Most times when you take your smartphone out of your bag, pocket, or purse, you probably know exactly what you're going to do with it. Make a call, send a text, take a selfie, browse viral videos on YouTube, or one of the other many things a smartphone can do nowadays.

Security is a priority for many when they first set up their mobile devices. Nobody wants to have a stranger or nosey friend go through their phone and discover risqué photos or embarrassing text messages. These days, the closet is gone—everyone keeps their skeletons in their phones.

Welcome back, my novice hackers! In a recent tutorial, I showed you how to use shikata_ga_nai to change the signature of a payload to evade detection by security devices (firewalls, IDS, etc.) and AV software.

Welcome back, my rookie hackers! Most often, the professional hacker is seeking protected information from the target system or network. This might be credit card numbers, personally identifiable information, or intellectual property (formulas, plans, blueprints, designs, etc.). Most of my Null Byte guides have been focused on getting into the system, but this only begs the question—"what do I do when I get there?"

Time is money, and if your job requires sending out hundreds of generic emails—think "Thank You" notes and sales pitches—you could save days of work by creating templates stored within your Gmail called "canned responses."

LG's arsenal of screen-off and screen-on tap gestures recently expanded into lock screen territory. Dubbed "Knock Code", this feature allows owners of various LG phones, like the G2 and upcoming G3 to unlock their phone with a series of taps on the screen. The most impressive part is that the screen doesn't even need to be on!

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

Once you unlock your bootloader and root, you're left with one more hurdle to overcome, and that's getting S-Off.

A few days ago I finally finished my 2 week journey into trying to get OpenVas to work properly. You all may have noticed that you can't just click the setup openvas in kali and have it working properly.

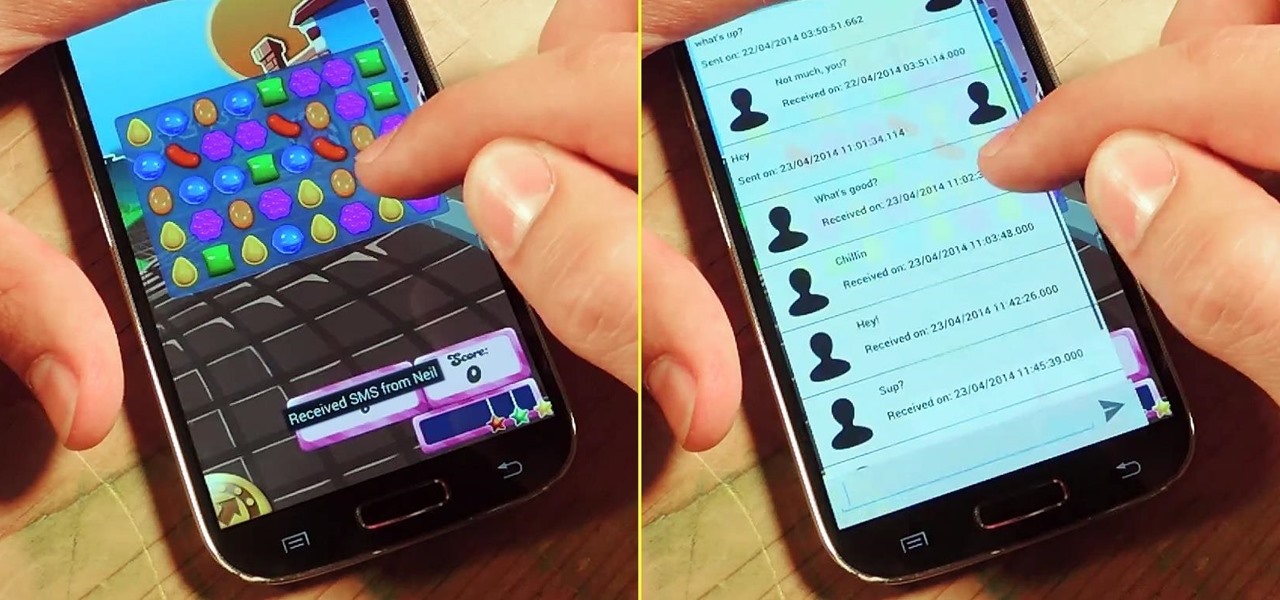
I'm a textaholic, as I've said many times before, but even textaholics forget to respond sometimes. When I'm watching a YouTube clip or devouring delicious snacks in Candy Crush Saga, I'll often ignore incoming texts and forget to respond later.

Whether you've been fully converted or just want a little Apple with your Android, adding your iCloud email to your Galaxy Note 3 is a fairly simple task. Usually, Apple and Android don't play nice, but your iCloud address can be added to your stock email app just like any other email account.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

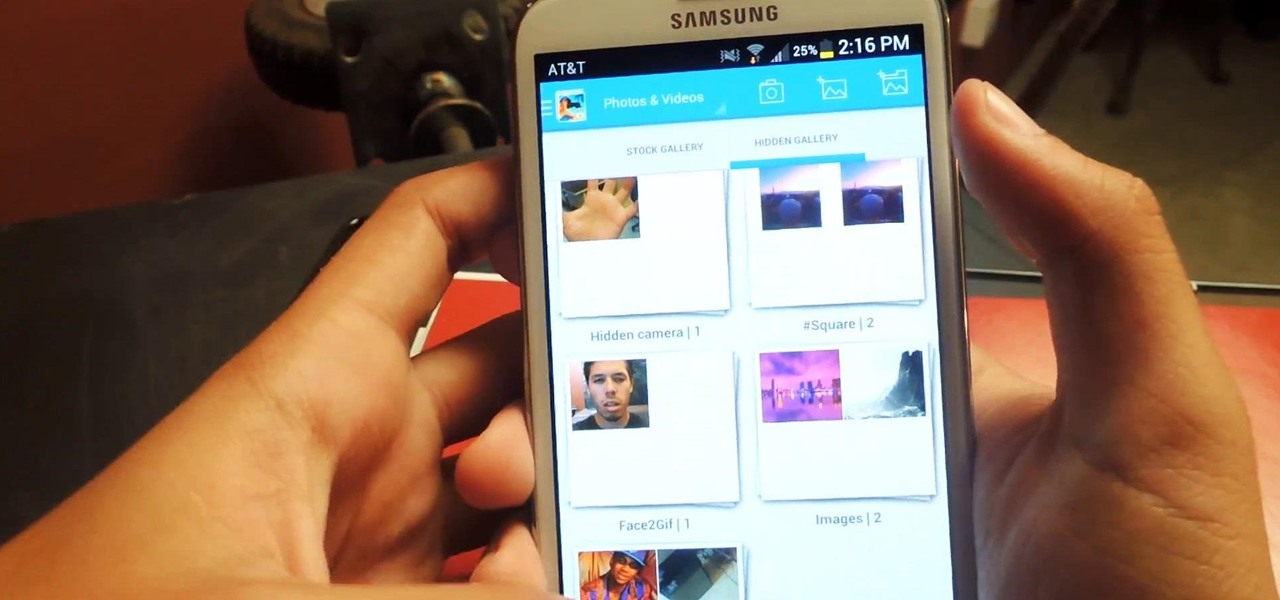
As respectful as you may be, it's hard to resist looking through someone's iPhone when given the chance. You're not trying to snoop around, but it's just too easy to open up apps and read embarrassing emails or find scandalous Instagram follows. It's like looking through a digital diary riddled with deep, dark secrets.

Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

While still extremely awesome, the Samsung Galaxy Gear smartwatch is limited as to what you can download on to it, especially apps. It also doesn't have its own internet access (only Bluetooth), so apps like Instagram, Facebook, and Vine have yet to make their way to the Gear Store.

Regardless of how great your friends and family are, they'll more than likely go through your photographs if they had the chance. Hell, if my friend were to leave his/her phone lying around, I'd go through it—no doubt.

This week, Silk Road was shut down for good when the FBI seized the anonymous online marketplace after Ross Ulbricht, aka Dread Pirate Roberts, was arrested. This comes just two weeks after another illegal marketplace called Atlantis shutdown. However, there are plenty of other black markets hiding within the Deep Web, freely and anonymously accessible using the Tor browser.

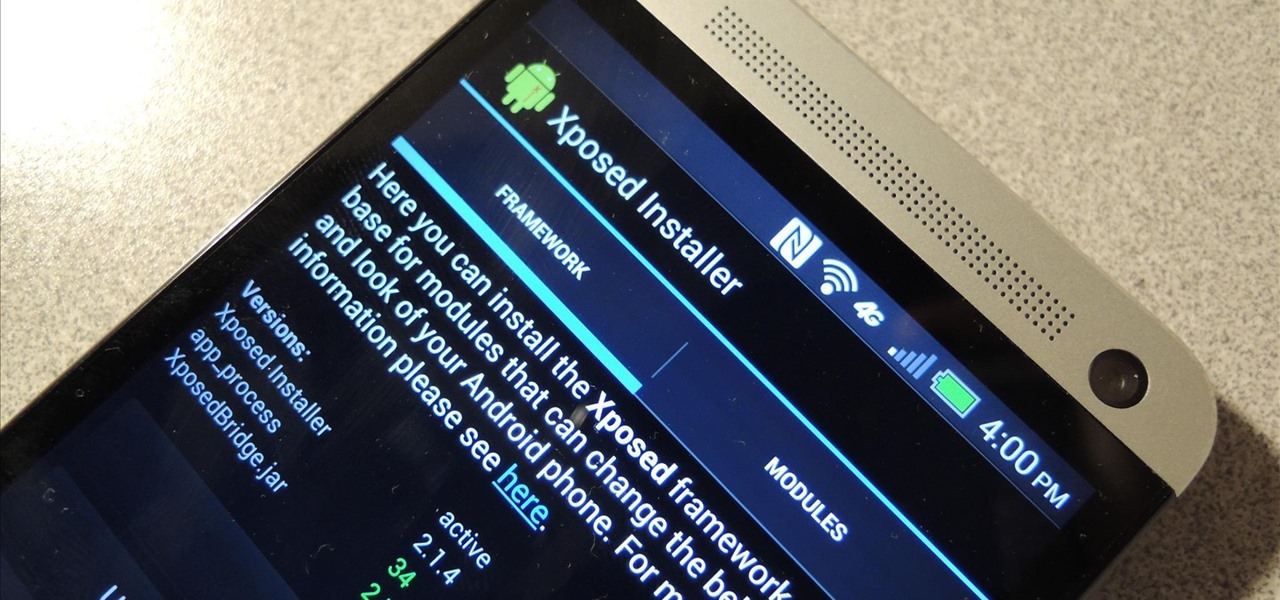
Update: The installation process for Xposed Installer is now dead simple—check out our updated guide!

Nine times out of ten, when you pick up your Samsung Galaxy Note 2, you already know what app you're going to be using. If you only have Swipe to unlock enabled, finding that app is as easy as swiping and locating the app on your Home screen or in the app drawer.

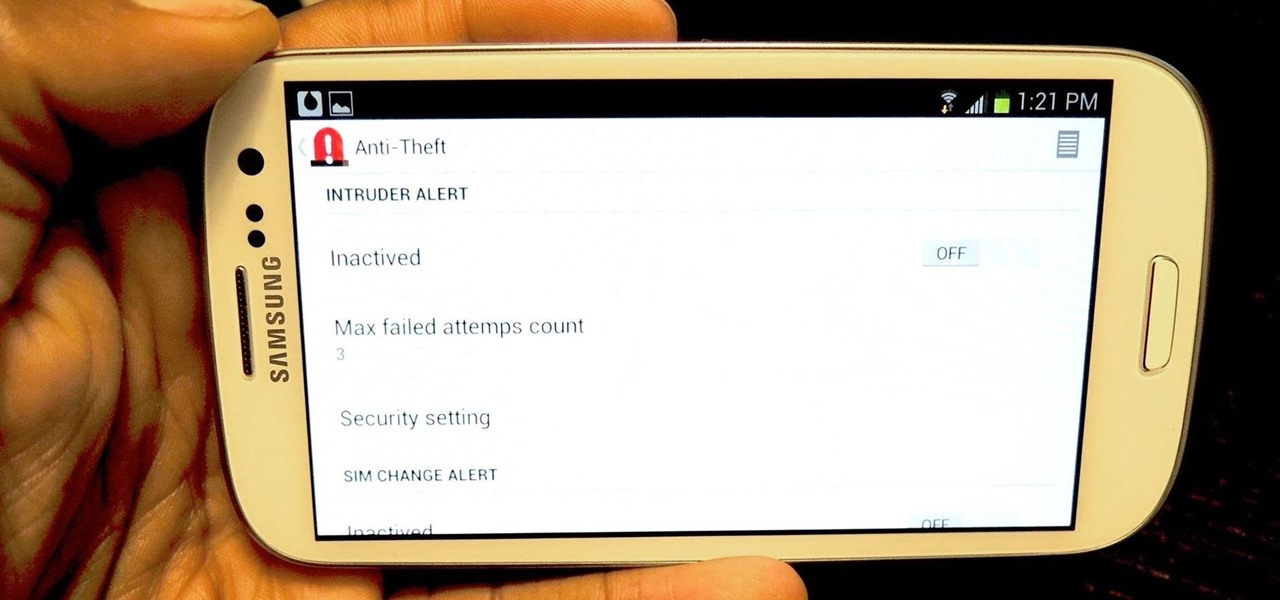
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

Rooting a mobile device may not be a big deal these days, but not being able to root definitely is. Even the Library of Congress, National Telecommunications and Information Administration, and White House can agree on that.

Welcome back, my hacker novitiates! Many of you have written me that you're having difficulty installing and running Metasploit on a variety of platforms. No matter if you're using Mac, Linux, or Windows, I strongly recommend you install BackTrack as your secondary OS, a virtaulization system, or on an external drive. This particular Linux distribution has many hacking and security tools integrated—including Metasploit.

According to WitsView, 8-inch displays will rule the tablet scene this year at 11.9% market share, compared to yesteryear's 2.6% market share. By year's end, it'll be almost 18%.

I recently had my iPhone stolen at public park and did everything I could to locate it, but with Find My iPhone disabled (I know, what an idiot) and no exact address to give to the police, I had about a .00000001 percent chance of getting it back.

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Last weekend, some unlucky Gmail users inadvertently had their email accounts wiped out. Actually, it was 0.02 percent of all Gmail users—or roughly 40,000 of the 200 million who use the email service, due to an "unexpected bug" which affected copies of the data. Gmail does make backup files of everything, so eventually everyone will reclaim their email history. In fact, as of yesterday, Google has successfully restored all information from their backup tapes and has started returning everyon...

Thanks to Yifan Lu, it's been discovered that the operating system running on the Kindle Touch is written mostly in HTML5 and JavaScript, unlike the previous models which used Java. This is exciting, because when a device is hacked or rooted, that means homebrew programs can be run on the device, maximizing its potential and getting the most for your money.

This video tutorial belongs to the software category which is going to show you how to convert a Word document to a password protected PDF file with NovaPDF. Go to NovaPDF and download the program and install it. It is a paid program. Select the word document that you want to convert and select print option. Under the name of the printer you will find novaPDF option. Select this and click 'preferences'. Now click on 'security' and select high level encryption. In the document permissions, sel...

To take apart a PS3, you will need the following tools: Phillips-head screwdriverPliersTiny Phillips-head screwdriversTiny flat-head screwdrivers

Do you like to play hockey but have no idea how to skate? Are you more of a summer person than a winter one? Do you live somewhere where ice is hard to find? Well, then check out this tutorial and learn to play street hockey! Get all the fun of hockey without the cold, icy mess!

Cars are expensive to buy, replace or repair. Check out this video and learn how to avoid the most statistically dangerous parking areas. There is no guarantee that no one will touch your vehicle, but by take precautions you are much less likely to be targeted.

Nothing to wear but have an old scarf hanging around? No problem! In a few easy steps you can transform that boring scarf into a cute, summery halter top!

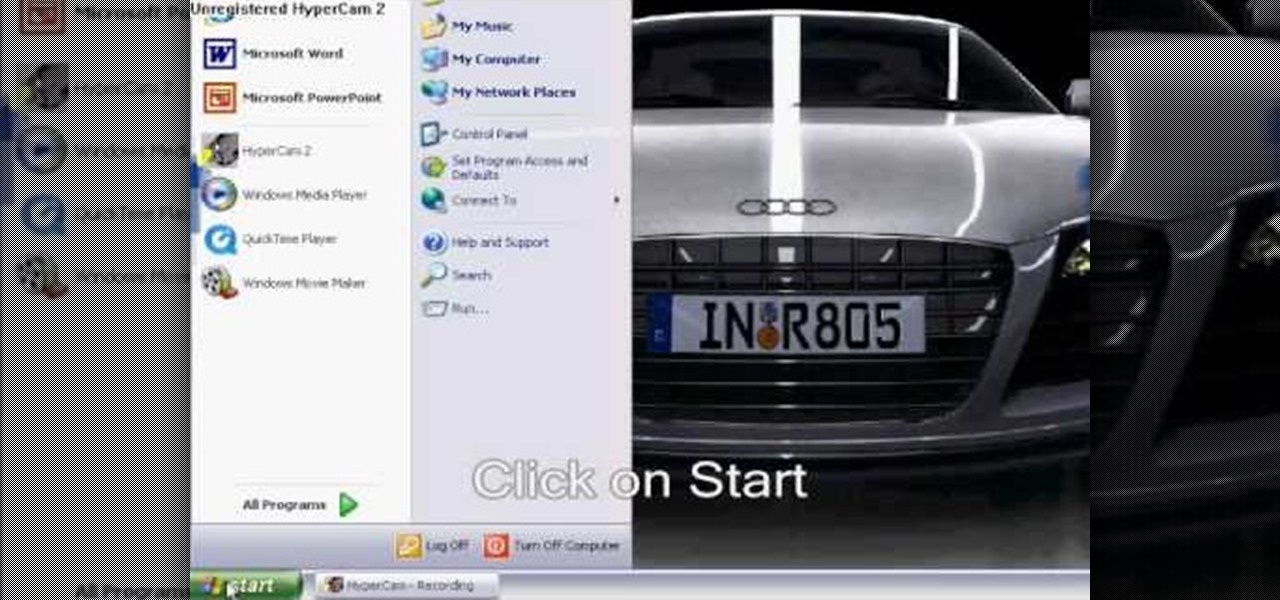
Follow the steps outlined in this video to learn how to connect to XBox Live using a laptop running Windows XP. The first step is to connect the XBox with the laptop by using an Ethernet cable. When they are connected you have to click on Start and select 'Connect To' and then 'Show all connections'. Select both the Wireless Area connection and the Local area connection icons by highlighting both of them. To do so hold the Ctrl button until they are both highlighted. At this point right click...

Stan shows an easy way to see and clean the files that are hogging hard drive space in the computer using a free software called "windirtstat". Now enter the following address in the web browser "windirtstat.info" and scroll down the page until you get the downloading and installing section. Click on the link "windirtstat1.1.2Setup(Ansi&Unicode)" which will be right after the "for all flavors of windows" this will direct you to "SOURCEFORGE.NET" download creations. This will ask you to save t...

Keep your house safe! Learn how to replace door locks in this free home security video from our professional handyman.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

There are countless ways in which a talented and trained programmer and tech pro can earn a lucrative living in an increasingly data-driven age — from writing and creating apps and games to working for a cybersecurity firm or even the federal government.

Despite Samsung's long running support for Wi-Fi Direct, most users still struggle to transfer files between their devices. Whereas Apple has AirDrop, Samsung's previous solution wasn't so obvious. With the Galaxy S20 and Galaxy Z Flip, Samsung hopes to correct this with "Quick Share," a file transfer system that still uses Wi-Fi Direct but makes it easier to use.