With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

I'm a sucker for sushi, both in its traditional forms and its modern fusion creations. When the infamous sushi burritos surfaced, I'm not ashamed to admit that I waited in a ridiculously long line for what is essentially an uncut sushi roll. (As for whether it was worth it or not, well... that's another story.)

When it comes to photographing products, models, and other small objects, a good light box makes the process super easy, no matter what your skill level is. However, if you want to create decent 360-degree images, things get tricky really fast. A new product, the Foldio360, may provide some much needed relief though.
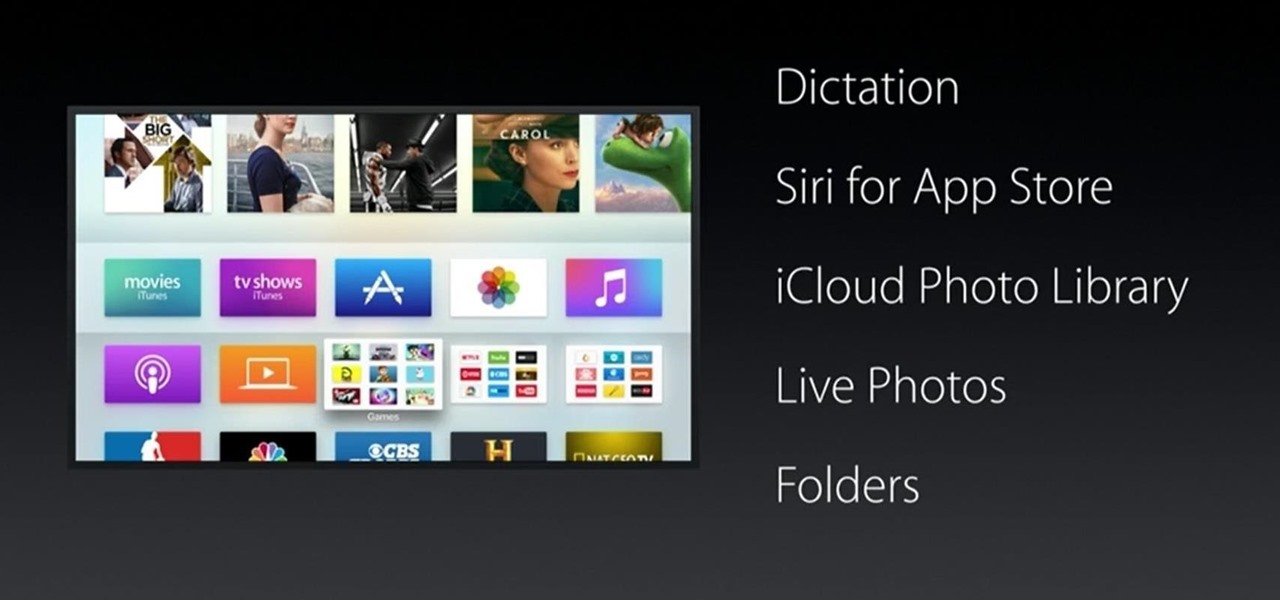
Apple will release tvOS 9.2 for the latest Apple TV today, bringing some major features to the streaming device. The software update, announced at today's Apple event, comes with Siri voice dictation, full iCloud photo viewing, and support for Bluetooth keyboards. Since Apple has already been beta-testing tvOS 9.2 for months, it's ready for a public rollout.
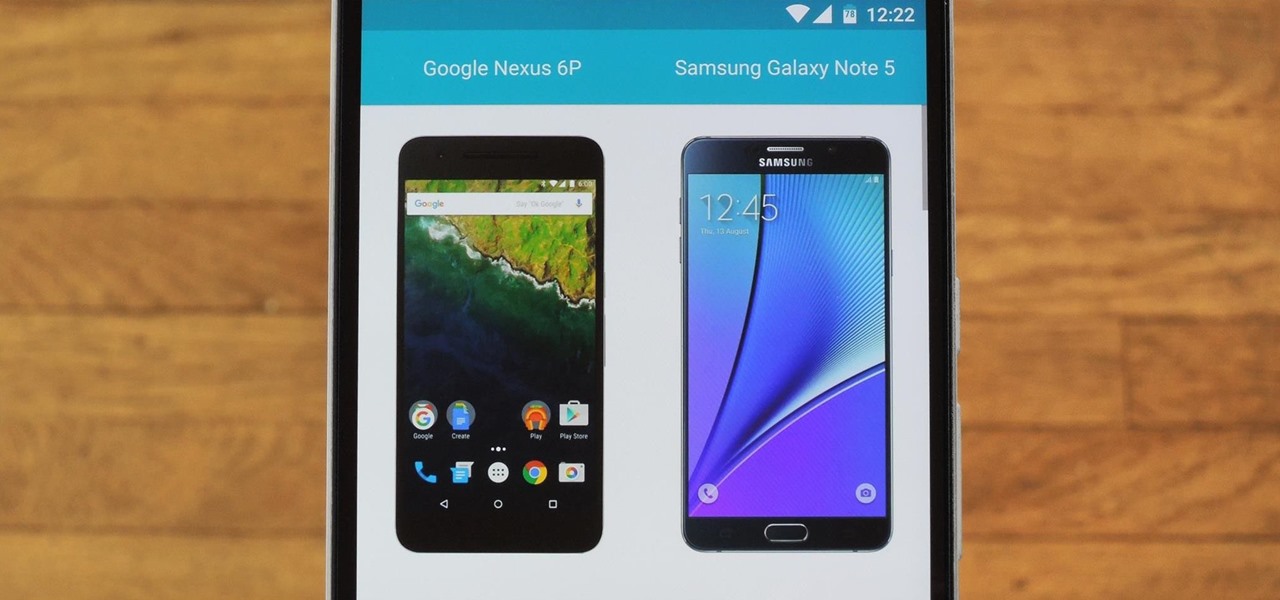
Shopping for a new phone is an entire ordeal. Even when you've narrowed it down to a few choices, comparing the finalists can be difficult, because specs and prices are scattered around on various different manufacturer websites, and if you're trying to do this on your current phone, most of these websites aren't optimized for mobile viewing.

Welcome back to another episode of Java Tutorials, In today's tutorial, we'll be learning about what methods are, proper syntax when writing Methods, and why they are beneficial in a program's code.

Welcome back, my budding hackers! One of the most basic skills the forensic investigator must master is the acquisition of data in a forensically sound manner. If data is not captured in a forensically sound manner, it may not be admissible in court. In my Kali Forensics series, I showed you how to acquire a forensically sound, bit-by-bit image of a storage device such as a hard drive or flash drive, but now let's dive into live memory.

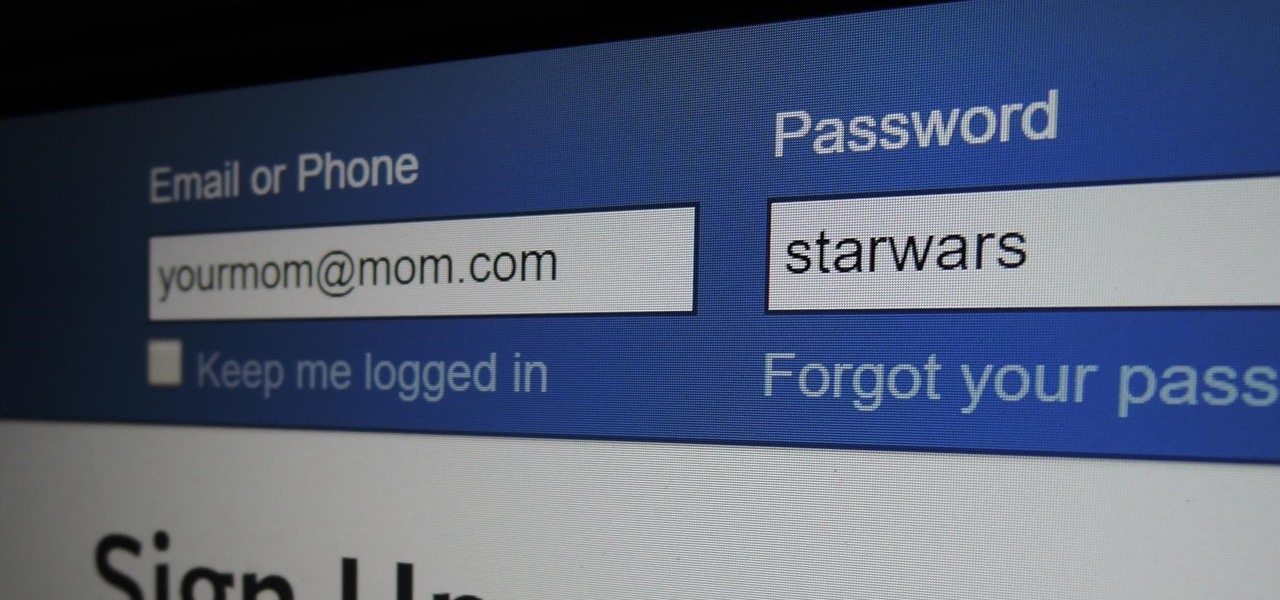
Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

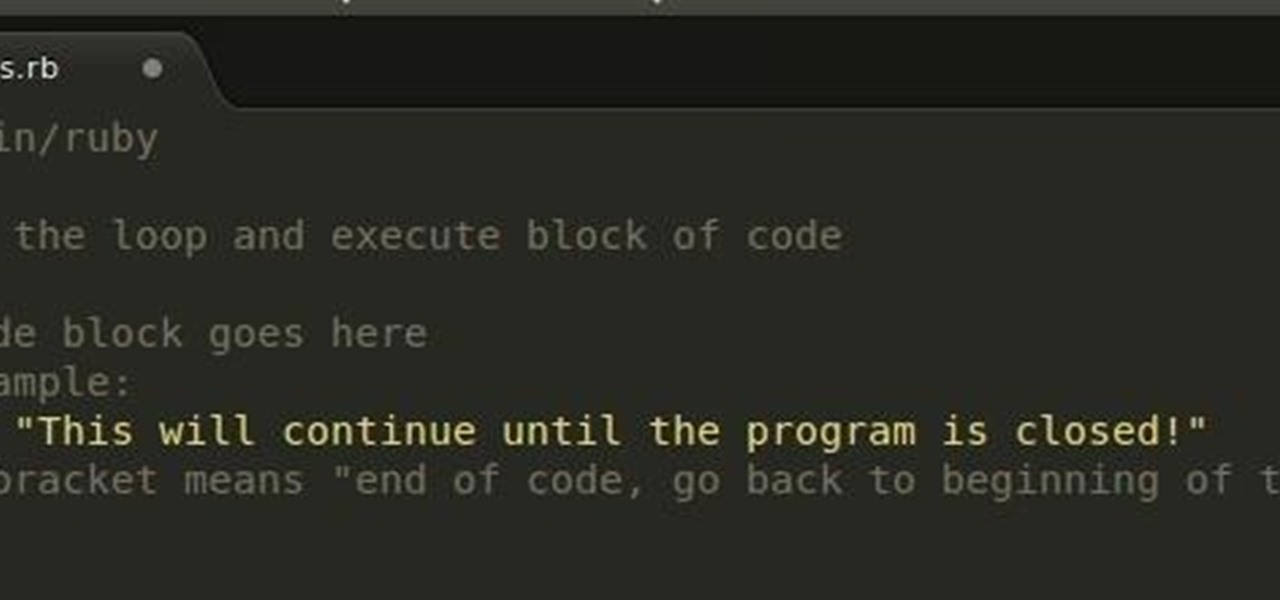
In the last Ruby article, we talked about how to store information in three different kinds of storages: variable, array, and a hash. After we get the data, we have many ways of using them, but, for right now,

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Mac OS X 10.11 and iOS 9 won't be officially released until later this year, but that doesn't mean you can't get a taste of it today. And the easiest way to do that is to download the new El Capitan and iOS 9 wallpapers.

Unlike the Moto X with its Active Display or the Nexus 6 and its Ambient Display, some devices (especially those now running Lollipop) do not include a function that permits the display to turn on upon getting new notifications while the device remains locked or the display inactive.

Some third-party keyboards, like SwiftKey for example, include a convenient feature that suggests emojis as your type based on the content of what you're saying. Unfortunately, many keyboards, including most stock ones, don't include this function.

Apple Watch doesn't include a multitasking feature like its iPhone companion, so there's no way to show active apps or swipe up to force-close one. Watch is an extension of the iPhone, not a replacement, so including a fully-functional multitasking feature seems impractical.

Snapchat developers insist that the app stay true to what its always been: a service for snapping and sharing self-destructing images. This belief is further hit home with their strict 31-character text limit, which some people refuse to abide by. Namely, Snapchatter Shayne Skellett.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

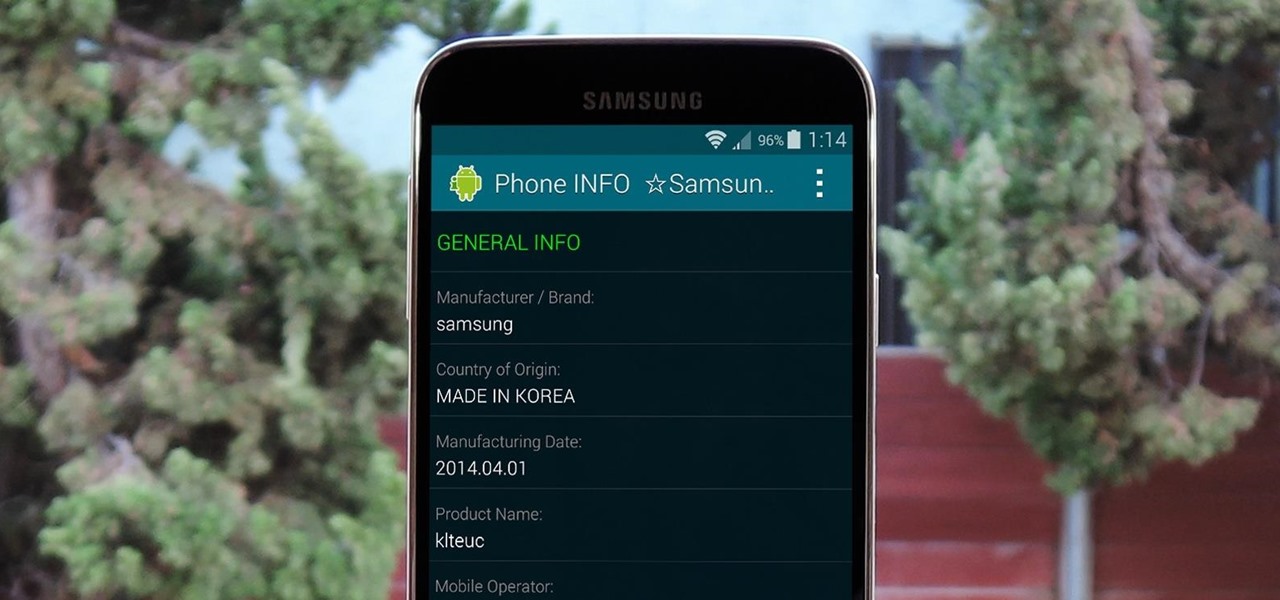
Before you purchased your smartphone or tablet, the device had already embarked on quite a long journey. From product development to manufacturing, your Samsung Galaxy device had already developed a rich history prior to your ownership.

Live wallpapers, like the classic Mario-themed one we previously covered, is a great way to spruce up your device and get some simple amusement. Unfortunately, they also drain more battery than conventional wallpapers. Which brings me to ASUS LiveOcean.

With intelligent grammar check, accurate predictive text, swipe gestures, and plenty of themes, it makes sense that Ginger Keyboard has well over a million downloads on the Google Play Store, making it one of the more popular keyboards available for Android users.

Google Earth has long served as a great tool to explore the furthest regions of our beautiful planet from the comfort of our own homes, but for those with more than just a recreational interest, a bundle of pro features had always cost $399... a year.

With Android devices getting bigger by the year, you'd think there would be a native multitasking solution by now. While Samsung and LG have included such features in their customized builds of Android, the stock base that manufacturers start with still doesn't include multitasking support.

Bow down, peasants: your gingerbread house just got owned. By whom? Martha Stewart, of course. The lifestyle guru has constructed elaborate gingerbread buildings in the past, but this year PBS asked her to build a gingerbread reproduction of Downton Abbey, in honor of the show's fifth season coming to PBS starting Jan. 4th, 2015. (PS: For those of you in the UK, the fifth season's Christmas special will be airing on Dec. 25th, 2014.) The materials included 11 batches of gingerbread, 16 cups o...

The prevalence of smartphones has had profound effects on how we communicate, view media, and preserve memories, among other things. But all of these new forms of doing things are snatched away from us as soon as our phones lose power. While work is constantly being done to stretch and extend battery life, it hasn't moved fast enough for the vast majority of us.

As far as customization goes, there's nothing you can do to change the look and function of the Control Center on your iPhone. By default, you can't alter the system toggles, but if your device is jailbroken, it's a completely different story. With the help of a tweak from developer plipala, called CCSettings for iOS 8, you can add, remove, and rearrange your Control Center toggles.

In previous posts here, I have pointed out that hackers are in high demand around the world and in nearly every industry. Every military and espionage unit of every country is trying to hire high-quality, experienced hackers as fast as they can to hack their adversaries' computer systems in order to gain a strategic advantage and to spy.

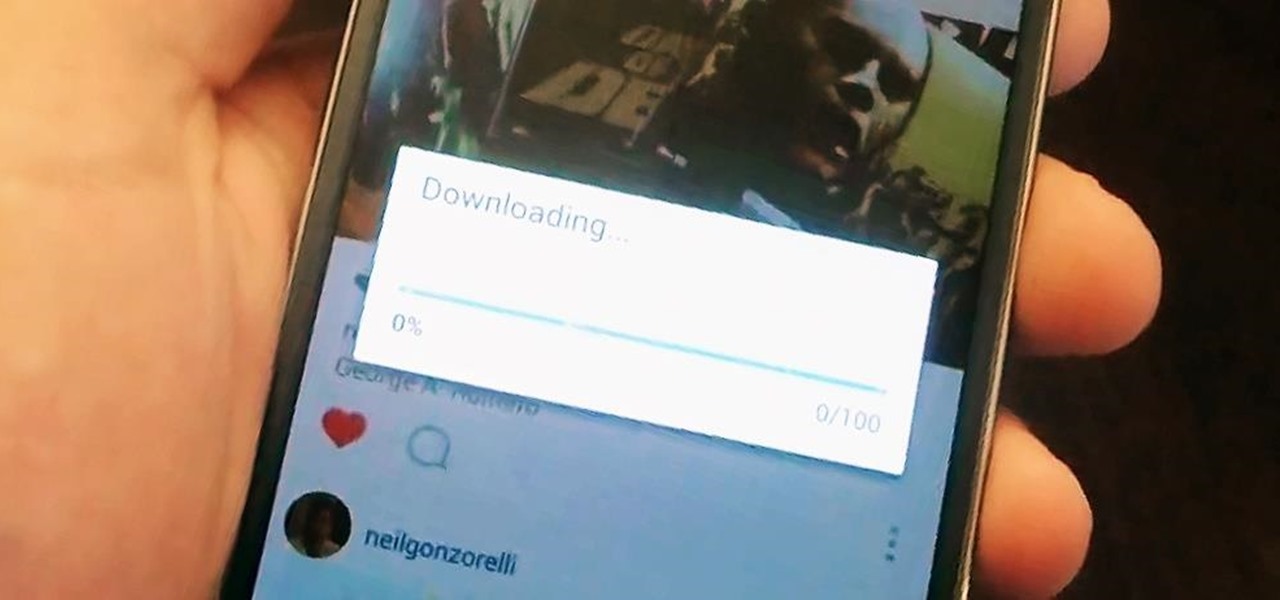
Scrolling through my Instagram feed, I inevitably come across an image or video that I genuinely like amongst the countless selfies and plates of food porn. Naturally I want to save this image before it's buried under new posts from the heaps of people I follow, but I'm left stranded with only the ability to take a screenshot.

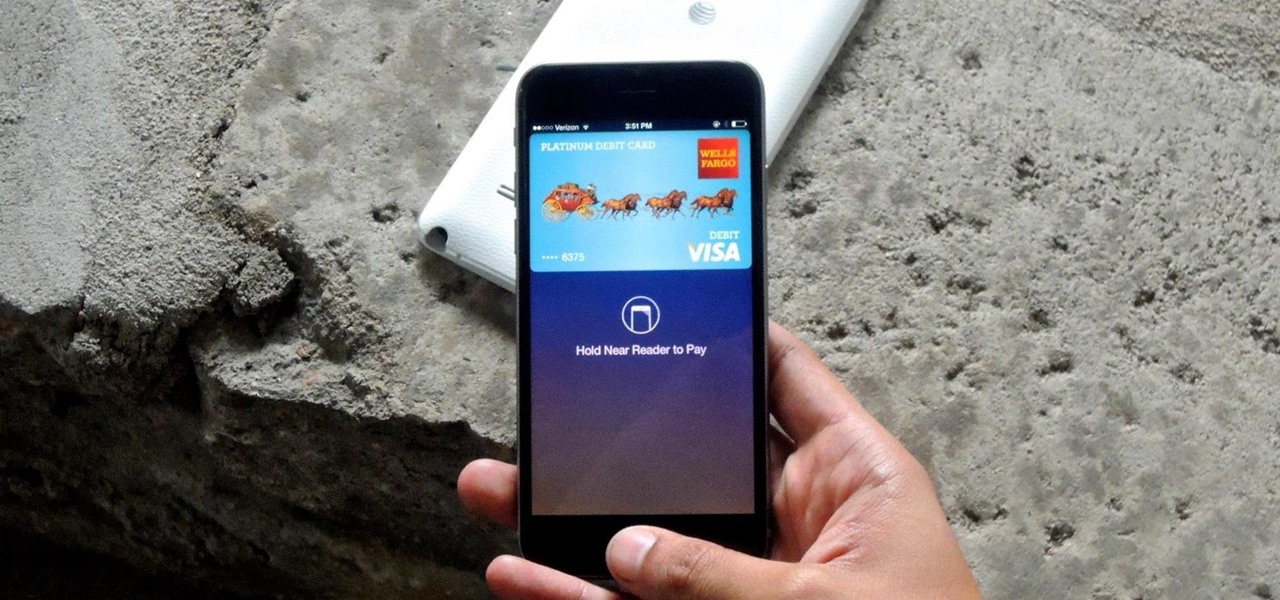
Apple Pay is ready for use at over 220,000 outlets across the United States. By using your iPhone 6 or 6 Plus, all you have to do is point your device at any NFC-enabled point-of-sale system compatible with Apple Pay, press your fingerprint on the home button, and voilà—you've just paid for something with your card. As a matter of fact, the store doesn't even need to have Apple Pay compatibility to work with your phone. If their machines have NFC-technology, they'll recognize your device (unl...

With the Power key located on the back of the device, LG included a convenient "double-tap to sleep" function in their G2 and G3 devices. The function allows users to simply double-tap the display to put their device to sleep instead of picking it up and pressing the Power key.

For the most part, Finder has had the same basic functionality through the various releases of OS X. But Apple's lack of interest in adding new bells and whistles to the backbone of their operating system simply means that 3rd-party developers get to shine, and Tran Ky Nam is one such developer. He created his own extension for Finder that adds tabbed browsing, dual pane mode, cut & paste functionality, and much, much more.

With root access, you're granted greater control over your device, allowing you to do things that your Android system wouldn't allow otherwise. Things like installing Xposed mods are made possible with root, but other advantages address performance and security, like stopping your Android logging, which is exactly what we'll be going over today.

Among the additions that Apple's included in iOS 8 for iPhones are a couple of new features to the Camera app, including a timer and manual control of the exposure setting. Hit up the video to see how these new features work, of scroll down for the written walkthrough.

The camera on the Amazon Fire Phone is simple and easy-to-use, with a 13-megapixel rear shooter with optical image stabilization, but there are a couple of features that makes this camera stand out from others.

If you thought iOS 7 was a drastic change from previous iterations, iOS 8 will certainly continue to rock the boat. From a revamped Control Center to enhanced "Continuity" to ephemeral messaging, Apple's newest mobile operating system will have many of you relearning the "basics."

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

E3, or the Electronic Entertainment Expo, is the 20th annual trade show for video games and gaming tech. The event takes place on Tuesday, June 10th at the Los Angeles Convention Center, and you can watch a live stream of the event on Twitch.

When looking at weather applications and widgets, one major characteristic I look for is efficiency; something that will separate it from the rest of the herd. The stock weather widget looks great on my home screen, but I have to exit whatever app or game I'm in when someone asks me about the weather.

The official Google Hangouts app has been around for a while, and is the standard messaging app on Nexus devices, but Google didn't make each version equal. On the iOS version, you get the feature of adding "stickers"—GIF emoticons—but Google left that out of the Android version.

HTC introduced their version of gesture controls to the masses when they launched the HTC One M8, and while the feature includes gestures to open the camera, start voice dialing, and unlock the device, it does not include one to lock it.