In this video tutorial, viewers learn how to set and encrypt your Wi-Fi password using WPA on a Linskys router. Begin by opening your web browser and type in the address: Click Enter. Now type in your user name and password, and click OK. Then click on the Wireless tab and select Wireless Security. In the Security Mode drop-down menu, select WPA Pre-Shared Key and then type in a password under WPA Shared Key. Finish by clicking on Save Changes. This video will benefit th...

Installing a deadbolt is a relatively quick and simple do-it-yourself project. You can make your home much safer – and less attractive to thieves --- with a little effort and a few simple tools.
Hi fellows! I finally decided to join this forum, which I find very interesting and has some great contributions into the tech and security space, appreciate it!
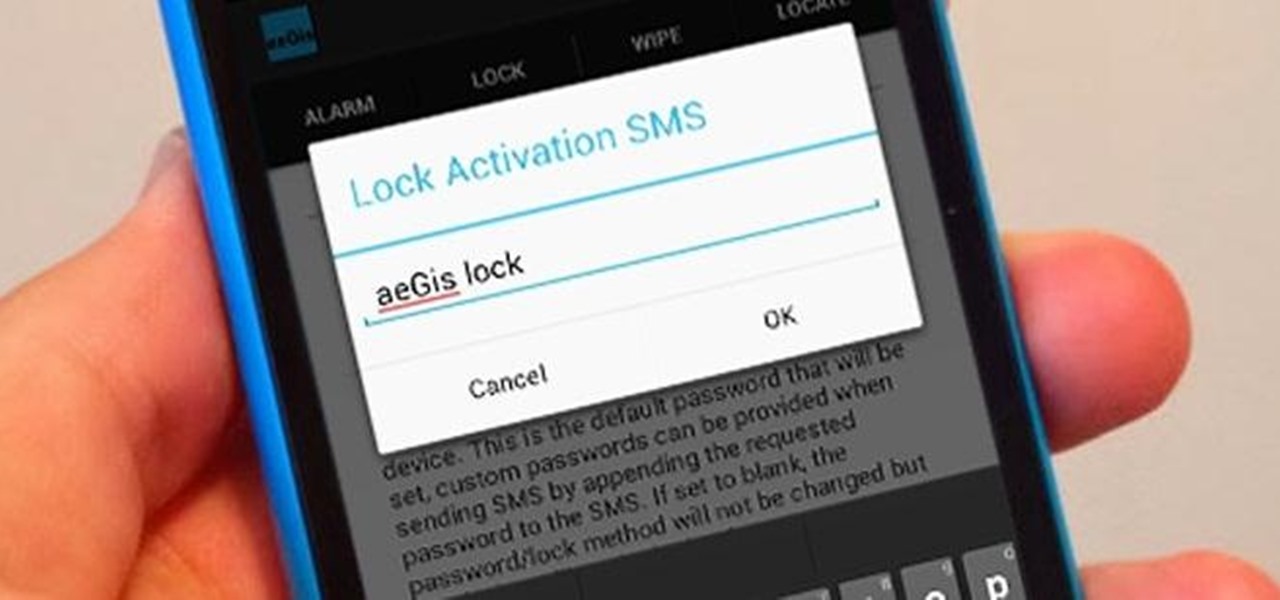
The great thing about security apps (other than the obvious) is that there is an abundance of them littered throughout the Google Play store. Cerberus, Got Ya!, Avast! Mobile Security, Norton Security & Antivirus, and Android Lost Free are just a few of the gems you can find in the plentiful sea of security apps for Android. Once in awhile, though, a new security application comes along that stands out from the rest, like AeGis.

Check out this computer software tutorial from Dummies.com. This tutorial is made for PCs. Increasing a PC's Windows Vista security is easily done by turning on the Windows firewall and Windows Defender. There's no need to download the firewall or Defender. Protection against spyware and other security risks increases upon enabling these free, built-in Windows solutions. Enable the Windows firewall and Windows Defender.
In late 2011, representative from China, Russia, Tajikistan and Uzbekistan submitted a proposal called the International Code of Conduct for Information Security (ICCIS) to the UN Secretary General Ban Ki-moon that called for international consensus of a global set of rules and regulations that standardize information flow on the internet.

People sometimes ask me about the IT industry here in the states. These folks are usually either trying to get into a certain field, or looking to switch or move into another one. Right now, you may currently be a Computer Science major that will be graduating shortly and are interested in the current state of IT security.
The department of Homeland Security released a list of 'words and phrases' it uses to search social media for terrorism, and whatever else they decide they are looking for that day. Read some of these. A few are obvious "bomb, nuke" and some "target, event" are just down right vague. More reasons to watch what you do on the Internet. You are not the only one watching!

UK-based artist Matthew Nicholson is a man of many talents: designer, photographer, professional free runner and papercraft engineer—and in the latter of which, he generously posts free downloadable DIY kits for your folding pleasure.

Have an old-school tabula recta lying around? No? Then just print out the chart below. Nothing ensures better password security than this centuries-old cipher technique. Here's how it works, via Wikipedia:

The end of Daylight Saving Time means two things: a little less light and, as a result, a little less security. This CCTV lamp will give you more of both. And in the nick of time! We fall back to Standard Time at 2 AM on Sunday, November 7th. Better get building!

Four key Syrian military officials including Defense Minister Gen. Daoud Rajha and President Bashar al-Assad’s brother-in-law Assef Shawkat, who served as his deputy, were killed at a top-level meeting in central Damascus. Syria's top security ministers slain in Damascus bombing — RT.

In this video tutorial, viewers learn how to password protect their files. This task can only be done on a Windows computer. Begin by creating a Microsoft Word document. Simply right-click on the desktop, go to New and select Microsoft Word Document. Then double-click on the document and create your text document. Now to save it, click on File and select Save As. Name the file. Now click on the Tools drop-down menu and select Security Options. Then type in a password, reconfirm the password a...

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...

This turon (banana lumpia) is one of my favorite meriendas (light meals), and it's so easy to make, even a child can do it! It's a must try, especially if you can't think about something to cook. So, for all the diehard banana fans, this is for you.

Have you ever noticed that whenever you setup your voicemail account after getting a new cell phone number, it asks you to create a security pin to access your voicemail from other phone lines?

Have an HTC smartphone? Chances are that some of your stored personal data has been hijacked by malicious apps on your device. Android apps that have permission to access the Internet, which is pretty much every ad-supported app out there, can snag valuable information such as email addresses, location history, phone logs, text messages, and more.

Since its inception in 2007, the Pwn2Own computer hacking contest has been challenging the vulnerability of mobile phones and web-related software. In 2010, the fruit of two full days of hacking came down to the exploitation of the following web browsers: Safari 4 on Mac OS X, Internet Explorer 8 on Windows 7, and Firefox 3.6 on Windows 7. The winners walked away with the successfully hacked computer, plus a cash prize, but they left one Godly browser intact: Google Chrome. Even the savviest ...

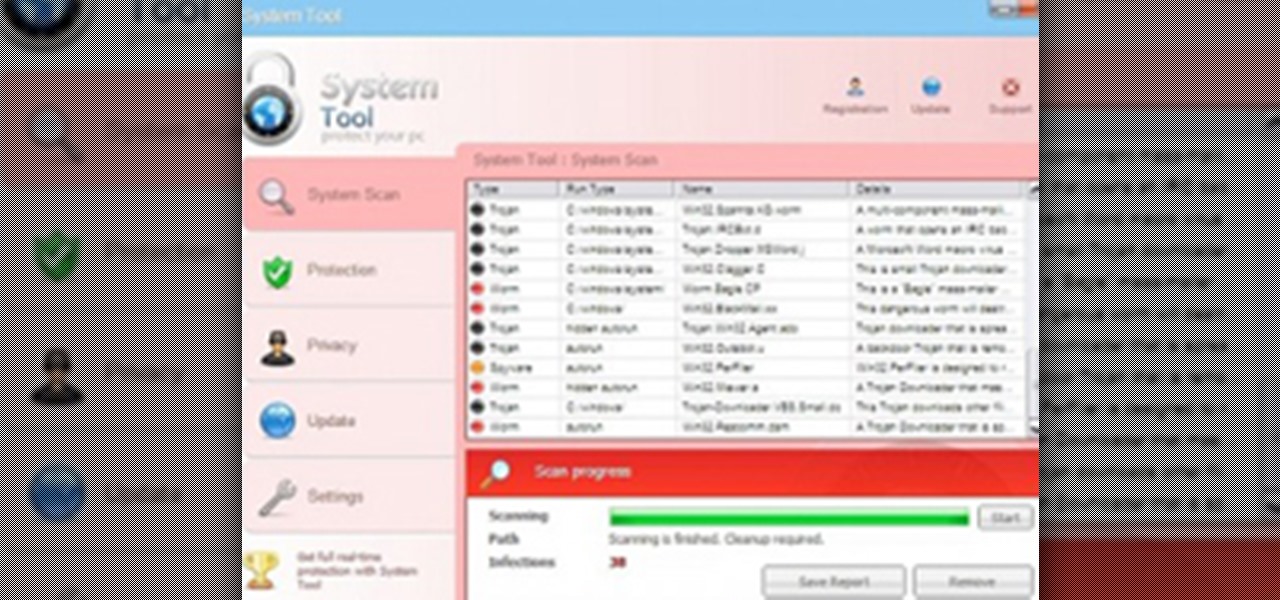
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

There are so many hackers around these days, and they are becoming very smart. So smart that they have successfully taken down many government websites. The most recent attack was on the Department of Justice (DOJ). To read about the history of these hackers, check out Wikipedia.

Backtrack 5 is a Security Essentials Backtrack is a suite of tools to help with Penetration of any Network, Unix, Linux, or Microsoft Based. Backtrack 5 is good for WEP & WPA hacking and penetration testing.

Screw gaming, let's get to the serious stuff! Here's an amazing video of a Kinect hack that lets one see what its camera sees - in 3D.

Life is getting more and more convenient. You can pick up a wireless signal at nearly any coffee shop these days (Starbucks is now officially free in every location across the nation), as well as airports, libraries, hotels and more. However, along with this convenience comes the risk of security breach. Passwords. Emails. Account numbers.

Xeni visits the offices of the Electronic Frontier Foundation and speaks with Jake Appelbaum and Bill Paul, two of the authors of a security research paper that shows how your computer's memory can be tricked into revealing data you thought was safely encrypted, and out of the reach of others. Hack into encrypted computer data.
While following a tutorial on python recon tools, I found a new way to access the command prompt on a school network. While there are other ways of bypassing security, it's nice to learn use Python's OS library.

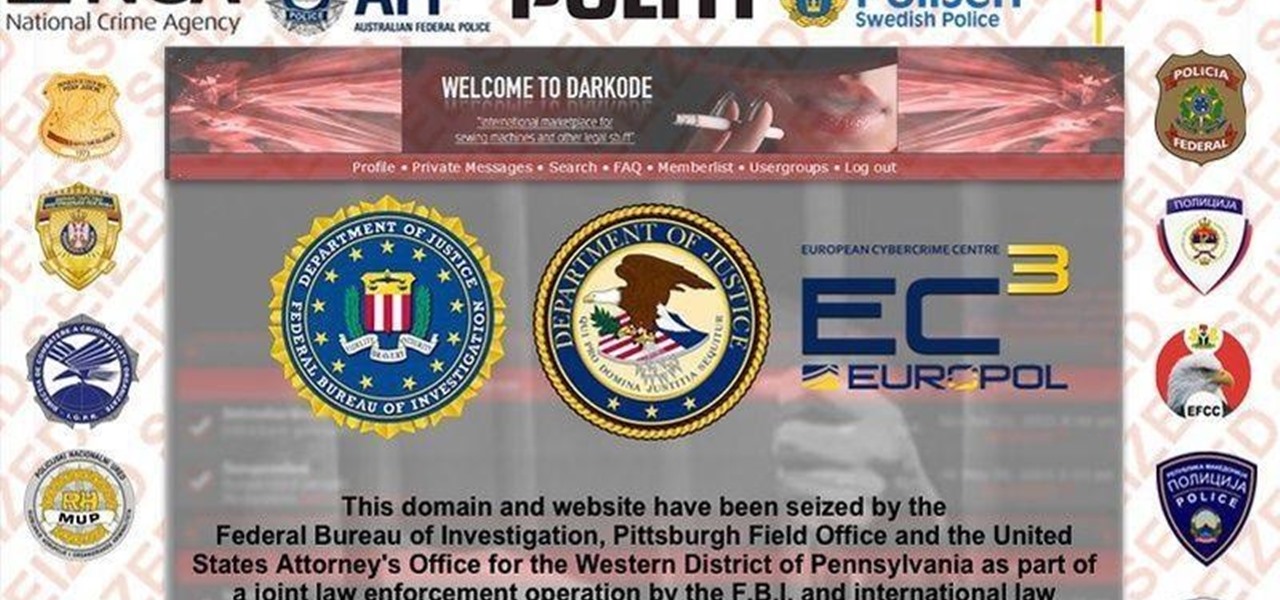
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...

Lorrie Faith Cranor: What’s wrong with your pa$$w0rd? | Talk Video | TED.com.

Two former high-ranking officials at the U.S. National Security Agency (NSA), a federal bureaucracy that collects data and intelligence on foreign communications for national security purposes, have come forward with allegations that the NSA actively monitors Americans as well. According to testimonies from both Thomas Drake, a former NSA senior official, and Kirk Wiebe, a former NSA senior analyst, the agency actively monitors and collects intelligence on every single American as part of a m...

Oh yeah, this is a big topic, at-least for me. All the frequent flyers will/should be interested in this topic. I'm sure all of you have heard at-least something about the TSA, and most of it should have been bad. Complaints, lawsuits and general disgust surround this organization. Is there a reason, or are the 'extremist liberals' at it again? Let's find out!

Pull up outside any construction site and you'll see tools scattered about—hammers, jigsaws, nail guns, hydraulic pipe benders—these are the tools of the trade. You would be hard-pressed to build a home or office building with just your hands! On that same page, security professionals also have their own go-to tools that they use on the job site, only their job site is your server.

Previously, we talked about how to secure Firefox. Today, we will talk about securing a Chromium based Browser. Why? Because Chrome recently beat Firefox in holding more customers.

The last few months of WikiLeaks controversy has surely peaked your interest, but when viewing the WikiLeaks site, finding what you want is quite a hard task.

Having bills to pay is one of the worst parts of life, especially around the holidays. And if you're extremely unlucky, you might also have to pay some hefty medical bills. This can put a heavy damper on plans, wants and needs. What's worse? The people that you owe money to are pushy and always bother you to pay in a more timely fashion, or worse, pay bigger premiums.

Mediocre free Flash game websites are all too common. Many of them thrive off peddling the same few popular games to fans who have slim cause to pick one over the other. They thrive off the indifference of casual gamers and an environment that does not have to stand out to survive, only appeal to the lowest common gaming denominator with tower defense clones and brightly colored Peggle knockoffs. In that context, what Nitrome is doing seems downright commendable.

Dropbox continues to make headlines with their recent programming blunder which left the accounts of its 25 million customers wide open during a four-hour time span. During the duration, anyone in the world could access any Dropbox profile by typing in any password. And seeing as this wasn't the first security failure, everyone, including the most loyal users are considering dropping the Dropbox.

Apple just released iOS 13.5.1, the latest update for iPhone, on Monday, June 1. The update comes 12 days after iOS 13.5, which introduced COVID-19 exposure notifications, a Group FaceTime update, and Face ID improvements when wearing a mask.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

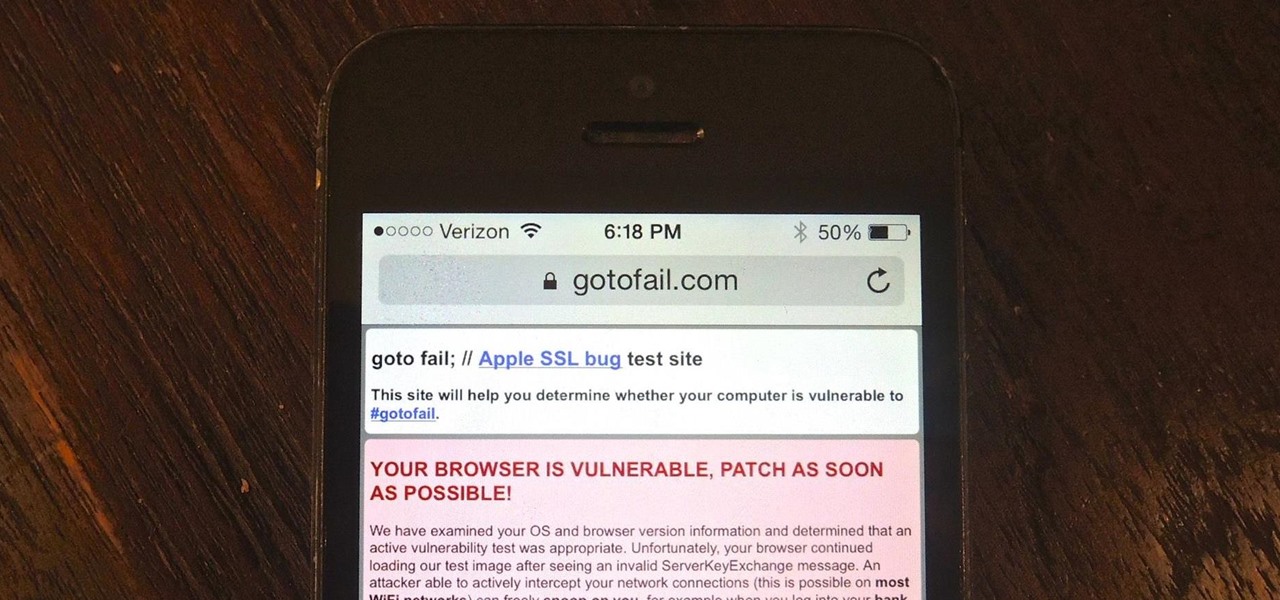
Apple released iOS 7.0.6 last week, an update to fix a serious security flaw that allowed hackers to not only capture sensitive user information such as bank statements and passwords, but also modify that same data on secure HTTPS sessions.