If you want to use your iPhone with another carrier, all you have to do is contact the original carrier to request an unlock, which is usually granted in a few days. Unfortunately, you need to meet specific criteria to officially carrier-unlock your iPhone, like paying off the device in full and completing any contracts. But that doesn't mean there isn't a workaround you can use beforehand.

As we enter the second half of 2018, rumors for the second season of flagships have started to emerge. On the Android side, this means the latest iterations of the Google Pixel, Galaxy Note, LG V series, and Huawei Mate. Thanks to FunkyHuawei and XDA, we now have some solid rumors regarding the Huawei Mate 20.
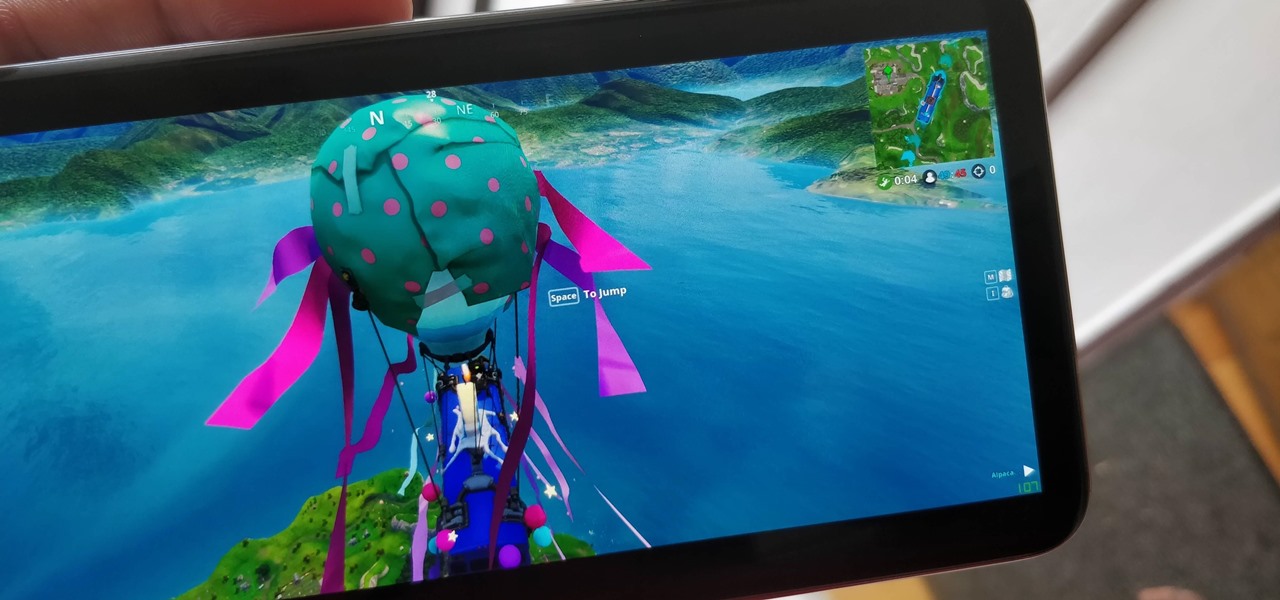
Since early March, iOS users have been able to enjoy the most popular video game sweeping the rounds. Android users have been left envious as they wait for a "few months," the only vague release date given by Epic Games. In the meantime, there are a few ways we can still satisfy our urge to play.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

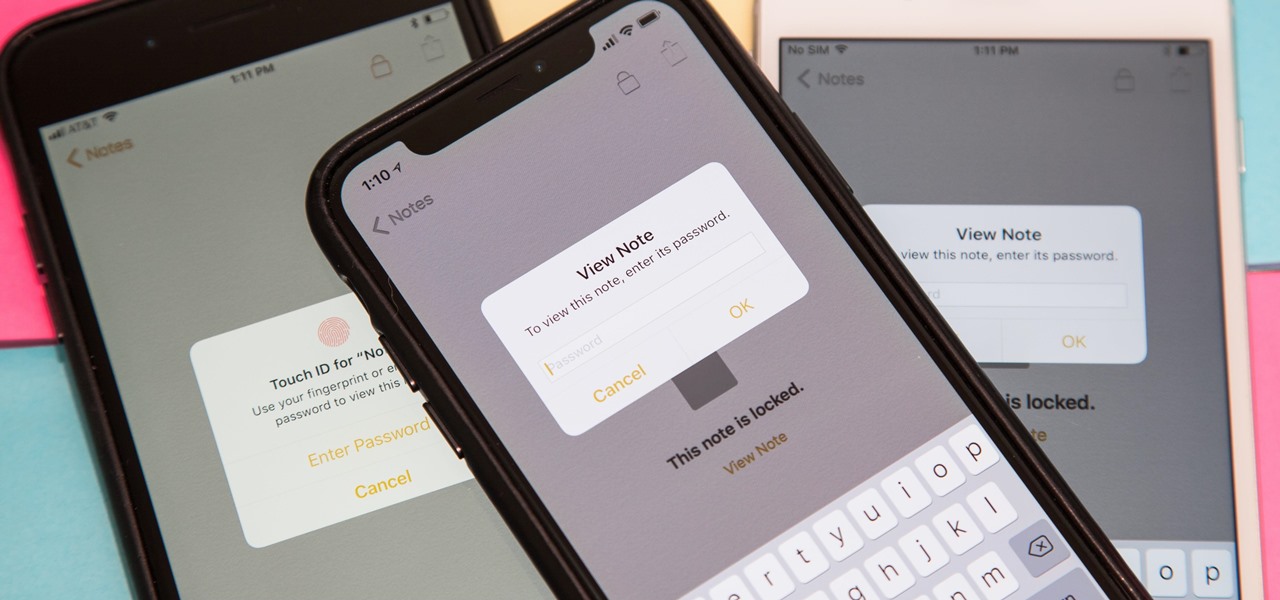
It's no secret that you can protect notes on your iPhone with a password, but one thing that most people don't know is that you can actually set unique passwords for each note instead of a blanket password for all of them. It's not obvious at all in the Notes app, but it's easy to do once you've got the hang of it.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

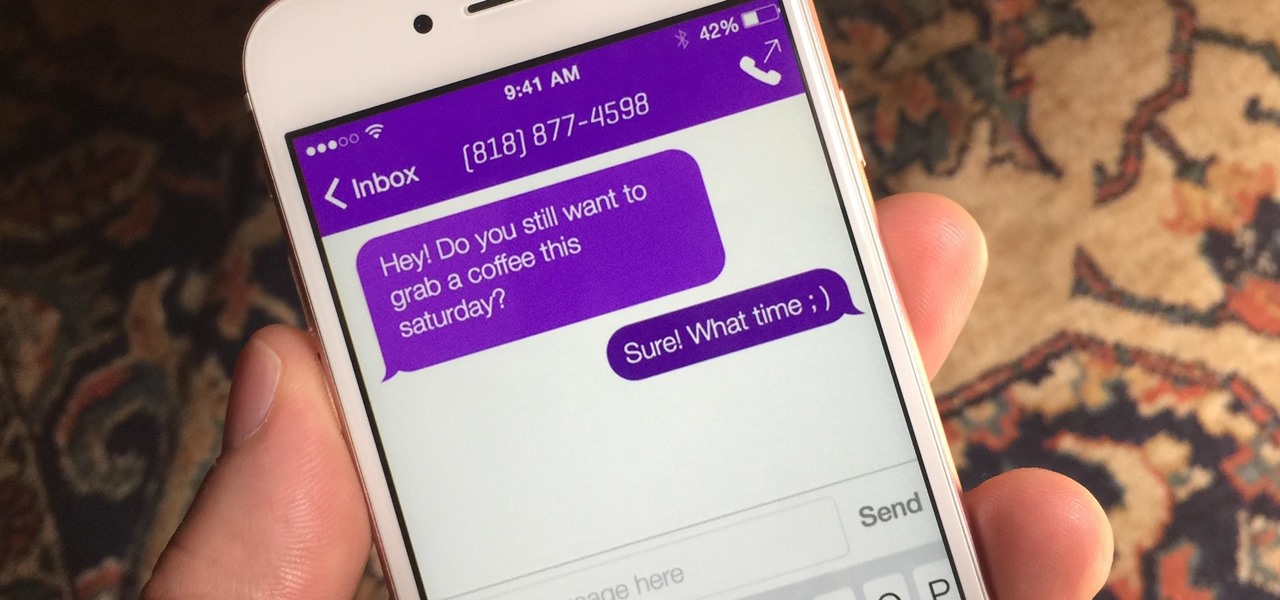
When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Nova Launcher is one of the most popular apps on the Play Store thanks to its rich features and fluid navigation. But one downside that comes with this abundance of features is that much of Nova's functionality is lost on the masses. Fortunately, I've used Nova for several years and learned a few tricks along the way.

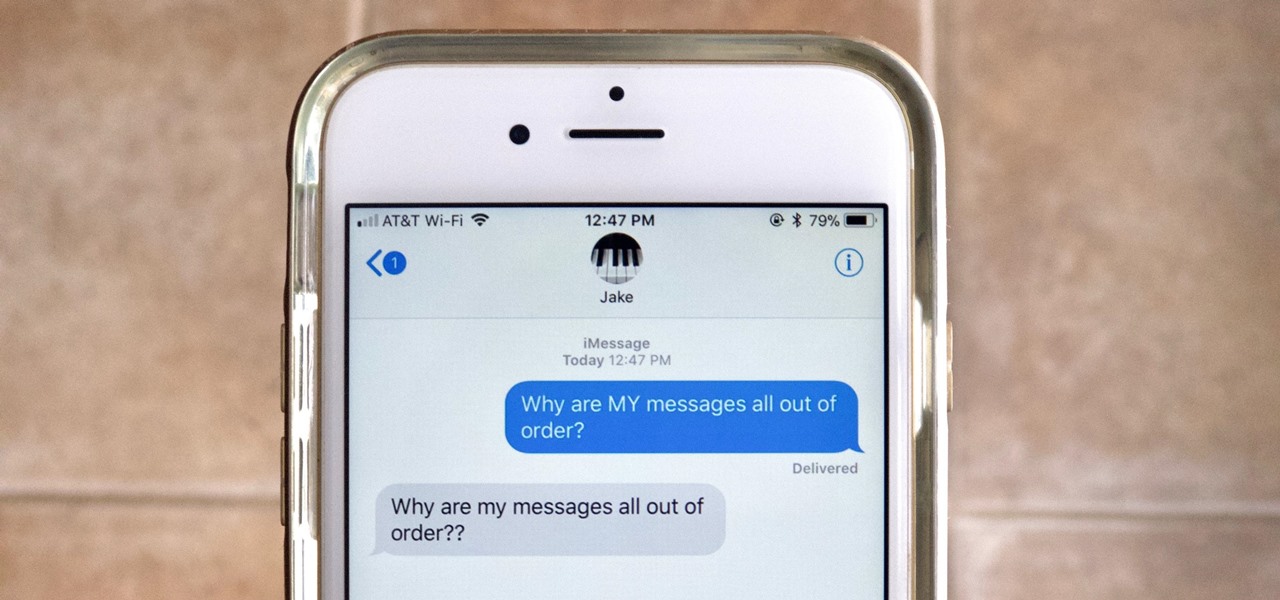
One of Apple's best products is iMessage, which allows for quick, creative, and free messaging between iOS and Mac devices. However, users are reporting that conversation threads in the Messages app are occasionally out of order, which is equal parts confusing and annoying. Luckily, we have some ideas on how to fix the problem.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Last week, augmented reality startup Proxy42 released Father.IO, a multiplayer game that turns any indoor or outdoor space into a laser tag arena.

Apple released the iOS 11.2 update for the iPhone to the masses early morning on Dec. 2, and here are all the new features and important bug fixes you need to know about.

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

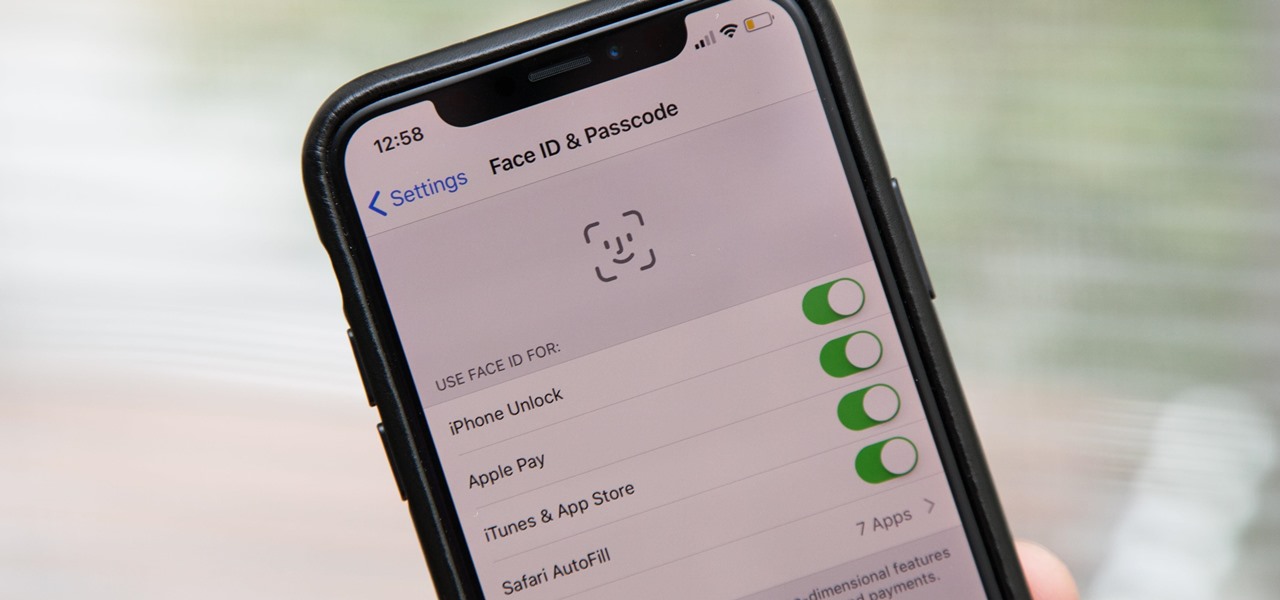
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

On June 11, 2016, an Arizona woman died from what appeared to be several infections, including pneumonia. She likely caught at least one of these from her dog.

Whether or not a microbe is successful at establishing an infection depends both on the microbe and the host. Scientists from Duke found that a single DNA change can allow Salmonella typhi, the bacteria that causes typhoid fever, to invade cells. That single genetic variation increased the amount of cholesterol on cell membranes that Salmonella and other bacteria use as a docking station to attach to a cell to invade it. They also found that common cholesterol-lowering drugs protected zebrafi...

The new iOS 11 was just released by Apple, and you can install it right now. Overall, it's got some great features, but how does it fare battery-wise on your iPhone? And how can you increase daily battery life for more juice and less charging every day?

On April 7, 2017, residents in Dallas, Texas, woke to the sound of emergency sirens blaring all over the city. No one could shut them off, and after repeated efforts to contain the situation, the city had to shut down the entire system. While the media reported a sophisticated computer hack was responsible, the truth was much less high-tech.

When building anything of a social nature, be it a local roller derby or softball team, a club dance night for chiptune, or building new technology markets, the community around those ideas are an important factor in helping these things not only come into existence but to grow into something that enlightens everyone involved. The community around an idea can actually make or break these new ventures — and this applies to augmented and mixed reality as well.

HIV-infected people who are treated long-term with antiviral drugs may have no detectable virus in their body, but scientists know there are pools of the virus hiding there, awaiting the chance to emerge and wreak havoc again. Since scientists discovered these latent pools, they have been trying to figure out if the remaining HIV is the cause of or caused by increased activation of the immune system.

The '90s were a great decade to be alive. Before the internet became a high-availability service, we were untethered from the bombardment of media present in today's culture. Children ran through the streets with levels of physical exertion beyond what's required to capture fictional creatures found in Pokémon GO. However, there were some video game consoles that kept kids indoors, such as the Game Boy, SNES, and more importantly—the first ever PlayStation.

While its direct-selling model echoes brands like Avon and Tupperware, Indonesia's MindStores gives the approach a modern twist—with augmented reality.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

Google's former Self-Driving Car project, now graduated from Alphabet's X division as Waymo, has found a collaborator and potential new partner in Honda. This is an interesting turn of events given traditional automakers' reluctance to work with driverless-car startups over the years.

In my days as a hardware tech, I often came across motivated do-it-yourselfers who watched a video or two on how to repair a phone and thought that they'd give it a go. More often than not, they failed miserably and damaged their phones (and wallets) even more in the process.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

Fight me all you want, but it ain't a party without alcohol—whether it's a Halloween party, Christmas party, dinner party, or even a damn wedding. (If you think that people will stick around after dinner for a dry wedding, then you're sorely mistaken.)

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

If you've ever played the game of Would You Rather, you've probably been given the ultimatum between eating insects or doing something else that sounds absurd, like licking a cactus. I'm advising you to always choose the insects, and here's why:

Throwaway phones aren't just for seedy criminals and spies—they can be useful for many everyday situations.

I've been an iPhone user in the iOS ecosystem for years now after a brief stint in the Android realm. But, I'm also enthusiastic about varying forms of technology in general; I realize that iOS is far from perfect and that healthy market competition is beneficial for all. So, naturally being curious about other platforms, I decided to take Windows Phone for an extended trial run.

When you're trying to cut some calories or just eat more veggies, it's important to enjoy what you're eating. If all you're doing is telling yourself "no" and focusing on what you can't eat, you are pretty much destined to fail at your diet.

While attempting to hack a web app, there may come a point where the attacker may have to escape the default directory in order to access unauthorized files. This is known as a directory traversal attack. Much as the name implies, this attack involved traversing the servers directories. But in order to move to an unauthorized directory, we need to know where those directories are. Today we'll be building a tool to brute force these directory locations based on HTTP response codes. Before we g...

If you think that "pawpaw" is just an affectionate name for your grandfather or a cute way of talking about your cat's feet, you're missing out on one of the most interesting fruits out there.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?