
How To: Use the iMovie video library
This tutorial explains what the video library is and how to access and use it. You'll need to know this if you want to work with all your imported video footage and movies.


This tutorial explains what the video library is and how to access and use it. You'll need to know this if you want to work with all your imported video footage and movies.

Botanically, tomatoes are fruits, but an 1893 Supreme Court decision changes that. They were ruled to be considered vegetables, allowing for a higher tax to be placed on imported tomatoes. Seems silly now. Tomatoes are rich in vitamins A, C, and K, as well as lycopene, a cancer-fighter. Enjoy tomatoes throughout the year by canning your summer harvest.
Shaun will teach us how to create a 3D video game compatible with MAC or PC with no prior programming knowledge. First download Alice, a 3D World program that can be turned into a video game. Open Alice, click on "add objects", click on "more controls" and select your choice of aspect ratio such wide screen. Now you can import your own 3D models that Shaun will show you at the end of the tutorial or choose from a wide selection that comes with Alice. In addition, if you click on "home," "web ...

Learn about drag & car racing with expert tips and advice on imports and different motors and engines in this free car-racing video series on NHRA and IHRA racing events.
If you're a frequent Null Byte reader, chances are you're already up to speed with at least one or two programming languages or development platforms. But in a world that's becoming increasingly reliant on high-powered apps and responsive websites, knowing the fundamentals of just a few go-to programming languages isn't going to cut it if you want to be competitive and successful.
It's no secret that learning how to code is one of the best things you can do if you want to land a high-paying career in a world that's heavily reliant on web and app development.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

For anyone using open source information to conduct an investigation, a balance between powerful tools and privacy controls are a must. Buscador is a virtual machine packed full of useful OSINT tools and streamlined for online research. This program can easily be set up in VirtualBox, and once that's done, we'll walk you through some of the most useful tools included in it.

Have you noticed the many utility ARKit apps on the App Store that allow you to measure the sizes of horizontal planes in the world? Guess what? After this tutorial, you'll be able to do this yourself!

Once a hacker has created a PowerShell payload to evade antivirus software and set up msfconsole on their attack system, they can then move onto disguising their executable to make it appear as a regular text file. This is how they will get a Windows 10 users to actually open the payload without knowing they are doing so.
If you've contemplated what's possible with augmented reality on mobile devices, and your interest has been piqued enough to start building your own Android-based AR app, then this is a great place to to acquire the basic beginner skills to complete it. Once we get everything installed, we'll create a simple project that allows us to detect surfaces and place custom objects on those surfaces.
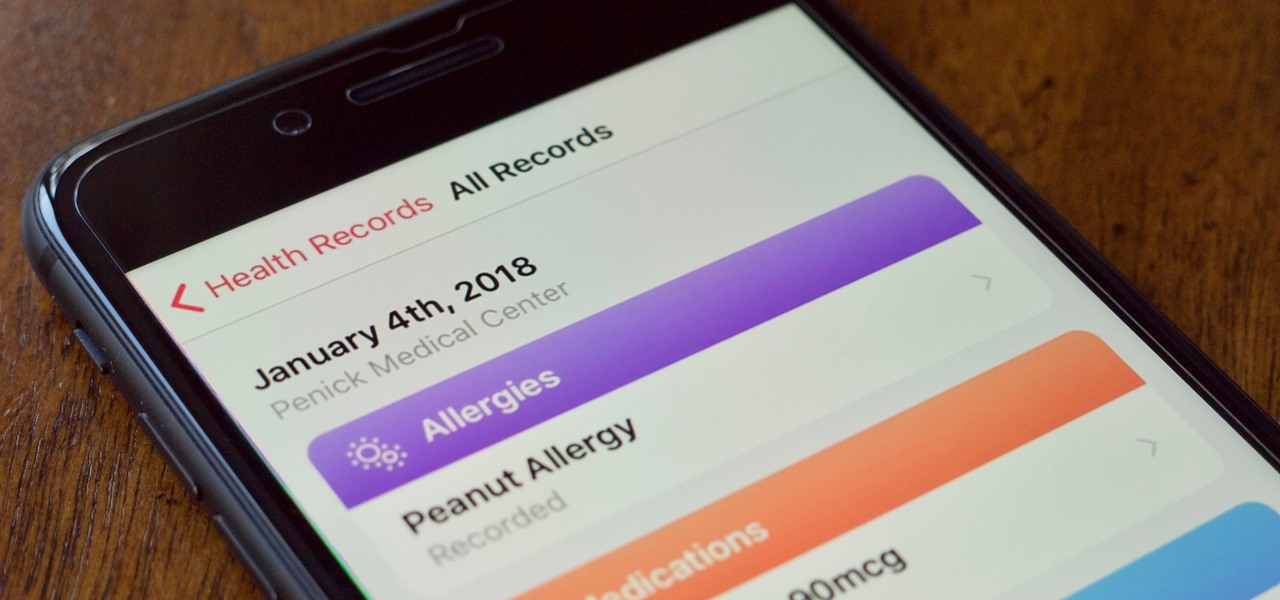
Mobile phones are not only essential for work and communication, they're quickly becoming an integral asset to our health. Your iPhone can store valuable data about fitness, nutrition, heart health, and so much more. And since iOS 11.3, your iPhone can even import a list of allergies, medications, immunizations, hospital visits, and other health information from your doctor or hospital.

Hacking from a host machine without any form of proxying is reckless for a hacker, and in a penetration test, could lead to an important IP address becoming quickly blacklisted by the target. By routing all traffic over Tor and reducing the threat of malicious entrance and exit nodes with a VPN, we can configure Kali to become thoroughly private and anonymous.

In 2013, Offensive Security released Kali Linux, a rebuild of BackTrack Linux derived from Debian. Since then, Kali has gone on to become somewhat of a standard for penetration testing. It comes preconfigured with a collection of tools accessible by a menu system, tied together with the Gnome desktop environment. However, Kali Linux isn't the only penetration-testing distribution available.
Are you interested in video editing, but have no background in it? Are you looking to put together a short from some clips you've shot, but don't know where to start? You could use iMovie, an application that comes free with every iPhone, but then what would you do on Android? There must be a universal solution that works across both iOS and Android to let you work however and wherever you like.

If you use the Google Assistant on your Android device, you can easily send a text message to any one of your contacts. But even though that same Assistant is powering the Google Home, you can't use the smart speaker to accomplish the same task — at least, not without some tinkering.
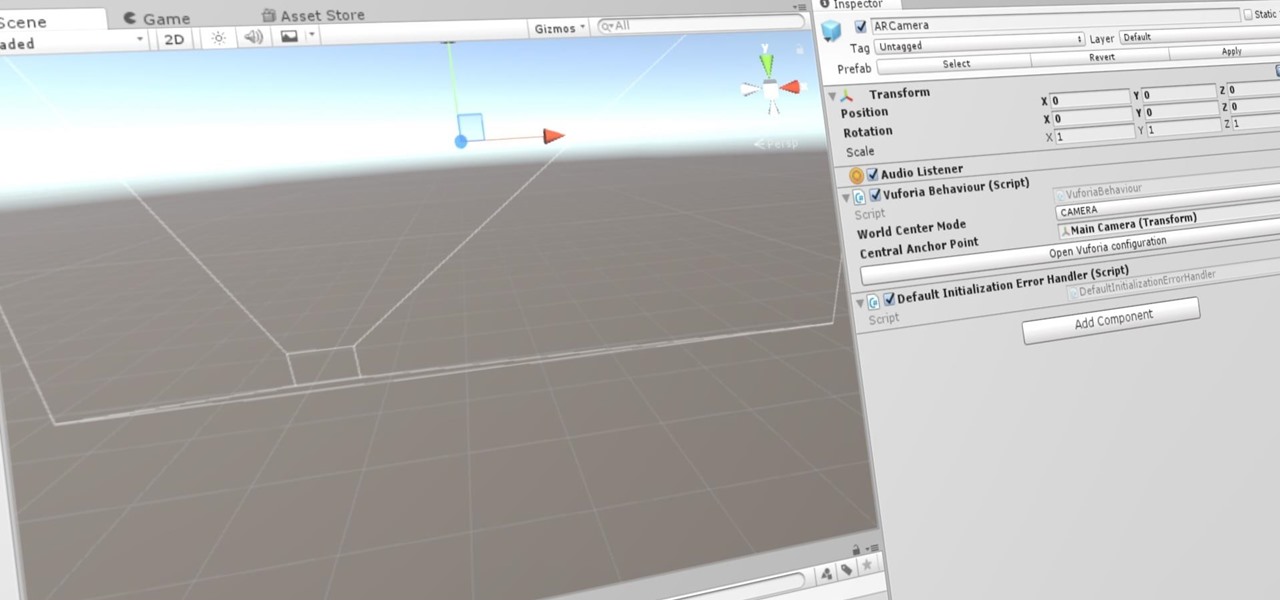
Now that we've set up Vuforia in Unity, we can work on the more exciting aspects of making physical objects come to life on the HoloLens. In this guide, we will choose an image (something that you physically have in your home), build our ImageTarget database, and then set up our Unity camera to be able to recognize the chosen image so that it can overlay the 3D holographic effect on top of it.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

There are quite a few flaws with Apple's mobile products, and one that drives me crazy is their reliance upon iTunes for all your music syncing needs. If you want a song on your iPhone, you pretty much have to use iTunes to get it on there. Either that or buy it directly from the iTunes app on your device.

If you are new to matchmoving, this video is for you. Learn the basics of matchmoving with Boujou 4 and compositing in 3ds Max 7 from this video.

Learn how to draw an old-world style tattered scroll that's all beat up. It's all drawn from scratch in Photoshop with a wacom tablet and then the final drawing is imported into Adobe Illustrator for Live Tracing. The finished product is a nice piece of vector art. In fact, there will be a new Tattered Scrolls set in Go Media's new Vector Pack 12 to be released later this month and this piece will be in it.

Want to play import games on your Playstation 2 console? Take a look at this instructional video and learn how to install the flip top cover case onto your PS2 console, an essential mod component that'll allow you to play those games that were never released in the US.

Sean Astin hosts AFI's filmmaking tutorial series, LIGHTS, CAMERA, EDUCATION! In this segment, we explore the importance of organizing for the editing process and how to import your footage to a computer.
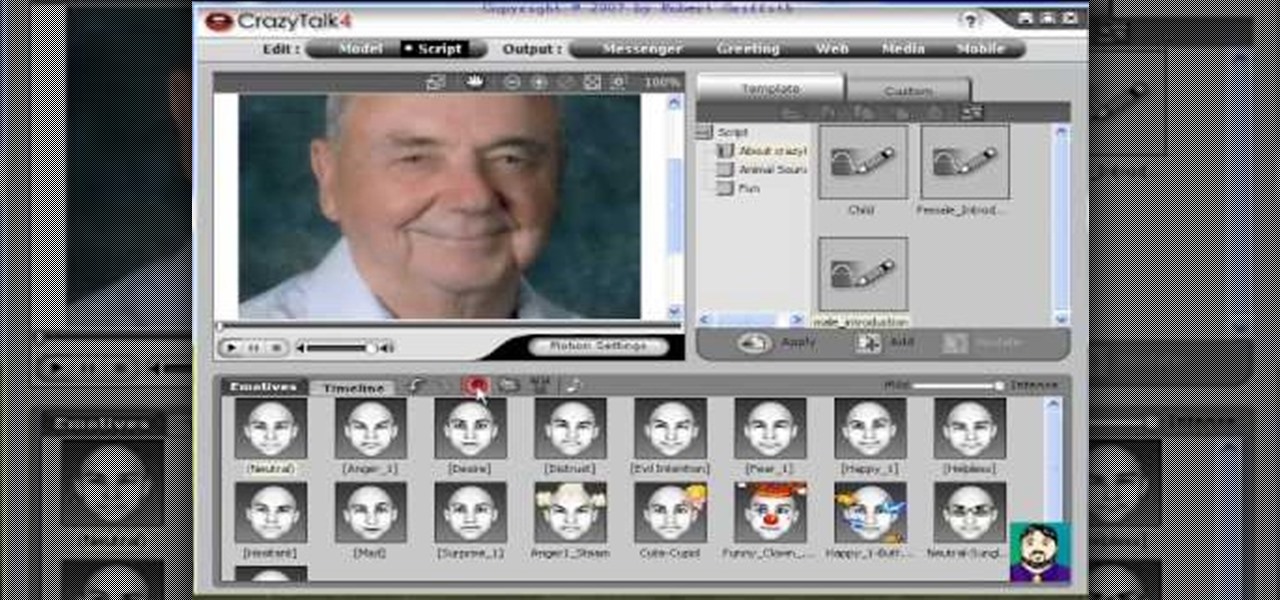
This unusual program (Crazy Talk 4) allows you to import a photograph and quickly have it talking to you.
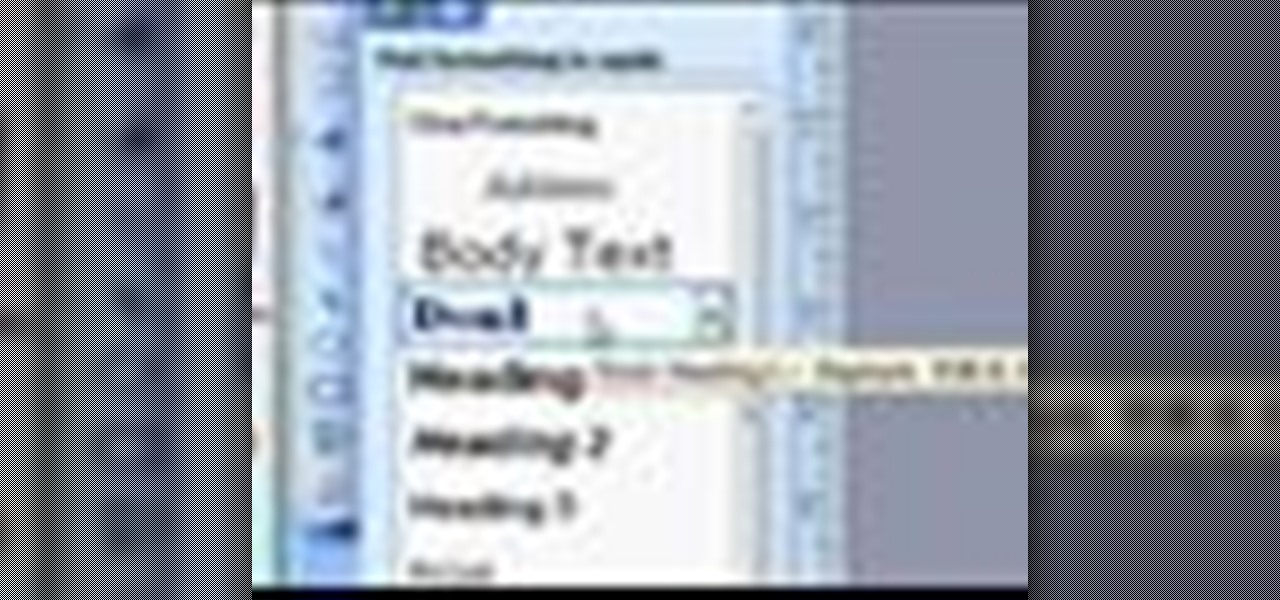
Strapped for time? Learn how to quickly format a Microsoft Publisher document so it looks like your other word processing files.

While Snapchat had a head start in making augmented camera effects popular on smartphones, Facebook has spent the past few years in hot pursuit, with no less than three apps offering mobile AR experiences, plus its Portal hardware lineup of smart home devices.

As one of the household brands in creative software, Adobe is now ready to lay its claim to the artistic side of augmented reality.
Your Pixel has a few hidden features you probably don't know about, like the ability to clean up your funky contacts list. Since I'm sure you haven't manually organized your contacts since the inception of Android, there are likely some incomplete and duplicate contacts. Thankfully, your phone can fix this automatically.

The landscape of augmented reality marketing is growing by leaps and bounds nearly every month, with Hollywood and the cosmetics industry leading the way.

Unlike some of the popular app lockers out there, a nifty app fittingly named App Hider completely erases apps, files, and their associated footprints from your smartphone. Think of App Hider as a micro-OS within your smartphone's system. This miniature ecosystem can operate copied apps independently, thus giving it an unprecedented layer of privacy and freedom within your handset.

Thanks to a new update to Amazon Sumerian, developers will now be able to not only create more realistic 3D content, but also build AR experiences more easily.

Much of the excitement around the HoloLens 2 has moved on to many wondering when we'll finally be able to get our hands on what is now the best augmented reality device on the market.

Among all the new Magic Leap app announcements made at the recent L.E.A.P. conference, an update to one of the company's major in-house apps went mostly unnoticed: Create 1.1.
At its F8 developers conference on Tuesday, Facebook announced new tools and features coming in a new version of AR Studio, including the integration of 3D content aggregator Sketchfab's Download API.
Following San Francisco-based Occipital's successful Structure Sensor Kickstarter campaign, the release of its Bridge AR/VR headset, as well as a string of technology and company acquisitions, the company has built a rather strong name for itself in the AR community. And now, with the first public release of its Bridge Engine on Thursday, the company continues to expand the features its platform has to offer, with hopes of bringing in more developers to utilize it.