
How To: Make your own clay
Put your imagination into solid form by working with clay. Now all you need is the clay. No need to buy it at the store when you can make all the clay you like at home. Clay is a fun medium for adults and kids to work in.


Put your imagination into solid form by working with clay. Now all you need is the clay. No need to buy it at the store when you can make all the clay you like at home. Clay is a fun medium for adults and kids to work in.
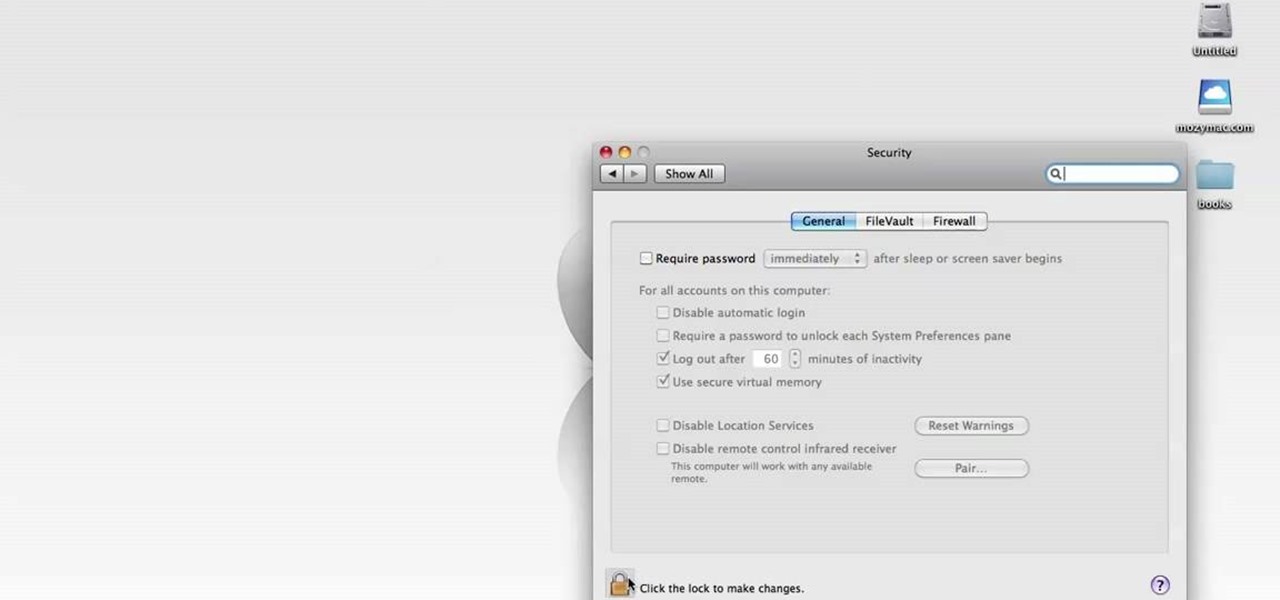
Every new Apple computer ships with an Apple remote, which can activate the Front Row program and let you play music, view photos or watch videos when you are away from your computer. However, Apple remotes will connect to all nearby devices, so people with multiple Macs or iPods close to each other, may have trouble controlling them with the remote. In that situation, it's wise to disable the Apple remote connection on the devices you do not want to connect to.
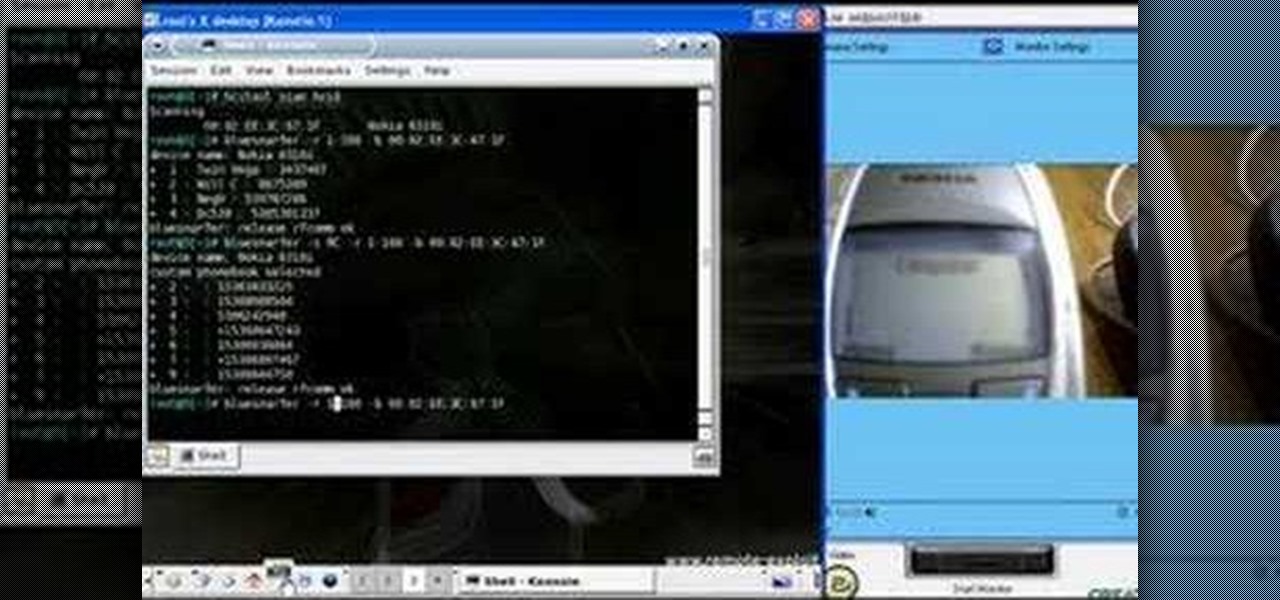
Check out this video tutorial to see how to bluesnarf a Nokia 6310i handset (cell phone). What is Bluesnarfing exactly?

In these home security and safety videos, learn how to upgrade your house in some important ways. Our expert, Jon Olson, will show you how to secure your windows and sliding glass doors, some of your home’s most vulnerable entries, with bar locks. Learn how to install a door guard latch to keep small children from getting out, as well as a peep hole to see who’s at the front door. Finally, get some important fire safety tips and learn how to install smoke detectors for your home.

In this series of video clips you’ll learn how to install a keyless entry deadbolt security system in your home. Expert locksmith J. Daniel Nell takes you through the entire process step-by-step, showing you what tools you’ll need to complete the job, how to remove your old deadbolt lock from the door, how to install the electric wiring, program and operate the keypad, and offers tips on maintenance and more.

In this video series, learn how to tackle a fairly simple do-it-yourself home improvement project that can significantly strengthen your security system. Our expert, Daniel Nell, will show you how to install a single-cylinder deadbolt lock on any door in your home. Watch these step-by-step video clips and get tips on how to measure for the deadbolt, drill the hole, install the strike plate, and connect the latch.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

If you prefer to use Google or another search engine for everyday browsing in Safari but would also like a more secure browsing experience for all your secret searches, there's a simple way to switch between them quickly while also adding additional layers of security on top of your already clandestine browsing.

Apple just released its iOS 16.6 update for iPhone on July 24. When you install the new software, it may look like there's not much to it since Apple doesn't include any features in the release notes beyond "important bug fixes and security updates," but a few new features are hiding within.

One UI has an exciting privacy feature that lets you lock apps, photos, videos, and files on your Galaxy device behind Samsung's defense-grade Knox security platform. Only you can unlock it using a pattern, PIN, or passcode, or with biometrics like fingerprint and iris locks. It's like having a safe built right into your smartphone, and it couldn't be easier to set up.
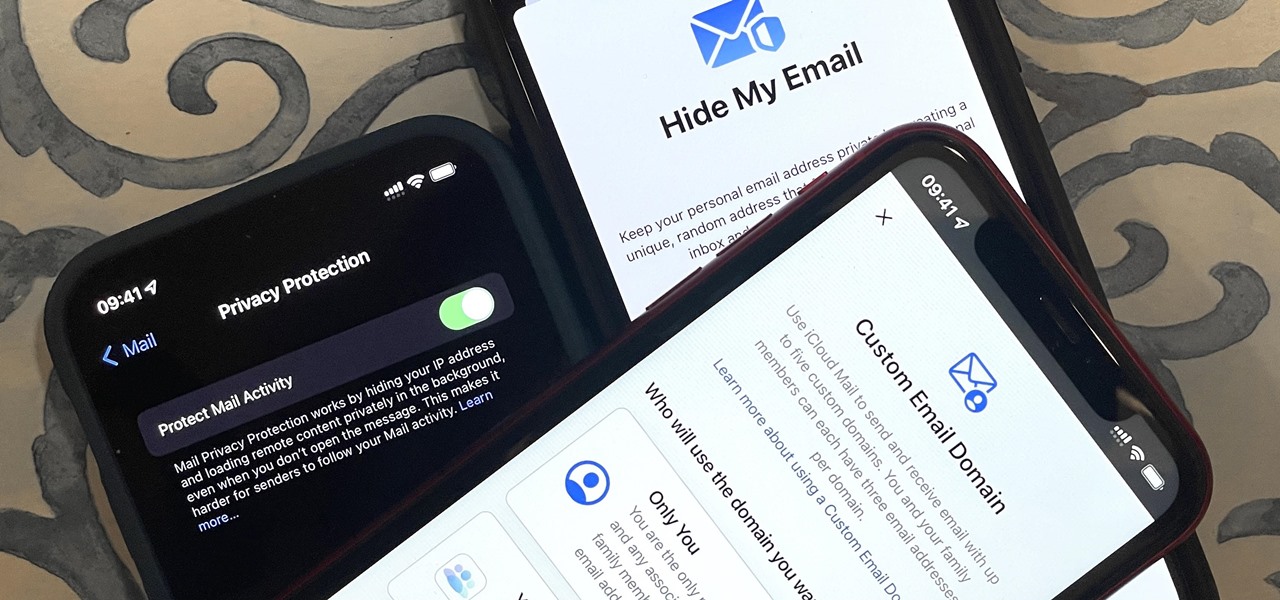
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

On Monday, the social media giant Facebook suffered a massive outage that, as of this writing, is still in effect.
Pretend you're a phone thief for a moment. You might be a pickpocket or a stickup kid, but you're in possession of other people's phones on a regular basis. Now ask yourself this: what's the first thing you do after you steal a phone?
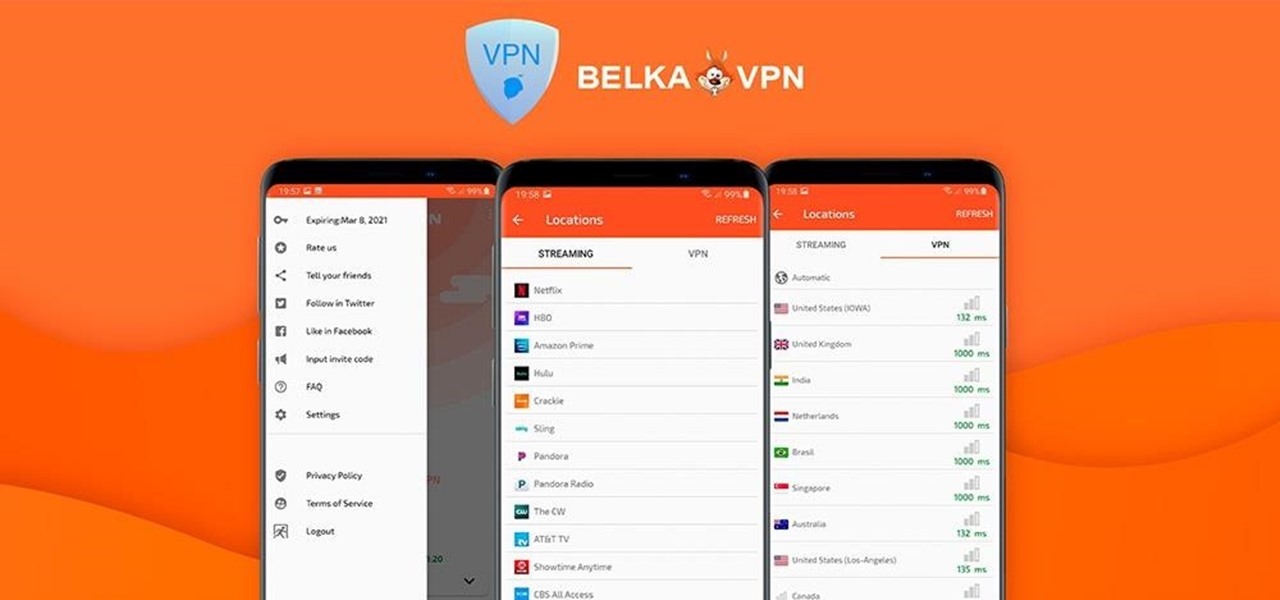
If you're concerned about your data ending up where you don't want it online, then a VPN is something you'll want to consider. A VPN can prevent your bank account information from leaking, your data from being taken directly from your device, and it doesn't come at the cost of any of the convenience we've grown to expect and require from the internet.
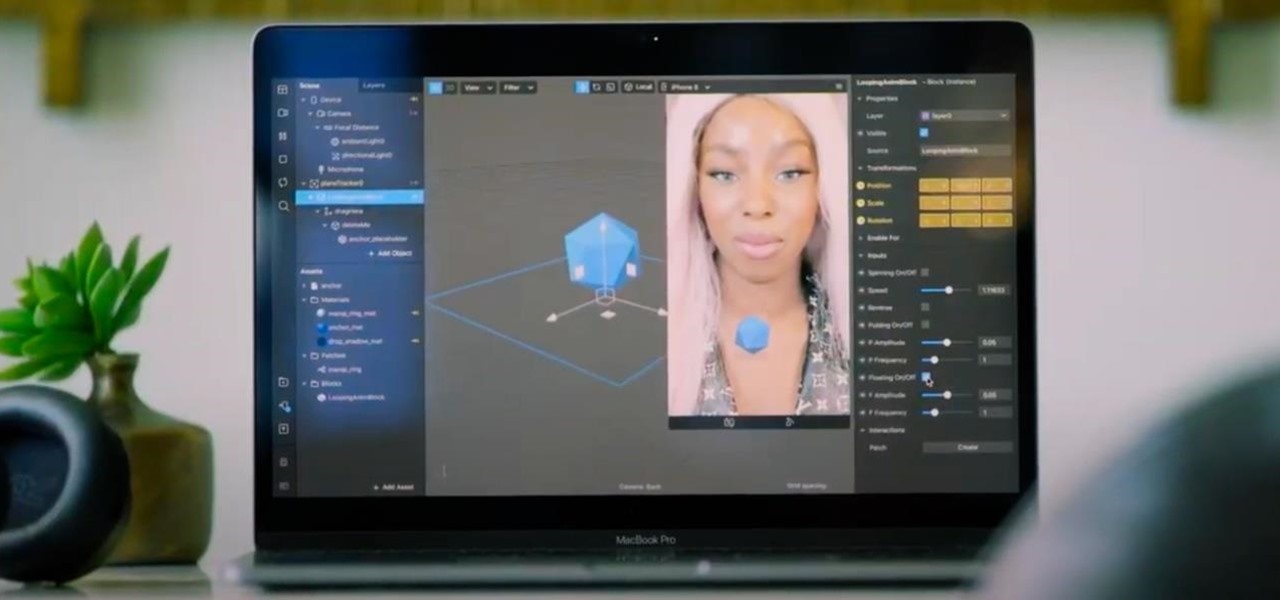
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

There's no better time to reset, improve yourself, and develop new skills than at the start of a brand new year, where you're stuck at home with nothing better to do. Thankfully, this amazing deal on The 2021 Career & Self Development Master Class has come at a perfect time. Right now, it's on sale for just $39.99 — that's a whopping 98% off the regular price of $2,000.
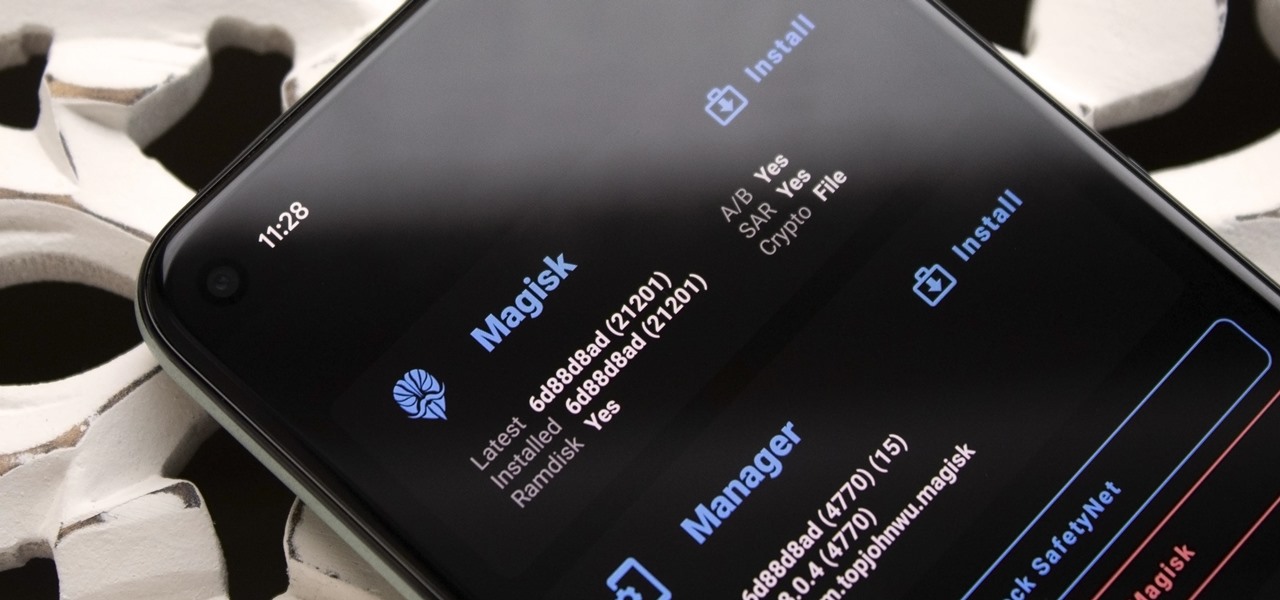
Okay, so you rooted your Android phone .... now what? There are a few ducks you need to get into a row, like backing up your stock boot image, getting SafetyNet sorted, and improving security with biometrics. But there are also awesome root mods waiting for you — just don't get ahead of yourself.

After updating to iOS 14 or getting a new iPhone with iOS 14 preinstalled, you'll notice orange and green dots that occasionally appear at the top of your iPhone. These dots appear on all supported iOS 14 devices, from the iPhone 6S to the iPhone 12 Pro Max, and are there to protect you, but how?

Amazon Web Services (AWS) offers over 200 services, including networking, computing, storage, analytics, blockchain, mobile, and developer tools. Not surprisingly, numerous companies rely on AWS's massive infrastructure. Instead of building their own server farms, they rent space and computing power from AWS's secure and robust system.
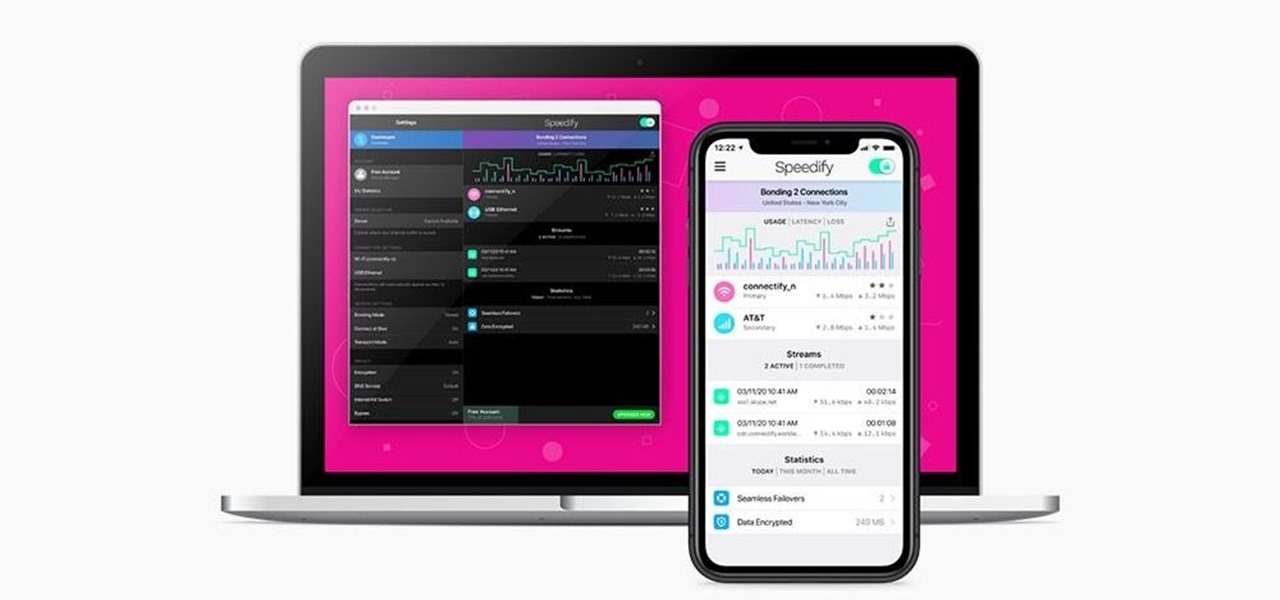
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?
It can seem as though there's a virtually endless number of essential programming languages to choose from these days. And complicating matters even further for aspiring or even established programmers, developers, and hackers is the fact that most languages are a bit esoteric and suited for only a certain number of relatively finite tasks.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

TWRP has been the king of custom recovery on Android for years now, thanks to device compatibility and core features. But there's a new player in town — at least, for OnePlus devices — and it's got a lot of useful features that might finally get you to ditch TWRP.
Google's feature drops for Pixel devices have added fun and useful new abilities, such as AR effects for Duo, Call Screen automation, scheduling Dark Mode, and Quick Access Wallet for Google Pay, that are exclusive to the company's line of smartphones.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

Penetration-testing frameworks can be incredibly useful since they often streamline certain processes and save time by having a lot of tools available in one place. Of course, the most popular pentesting framework is undoubtedly Metasploit, but there are many others out there that cater to particular needs. For auditing web applications and servers, Tishna comes in handy.

In the event of an emergency where you can't answer for yourself, trained professionals can view your Medical ID on your iPhone to learn about your medical situation, granted that you have created one. But that's not all your Medical ID can do. With a new feature, iOS can share your Medical ID data automatically with first responders when you place an emergency call.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

Netflix has offered its beta program officially through the Play Store for some time now. Still, the issue most of us face — the beta availability is always scarce. Without getting lucky and landing a beta spot early on when the gates were open, there wasn't much you could do about it. However, there's now a brand new method you can use to sideload the Netflix beta app and join in on the fun.

Hacking web applications can sometimes be challenging due to the sheer amount of moving parts they possess. At the core of these apps are HTTP requests and parameters, but these things are often concealed from the user, due to security reasons, convenience, or both. However, a tool called Arjun can be used to discover hidden HTTP parameters in web apps.

If you haven't used a Samsung device in a few years, the Galaxy S20 series will be your first taste of One UI 2, the skin running on top of Android 10. Although One UI is on the heavier side, it has loads of exciting features that go beyond what's offered in stock Android.

It feels like just yesterday Apple unveiled iOS 13 to the world, introducing game-changing features like system-wide dark mode and enhanced editing tools in Photos. But WWDC 2020 is rapidly approaching, which means iOS 14 is as well. As it turns out, we don't need to wait for an official announcement to get an idea of what new features and changes are coming to iPhone this year.

If you have an Android device that Netflix does not support, you can check the Play Store and it simply won't be there. But just because you're unable to download it through official means doesn't mean you have to live without Netflix since there's a way you can sideload it manually.

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.
PayPal is one of the most popular payment systems across the globe. It makes payments fast, easy, and secure, and with 250+ million users, it's not going anywhere. If you're new to the online service, one of the first things you should learn is how to add your bank account, credit card, or debit card to PayPal, and make your life easier when it comes to online payments and withdrawals.

While consumer-grade smartglasses are the holy grail for tech companies, smartglasses maker Vuzix knows where its bread is buttered, and that's in the enterprise segment.

No operating system is stricken with as many vulnerabilities as Windows, and it's often a race to release the latest patches to fix things. From an attacker's point of view, knowing which patches are present on a Windows machine can make or break successful exploitation. Today, we will be covering three methods of patch enumeration, using Metasploit, WMIC, and Windows Exploit Suggester.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.