When I was unemployed I looked for different ways to make money. Most of that work was connected with online stuff; I’ve tried writing content, refreshed my old Photoshop skills and even created postcards, but then I realized that my passion to music can bring me more money than all of the other work. I was an active member of a few musical forums and started to add affiliate links to my posts instead of simple ones, so they can be profitable.
SQL injection is a common web application attack that focuses on the database backend. WebGoat is a deliberately insecure J2EE web application maintained by OWASP designed to teach web application security lessons. I plan to use WebGoat for a few future videos. This first WebGoat video will show the basics of installing WebGoat and doing two of its SQL injection lessons. Hack websites with SQL injection and WebGoat.
In a riveting interview on TruNews Radio, Wednesday, private investigator Doug Hagmann said high-level, reliable sources told him the U.S. Department of Homeland Security (DHS) is preparing for “massive civil war” in America.

As hard as you try to protect your valuable information with strong passwords and anti-doxing measures, there's nothing you can really do when someone else gives up your goods. And that is the case with the recent Global Payments breach.

US Secretary of State Hillary Clinton lashed out against Russia and China after a meeting in Tunis. The meeting aimed to increase pressure on Syria to stop its bloodshed. Hillary represents the US as an ally for the rebels.

Merry Christmas all! I hope you are all having a very wonderful day!

This article relates to changing the settings in Adobe Flash so that you can improve your overall computer security and privacy. Changing these settings might have a negative performance impact on your computer - but it is worth while.

Security awareness seems to be a hot topic these days on the web, with developers making apps and devices that can hack networks and machines with just a few clicks. But these applications aren't only exploiting security flaws in systems and networks, they're being used by amateur and wannabe hackers who want to have a little fun, but don't want to learn how to actually "hack" anything.

Unbeknownst to you, hundreds of retailers, shopping malls, coffee shops, and airports track and log your movements. Using sensors installed by retail analytics companies, businesses sniff out your smartphone's MAC address, a unique fixed identifier to your device, whenever your device interacts with their Wi-Fi hotspots.

Security is always a top priority for our smartphones. Leaving your phone at the bar or even at a friend's house can leave you open to hacks and lead to the loss of sensitive information.

The new Jelly Bean 4.2 is a great improvement over previous Android versions for the most part, except one thing—the lockscreen. Users have voiced their complaints in regards to Android 4.2's new lockscreen features, and it's not pretty.

In this video tutorial, viewers learn how to change the default password on a NET-GEAR router. Begin by opening your web browser and go to this site: Router Login. When the Prompt window opens, type in your router's user name and password, and click OK. In the sidebar, under Maintenance, click on Set Password. Now type in the old password, new password and re-type the new password once again to confirm. Finish by clicking Apply. This video will benefit those viewers who use a NET-Gear router,...

In this video tutorial, viewers learn how to change the default password on Apple Airport Base stations. Begin by selecting the Apple Airport Express item. Then double-click the Apple Airport Express item or press the Configure button on the bottom right of the screen. Now enter your password and click OK. Then click on the Airport tab and click on Change Password beside your Airport name. Now type in the new password, confirm it by re-typing it and click on Change. Finish by clicking on Upda...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

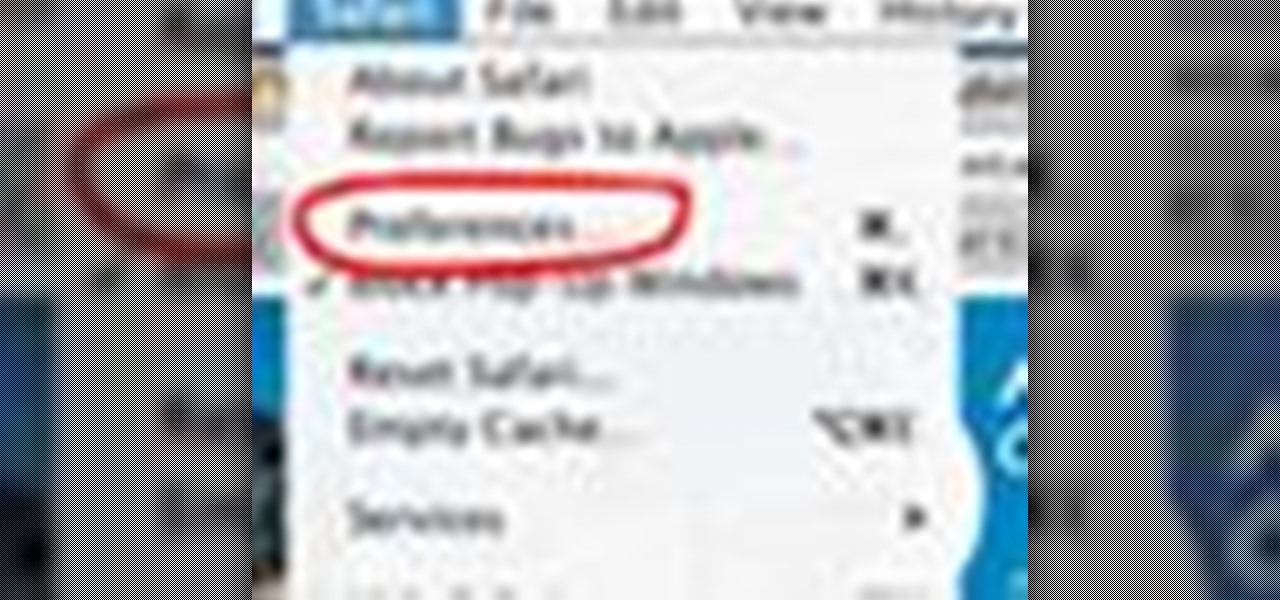
Safari v1.0 is a web browser for Mac OS X. This simple video explains how to disable accepting cookies in the Safari web browser. There are only 4 very easy steps to follow. Open your Safari web browser window. On the your Safari browser left menu tab click on Safari, a drop down will appear once you click it.

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

Check out this hacking video tutorial to learn how to hack a cell phone with a magnet. You can easily hack Verizon's Motorola RAZR mobile phone to bypass the user password.

In this tutorial, you'll learn how to exploit weak security questions to take control of a given Yahoo! Mail account in much the same way Sarah Palin's Yahoo! account was recently "hacked." (To access Sarah Palin's account you will need, in addition to the tutorial, some manner of time travel device.) For a detailed, step-by-step reenactment of the "hack" (scare quotes very much intended), take a look. "Hack" Sarah Palin's Yahoo! Mail account.

Looking for a front-yard upgrade that'll have visitors beating a well-lit path to your door? The answer is an easy to install pathway lighting set. Too often, we're forced to choose between form and function. But when it comes to the route that leads to your front door, you can have it both ways: a pathway lighting system that combines the safety and security of good exterior illumination along with decorative elements that enhance your landscaping. Even though you might not have any experien...

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Chicago cops, the FBI, Homeland Security, Secret Service and a large number of unnamed others have established a high-tech secret command center to surveil people exercising their First Amendment right in Chicago as the NATO war council unfolds this weekend.
Just a few days after a senior US counter-terrorism expert warned that US drone strikes were turning Yemen into the “Arabian equivalent of Waziristan”, US drone strikes yesterday aped the tactic of ‘follow up’ strikes used by the US in Pakistan.
Soon, Americans may find every private email they write could be opened, copied and inspected by government snoopers. The latest cyber security bill – called CISPA – has passed the House of Representatives, coming a step closer to becoming law. President Barack Obama has threatened to veto the act, if it goes through in the Senate. He cited civil liberty concerns as the reason for his threat. CISPA has raised a massive outcry with internet users and freedom activists, who say it’s a hard hit ...
National Security Agency whistleblower William Binney reveals he believes domestic surveillance has become more expansive under President Obama than President George W. Bush. He estimates the NSA has assembled 20 trillion "transactions" — phone calls, emails and other forms of data — from Americans. This likely includes copies of almost all of the emails sent and received from most people living in the United States. Binney talks about Section 215 of the USA PATRIOT Act and challenges NSA Dir...

There is a vast amount of knowledge out there on computers! In fact, it is so vast that no single person could ever possibly ever learn everything there is to learn about hacking or computers in general. People usually specialize in a certain field: cryptography, computer security, networking, software development, testing, and so on...It's probably a bit premature to decide what you want your speciality to be, but keeping the question in the back of your mind will help give you direction in ...
Monday 27 February, WikiLeaks began publishing The Global Intelligence Files – more than five million emails from the Texas-headquartered "global intelligence" company Stratfor. The emails date from between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal’s Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agenc...

When it comes to webcams these days, most people are using their laptops over desktops. The cameras are centered, integrated, and require no configuring. They're a cinch and usually have great resolution. So, then what do we do with all of those old wired desktop webcams that we've accrued over the years? Even if you still use an external USB one, chances are you're not using it daily, so why not come up with a better use for it?

If you saw my last tutorial on retiring early and wealthy, you now know how anyone can invest a small amount of money over the course of their life, and by exploiting compound interest, achieve an extremely comfortable and easy going retirement. In Part 2, we are going to dive into something a little more risky: Tax liens.

Here's a trophy guide for Payday: The Heist that requires excellent teamwork. To get the 'No Photos' trophy, you'll need to take out all of the security cameras in the level First World Bank within ten seconds of drawing your weapon.

Mobile devices can do just about anything these days, thanks to third-party developers. iPhones and Android devices have been known to do some pretty wild things. Need a dupe key made? Scan and order one with your iPhone. Want to know if you're hotter than Justin Bieber? Compare your facial features. Are you a policeman who needs to ID a suspect? Scan their fingerprints and irides. Want to control your Canon DSLR remotely? Use your Android phone.

Team Fortress 2 (TF2) is one of the best multiplayer games of all time. It took nine years to make, and the developers have supported it with more post-release free updates than any other game ever. Four years after its release in 2007, it is still immensely popular, and although its price has gone down, Valve has managed to continue making a massive profit by introducing the first successful microtransaction model in a mainstream American shooter. That model has been so successful that it lo...

One of the biggest advantages iOS has over Android as a mobile platform is how readily and fully it has embraced mobile gaming. There are over 200,000 games available in the Apple store, compared to approximately 100,000 in the Android Marketplace. As an Android-using gamer, this has always bothered me.

About two months ago, the massive Gawker Media hack was a wake up call for many web denizens on the importance of proper password security. Data analyzed by the Wall Street Journal revealed the three most popular passwords recovered from the hack were downright idiotic—123456, password, and 12345678. If past events weren't motivation enough for crafting a strong password, then maybe a racy 8-bit stripper is. Naked Password is a jQuery plugin by Platform45 that rewards you with an accelerating...

When choosing a security system for the office, Billy Chasen decided to ditch the traditional lock & key barricade for something a little more 21st century. He hacked together a device that uses a web server, servo motor and some parts from Home Depot to enable locking & unlocking via text message. Chasen maintains a list which gives access to green lit office workers, who enter by simply texting "lock" or "unlock"... and voilà, open sesame.

The German police have their panties in a bunch over a highly inflammatory sculpture of a urinating policewoman by artist Marcel Walldorf. Entitled "Petra", the hyperrealistic figure depicts a female officer crouched, peeing with buttocks exposed. The most chilling detail is her riot baton casually propped on the wall next to her.

Note: Little Brother is available as a free ebook download. Warnings

Up for auction at Heritage, JFK's crusty old birthday cake, presented to him at his 45th birthday party in Madison Square Garden back in 1962. Marilyn Monroe performed her legendary “Happy Birthday, Mr. President” at this very event.

WonderHowTo loves paper artillery. More sophisticated in construction than Box Wars, plus tense on-camera drama to boot, Cardboard Warfare is a tight homage to the paper gun. Not completely sold on the acting, but I'm really digging the mise-en-scène. Says creator Clinton Jones, aka, pwnisher:

In this tutorial, we learn how to find an IP address in Hotmail. First, open up your Hotmail in box and right click on the email you want the IP address of. Now, select "view source" and find where it says "received: from" or "X-Originating IP". This will give you the exact IP of where this email was sent from. You can use this for any email you receive and the best part is that it only takes a few simple clicks of the mouse and a few seconds out of your day! This can help you bump up securit...

Congrats to MuscleNerd, the first to jailbreak the almighty iPad. Via DVICE: