Vine and the subsequent Instagram update, abbreviated video sharing has come to the masses, to be experimented with in an unprecedented way.

Hand washing is something you learn from a young age, but how do you know you are doing it correctly? Keeping your hands clean is one of the best things you can do to keep others and yourself healthy. In this tutorial, Memorial Health will teach you the best way to wash your hands and prevent the spread of germs. There are two ways to clean germs from your hands: soap and water and alcohol-based handrubs. Watch this video to find out how to use both effectively. The video will show you how a ...

Breathing oxygen is an extremely important component of staying alive, right? Well, the same goes for running. If you're not breathing properly, you're running is going to suffer.

In this "super" video tutorial, you'll learn how to convert a Super Nintendo controller to PC controller. Now, dig deep into your garage and pull out those old SNES pads (or controllers) and get ready for some "super" modding!

The author of this video does a wonderful job of explaining to the viewer in easy to follow instructions how to accomplish the double crochet stitch. This video will explain the method in a way that will be easy to follow by beginners or those getting back in crocheting. The step by step instruction will aid the viewer in accomplishing this basic stitch method. The author demonstrates this method using a sampler scarf and shows you how to implement the double crochet stitch in other projects ...

RC Car Action Magazine Editor Matt Higgins shows you how to make painting your RC bodies easier and more effective. Paint can add a personalized touch to your RC vehicle, but there are tips to make the painting easier. Watch this video tutorial and learn how to effectively paint the body of an RC vehicle.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

For about a million Americans each year, a joint replacement brings relief from pain and restored mobility. But, 5–10% of those people have to endure another surgery within seven years, and most of those are due to an infection in their new joint. If doctors could treat infections more effectively, patients could avoid a second surgery, more pain, and another rehabilitation.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

Greetings my fellow hackers, In the previous article, I discussed briefly about ransomwares and their devastating capabilities. Devastating in a way that ransomwares are not only known to encrypt files but to also lockout some specific functions of the system and hold it up for a ransom.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.