Cleanliness is next to godliness. My interpretation of that age-old adage means that keeping your house clean is just as un-fun and boring as being a goody two shoes. That's why they call things like laundry and doing dishes "chores," I assume. Yuck.

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

The start of a new year is generally thought of as a chance to start over, a time to improve or "fix" things in your life. Yet most people who set stringent New Year's resolutions find themselves failing within weeks—or even days—of setting their lofty goals.

Fall is my favorite time of year, yet I cringe every time it begins. Why? Because it seems like every business is in a frenzy to start the Christmas shopping season the day after Halloween ends. For those of us who are fans of pumpkins, that's a buzzkill.

French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast dish.

Go to a chain supermarket, and chances are you'll see one type of garlic—maybe two or three if you're lucky. However, there's a mouthwatering slew of Allium sativum out there, far beyond those papery white bulbs most of us encounter at the nearest Stop 'n' Shop.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Foodies and big-time chefs like Thomas Keller go crazy for fleur de sel. This finishing salt appears in fancy eateries and cookbooks the world over, and in the early 2000s, it was not uncommon to see diners in a high-end restaurant sprinkle a pinch of fleur de sel on their plates from their own personal stash.

There are many impressive features on a Samsung Galaxy Note 2, but just like any other smartphone on the market, the most used one is the camera. How many times did you take a picture today? Or admire all the selfies in your gallery? Or upload a video to Instagram, Vine, or Snapchat?

I obviously do a lot of Steampunk projects, but there are a ton of things out there that I haven't tried yet. So, in an effort to broaden my horizons, I recently taught myself how to use Arduinos, which I plan to incorporate into some of my future Steampunk builds.

Let's say that you've got the look down, and you have your Steampunk props all ready to go. Congratulations! You're a Steampunk!

While I am a writer with a degree in Creative Writing, I haven't published any Steampunk fiction. However, as a panelist and track director, I've been on panels with many well-known Steampunk writers and have gleaned insight from the things they've said. I've compiled some of those things into this post, which will hopefully be helpful to all of the writers out there!

The new iPhone 5 was just revealed yesterday, and it's 18 percent thinner and just 1/5 the weight of its 4S predecessor. It's also taller with a larger screen, which gives you a fifth row for apps now. As far as speed is concerned, it has a speedy A6 chip and can tap into wireless 4G LTE networks for fast Internet. Both the iSight and front-facing FaceTime cameras were improved, too. The only downside seems to be the tinier "Lightning" connector, which replaces the standard 30-pin connector w...

Today's post is a small go-to guide for beginner programmers in Null Byte. With many of our community members picking up programming from our Community Bytes, it only makes sense to lay out a one-stop guide for your reference. Hopefully this guide will help you make an educated and thoughtful choice on what programming languages you want to learn, and how you want to learn said languages.

Growing up, I was told that hard work could get me anything I wanted. But with Apple's Image Playground, I can create almost any illustration or drawing imaginable just by typing or selecting a suggestion. This groundbreaking feature in Apple Intelligence lets you generate images from simple prompts, opening up exciting possibilities for creativity.

You no longer have to worry about repair technicians accessing the personal information on your iPhone when you send it in for repairs. With Apple's new security feature, you'll no longer have to erase your iPhone to ensure your photos, messages, accounts, and other private data remain for your eyes only.

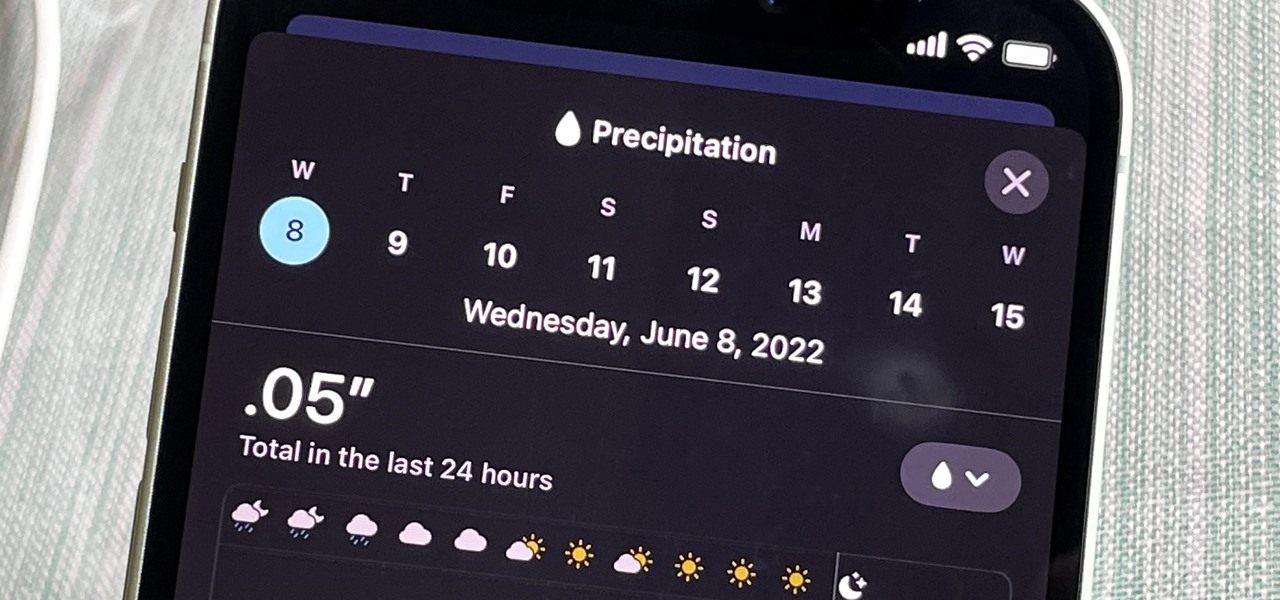
Your iPhone's Weather app received its biggest update yet. Apple finally incorporated its Dark Sky purchase into Apple Weather, so you'll see more information for each location's forecast. Plus, there are a few surprises to be excited about, such as the ability to add more trackable cities.

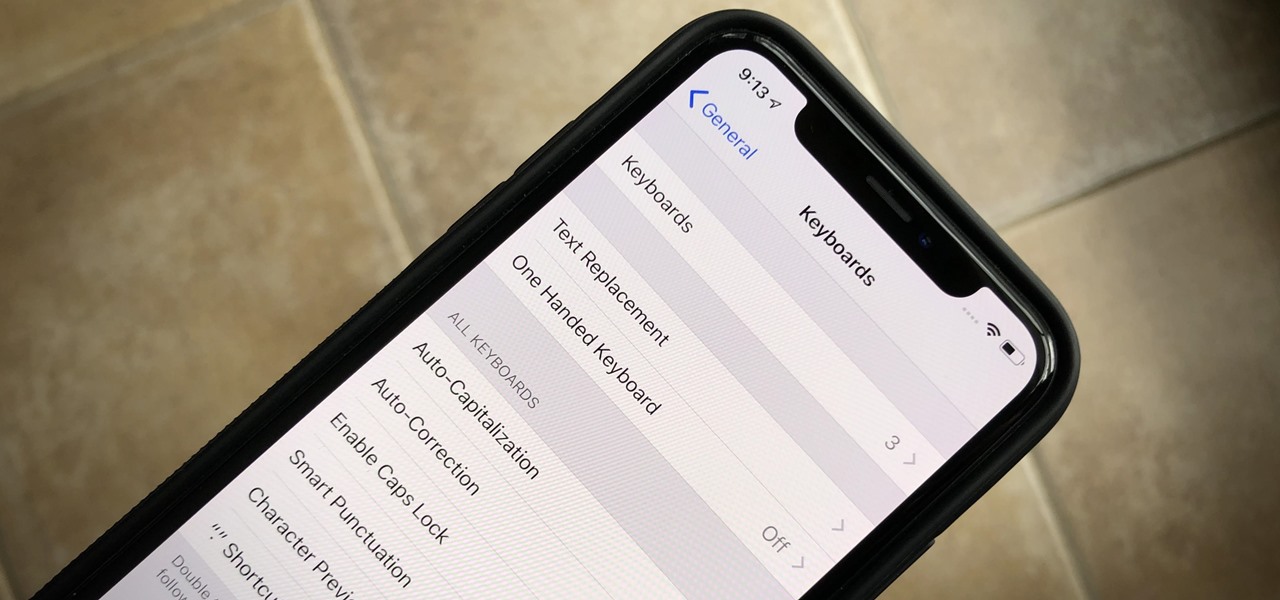
Almost 190 secret characters are hiding behind your iPhone's default keyboard, and I'm not talking about what you see after tapping the "123" or "#+=" keys. These special composite characters can include accents, dots, and other diacritics, and you'll even see some strange typographical characters like the section sign, inverted marks, and per mille symbol. Here's how you find them.

If you consider yourself an emoji master, you'll have to retrain yourself once you install iOS 14.5 on your iPhone. Why? Because there are 217 new ones available to incorporate into your sometimes cryptic emoji messages.

One of the most significant changes in iOS 14 is something we've wanted for a very long time, and it will change the way you use your iPhone. Since the very first iPhone OS 1 (yes, before it was even "iOS"), we've been stuck with Apple Mail as the default emailing app. That all changes now.

It's been a long time coming, but Apple Maps finally has cycling directions for your iPhone. Google Maps has had cycling support for ten years now, though, many of its more useful features had been incorporated within the last few years. Well, with iOS 14, Apple has caught up, and it's done a fantastic job.

The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

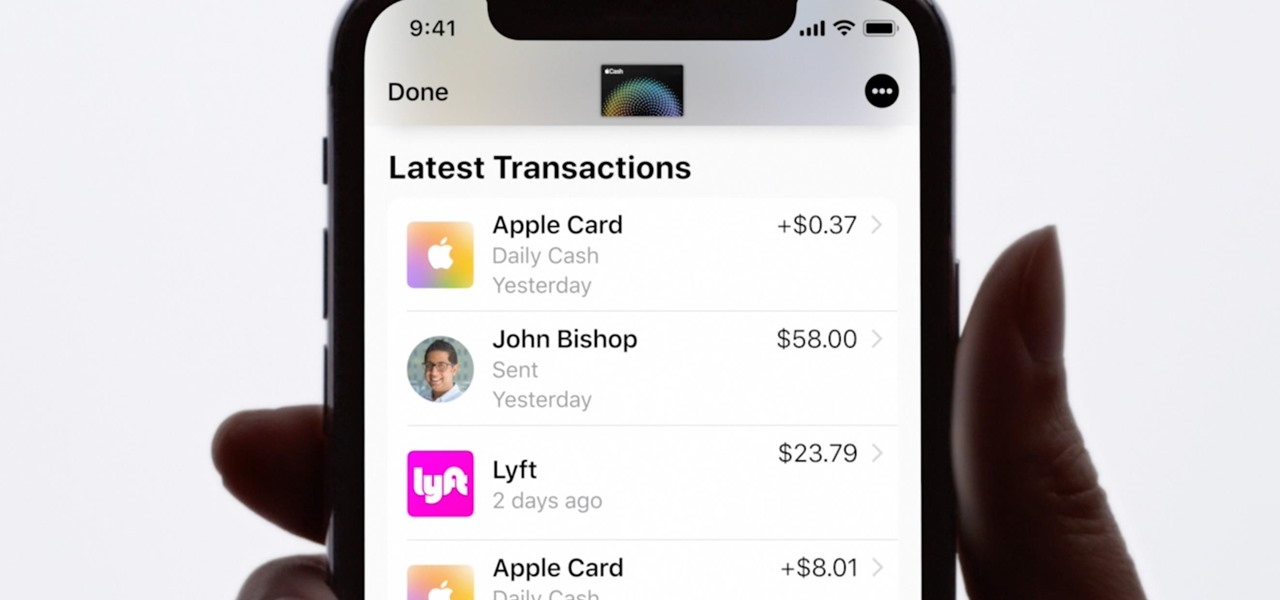
Apple Card is the iPhone OEM's big leap into the credit card market. Its low barrier to entry and ease of use make it an appealing option, especially for those who often pay for goods with Apple Pay. To get the best rewards possible, make sure you use the Apple Card at stores where you can get 3% cash back.

The first developer beta for iOS 13 is available to install on iPhone models, but the process for doing so may be a bumpy ride. Apple has not included configuration profiles for the developer beta yet, and many developers are having issues installing iOS 13 even with macOS 10.15 Catalina installed. Plus, since this is the first beta, there are a lot of problems with old and new features to work the kinks out of.

The hugely successful S10 series of flagships may be a tough act to follow, but Samsung has proven that it's up to the task with the Galaxy Note 10. The latest phablet bearing the Note name is the first of its line to come with an even larger variant, and boasts an eye-pleasing design with impressive performance to boot.

For years, iPhones have had haptic feedback, but Apple didn't incorporate it into the stock iOS keyboard until iOS 16. To use keyboard haptics in iOS 15 and older — or as an alternative to the default keyboard's in iOS 16 — you can take advantage of third-party keyboards like Gboard.

You know your infant is advanced. Maybe you want to give her or him a head start at learning things like writing code to develop the next big Fortnite game. Or maybe you just want to play Fortnite with your infant. But the American Academy of Pediatrics discourages screen time for kids under than 18 months, with just one exception: video chat.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Look, tests are no fun, and doing poorly on them is rarely an option. Whether you're studious or a slacker, everyone needs a little boost now and again. While students have found ways to cheat as long as tests have existed, the invention of smartphones has greatly enhanced the potential to get ... creative.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

They're finally here — Samsung has officially revealed the Galaxy S9 and S9+, which run Android Oreo out of the box. Since we've spent plenty of time with the Oreo beta for the Galaxy S8, we already know about some of the best new software features coming to the Galaxy S9. Like previous updates, Samsung has enhanced its software with a fresh look and brand new functionality.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

Samsung has finally rolled out the Android Oreo update for the Galaxy S8 and S8+. If you're just now getting the update, you'll be happy to know that your Galaxy just got upgraded with plenty of cool new features. Like previous updates, Samsung has improved upon its software by including a new look and new functionality.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

All fields of study have their own language. For people interested in learning about microbes, the language can sometimes be downright difficult — but it doesn't need to be. From antibiotics to xerophiles, we have you covered in an easy-to-understand glossary.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

The oven is arguably our most essential kitchen appliance (right alongside the fridge, freezer, and yes, even the microwave). But even though we've been using them for a few millennia, many of us know so little about our ovens that our cooking or baking can feel like a roll of the dice sometimes.