
News: Google Releases Glass Enterprise Edition 2, Includes Qualcomm Snapdragon XR1Upgrade
As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).


As the tech world patiently waits for the advent of mainstream consumer smartglasses, Google is content to stick to the business world (for now).

The perfect promotion for Pokémon: Detective Pikachu has finally come to fruition as Niantic has added some movie-related perks to Pokémon GO.

While North has yet to add third-party app support to its Focals smartglasses, the company has been diligent as of late in its efforts to add more functionality to the bare-bones AR device.

In an effort to raise awareness regarding the impact of emissions on the environment, Snap has partnered with the United Nations Environment Programme to use augmented reality to show how much ocean levels will rise over the next 80 years.

One of the biggest advantages of the front-mounted ultrasonic fingerprint sensor found on the Galaxy S10 and S10+ is that you no longer have to physically pick up your device and reach around the back to unlock it. Instead, you simply place your finger on the screen for easier access and added convenience — at least on paper.
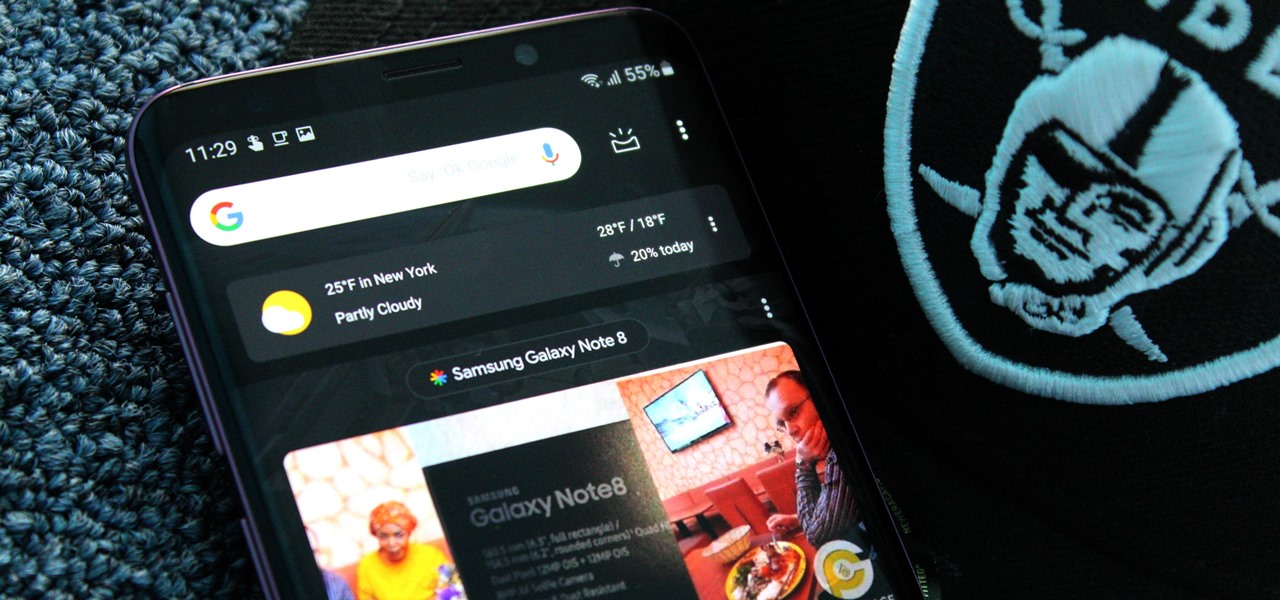
The word on the street is Android users want a dark mode. With the increased usage of AMOLED panels on smartphones (including some midrange devices), there is a considerable demand for dark themes and their battery saving benefits. Recently, Nova just added the feature to Google Discover.

The week of the annual Consumer Electronics Show is supposed to be filled with good news for the augmented reality industry as AR headset and smartglasses makers show off their new wares.
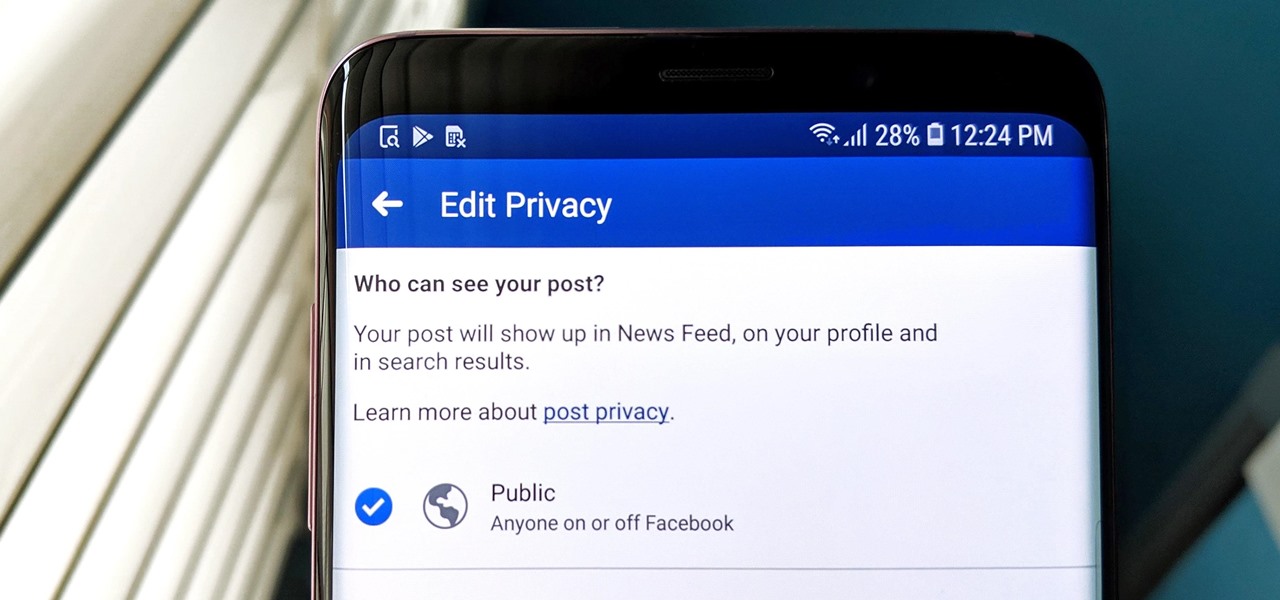
Facebook has grown into one of the central hubs of the internet where ideas are shared with others. But with the rise of brand development, individuals and companies need to get their messages out beyond their group of Facebook friends so it can be seen by more of the world.
With the increasing popularity of OLED displays, companies like Apple, Google, and Samsung have all shifted away from traditional LCDs for their flagship devices. An OLED screen provides deeper blacks and is better for battery life since each pixel can be controlled individually while emitting its own light. This, in turn, has made dark themes an important software feature.

Returning to the spotlight after its debut at last year's CES, augmented reality smartglasses maker Rokid is back with a new update.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

Apple's stock Podcasts app in iOS remains my go-to for all of my podcast-listening needs, but skipping around during an episode can be frustrating. Scrubbing audio along the timeline is often an imprecise maneuver, which is why the skip buttons can be so useful and efficient. Without customizing skip lengths, however, you may find yourself tapping far more than you need to.

Augmented reality productivity software maker Upskill has expanded the reach of its Skylight platform with support for Microsoft HoloLens.

The latest business move by Magic Leap could result in a significant boost to its spatial computing platform's performance and headset design.
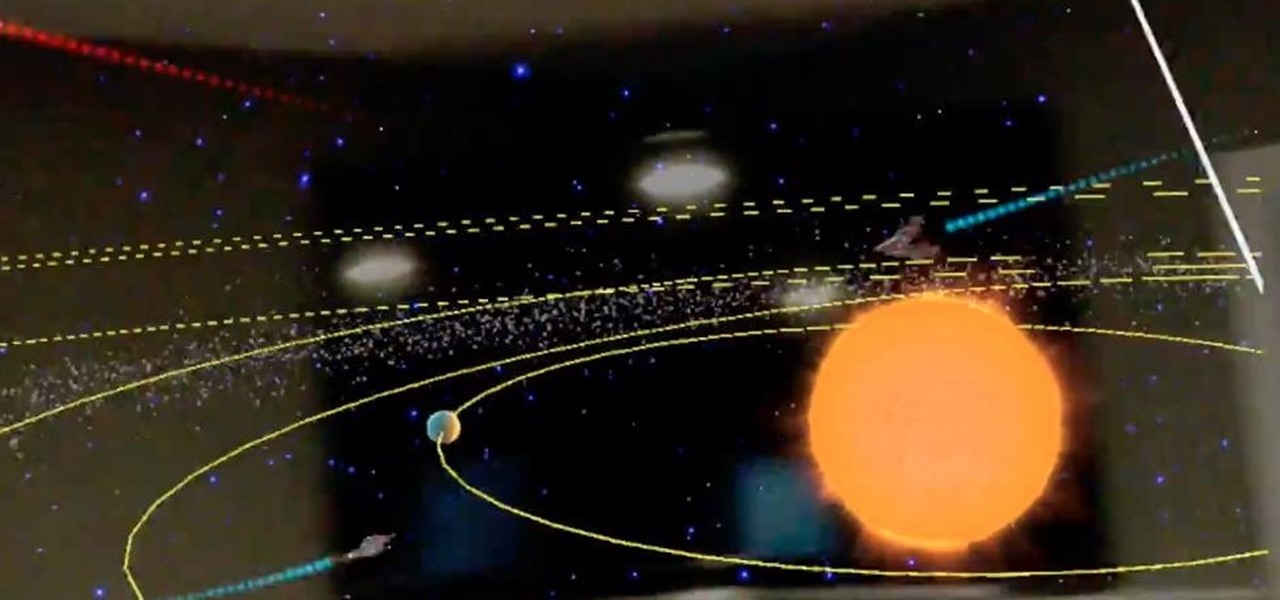
One developer has taken the formal name of the Magic Leap One: Creator Edition quite literally with an app that enables users to create a custom universe in their own living room.

Four months after unveiling the latest productivity apps for the HoloLens, Microsoft now has a series of compelling real-world use case videos showing how the augmented reality device and its apps are helping oil giant Chevron.

For the majority of phones, Android's volume rocker is wrong. A large vocal part of the Android community wishes the volume buttons' default control was the media volume, not the ringer. Although the Galaxy Note 9 is in the "wrong" camp, Samsung has included multiple ways to change it.

The latest sponsored augmented reality experience on Snapchat from a movie studio might be its scariest — and perhaps most popular — yet.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

The fortunes of ARKit and ARCore are still in the hands of developers, who have been increasing the number of mobile augmented reality apps on the market, but perhaps not as fast as companies like Apple might have expected. But one new product is looking to literally kickstart mobile AR gaming by introducing a few key components that harness the traditional board game model.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

Just like cash, bitcoin is used for everything from regular day-to-day business to criminal activities. However, unlike physical cash, the blockchain is permanent and immutable, which means anyone from a teen to the US government can follow every single transaction you make without you even knowing about it. However, there are ways to add layers of anonymity to your bitcoin transactions.

Every once in a while, we find ourselves in a predicament where we need an inexpensive smartphone. Whether we're finally upgrading from that feature phone we held onto too long or we dropped our current smartphone, sometimes we need a quick replacement to get back on track. That's where Android One comes in.

Based on its continued research, it appears Microsoft recognizes that the next HoloLens needs a wider field of view (FoV). Based on a recently-revealed documentation, the company's research team has found another way to accomplish that objective.

While Vuzix is beefing up the processing power of its next-generation smartglasses with the Qualcomm Snapdragon XR1, the company will also give its devices an upgraded display engine.
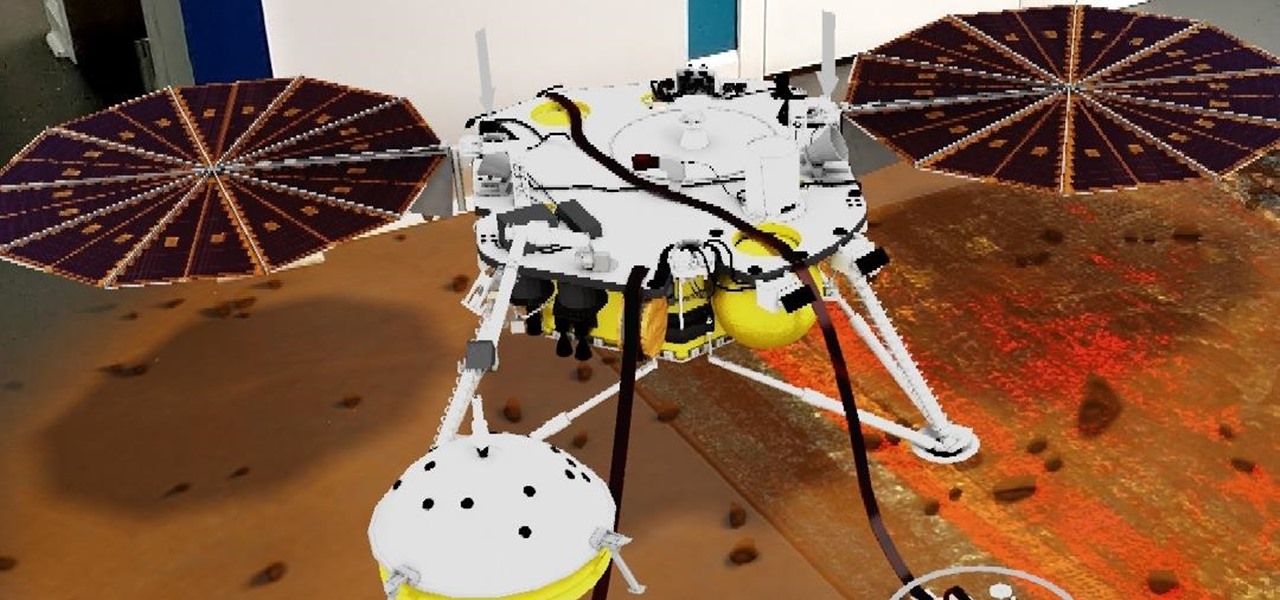
In the latest installment in its burgeoning augmented reality journalism practice, The New York Times is bringing its readers closer to Mars and NASA's latest spacecraft set to travel to the red planet.

While some in the augmented reality space are tweeting about future amazing immersive experiences and others are showing off cool experiments, Microsoft continues to move forward with tangible business solutions right now that show how the HoloLens can improve business.

Beginners learning brute-forcing attacks against WPA handshakes are often let down by the limitations of default wordlists like RockYou based on stolen passwords. The science of brute-forcing goes beyond using these default lists, allowing us to be more efficient by making customized wordlists. Using the Mentalist, we can generate millions of likely passwords based on details about the target.

If bezel-less was the goal of OEMs in 2017, 2018 seems to be the year of the notch. Thanks in no small part to Apple's iPhone X, more and more smartphone manufacturers are designing their displays with this polarizing cutout. While many are frustrated with the trend, it's worth taking the time to consider what each phone gains with the unique design.

The business of enabling the development of augmented reality experiences appears to be as lucrative as AR app development itself.

A report from app data firm Sensor Tower reveals that more than 13 million ARKit apps have been installed on iPhones and iPads within the first six months since the toolkit launched with iOS 11.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.
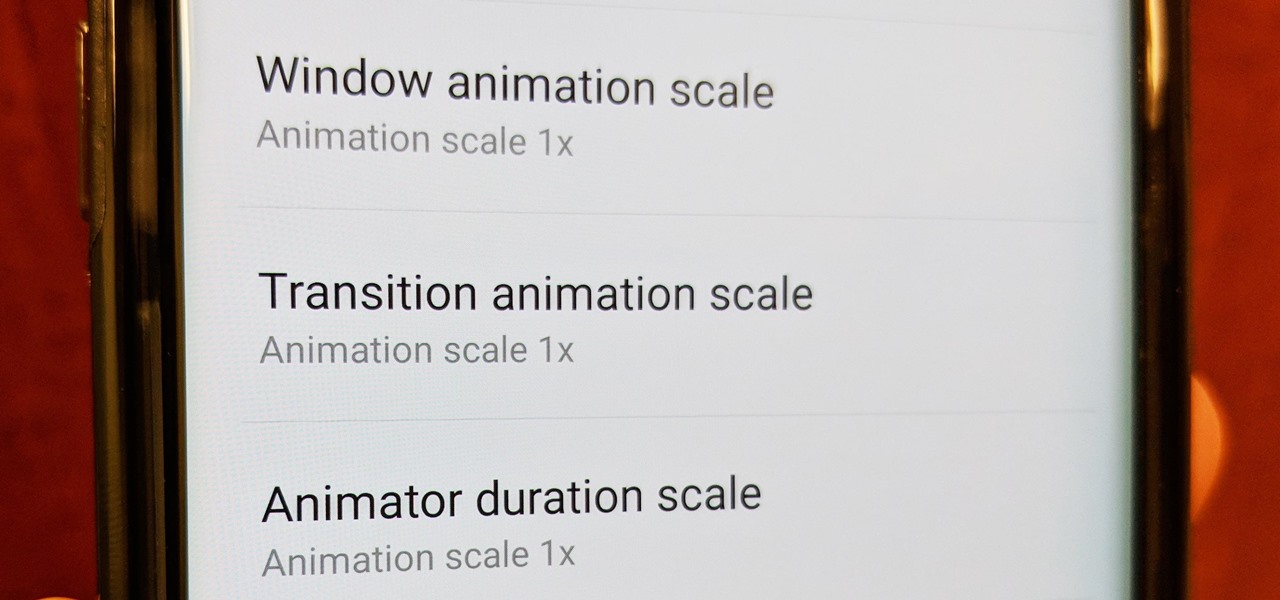
Samsung just launched their Galaxy S9 flagship, with preorders shipping in the US already. The Galaxy S9 is an amazing smartphone, with a number of advanced features. Despite this, over time your S9 or S9+ may slow down a bit more than you would like. Thankfully, there is a longstanding trick in the Android community that can speed things up a bit.

Next to things like natural disasters and disease, the specter of war is one of the only things that threatens to derail the 21st century's long stretch of technological innovation. Now a new app is using augmented reality to remind us of that by focusing on those most impacted by war — children.

Samsung's Galaxy S9 has the best smartphone display among any in its class, beating out the likes of the Google Pixel 2 XL and iPhone X. However, Samsung doesn't unlock the true power of its screen out of the box. To do that, you'll need to rummage through a few settings on your way to maxing out the resolution of your Galaxy S9 or S9+.

Enterprise augmented reality software provider Upskill has raised $17.2 million in its latest round of funding, led by new investors Cisco and Accenture.

While everyone was marveling at the latest drama over at Magic Leap involving employees last week, a major rumor listed in one of the reports, related to the company's flagship device, was mostly overlooked.

Recently, many manufacturers have started offering phones with a clean, stock Android UI. Motorola, Essential, Nokia, and OnePlus are probably the biggest names that have listened to user feedback and shifted more towards AOSP. But if your phone still has a bloated OEM skin, there are a few things you can do about it.

As the third-largest smartphone manufacturer in the world, Apple devices are a constant target for hackers everywhere. While iOS has seen fewer common vulnerabilities and exploits (CVEs) in recent years, iPhones still aren't hack-proof. Fortunately, you can strengthen your security with the help of a few apps.

With the release of the iOS 11.3, iPhone users have new features to both sift through and look forward to, such as increased battery health information and control, new Animoji on iPhone X, and Health Records in the Health app. A smaller change with the update, however, is also a useful one — a new way to sort App Store reviews.