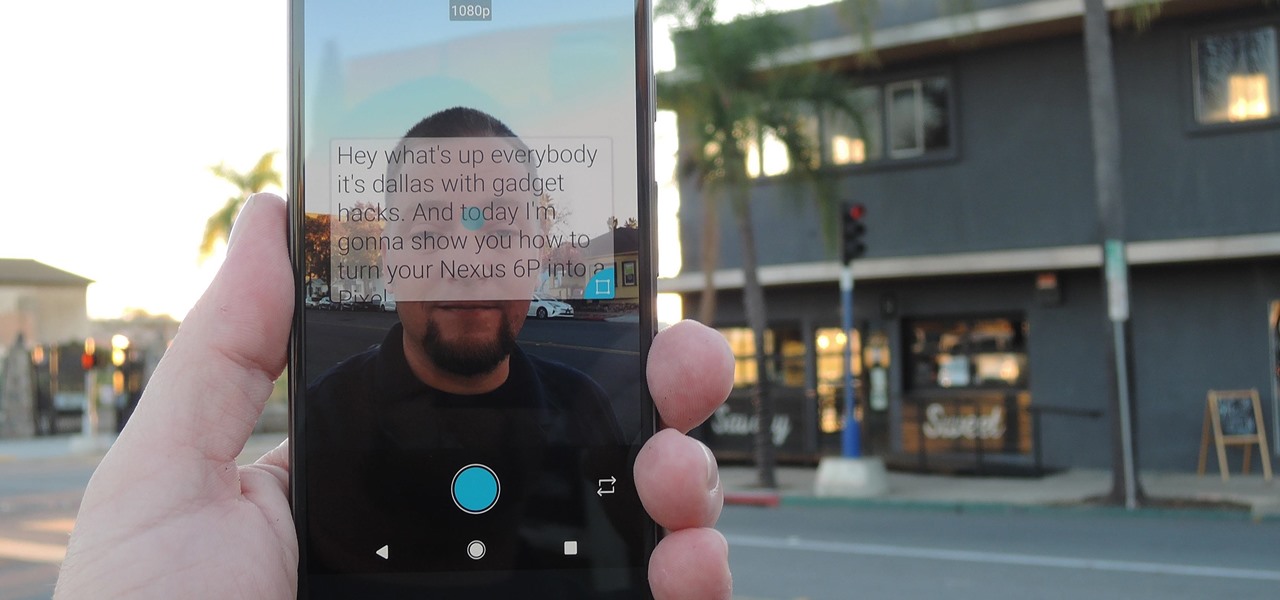
With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.
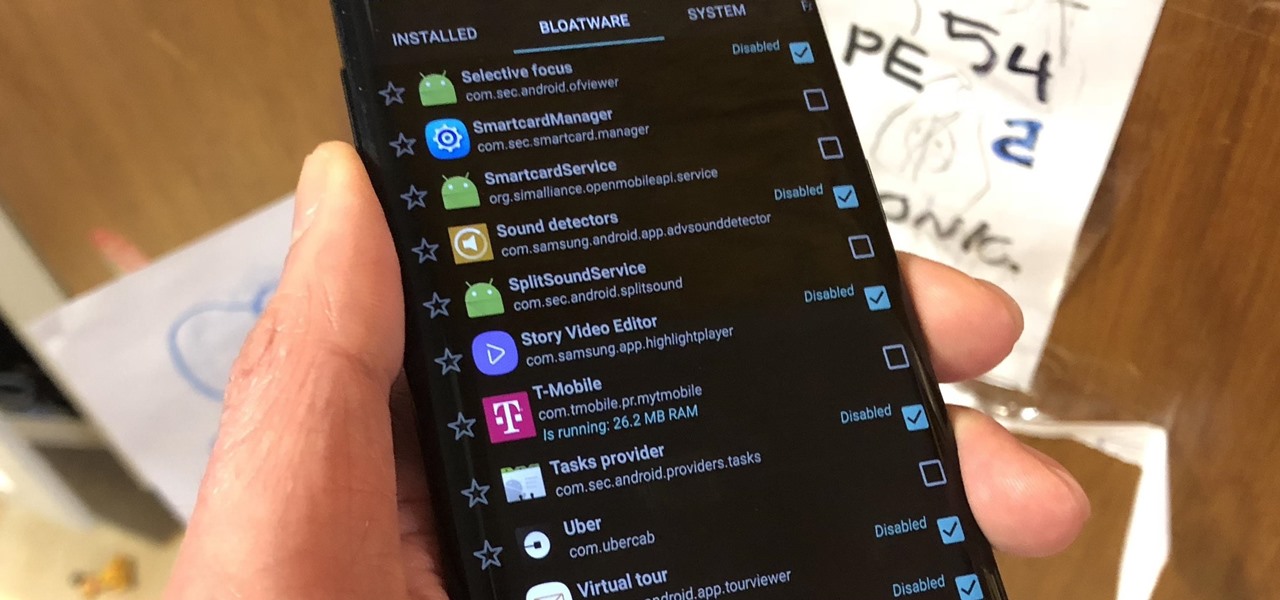
Carrier-branded Galaxy S9 models come with a ton of bloatware that you usually can't get rid of without rooting. With a little digital elbow grease, however, there is a way to disable bloatware on your S9 or S9+, and it's a lot safer that attempting to root and modify you precious device.

Whether you're a veteran augmented reality developer looking for a quick access point to add a new platform to your arsenal or just getting started with your first AR head-mounted display, get ready to start developing for the Meta 2.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

Welcome back everyone! It's been awhile hasn't it? Sorry for being so quiet, but my CCNA courses have really picked up recently. In the last article we covered how to import modules and how we can use them. In this article, we'll actually be covering a module that is essential to the hacking aspect of Python, sockets.

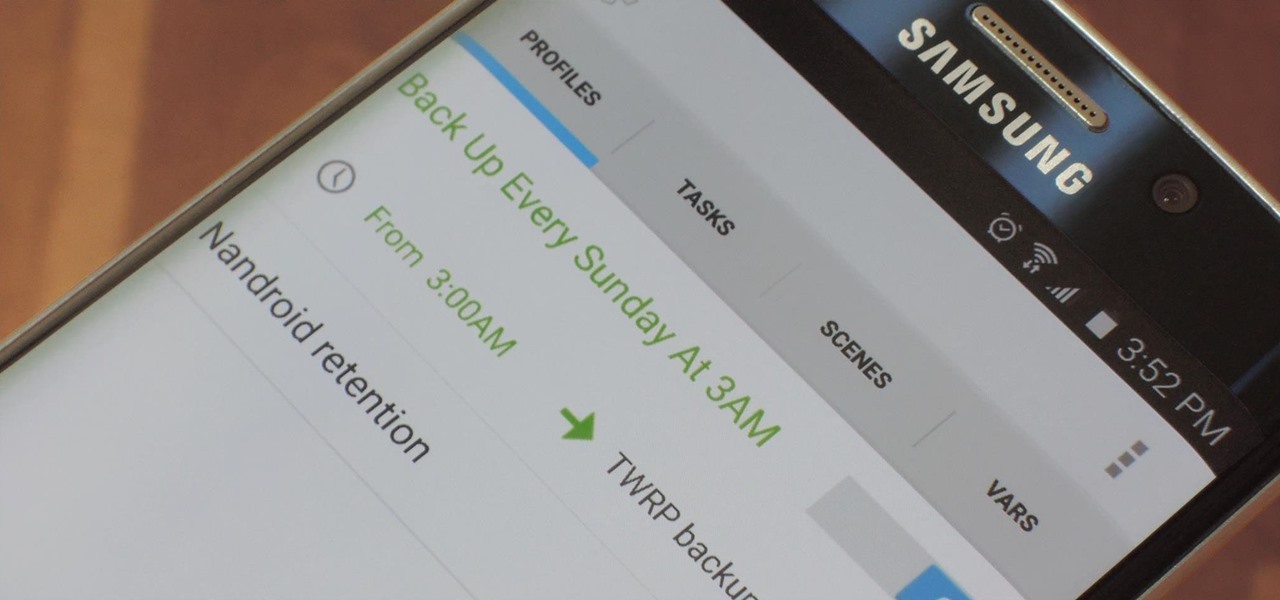
NANDroid backups are one of the best reasons to root your Android device and install a custom recovery. They're essentially a snapshot of your phone's entire operating system and all installed apps, so if you ever screw something up when installing a flashable ZIP or custom ROM, you can restore your NANDroid backup to get everything back to normal.

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

No matter how careful or decent you are, there will always be pictures or videos that you want to keep private. They say a picture is worth a thousand words, but if someone were to go through my photo gallery, only one word would be coming out of my mouth—"%@&#!!"

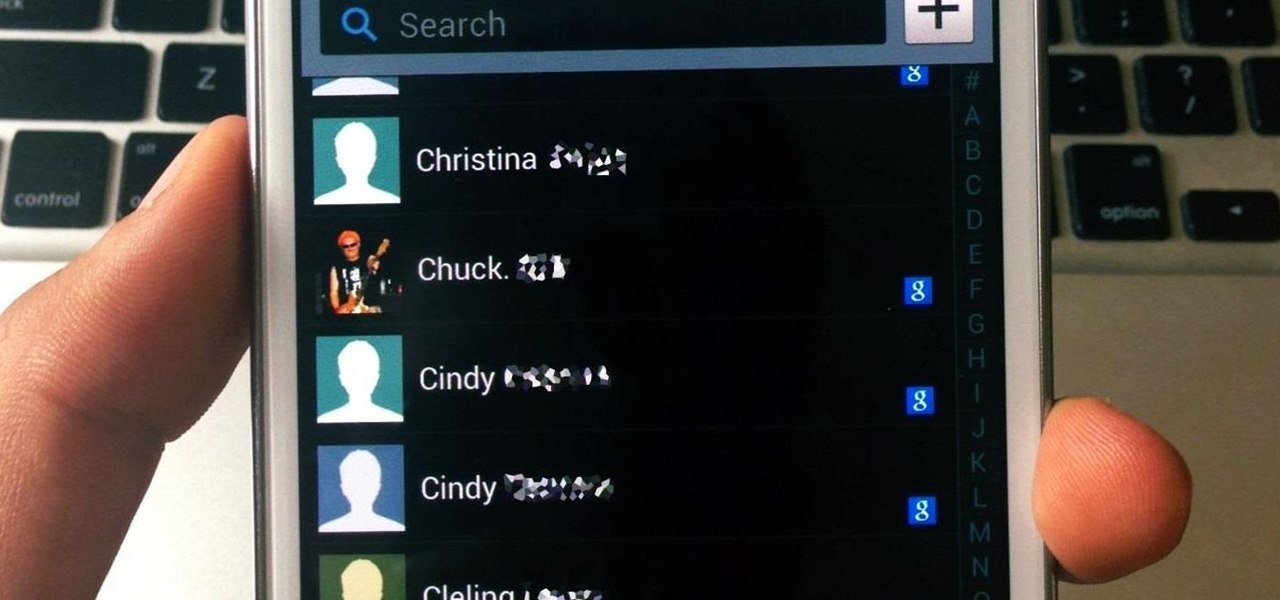
Why is transferring contacts from an old smartphone to a new one still insanely difficult? I can check my bank account, upload a picture to Instagram, email someone across the globe, and check the weather forecast on my phone—all in under five minutes.

Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

In photography, creating a double or multiple exposure photo involves combining two different images to make one single image. This technique has been used in film photography by exposing a piece of film twice to two different images. The second image becomes superimposed onto the first image, creating various effects that may mirror one another or seem ghostly.

If you've used PowerPoint in the past, you're probably used to version available on Windows, but you can do even more in PowerPoint 2008 for Mac. There are tons of new features that slideshow builders will love, but sometimes you can never know about them unless someone tells you about them. The Microsoft Office for Mac team shows you all the great features in this how-to video.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.

On Thursday, Snapchat opened up its walled garden of World Lenses to the masses of creators with the launch of Lens Studio.

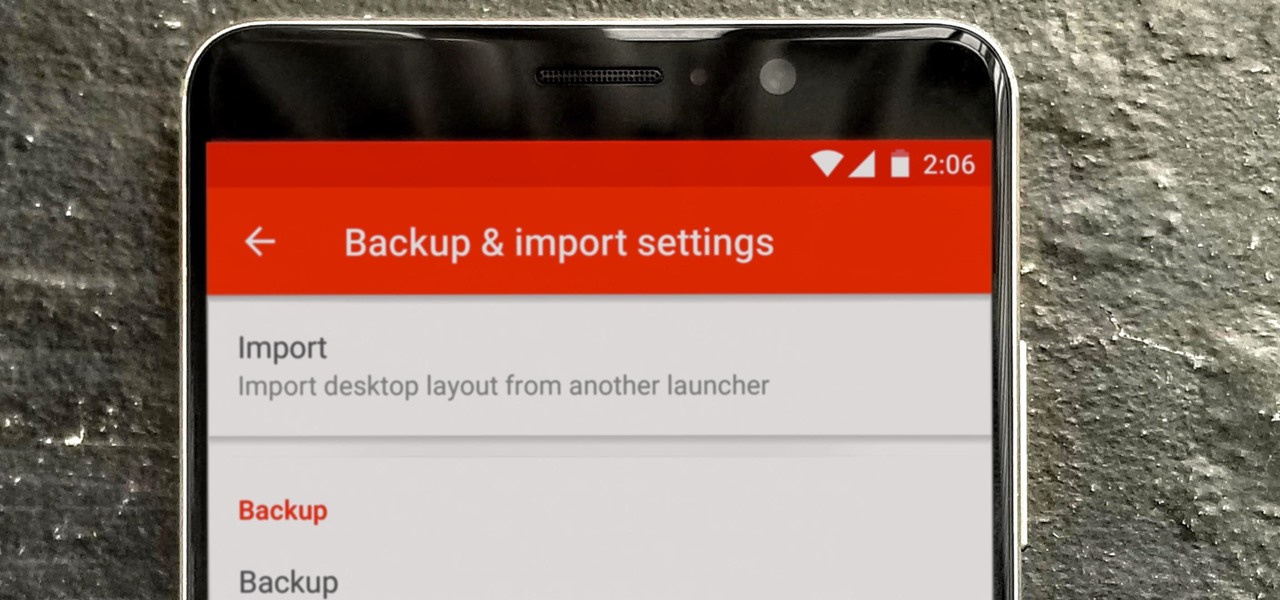
So you spent all day customizing your phone. You tinkered with all the settings, searched the web high and low for the perfect wallpaper, and found an ideal icon pack to complement the color scheme. You go to sleep, proud of the work you accomplished when the unspeakable happens — your phone freezes and tech support is telling you to do a factory reset to fix the problem.

Thanks to live-streaming video and social media apps like Facebook, Instagram, and Snapchat, we're all on camera nowadays. Unfortunately, though, we don't have a script to work with when we're shooting selfie videos, so it's hard to come off as perfectly eloquent when you're just freestyling off the top of your head.

After a few months, I get so fed up with hearing the same ringtone go off alongside each new notification that I'm forced to switch things up—only to end up repeating this whole process when the new one gets played out. And I'm sure people around me are equally sick of listening to that tired old tone towards the end as well. I mean, a decade later, I'm convinced that Nokia tone is permanently implanted in my brain.

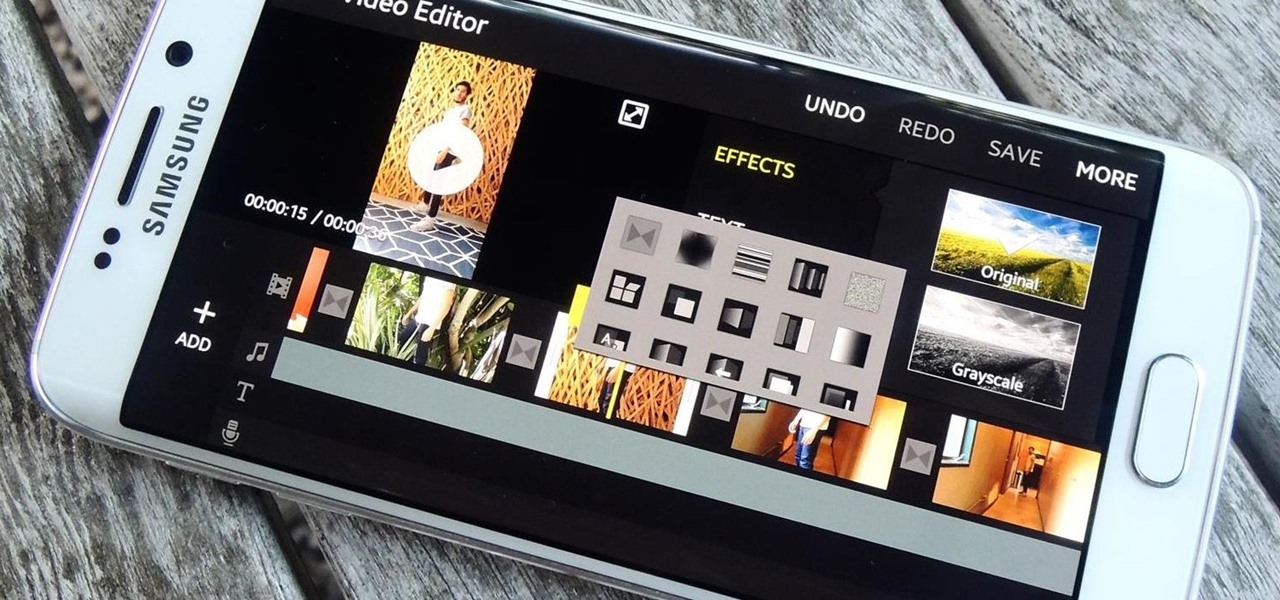
Editing a video by trimming or adding audio is fairly simple on Galaxy devices, but if you want to include other clips or transition animations and really get those creative juices flowing, you might find the standard editing tools limited—unless you know how to unlock Samsung's hidden video editor.

Welcome back, my greenhorn hackers! Digital forensics and hacking are complementary disciplines. The better you are at digital forensics, the better hacker you are, and the better hacker you are, the better you are digital forensics. Unfortunately, few people in either profession cross these discipline lines.

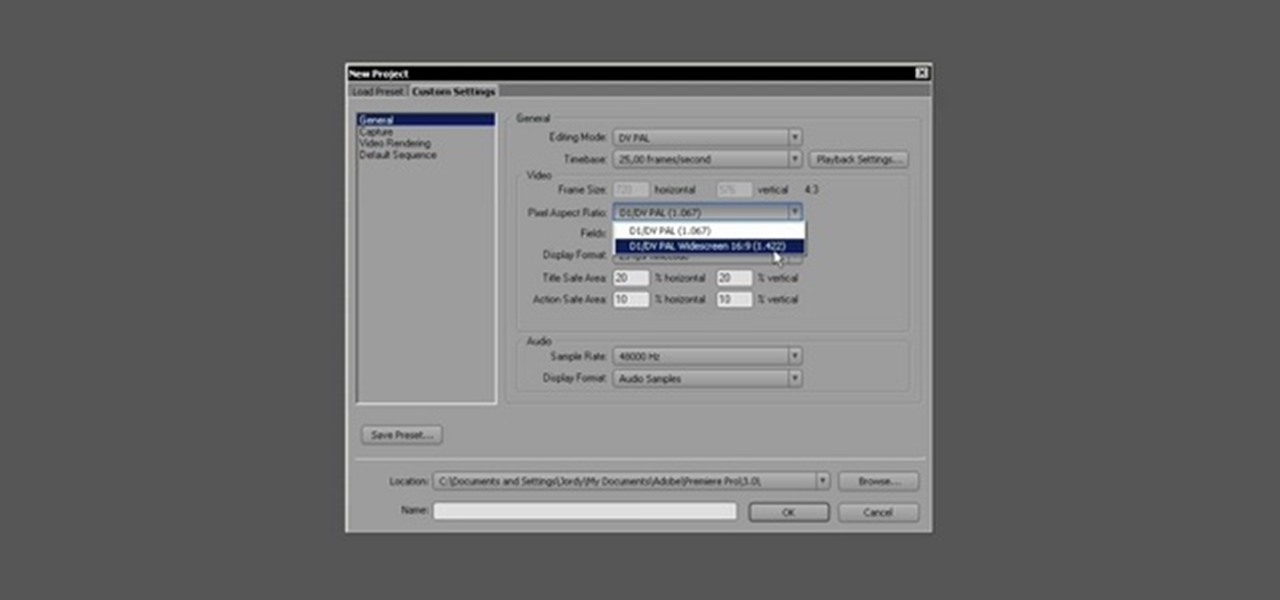
For a new user, Adobe Premier Pro can be overwhelming. There's just so much you can do! So, a little guidance, or shall we say "basic training," is what you'll need to get started editing your own home video or professional film. This five-part series is your basic training, taught by Jordy Vandeput, showing you the basic, need-to-know stuff in Premiere Pro CS3.

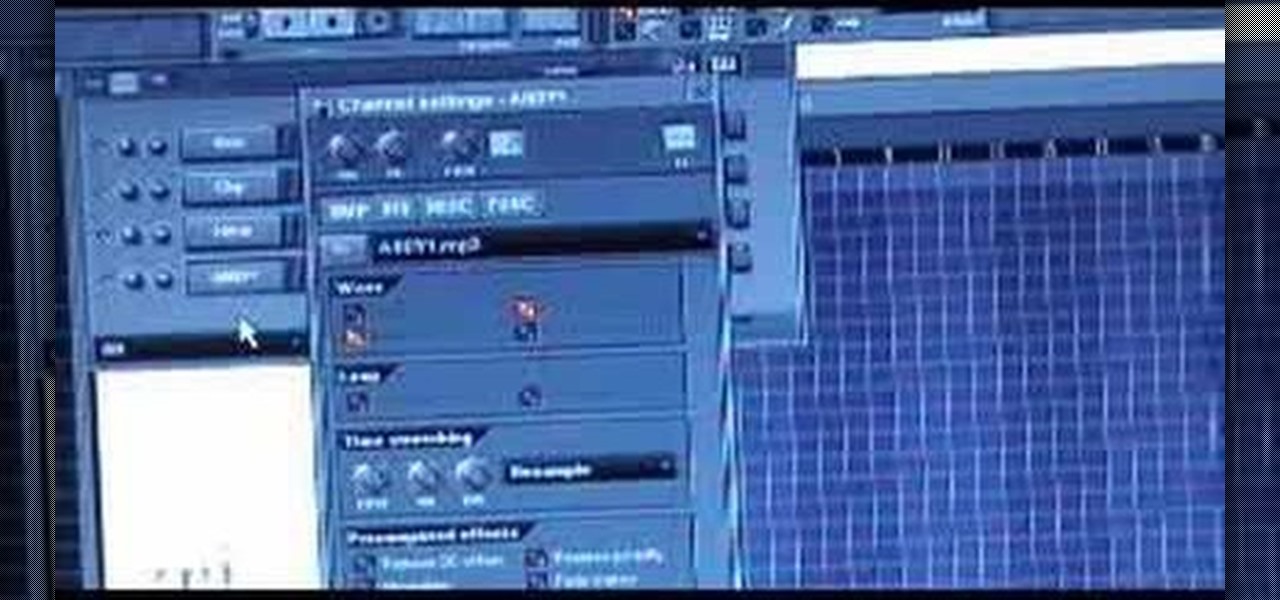
This is a quick and effective tutorial shows you how to import any kind of music file into FL Studio. Watch and learn how to import a sample into Fruity Loops.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

This video tutorial will walk you, step by step, through the process of importing data directly from an Excel document to a MySQL database server using the smart copy feature available in the DreamCoder for MySQL. For more information, press play!

If you've ever missed an important phone call because you're hands were too dirty to touch the screen, you won't have to worry much longer about it happening again. Apple is remedying this age-old problem on the iPhone with a hidden feature in iOS 11 that ensures you'll never miss another call again.

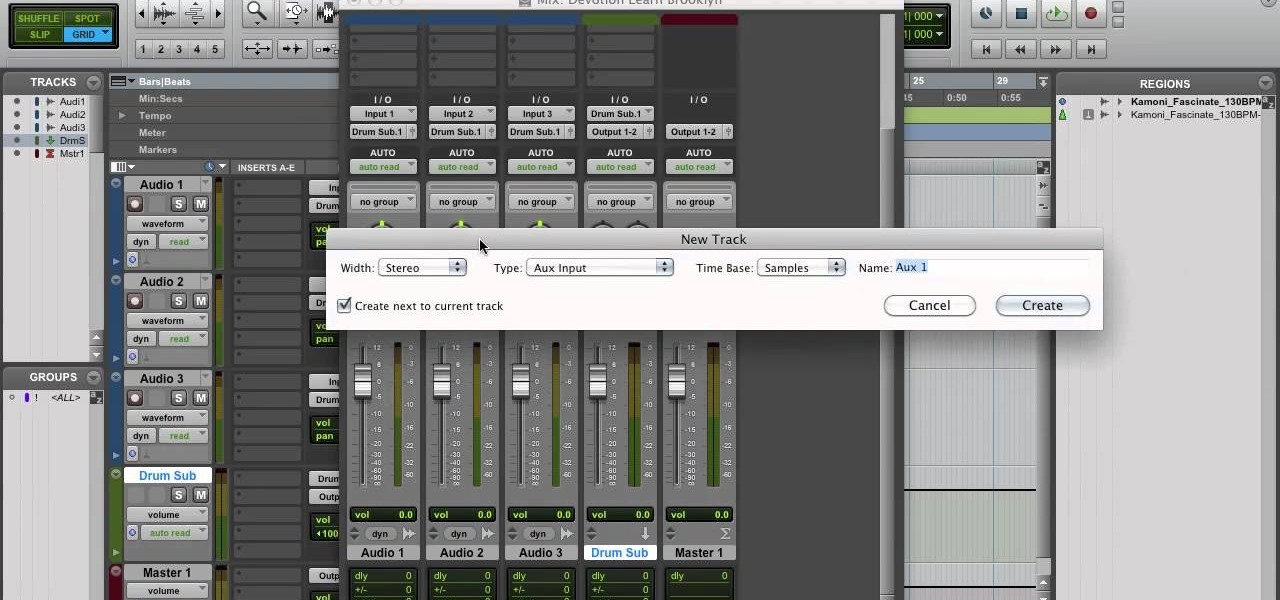
Move over Pro Tools LE— Pro Tools 9 is here! One of the most exciting things about Pro Tools 9 is that there's more tracks without having to have a Toolkit. Another great thing is being able to run Pro Tools without having to use Digidesign, M-Audio or any Avid hardware. Also, there's Delay Compensation Engine on a native system that doesn't require HD hardware or HD native. And this is just the beginning. To see more of the features in Pro Tools 9, watch this overview video.

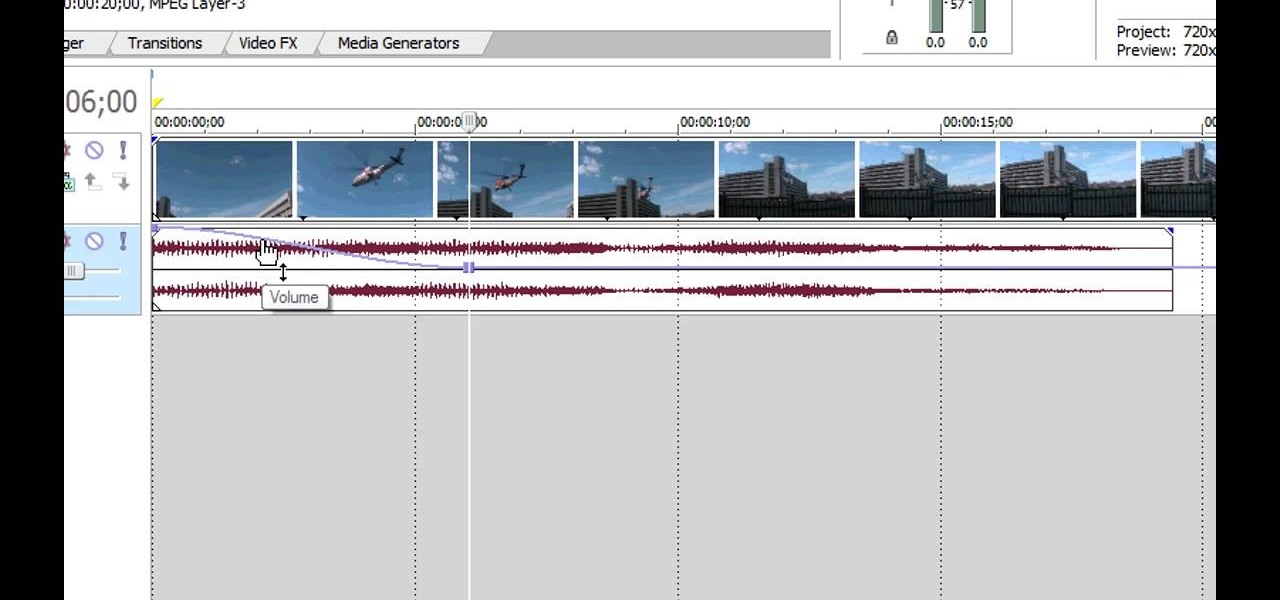
You can replace the audio in Sony Vegas. To do this first delete the audio which you want to remove by selecting it on the right side and press delete. Now go to the website like findsound.com and download the sound and then import it to the Sony Vegas and drag it to the layers. If your sound file has some blank space you can delete it by just selecting it and press delete. Now drag the audio to the begining of the video. Now you can play the video and hear the sound is better than before. No...

This is a tutorial for controlling the Pine tip moth. Identifying and controlling the pine tip moth consists of studying the small plants of pine. The attacks on pine trees is caused by Nantucket pine tree moth found along the Rio Grande Valley as far north as Espanola, it has spread to South Arizona and California by importing grafts from Mexico. The moths are 3/8 inch long reddish brown to grey in color. They attack the main stem of the baby plant and the pines instead of growing vertical g...

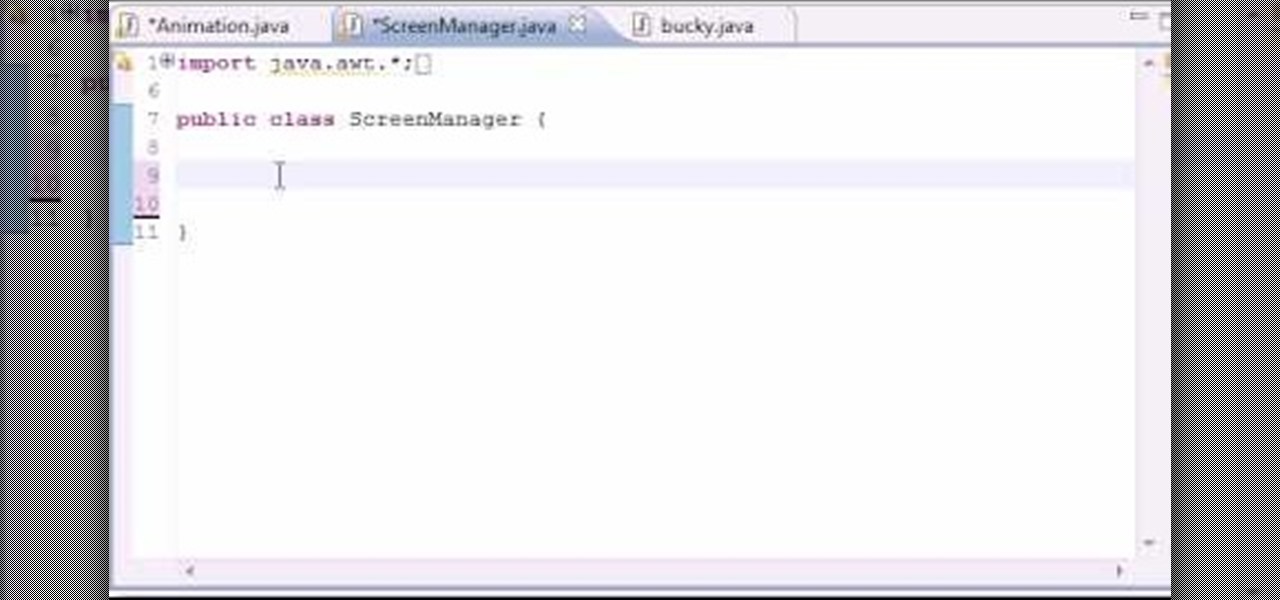
In this 14th video in a series about JAVA game development, "thenewboston" (Bucky Roberts) explains how to redefine your screen to avoid annoying flickering. Flickering in JAVA games often occurs because of time lags as the viewer watches the computer draw a new screen, pixel by pixel. Pre-installed code in JAVA can be used to eliminate this problem by taking advantage of "Buffering" and "Page Flipping". These functions permit you to delay the composition of a new screen until it is finished,...

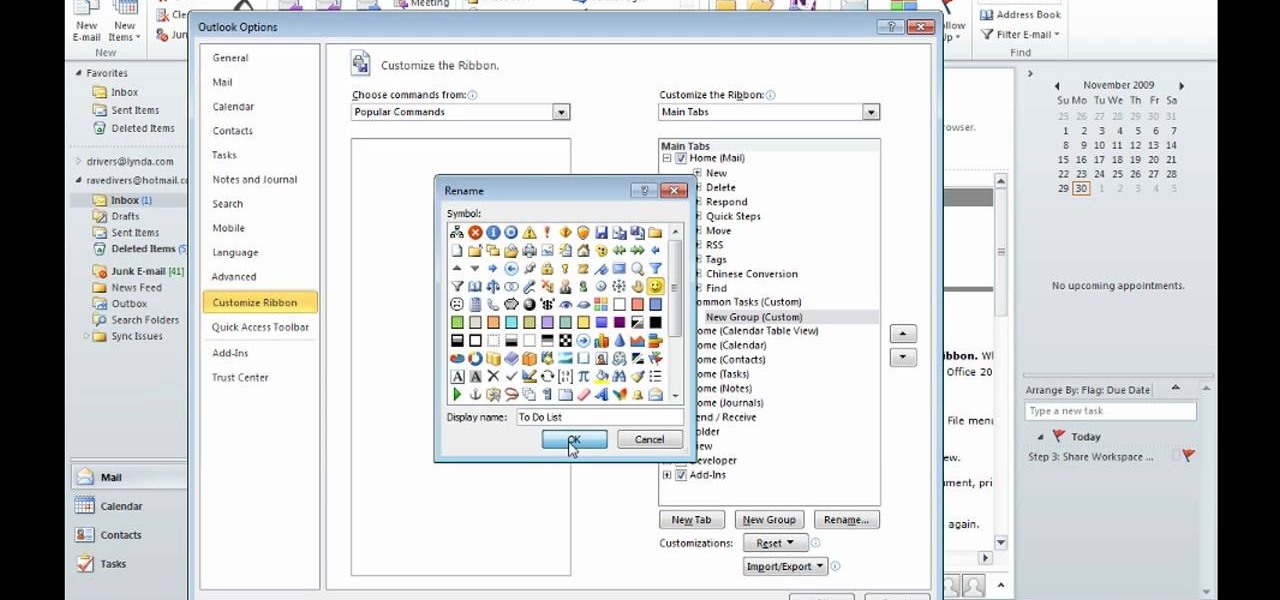
After you launch Outlook 2010 in your computer, you will see the Ribbon strip immediately in the main window. The button for writing a new e-mail is separated from a button for creating new items in the calendar, contact list or task manager. An independent Quick Steps section offers functions allowing you to move a message into different folders, to save it into a calendar as a meeting reminder, to quickly forward it to a chosen person or to more people and to forward it with a FYI note. If ...

First you need to do is press the t button in your keyboard and add a new mono track. Choose mono in format and click OK.

In order to make Custom titles in IMovie '09, you will need the following: Seashore or any other compatible program.

The video demonstrates how to add animated images and video content to your Microsoft PowerPoint presentation.

This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

Tasktutorial teaches you how to create a sound on/off button using Flash. Name the first layer Actionscript. Go to frame 1, then window - actions. Add stop(); Go to frame 2, then window - actions. Add stopallsounds(); Create a new layer and select the text tool. Write off on. Change the color to black. Select the text and hit CTRL + B to break apart the letters. Select off, hit F8 and select convert to button. Name it off. Do the same for on, but name it on. Double click to open the off butto...

This video is about sliding an object from left to right in Flash. We will be creating a simple, core animation in Flash. First, let's import an image to our scene. Place it here. Now, let's convert our image into a movie clip. Change the frames per second value. Now, go to the frame and enter the key frame. Bring the image here. Let's rotate our image a little bit using the free transform tool. That will give more dynamic animation. Go to frame 30 and hit F6. Now, we need to add motion. Chan...

This six-part video tutorial, goes over how to make beats in Adobe Director. The six different videos go over the following:

There are varied approaches to using SketchUp with CAD files. This video series presents one method we suggest as it is quick and creates a good clean SketchUp model.