The evidence is mounting and is becoming indisputable: Gut bacteria play a role in strokes and heart attacks. The link may seem a little far-fetched, but cardiovascular disease may have less to do with what we eat and more to do with what chemicals gut bacteria make from the food we eat.
Winter is coming for Amazon. It looks like the company is having another go at the smartphone world with its release of new smartphones branded as "Ice".
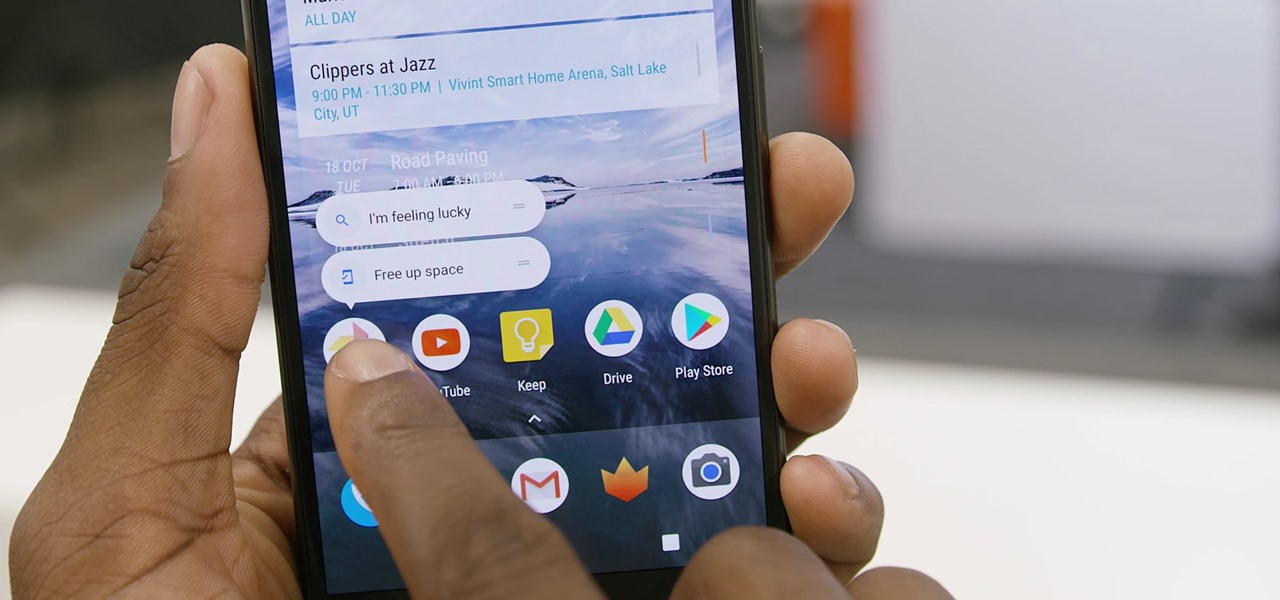
Google's got quite a few tricks up its sleeve with their Pixel and Pixel XL flagships, including functionality we've never seen before on Android. One awesome feature is called "App Shortcuts," and the basic premise is strikingly similar to Apple's 3D Touch—just long-press an app icon, then you'll get a pop-up that lets you perform quick actions.

When you were unboxing your Galaxy Note7, you probably wondered why a little metal claw tool was included in the packaging. Then, if you looked closer, you saw there were five plastic sticks included with the claw tool that came in two different colors.

The new USB Type-C standard was supposed to revolutionize smartphone charging, but so far, it's done more harm than good. Many cable and charger manufacturers are struggling to keep their products in line with the proper USB-C specifications, so as a result, we now have to check to see if a cable is compliant before purchasing one.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

CyanogenMod has always been on the forefront of ROM customization, and its newest release, CyanogenMod 12, is no exception. In the newest nightlies, they have included an updated version of their Theme Engine, which allows you to effortlessly change the way your entire system looks.

The Snapdragon 801 processor inside the OnePlus One puts the device on par with other phones like the HTC One M8 and LG G3 in terms of power and speed. While the OPO is just as fast and responsive as many of the flagships currently available, there's no reason why we can't try to squeeze every last bit of speed and performance out of it.

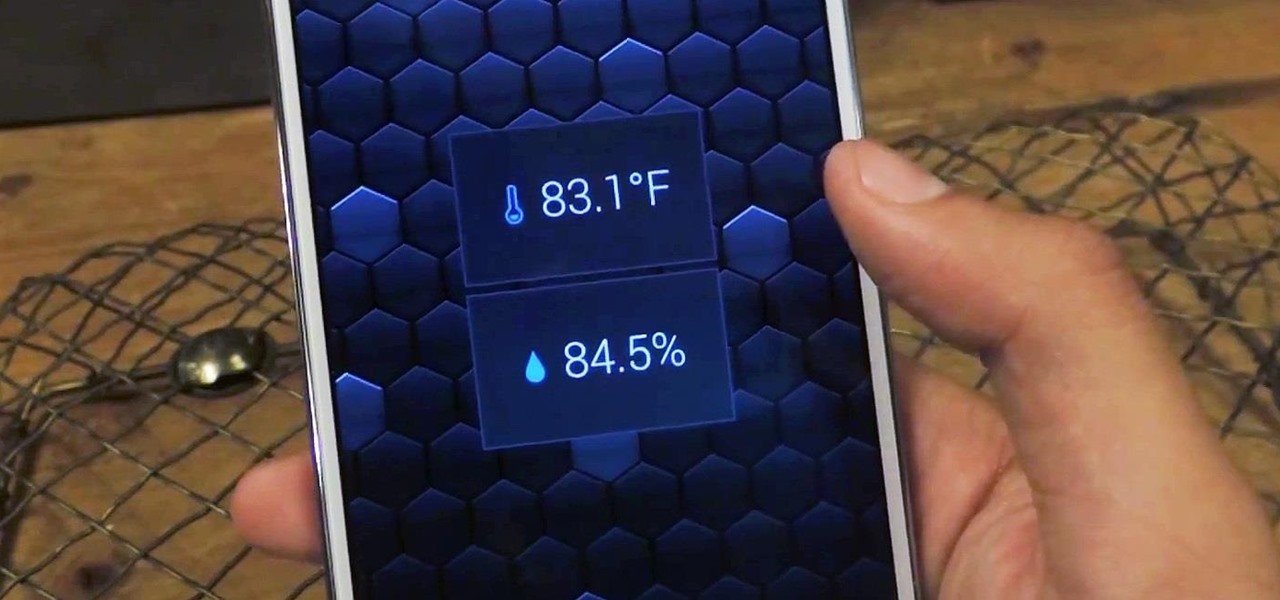
The majority of Android devices have built-in sensors underneath the hood that measure motion, position, and several environmental parameters that provide data needed to monitor your movements and adjust accordingly.

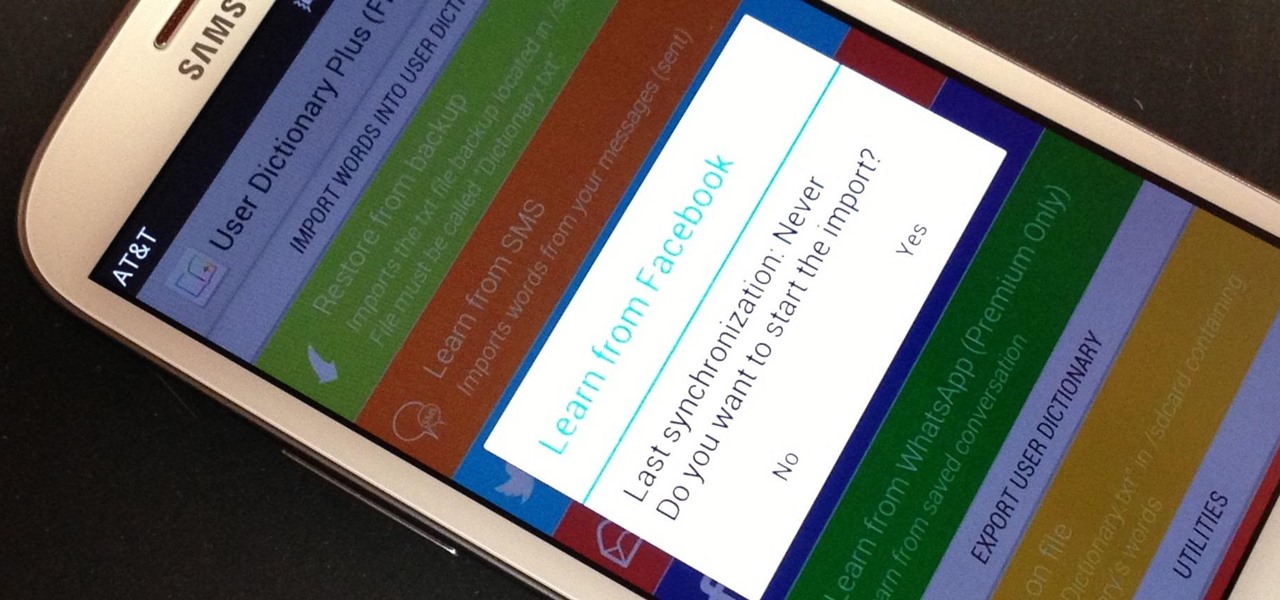
My standard text greeting to friends is something along the lines of "Wazzup biznitch?"—but apparently the auto-correct function on my Samsung Galaxy S3 has a problem with that. Time after time I have to retype it or just add all my made-up words to the word list—and I use a lot of made-up words, because that's what bosses do. But texting isn't the only way I communicate. I also use email, chat, and social media on a daily basis—and I don't always use my phone. So, wouldn't it be awesome if m...

Builds in Minecraft aren't usually for your own personal enjoyment; most people want to show them off to others. So to some extent, builds need to be user-friendly. That is, they should automatically guide people to areas of interest or importance. One particularly stylish way to do that is by using guide lights. I have two different designs included here, which you can either use or adapt to your own purposes.

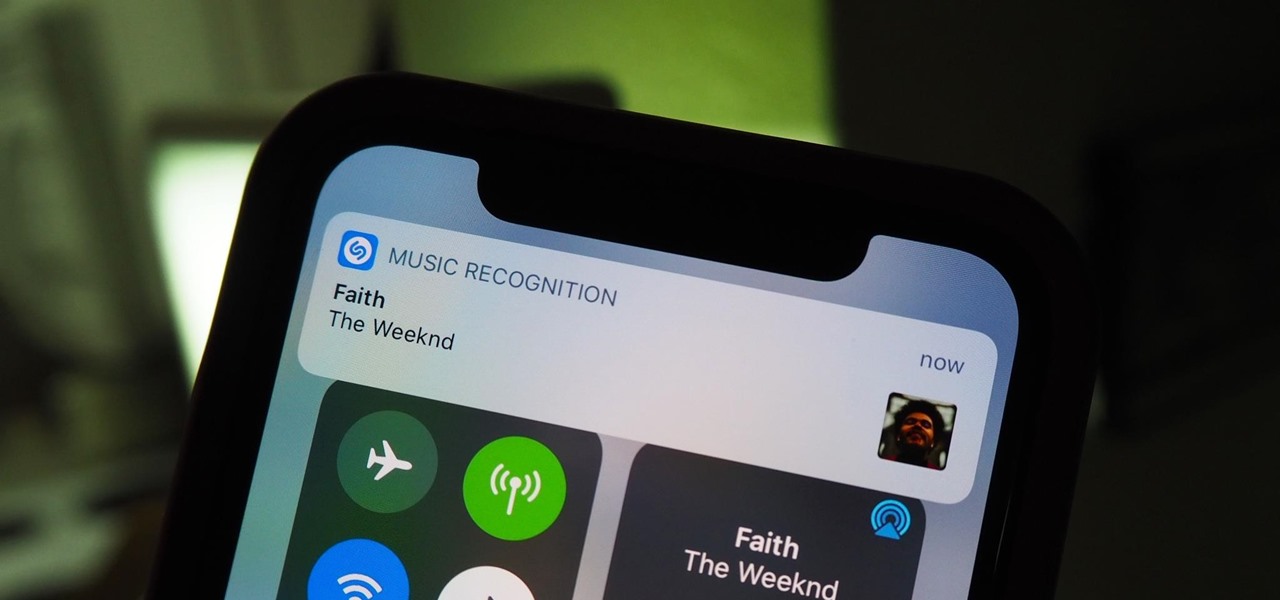
With or without the Shazam app, which Apple acquired in 2017, you can use Siri on your iPhone to identify music playing around you that you want to know more about. In the iOS 14.2 update, there's another way to name songs on your iPhone.

Surprising? No. Exciting? Absolutely. After a grand introduction by at the Apple event on September 10, 2019, the iPhone 11 is finally here. We may have known nearly everything about this new iOS device ahead of time, thanks to the usual surge of reliable leaks and rumors.

As I've mentioned in recent days, it was refreshing to discover that Microsoft's HoloLens 2 stage production was every bit as accurate as presented (check out my hands-on test of the device for more on that).

Its official: On May 8, T-Mobile finally released the Android Oreo update for the LG V30 and V30+. Now, every major US wireless carrier has pushed the update. For me, this update is a big deal. Not only does Android Oreo bring some new tools and features, but LG has also included a few additions as well.

Update: Google's new Pixel models have been released! Check out our full guides on the Pixel 3 and Pixel 3 XL to see all the details, but we'll leave the rumor roundup intact below for posterity.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

With portable devices being a necessity in modern everyday life, they may be subject to overuse, improper charging, or normal wear and tear. For those people who carry around their smartphone or iPod with them all of the time, how many times have you been out and about just to have your portable device die on you?

In a previous post, I wrote about how controversy changed SCRABBLE, about how the SCRABBLE Dictionary evolved thanks to Judith Grad and her crusade to rid the world of derogatory and racist words. She won, at least in some manner, but the fact still remains, racist or not—words are words, and they're here to stay.

With the Kodak Zi8, the power to capture razor-sharp, full 1080p HD video fits in the palm of your hand. Its easy, one-touch operation and incredible versatility make it the perfect camera for beginners, experts, and everyone in between.

Coders are accustomed to working remotely. The beauty of coding is that all you need is a laptop and a WiFi connection, which makes working anywhere a fairly simple transition. If you're looking for a career change, now might be the perfect time to give coding a try.

Data analytics is crucial to the operations of every modern business. This trend is going to continue: in three years, 71% of global enterprises predict a rapid increase in data analytics. Experienced professionals that can project manage data initiatives are in high demand.

The original iPhone SE was, for some, the perfect iPhone. It brought back the popular one-handed form factor of the iPhone 5 but packed in the internals of the then-new iPhone 6S. Now, the second-generation iPhone SE is here for 2020, but can it live up to what made the first-generation iPhone SE so popular?

Mobile gaming has exploded, with roughly $70 billion in revenue in 2019. This gave rise to the so-called gaming phone, headlined by names like Razer and ASUS. While the Galaxy S20, S20+, and S20 Ultra are being marketed as everyman devices, make no mistake — these are unstoppable mobile gaming machines.

Apple's Reminders app has never been particularly sexy or appealing, but that changes in iOS 13. Although the productivity tool has always been useful for quick to-dos, it now has an overhauled user interface with several new features, including grouping lists together for improved organization.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

To combat their poor coverage in rural areas, T-Mobile spent nearly $8 billion on 600 MHz spectrum in 2017, which was converted to LTE Band 71. With such a low frequency, the signal can travel further, providing LTE speeds to more Americans. But your phone also has to support this frequency, and so far, only a handful do.

Late last year, we got a little surprise from Razer. The gaming company released its first smartphone, and as expected, it targeted gamers. Branded as a gaming phone, it started a trend which several other companies followed soon after, including ASUS, Xiaomi, and even Samsung. So as you can imagine, many are excited about its successor.

The iPhone XR is the best bang for your buck option among the 2018 iPhones. Splitting the XR and XR Max right in the middle with screen size, it makes small compromises to to keep the price low. However, with the release of the Galaxy Note 9, Samsung has their own formidable middle option as well, the Galaxy S9+.

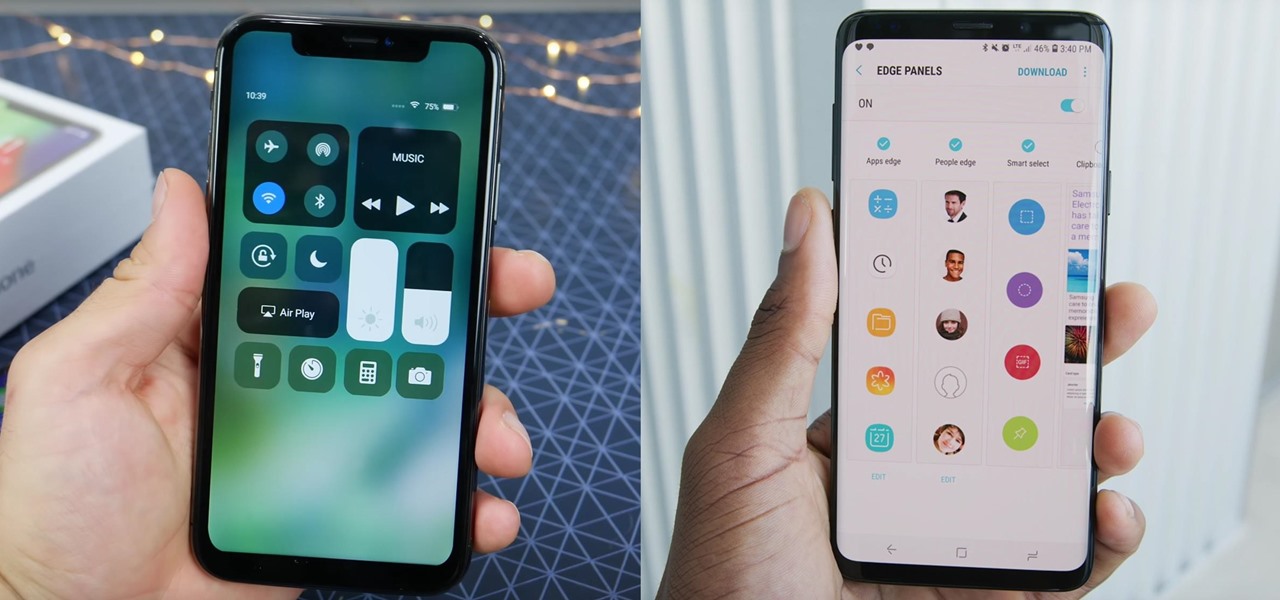
Until next March, the iPhone XS and Samsung Galaxy S9 will be the only phones considered by many. Whether you're an Apple fan wanting to see how your new phone stacks up against the competition or a buyer on the fence, here's how the latest flagships from the two biggest brands compare.

A simple security flaw can allow an attacker to gain a strong foothold with little effort on their part. When a web application permits remotely hosted files to be loaded without any validation, a whole can of worms is opened up, with consequences ranging from simple website defacement to full-on code execution. For this reason, RFI can be a promising path to obtaining a shell.

With iOS 12, your iPhone's Messages app has more features than ever to enhance iMessage and FaceTime. Included in these changes are the new camera effects, which allow users to add fun and unique customizations to their photos and videos with the in-app camera in Messages. Stickers, Memoji, and more await the photos you take and send in Messages. ...

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Another piece of Magic Leap's mysterious story has been uncovered thanks to a new patent application revealed on Thursday, March 15.

OnePlus has now officially upgraded both the 5 and 5T to Android 8.1 Oreo. As implied by the version number, this isn't a huge update from Android 8.0 Oreo. However, OnePlus has included a few of their own features as well.

As expected, Apple began pushing out the final version of iOS 11.2.5 to all iPads, iPhone, and iPod touches today after 41 days of beta testing. Highlights include a fix for the ChaiOS vulnerability, a persistent Now Playing bar in Music, and some signs of AirPlay 2 just in time for the HomePod launch on Feb. 9.

Technology ages rapidly. We're conditioned to refresh our iPhones every one or two years, and why wouldn't we? New iPhones are fast, and our old ones inevitably slow down, sometimes to an unusable degree. However, it turns out, there's something we can do about that, and it doesn't involve buying a new iPhone at all.