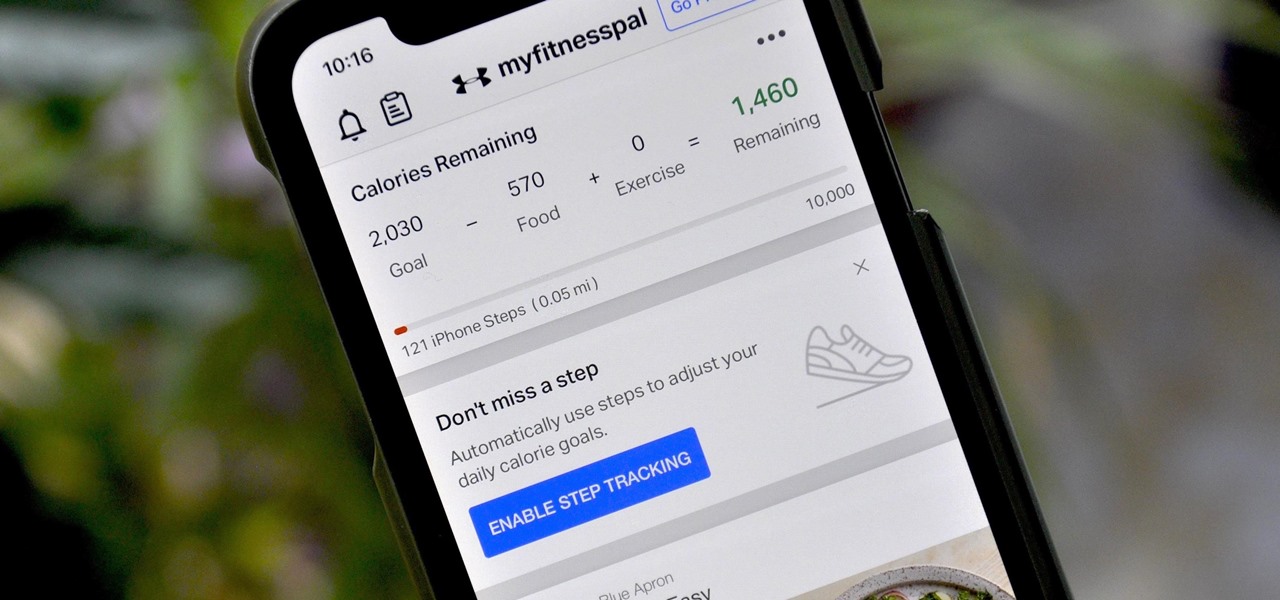
If you're new to MyFitnessPal, it might seem daunting. The app is way more than just a calorie counter, but that's because getting fit is just as much about changing your lifestyle as it is about watching what you eat. So don't let it overwhelm you — there are just a handful of tips you should know to hit the ground running.

Last year's augmented reality investments roundup was impressive. And in 2018, the dollars flowing toward AR haven't decreased, as venture capitalists and strategic investors continue to aggressively fund AR startups at a rapid pace.

The OnePlus 6T is easily one of 2018's best value phones for many reasons, especially when it comes to rooting and modding. But like many new phones, it's plagued with the single bottom-firing speaker that left us wanting more in the sound department. The speaker is decent on its own, but it appears to have some hidden potential at the same time.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.
With YouTube TV and DirecTV Now starting at $40/month, and others like Sling TV offering an eye-catching $25/month plan, streaming cable services may sound like a great way to cut costs while cutting the cord. But when you look at all the factors, the price you pay may very well end up being just as high as your traditional cable bill — if not more.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

With the new iPhones coming out, many see the current mobile market as just another epic battle between Samsung and Apple. But let's not forget there are many other phones that run Android. And when you start to sift through the specs, one stands out as a competitive alternative to the iPhone XR, the LG G7 ThinQ.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

All phones (yes, iPhones too) slow down over time. As your device gets bogged down by various apps and you begin to run out of storage, it's just an inevitability. That doesn't make it any less frustrating ... I mean, is there anything more annoying than a slow phone? My answer: No. Of course not. It's the single most annoying thing ever.

As penetration testers, we sometimes need to securely store customer data for prolonged periods. Bruteforce-resistant, vault-like containers can be created with just a few commands to protect ourselves from physical attacks and unintended data disclosures.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.

If you're on the hunt for a profitable side-gig, or even a completely new way to to make money, you'll want to take a look at Upwork, a leading freelancing platform that connects skilled freelancers with clients from all over the world.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

If there's one strength of Apple's that iOS and Android fans can agree on, it's the company's dedication to user privacy. With each new iteration of iOS, Apple builds upon these foundations, enhancing and increasing each iPhone's ability to protect its user's data. In iOS 12, Apple has added many new features to Safari, most of which have their own unique way of keeping you safe online.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

As the official release of iOS 12 nears closer each day, Apple continues to update its betas. The company released the fourth beta of the upcoming software to developers Tuesday, July 17, exactly two weeks after the release of the third developer beta which came out just a few days before the second public beta.

The latest Star Wars movie, Solo: A Star Wars Story, has grossed almost $350 million worldwide during its first month in theaters. This is a good opportunity to discuss how hackers can use media hype (in this case, Hollywood movie hype) to disarm an unsuspecting Windows user into inserting an evil USB stick into their computer.

Many of us rely on our smartphones for all our media needs. Now more than ever, we're using Bluetooth connections to play audio over speakers, headphones, car sound systems — the list goes on. If you own a Samsung smartphone like the Galaxy S9, there are a number of Bluetooth tweaks and hidden tricks that can maximize your audio experience.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

One of the primary factors that separates an augmented reality device from a standard heads-up display such as Google Glass is dimensional depth perception. This can be created by either RGB cameras, infrared depth cameras, or both, depending on the level of accuracy you're aiming for.

The LG G7 ThinQ will likely be lambasted for its notch and awkward name, but one thing they seem to have gotten right is the new display. The G7 ThinQ will give many a first look at a new type of panel with lots of promise. While it was previously limited to TVs, from what we know, it should really shine on a smaller screen.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

TouchWiz might not be the Android skin of choice for hardcore aficionados, but the Galaxy's OS still has a ton of great features up its sleeve that help provide one of the most enjoyable smartphone experiences out there. Many of these are relatively hidden and overlooked features that you may not be aware of.

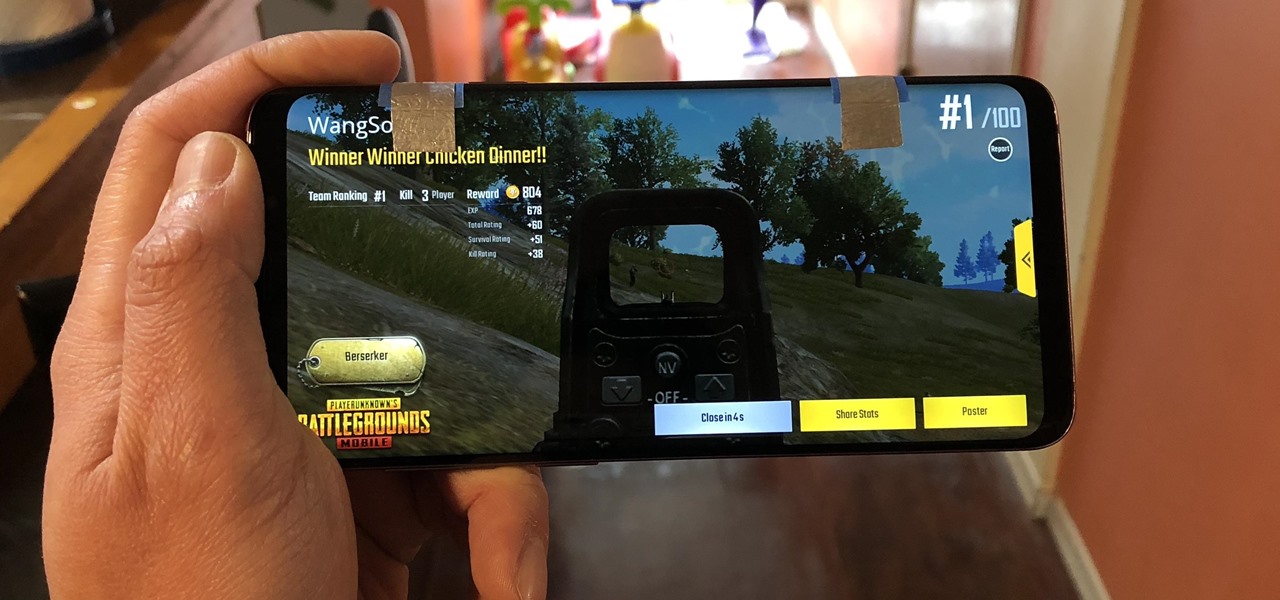
With ultra competitive games like Fortnite Battle Royale and PUBG taking the mobile world by storm, gamers are looking for ways to get a leg up on the competition. One of the biggest advantages you can give yourself is the ability to aim and shoot while on the move, but that's not exactly easy with a touchscreen.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

If you recently received your new Galaxy S9 or S9+, you're probably excited to try out all of the features the flagship offers. While many of the features are self-explanatory and easy to access, there are a handful of very useful items that Samsung has buried in the settings menu. Enabling these hidden features will help you unlock the true power of your new device.

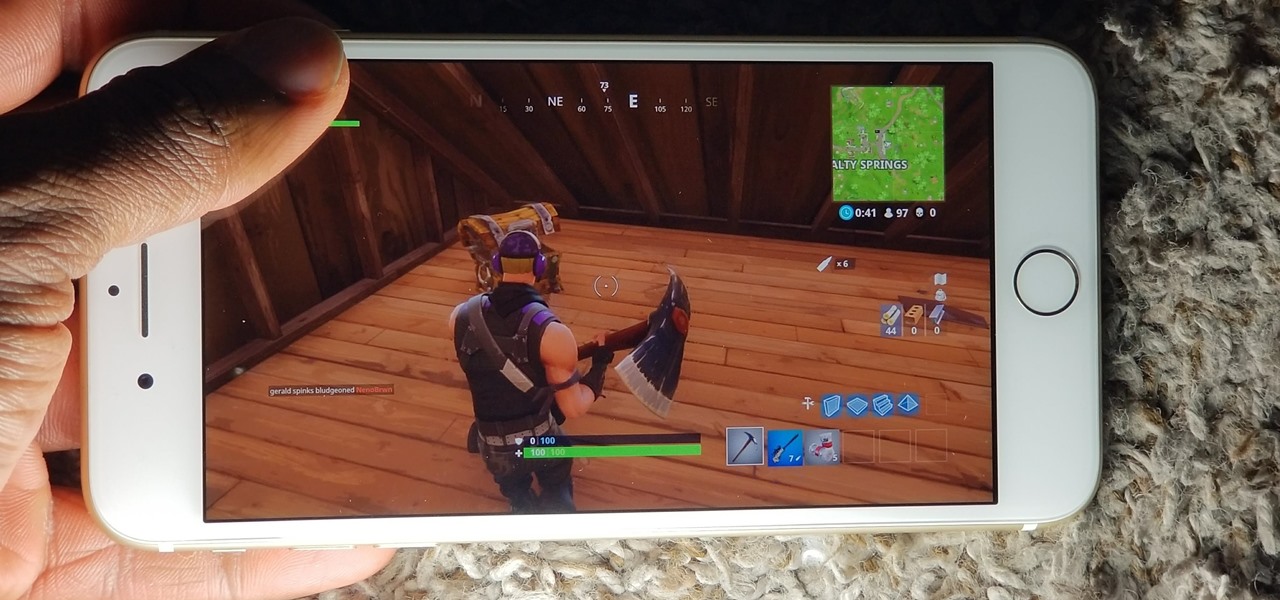
While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

It seems like each day new rumors and leaks come out for Huawei's upcoming P series devices. Everything from its name change to its specs has been leaked, sometimes with contradicting rumors. One of the biggest leaks is the inclusion of triple rear cameras, a first for smartphones.

The reveal of Magic Leap One: Creator Edition brought with it some insight into the path the device took from prototype to "final" design.

The headphone jack is becoming outdated technology in smartphones — that's what many manufacturers would have you believe. For the convenience of the audiophiles out there, we recently published our list of all phones that have removed the 3.5 mm jack. But what did each company gain inside their flagship phones by removing this supposedly antiquated port?

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Facebook really wants your phone number, nagging you for one as soon as you join. This isn't all bad since it can help secure your account with two-factor authentication. On the flipside, this makes it easy to reveal the private phone numbers of virtually anyone on Facebook, including celebrities and politicians. We're going to look at how a hacker would do this and how to protect yourself.

So, your grandmother finally wants to ditch her flip phone for a shiny new smartphone? Congratulations. But helping her get used to her new device, even when it's an iPhone, is no small task. Grandma mastered checking her email in late-2012 and just recently learned there's a thing called "Facebook." But we love grandma, and thanks to this guide, we can definitely make this happen for her.

With the V30, LG has really delivered an amazing smartphone that hits all the major features consumers want. Amazing camera, beautiful edge-to-edge display, great battery life, water resistance, and smooth performance — there isn't much not to like about the LG V30. Unfortunately, it does suffer from heavy bloatware thanks to the carriers. The good thing is, unlike in the past, you are not stuck with it.

On the airplane, in the middle of cold and flu season, your seatmate is spewing, despite the clutch of tissues in their lap. Your proximity to an infectious person probably leaves you daydreaming (or is it a nightmare?) of pandemics and estimating how likely it is that this seatmate's viral or bacterial effusions will circulate throughout the plane and infect everyone on board.

A deadly type of brain tumor and Zika-related brain damage in developing fetuses are devastating brain conditions that, at first glance, may seem unrelated. However, thanks to new research, their paths seem to cross in a way that could benefit patients. A new study has shown that Zika kills brain cancer stem cells, the kind of cells most resistant to treatment in patients with glioblastoma, a deadly brain tumor diagnosed in about 12,000 people in the US each year.

People infected with HIV take many different types of pills every day to decrease the amount of virus in their body, live a longer and healthier life, and to help prevent them from infecting others. That could all be in the past as new clinical trials testing the safety and effectiveness of a new type of treatment — injections given every four or eight weeks — look to be equally effective at keeping the virus at bay.

If you have a taste for sweets, you have at least one thing in common with mosquitoes. While too much sugar is unhealthy for humans, a new product makes sweets deadly to mosquitoes.