This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.
What is Google Dorking? Well, simply put, "Google Dorking" is just an efficient way to utilise keywords in order to perform very specific searches on a given subject. In this case, one would look for websites/servers that are vulnerable to attacks or are configured improperly by using specific search criteria that should yeild results, should it find matches to known mistakes/errors in a website or webserver.

Today's tutorial will teach you how to erase data permanently so that it cannot be recovered. Many believe that having a file shredder on the computer means you are up to no good.

Windows 8 Beta (Developer Preview) It wasn't that long ago Windows 7 was released - now Windows 8 Beta is here. I did do a Google search to see when the stable version will be out but wasn't able to find an official statement from Microsoft. However - I saw several articles on Google hinting that the final release might be in August or there about.

Google+ is taking over more and more of Google's core properties. This week, we've seen several announcements from Google blogs about new products, new features, new looks, new integrations. If you're like me, you actually want to know where to go for all the latest information on Google products.

There are a lot of fantastic video games out there. Indie Games Ichiban's bread and butter is making sure that you steer clear of the bad ones and embrace the good. But really, the biggest goal here is to help everyone have more fun. To that end, today a game is not recommended, but an event. If you like games—not just video games—but tabletop, board and even hopscotch, then PAX Prime is one of the best events you could possibly go to.

If you've gained entry into Google+, one of the first things you should do is adjust your Google account settings. Your settings will now look quite different, and you can adjust your notifications, password retrieval methods, and more. There are many settings that you may not have been aware of before.

Do you know how you are perceived by your peers? In real life and online? In the physical world, you could be seen as intelligent, thoughtful and hard-working, but on the Web you could be looked at as irrational, selfish and slothful. There's just something about the Internet that takes away a person's judgement and replaces it with impulsiveness—especially when it comes to Facebook.

Dactyloscopy isn’t going anywhere. Forensic science has much relied on fingerprinting as a means of identification, largely because of the massive amount of fingerprints stored in the FBI’s biometric database (IAFIS), which houses over 150,000 million prints. And thanks to the departure of messy ink-stained fingertips, biometric analysis isn’t just for solving crimes anymore.
Ron Paul Republicans take over Nevada GOP
Moscow, May 21 — Some Western countries are still considering a military operation against Iran as an option over its nuclear programme, a Russian minister said Sunday.
“The UK government is rounding on protesters ahead of this summer’s Olympics, issuing the first court order to ban an Occupy activist from the event. The unprecedented security measures for the Games have been branded as over-the-top,” reports RT.
Yesterday senior State Department official Alec Ross publicly announced that the Obama administration opposed CISPA, but refused to entertain the notion of the bill being vetoed.
The Obama administration is moving to strengthen its ties with Persian Gulf nations whose geography and oil resources have already made them key players in U.S. defense and energy security.

News in a nutshell: US to announce aerial blockade of Syria

SSH is amazing, and we praise its existence on Null Byte for many reasons. Notably, it allows us to reroute our traffic through encrypted ports on our local host to be sent to its destination when on the go. You can even control your home computers remotely over a secure and encrypted connection. This is handy for a multitude of reasons.

As of today (January 18, 2012) many websites have "blacked" out their content for the day, one of the more notable websites is Wikipedia.org. As this can be a small compromise as an act of protesting against the heinous bills going through the United States' Congress. A lot of these websites are using a type of Java-Script or JS for short, and others are using simple little Pop-Ups to block the sites. Through the use of some clever addons everyone that cares about their online security should...

Hello, welcome to my first post! Today, I would like to talk about setting up a Page File Encryption in Windows 7 and Vista. But first - what is a Page File Encryption? Why should you enable this option?

Friday's mission was to accomplish solving HackThisSite, basic mission 7, which required us to learn some basic Unix commands. If you have any prior experience using Unix commands, this should be a breeze for you if you sit and think for a second.

Welcome to Part 3 in my series on protecting your computer from prying eyes (Part 1, Part 2). In today's segment, we will be going over drive encryption using the TrueCrypt program on Windows OS. Drive encryption is a technique that masks your data with a cryptographic function. The encryption header stores the password that you have entered for the archive, which allows the data to be reversed and read from. Encrypted data is safe from anyone who wants to read it, other than people with the ...

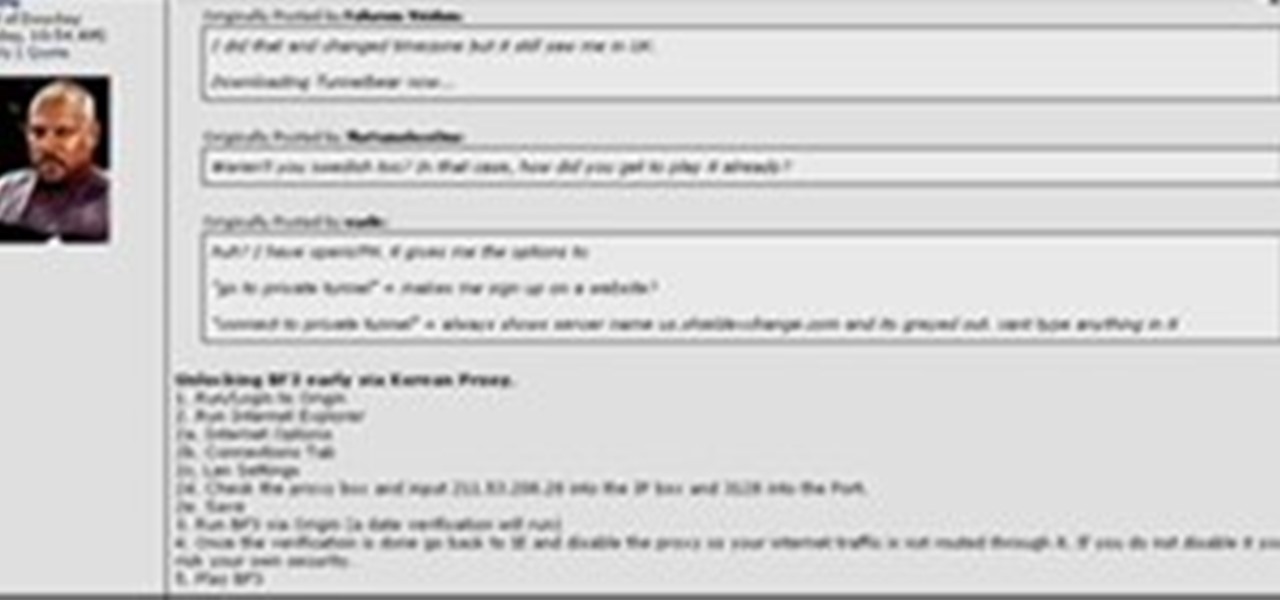
Battlefield 3 officially comes out tomorrow but people have figured out a way to play it today if you have it downloaded (digital pre-install). All you have to do is fake an ip to make it look like your timezone is ready to play. I'll try this when I get home, in the meantime:

Google's hard at work beefing up their new Google+ social network, and while they continue to improve new features like Circles and Hangouts, they haven't lost track of their other online features already widely in use. If you're already a part of the Google+ project (currently closed to invites right now), you've probably noticed the changes in Picasa Web, but Gmail has been getting some great updates as well—and you don't have to be in the Google+ network to use them.

For those who need security on their Android devices, the standard swipe lock screen just isn't enough, so it's necessary to install applications like GOTO and WidgetLocker to enable either pattern, password or PIN protection. This protection is great overall, but when you're frequently using your smartphone, having to keep unlocking the lock screen becomes quite an annoyance. You could be in a heated text conversation, following directions on a map or compulsively checking the news feed on F...

From Boing Boing, a highly amusing photo gallery of illegal goods seized by airport customs officials in Australia. Some are fairly typical, but others really make you wonder... Yes, I'm most definitely talking about the tropical fish skirt lady.

A man going by the pseudonym of Ed Dante has written an illuminating account on his life as a career cheater. His clients include ESL students, hopeless dummies, and spoiled, lazy rich kids:

1. Involves gate crashing a big awards event or film opening (like what AAF did with their song 'These Days': http://www.youtube.com/watch?v=JNM2tV3PA_8).

A radical art group of Russian political pranksters, who go by the name of Voina, have delivered a giant "Up Yours!" to the Russian government... in the form of a 213-foot-tall penis.

DARPA and Dallas's Southern Methodist University are collaborating on a super high tech camera, capable of scanning eyeballs in a moving crowd.

Today's WSJ takes a tour of Russian billionaire Andrey Melnichenko's 394-foot insanely luxe yacht, coined "A".

Hiroshi Ishiguro is at it again, but this time "it" has a winning smile. Japanese researchers have developed a humanoid robot that can laugh and smile, mimicking a real person's facial expressions. The android, called Geminoid F, is modeled after a woman in her twenties, with long black hair, silicone skin and lifelike teeth.

First Ever User-Generated HD Contest Vimeo and Canon have launched this wonderful contest for filmmakers shooting on Canon's EOS 7D DSLR.

Working from home is already challenging. Add the threat of a cyberattack into the mix, and the situation gets even hairier.

The shift to remote working in response to the COVID-19 pandemic has not slowed Google's efforts to fulfill its annual Android update cycle, as the third developer preview of Android 11 dropped on Thursday.

Apple just released iOS 12.3 developer beta 5 today, Tuesday, May 7. The release coincides directly with Google I/O, Google's big hardware and software presentation, and comes eight days after the release of 12.3 dev beta 4.

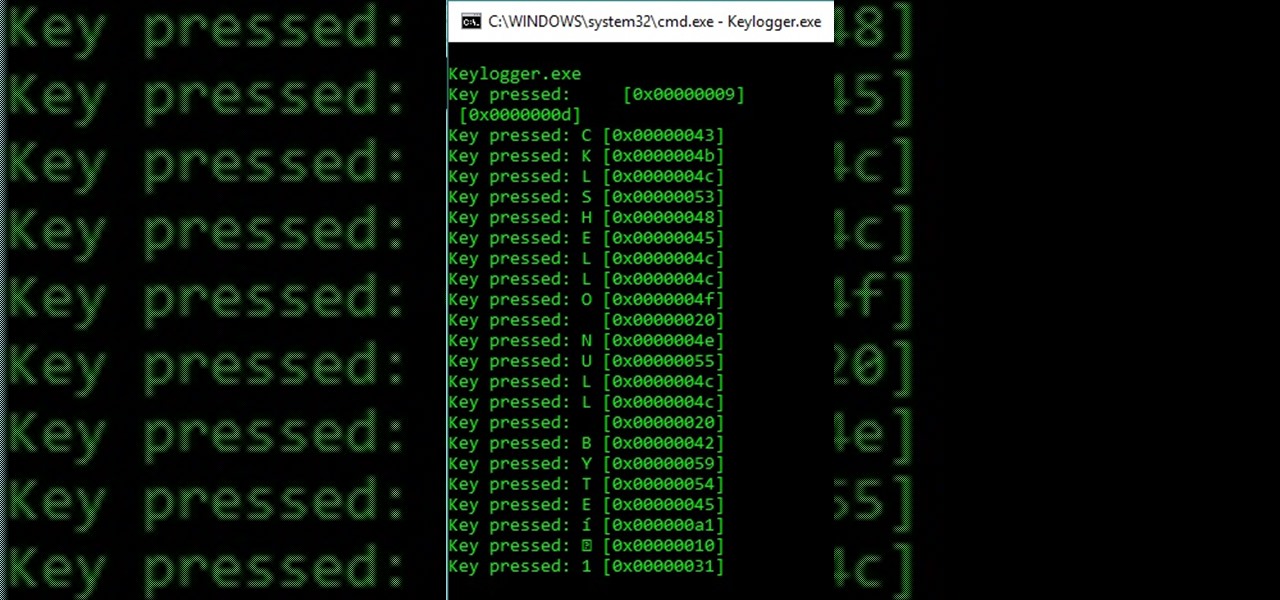
Yo yo yo, what's goin' on my devilish fiends? Have you come here to learn how to make a keylogger for malicious intent? You sly fox! But in all seriousness, this article will cover quite a simple method for creating the most basic of Windows keyloggers. You're in for a surprise! Let's dive right in!

Okay guys and gals, this will be a quick tutorial on using the incredibly helpful man pages. What Are Man Pages?

Hello y'all! I apologize if this question has been solved somewhere else, but I have looked around on Google, Yahoo, and Null Byte and have not been able to find any working solutions.

So you've got your shiny new LG G3, your accounts are all set up, and Google has restored all of your apps. Well... almost all of them.

The latest update to Google Search, which is rolling out right now, brings automatic parking spot pinning through its Google Now platform.

Google is set to release an update to their Hangouts messaging service starting this week. The update to version 2.1.075 brings new features, with the biggest ones being merged chat and SMS messages and a home screen widget. Here's a complete breakdown of the new features you can expect.