Null Byte is looking for forum moderators! Welcome to the ninth Community Byte for coding in Python and completing the challenges presented to us by HackThisSite. These sessions are created to bring our community together, to learn from each other, and grow together. Everyone is welcome, from novice programmers to aspiring hackers.

When it comes to social engineering, Null Byte is here to show you how it's done. Social engineering is the key fundamental to unlocking tons of possibilities and opportunities in your everyday life. So, what is social engineering? Social engineering can be called many things. It's taking nothing and turning it into something. It's taking the bad and making it good. Above everything else, it's the art of manipulating the world and people around you—coercing that salesman into giving you a low...

With the computer's rapid increases in power and efficiency, computer virtualization has taken the scene by storm. With virtualization software, and powerful enough computer hardware, your computer can run a virtual computer within itself. This effectively gives you multiple OS's on the host OS. This can be used for a lot of cool stuff that your computer would normally be limited by. Let's take a look at a few.

Halloween is just a few days away, and since I've been churning out the creepy Bingo of the Days for everyone the past few weeks, it seems fitting to do a puzzle based on them.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

Gone are the days when you had to carry a clunky DynaTAC to make phone calls, pocket phone book for you contact list, Sony Discman for your tunes, and wallet for you cash and credit cards. Today, all you need is your smartphone. To be specific, Google's Nexus S 4G on Sprint.

This week has been pretty exciting for both Facebook and Google. Facebook announced a slew of features that seem on the surface to copy Google+. For Google+ users, a lot of improvements, updates and features were implemented, and they're seeing a lot more overall integration with their Google account.

Speech recognition software made it easy to search Google on your smartphone, and Google Goggles made it easy to find answers from camera snapshots on your device. But now Google's bringing similar technology straight to your desktop, and with faster results—faster than Google Instant.

Aside from food, oxygen, sunlight and water, there are other necessities that humans arguably need today to survive—clothing, love and shelter among them. Almost everyone wears clothes, needs somebody (or something) to love and a place to call home. And what's the one thing that connects all three? Something we all have? Keys.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.

Japanese people are into many things Americans find weird—like YouTube's beloved canine-hosted cooking show or Daito Manabe's light up LED grills or even more insane, a vending machine that distributes live crabs. In light of these cultural oddities, the Japanese phenomenon of visual novels (NVL, or bijuaru noberu), seems relatively normal. A meeting place of books and video games, visual novels are a sort of "Choose-Your-Own-Adventure" for the new generation.

Gathering Vocabulary the right way
Student group hopes to keep bikes on campus By Conrad wilton · Daily Trojan

Oscar the cat is one lucky feline. After losing his two hind legs in a combine harvester, his loving owners had Oscar outfitted with two prosthetic paws, or metallic pegs to be more specific. This revolutionary veterinary procedure is nothing to scoff at - biomedical engineering experts and a neuro-orthopedic surgeon were both called in to create the world's first bionic cat. Via BBC:

Are you tired of doing the same exercises for abs? The jackknife crunch may be the answer to your problems. This exercise effectively works the core muscles. It should be noted that whenever the knees move toward the chest (the jackknife motion), the hip flexors are involved. The hip flexor muscles are actually part of the upper leg. They allow you to kick a ball or lift the knee from a standing position (as in running). Thus, if you are trying to isolate the abs, there are better alternative...

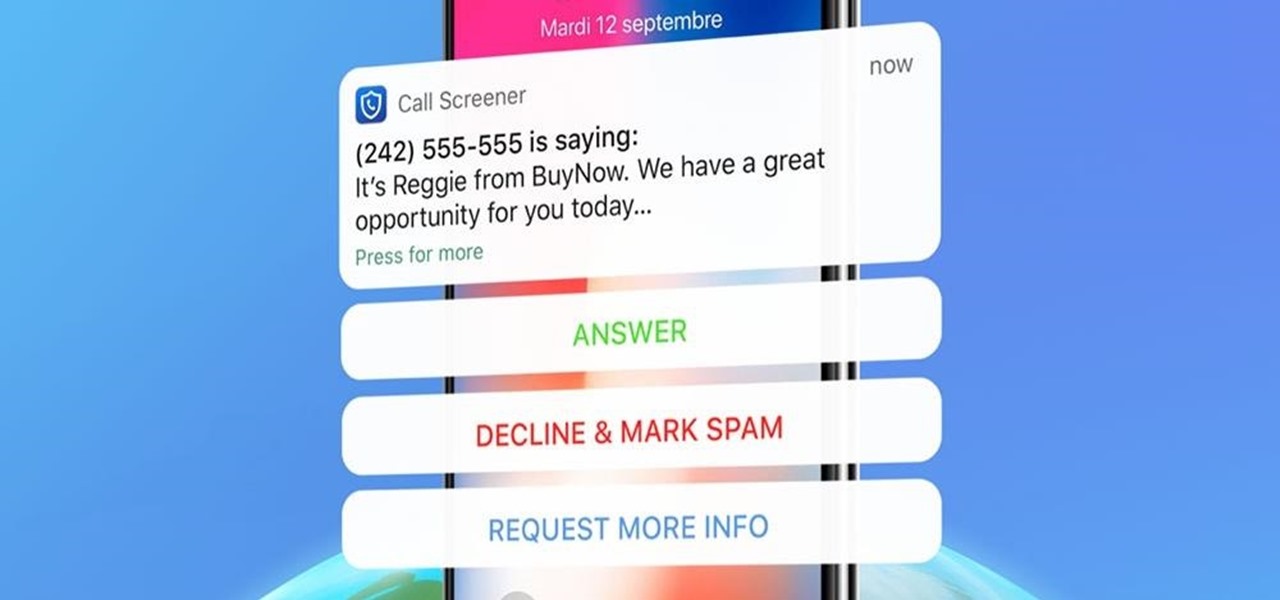
We all know the stress that a ringing phone causes these days. Should you pick up that unrecognizable number? More often than not, it's a bad decision. You hear the automated message and hang up. Or worse, a real human asks you about your day before trying to sell you something.

The second patent trial between Apple, Inc. and Samsung Electronics has effectively ended, with a jury ruling that Samsung did in fact infringe on two of Apple's patents. The reward of $119.6 billion is far lower than the $2.2 billion in damages that Apple seeked.

Apple's latest update, iOS 7.1, has flooded to iPhones and iPads across the world. Despite the buzz across the web covering most of its newest features, we found one nice little enhancement that has been overlooked.

Want to make your own soda or maybe just bring a dull one back to life? Homemade sodas don't always live up to the store bought ones because they can taste flat by comparison. This quick and easy method makes super fizzy drinks with only four ingredients. Because putting dry ice in a sealed bottle would effectively turn it into a bomb, you'll need to make a safety valve for the bottle.

Warfare strategies have become an inspiration to different marketing professionals, many of them drawing influence from Sun Tzu’s Art of War. This ancient Chinese text provided treaties on how to effectively manage resources, tactical positioning, and timing attacks. It also states that “..if you know your enemies and know yourself, you can win a hundred battles without a single loss”, a basic concept in which you have to always watch your competitor to anticipate his next move.

An effective warm up is essential for climbing: you will climb better and are less likely to sustain an injury. With no warm up, performance is compromised, fatigue comes quickly, and injuries are more likely. All together: Not Good!

You're currently playing a heated game of Scrabble or Words with Friends. The game is close, too close for comfort. But you're not sweating because you're confident. You play a huge word that puts you in the lead, but then when your letter tiles are drawn...

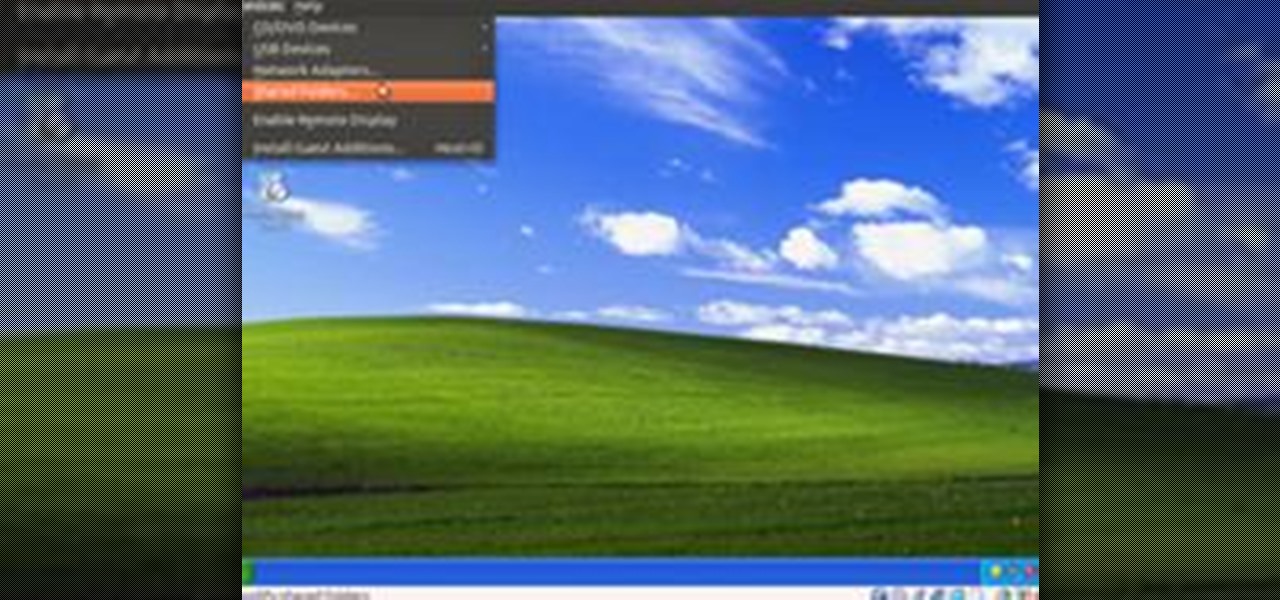
There are several virtual machine managers present in the market. However, the main functionality of all VMs are the same. Most people like to get free VM managers, so that they can install as many operating systems as they like over the host operating systems. One of these free VM managers is Oracle's VM VirtualBox, which can be downloaded from Oracle's website for all popular operating systems, such as Linux, Windows and Mac.

Want to learn how to walk on stilts? This video will give you the basics on how to practice safely and effectively. Do the basics when walking on stilts.

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

It's sad to say, but I will no longer be writing up anymore Scrabble Challenges. Frankly, I just don't have the time to make them now. And though they are incredibly fun and "challenging" to conjure up, I'm not sure that people are finding them as useful as I had hoped. But really, it all comes down to time. So, unless I have a future craving for puzzle-making, last week's Scrabble Challenge #20 was the last one.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. There are many ways to get around in Minecraft, from boats to mine carts, but did you know that you can travel even faster on foot? That's right, by creating a running track, players can run at super speeds! Not only is it the single fastest way to travel, it's easy to build as well. No redstone wires required.

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

Permanently deleting files is something that a lot of people aren't aware of. Actually, most people think that once a file is deleted, it is gone forever. This is not the case. Hard drives write to the disk via magnetic charges, positive and negative correlate to 1s and 0s for binary. This is then interpreted into information for the computer to use and access.

Welcome to Minecraft World! Check out our advanced tutorials and come play on our free server. You may know that Minecraft is an excellent creative tool, but perhaps less well known are the fascinating array of redstone powered games that have been made by players like you.
Oh, yeah. I was a skeptic, too. A few things are worth noting, though. 1) This stuff is cheap. You can get started on a project for very little money. Even advanced fabrication tools are reasonably priced.

Got a knack for speeding? Like running red lights? Believe or not, the police have better things to be doing than pulling you over, like catching real criminals. That's why more and more cameras are popping up at known speeding zones and on street corners—so the cops can clean up the streets, compared to just ticketing them.

Shoot-em-up games, or shmups, consist of lone or small groups of players shooting at and being shot at by hordes of colorful enemies. The genre is thought to have peaked in the mid-'90s, but recent games in the indie world may be saying otherwise. Geometry Wars and other twin-stick games kicked off the trend, but newbies Trouble Witches NEO, Outland and just-released Gatling Gears have brought some much needed originality into the modern shmup scene—making it something worth exploring again. ...
Beware the Canning Mission! The Zynga Community Forum is full of complaints about the new Canning Mission. Here is an outline:

Any time a feature is introduced in an MTG set and not replicated in subsequent sets, balancing issues are surely forthcoming. You wind up with one set that can do things the others can't, forcing players to counter that set with other cards from it, and generally limiting the creativity with which one can effectively play the game. Playing these types of cards is like playing trap defense in hockey or boxing like Floyd Mayweather: you might win, but neither you, your opponents, nor the peopl...

One of the most important marketing tools we should always be developing to help reinforce our brand is our references. Just like many companies use their client list and client references to build credibility and confidence for their products and services, we should also leverage our references to build credibility and confidence in our capabilities and brand. Sometimes reference checks are just a formality, but in most cases potential employers (i.e., potential clients) use reference checks...

The importance of the brow has not been forgotten as much as it has been overlooked. A natural tool of communication, the brows can convey surprise, disdain, and sorrow with a lift, a furrow, or an expressive softness. The masters of makeup, like Max Factor and Ben Nye, knew the importance of perfectly styled brows, and how that would affect the work of the actors with whom they worked.

We haven't seen an emoji update for iPhone since iOS 15.4, which gave us 112 new emoji characters, but that's finally changed with the release of iOS 16.4. Here are all the new emoji you get after installing the latest software update.