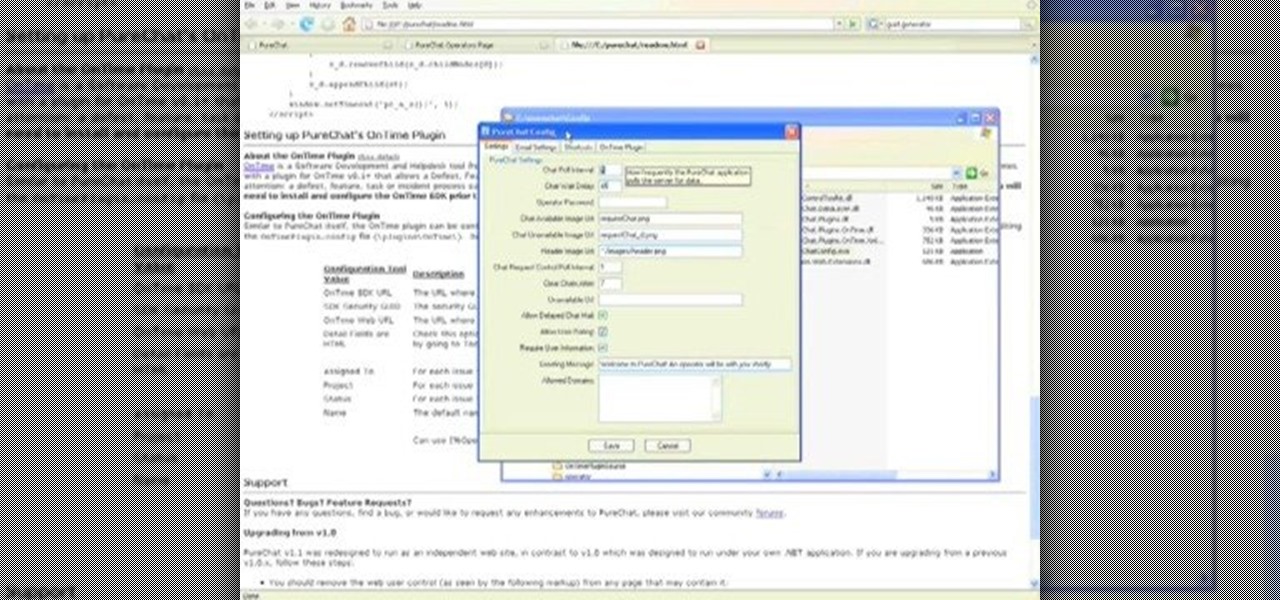
How To: Use PureChat with Axosoft OnTime 2008
PureChat 2008 ships with an OnTime plug-in that allows you to quickly turn live web chat conversations into defects, feature requests, incidents or tasks in OnTime -- with just a few mouse clicks!


PureChat 2008 ships with an OnTime plug-in that allows you to quickly turn live web chat conversations into defects, feature requests, incidents or tasks in OnTime -- with just a few mouse clicks!
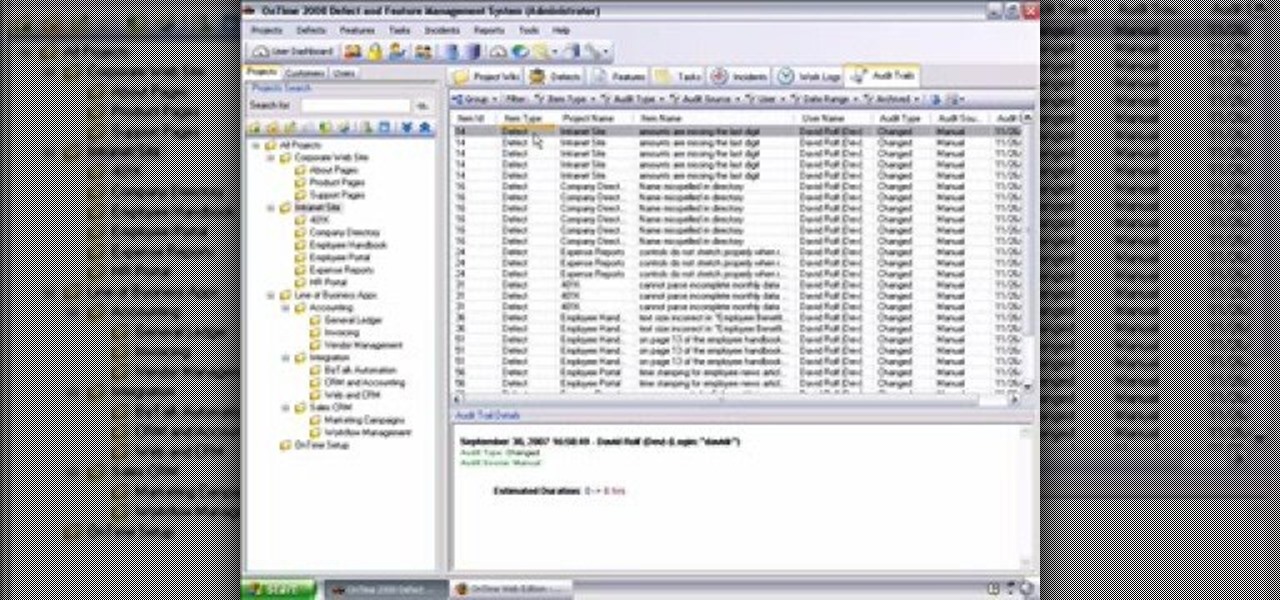
This installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite focuses on how you can see the history of your defects, features, tasks, and incidents, as well as project wiki pages. For more information, as well as to get started using the history and audit trails features in Axosoft OnTime 2008, take a look.
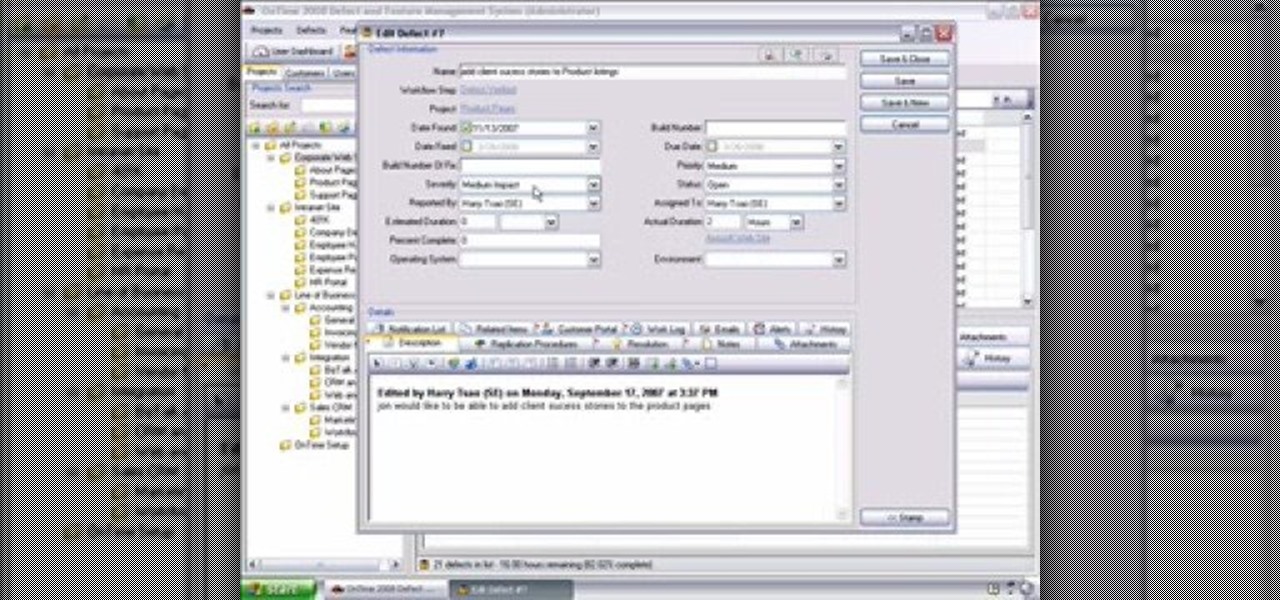
Worklogs are the time sheets of OnTime. They help track the time your developers spend working on bugs and features, or the time that tech support staff work on incidents. There are several ways to interact with worklogs and this installment from Axosoft's own series of video tutorials on the OnTime Project Management Suite covers them in detail.

In this Love Birds tutorial, the counselor, Roger Gil tells how to apologize to a woman. He says that we can apologize to women to reestablish some level of connection that has been damaged due to some incidents. He says that guys should not feel that apologizing is like surrendering. He says this can be an obstacle in the relationship. He says that the first step is to acknowledge the wrong action that we may have done. He says its not worth it to hurt a woman's feelings, and we should immed...

If all things go well, you'll only have to take your road test once. That's the goal: to ace your test on the first try and then start driving on your own. Granted, it's a nerve-racking experience, but keep in mind that the California Department of Motor Vehicles wants you to pass. So much so, they give you the examination answers ahead of time! All you have to do is study.

Cuphead may have taken the indie gaming scene by storm, but its "introduction" to the iOS App Store is what everyone in the smartphone world is talking about. There is no official Cuphead game available for iPhone, and that's what is so surprising — a fake version was approved and released for iOS devices, and at this scale, incidents like this just don't happen for Apple.

Ride-hailing services are everywhere nowadays and with new companies developing all the time, it is one of the most convenient ways for people to get around. Companies like Uber make it easy for passengers to call a car to pick them up and drive them to their desired location. These services have been especially helpful for commuters as well as those who might need a ride home after a night at the bar. However, ride-hailing services require driving with a total stranger, which means the safet...

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

An outbreak of anthrax from contaminated meat in Tanzania sickened dozens of people and moves the danger of this deadly bacteria back into focus.

Do you love a good mystery? Were you a huge fan of "The X Files" or any other freaky movie or TV show? If you are daring and not afraid of the unexplained, Paranormal Investigator may be the job for you. Check out this video to see if you qualify and exactly how you can get into this spooky field.

Location services provider Mapbox is expanding the reach of its augmented reality development capabilities to include apps for automobiles as well as smartphone navigation.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

Oh, Waze—you know, that Google-owned traffic navigation app that tempts drivers into stopping at local food joints like Dunkin' Donuts and Taco Bell? Well, now you can even order a large iced coffee through the app before you even arrive at a fast food hotspot.

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Apple is notoriously private when it comes to perspective products, but the latest leak from their De Anza office in Cupertino suggests that a new augmented reality device could be coming to a store near you.

This most recent school shooting, one of the worst in history, has devastated our country. That such an act can be performed not by a begrudged child, but by one or more adults, is nearly unthinkable.

With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.
If you don't want to be found on Twitter, there are several ways to do that without making your account private. For instance, you can choose an obscure username, omit your real name, or pick a random avatar. But there are lesser-known features deep in your settings that can also protect your privacy online, including preventing photo tags.

Traditional subdomain enumeration techniques create a lot of noise on the target server and may alert intrusion detection systems to an attacker's intentions. For a stealthier approach, there's a tool with the capability of finding hundreds of subdomains related to the target website without alarming the server administrators.

Legionnaires' disease is named after 1976 outbreak in Philadelphia that sickened 221 people and killed 34. More often striking adults over the age of 50, the Centers for Disease Control and Prevention (CDC) recently reported two cases where newborns contracted the often fatal disease — at their moment of birth.

As many of you know, I have been running a couple of series here on Null Byte about digital forensics called Digital Forensics for the Aspiring Hacker and Digital Forensics Using Kali. Although many readers have seemed to enjoy these series, just as many seem to be pondering, "Why should I study digital forensics?"
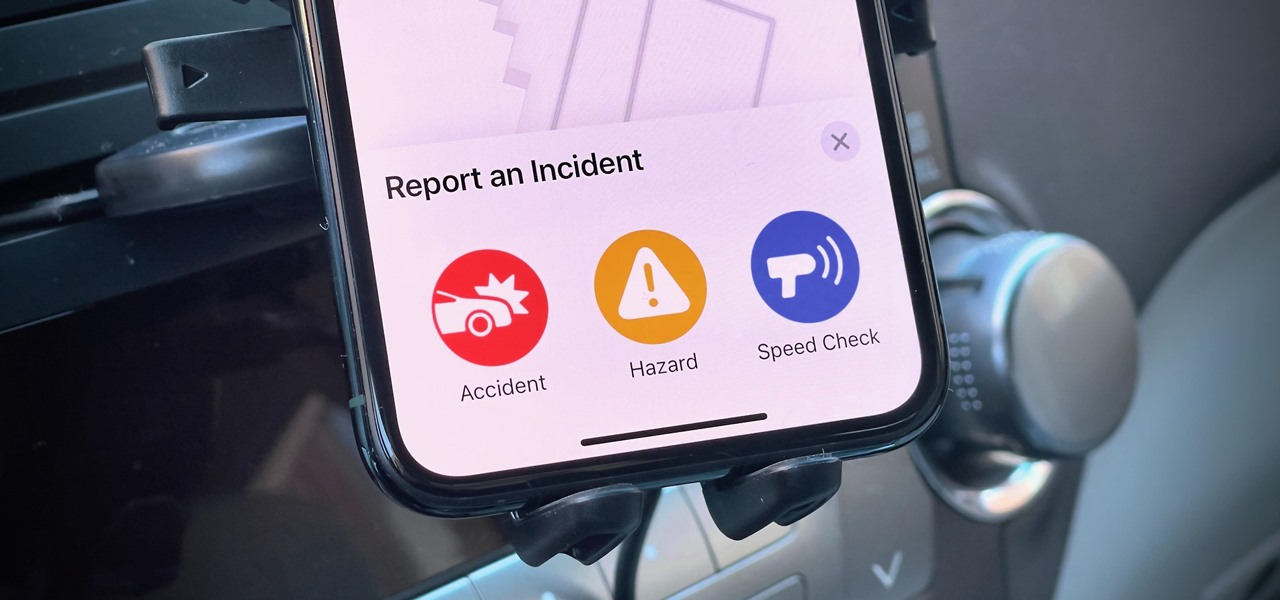
Driving is anything but problem-free. Speed traps, accidents, and other hazards can appear at any time, requiring motorists to be attentive, quick, and prepared for anything. If you see something dangerous on your route that you want to warn others about, there's an easy way to do so in Apple Maps.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

So the new iPhones have arrived. Like last year, Apple released three iPhones in three different sizes that vary in price and specs. There's the base model iPhone 11, and then there are the real deal, premium models, the iPhone 11 Pro and Pro Max.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

In our first part on software-defined radio and signals intelligence, we learned how to set up a radio listening station to find and decode hidden radio signals — just like the hackers who triggered the emergency siren system in Dallas, Texas, probably did. Now that we can hear in the radio spectrum, it's time to explore the possibilities of broadcasting in a radio-connected world.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
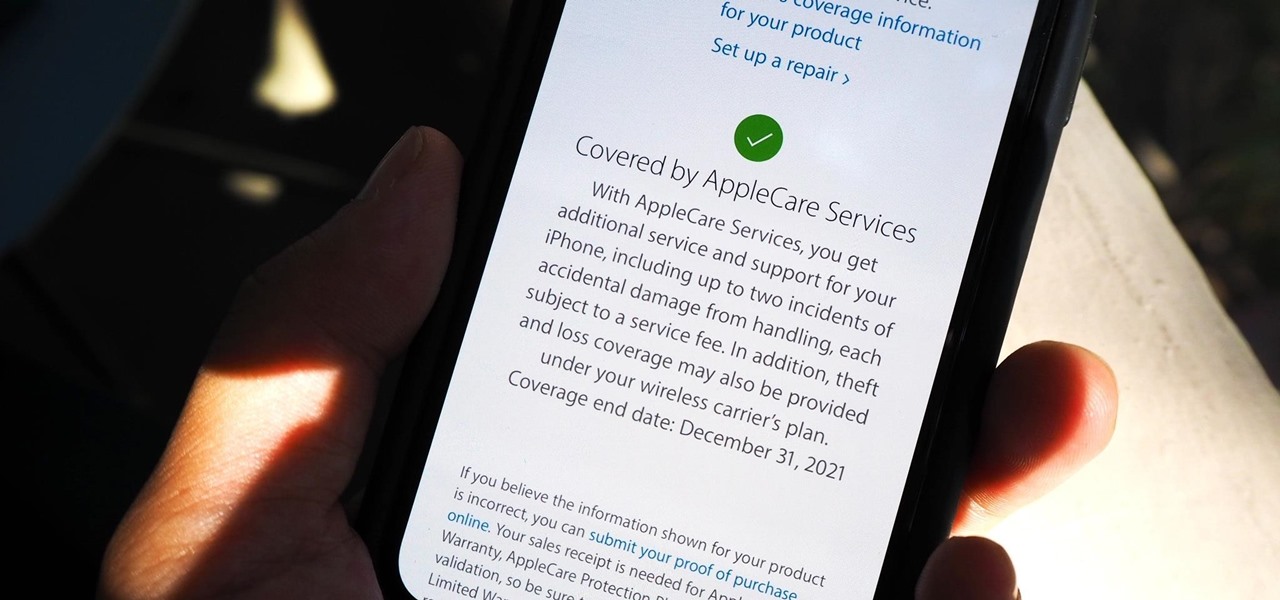
Let's say that the screen on your iPhone is showing signs of discoloration, which makes the display annoying to use. You'll need a replacement display or a new iPhone as soon as possible. If you have one of the newer iPhone models, the cost to fix it might be more than your wallet can handle, but a warranty may still cover it, and there are ways to check quickly.

Airgeddon is a multi-Bash network auditor capable of Wi-Fi jamming. This capability lets you target and disconnect devices from a wireless network, all without joining it. It runs on Kali, and we'll cover installing, configuring, and using its jamming functionalities on a small, inexpensive Raspberry Pi. When done correctly, it will deny service to a wireless network for up to several blocks.

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

Apple has four iPhone models for the remaining months of 2020, but the most impressive ones are the iPhone 12 Pro and iPhone 12 Pro Max. While the iPhone 12 and iPhone 12 mini are great smartphones, the "Pro" models offer more advanced features, especially for photographers and augmented reality enthusiasts.
In case you haven't figured out already, our government is always on the move to figure out new ways to extend their control. The CISPA, for one, is one of the best examples, along with "re-education" programs, and racial divide (Trayvon). What I've noticed in the past few months is that their new "ideas" are coming out at an increasingly alarming rate.

Image via Tiger Mom Says.
Multiple airport screeners have been arrested for allegedly taking handsome bribes to look the other way while loads of illegal drugs slipped through security at Los Angeles International Airport, federal officials announced today.
Residents of an Afghan village near where an American soldier is alleged to have killed 16 civilians are convinced that the slayings were in retaliation for a roadside bomb attack on U.S. forces in the same area a few days earlier.

TV newscasters love to run stories about out of control parents fighting at youth sporting events. Here is an example of a story