New statements from Apple make it clear that they do not believe a hacker, or group of hackers, breached any of their systems. This comes after a recent report from Motherboard that a hacker gang called the "Turkish Crime Family" is threatening to remotely wipe up to 559 million iPhones by April 7.

During the last few months, WhatsApp's Google Play Store ratings have been tanking—all the way down to an average of 3.4 stars from the instant messenger's usual average of 4.1. Within the last week, though, WhatsApp has received thousands of seemingly fake 5-star reviews that have bumped up the company's overall average to a 4.4.

Making a NANDroid backup can save you from all sorts of flashing-related mishaps and accidents. Bootloops, SystemUI crashes, accidental wipes, bad ZIPs, or a dozen other possibilities—there's almost no condition in which a NANDroid is unable to correct problems with your device. However, recent changes to Android have created an almost paradoxical situation where restoring a NANDroid can actually lock you out of your phone.

ProtonMail has long been the favorite of journalists and security-conscious professionals, with Edward Snowden the most famous example. But these days, everyone cares about anonymity, so it's no surprise that ProtonMail currently has over 2 million users. And now the service is even better.

Despite the availability of a vaccine against it, almost 50% of men aged 18-59 in the US are infected with the human papillomavirus (HPV). Why?

A scary piece of malware just got a lot more terrifying this week. Security firm Comodo reports that "Tordow," a banking Trojan first uncovered in September 2016, received a massive update this December.

One of our favorite features on the Pixel Launcher is its App Shortcuts, which work a lot like Apple's 3D Touch for iOS or Huawei's Force Touch. Instead of using pressure sensitivity to call up static and dynamic shortcut menus for apps, Launcher Shortcuts relied on a simple long-press. Now, in the Android 7.1 update for Pixels, there's an update to App Shortcuts that let's you pin shortcut options directly to your home screen for even quicker access.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

Google and Microsoft have both established platforms and hardware for emerging digital realities, but Apple, true to form, hasn't had much to say on the subject. They've shown interest in augmented reality, and we've seen patent filings that indicate research and development, but a recent rumor points to that research ending up in your car instead of a rose gold headset.

Android 7.0 Nougat has finally arrived—well, technically, it's in the process of arriving on Nexus devices across the globe. Google uses a staged rollout system to prevent excessive server load when issuing Android updates, which means even though Nougat has made its official debut already, you might not get that "Update available" notification for another few weeks.

When the Samsung Galaxy S7 and S7 Edge came to market in 2016, they were universally praised as being the pinnacle of Android smartphone design, even topping Consumer Reports' smartphone ratings.

Swipe keyboards such as GBoard, SwiftKey, TouchPal, and Swype are handy for quick one-thumbed typing on an iPhone, but Microsoft upped the game with its experimental Word Flow Keyboard. In short, the keyboard fans out to occupy the natural range of your thumb, where you can type or rely on predictive swiping.

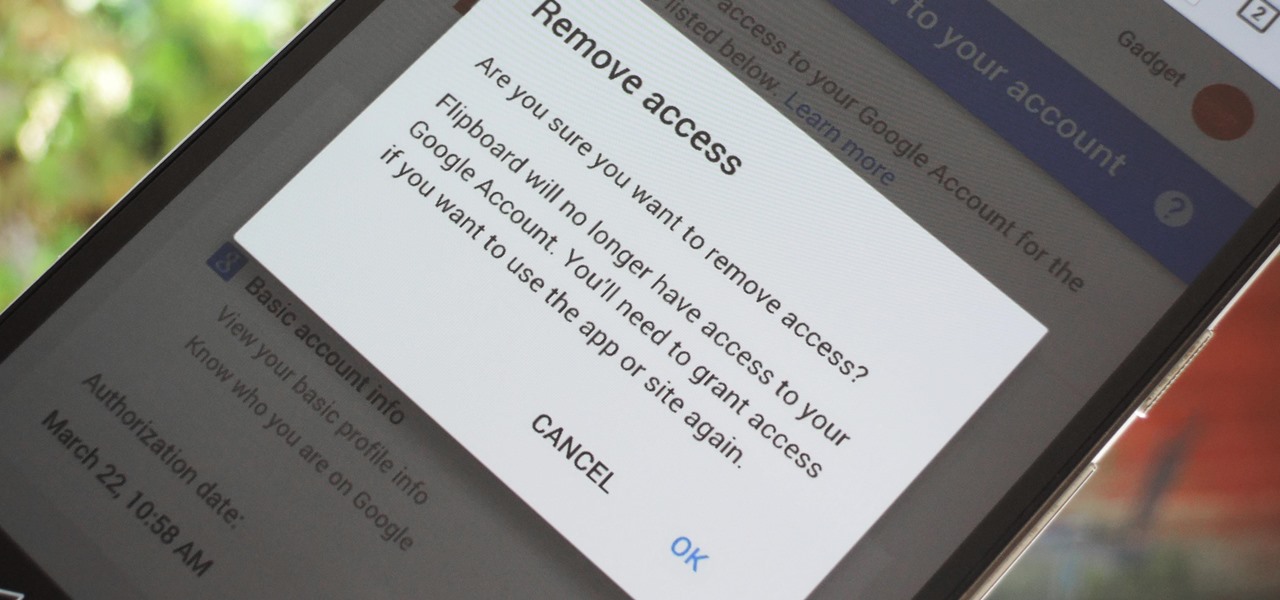
Many apps and services that are available for Android can only work if they have access to your Google account. While you're setting up one of these apps, you'll see a popup that says something like "This app would like to access your Google account," and the options are "Accept" or "Cancel." Of course we tap "Accept" here to ensure that the app will work properly, but what are the long-term repercussions of doing that?

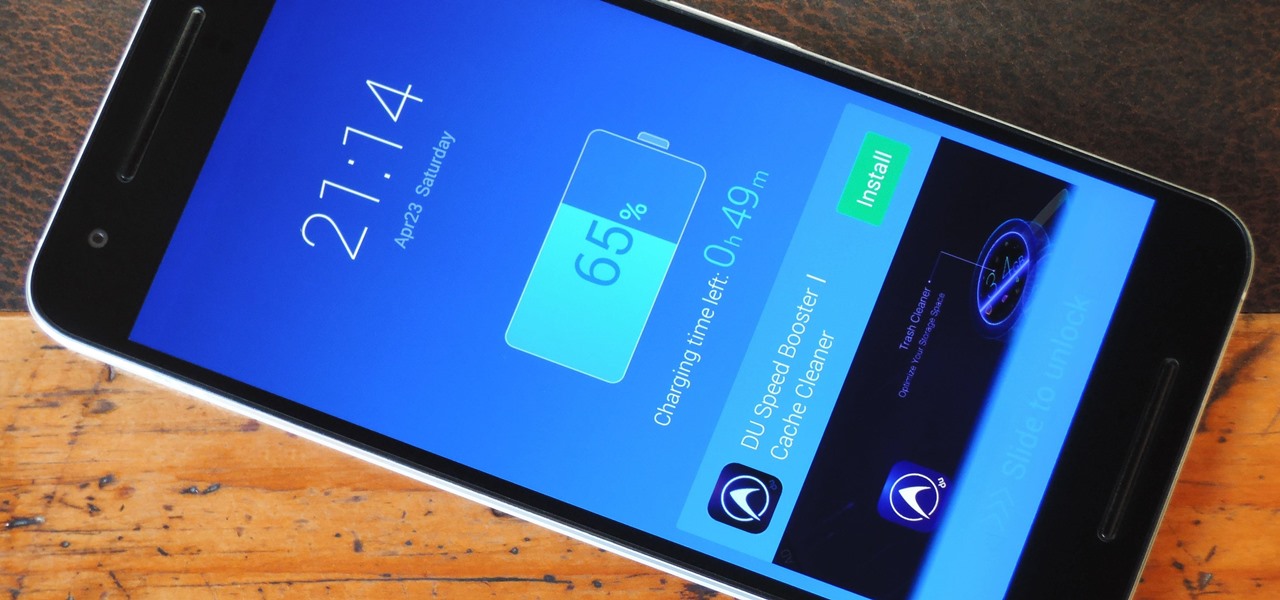
There was a somewhat recent outbreak of malware on Android, and it came from an unlikely source—the Google Play Store. Several established apps have received updates a few months ago that contained an unwanted add-on called either DU Quick Charge, DU Battery Boost, DU Boost Charge, DU Speed Charge, DU Speed Booster, or another name starting with DU.

With the FBI getting access to iPhones, and apps like Waze being used to track people's locations, you've got to wonder just how safe and secure your smartphone is... or isn't. When you consider everything you do on your phone, from taking and sharing pictures to mobile banking, keeping your information safe is a crucial step that may seem out of your hands.

The desktop browser market has some stiff competition going on, but Opera has always been able to maintain its market share by offering innovative features such as a data saver option. With over 350 million users, it's safe to say folks are appreciative of the efforts being made by the web browser's development team.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

Without explicit cooperation between Apple and the US government, authorities could still be monitoring Apple users. According to The Information, Apple is worried the servers it has been using might be bugged. We already know the NSA intercepts equipment to install backdoors, so this is a legitimate concern.

The Stagefright exploit, which allowed for malicious code to be embedded in files on your device, is now very real in the form of Metaphor. Developed by software research company NorthBit, Metaphor is their implementation of exploits to the Stagefright library, and when executed, can access and control data on your device.

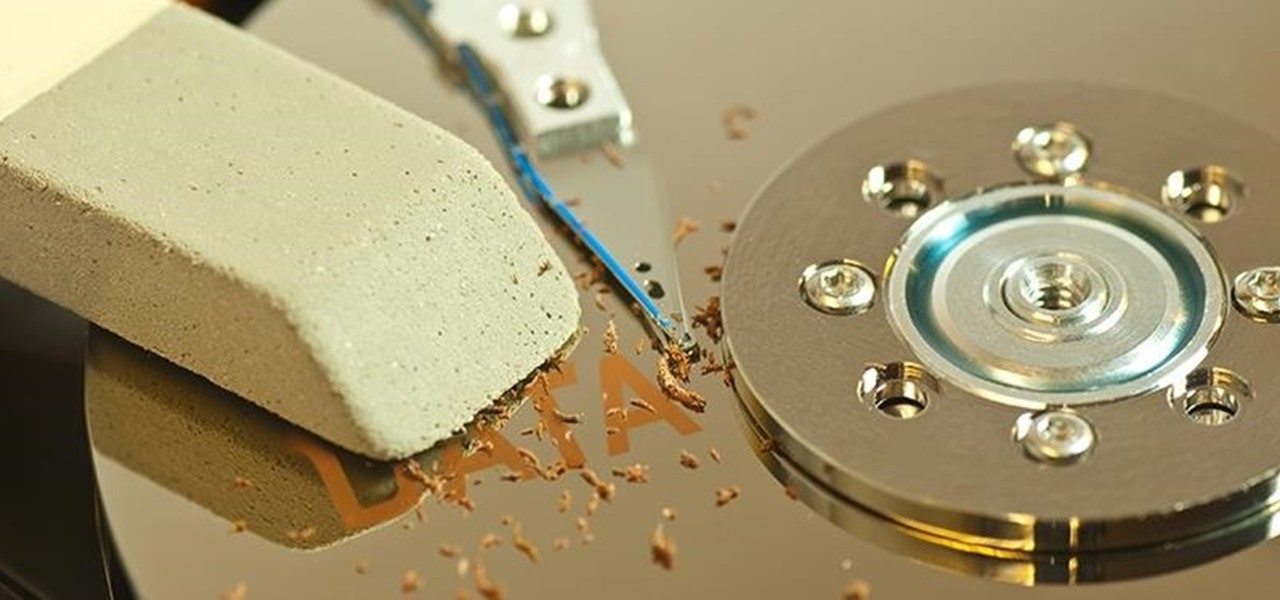
When you delete a file, Android doesn't actually remove it from your storage drive—instead, it simply marks that space as empty and pretends the file doesn't exist anymore. But deep down inside, the file that you originally wrote to that location is still physically there, at least until you randomly happen to save another file on top of that same spot.

One of the best uses for an old Android device is to turn it into a security webcam that can be accessed over the internet. But most of the time, this is a rather difficult process, because existing apps usually require you to mess around with network settings and configure a personal web server.

Welcome back, my greenhorn hackers! Over the years, I have written many articles here on Null Byte chronicling the many the hacks of the NSA, including the recent hack of the Juniper Networks VPN. (By the way, my speculation in that article has proven to be correct. The NSA did embed a backdoor on those devices.)

If you're experiencing issues with an app or custom ROM and would like to report your problem to the developer, there's no better way to do it than by capturing a logcat. Android keeps track of all the commands that have been executed by various apps and services, which means that when something goes wrong, the error is clearly shown in this so-called logcat.

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

What's up, peeps? In this quick tutorial, we will be looking at structs, a special kind of data type.

Before we begin learning about another vulnerability, we are going to explore printf in a bit more detail. This will be quick little tutorial.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

What's up guys! It's time to discuss strings in more detail. Review

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

The Fire TV Stick, as well as the Fire TV, may be limited by Amazon's fight on piracy, but after a quick sideloading of Kodi, the floodgates are back open with the freedom to stream just about any video or song you want.

The Xposed Framework was just recently made available for Android Marshmallow, but everything isn't quite back to status quo just yet. Sure, some Xposed modules function properly, but others are a bit buggy, and several don't even work at all. This is mostly a result of changes to the Android system that Lollipop modules relied upon, and such modules will need to be updated for Marshmallow compatibility.

You need a good microphone on your computer in order to make audio recordings, voice chat, or use speech recognition. However, not every computer comes with a built-in mic, and not every built-in mic works great.

welcome back my masters , teachers and classmates , in this second part of this 0-day series we will learn the basic of fuzzing, and i bought some gift for nullbyte(a 0 day vuln that will be released today exclusively on null-byte) .

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

Ideas can be a fleeting thought, just like a shooting star that appears and disappears within a brief moment. So when you're inspired and have an awesome idea, it's important to jot it down as soon as possible, otherwise it may vanish from your memory for good.

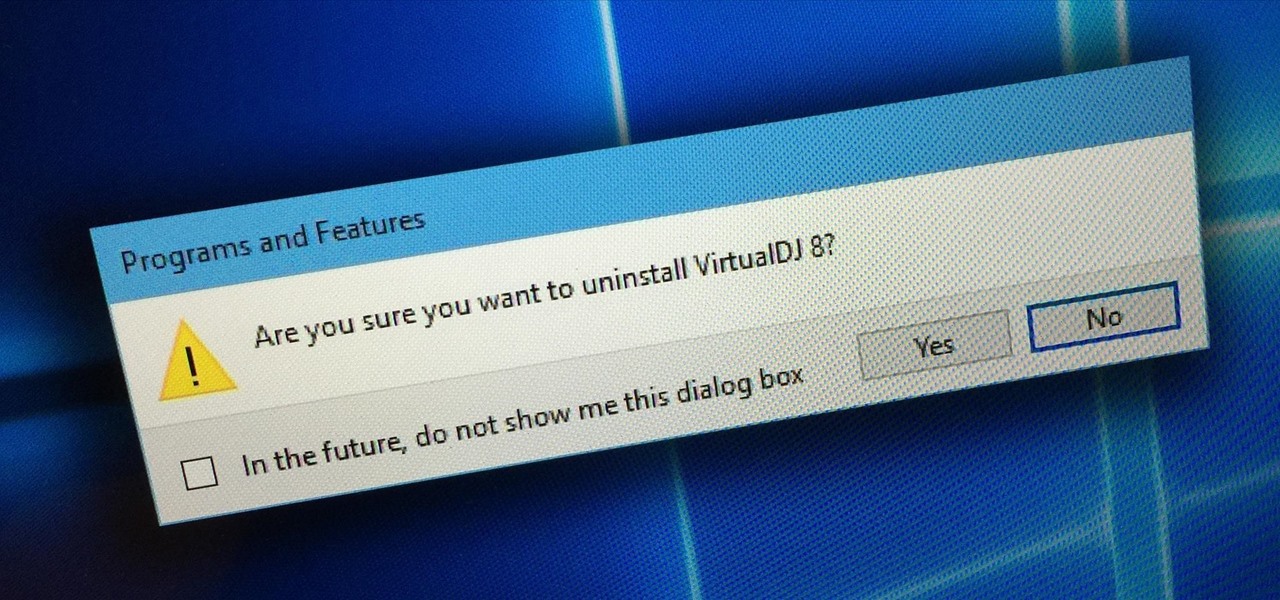
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.