On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

Defcon is the largest hacker conference with something for everyone, whether it be the talks, parties, villages, or any of the hundreds of events. In this guide, we'll take a holistic view at everything that goes into attending the con for the first time, from securing your electronics and making the most of your time to the logistics of getting there and finding the right place to stay.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Smartphones are still "phones," which means communicating with others is usually a primary use. Ranging from a simple "hi" to a more personal conversation and even sharing passwords, our messages should remain private so that only the intended recipient sees their content. While many apps tout end-to-end encryption, not all apps prioritize security and privacy.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.

Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

In the previous article, we learned how to set up our VPS, configure our PHP server, and developed an in-depth understanding of how the payload works. With all that taken care of, we can get into disguising our payload to appear as an image and crafting the note in the greeting card being delivered to our intended target.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

As a developer, before you can make augmented-reality robots that move around in the real world, controlled by a user's finger, you first need to learn how to harness the basics of designing AR software for a touchscreen interface.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Over the years, the internet has become a dangerous place. As its popularity has increased, it has attracted more hackers looking to make a quick buck. However, as our dependency on the web grows, it becomes increasingly difficult to sever all ties. This means we have to protect one of our weakest points, the password.

From Farmville to selling a company to Google, Amitt Mahajan has been through the startup ringer. Now, as managing partner with Presence Capital, he's funding the future of augmented and mixed reality.

It always looks different when it's not about you. The Internet is our world's Alterego. Those many bits don't really make sense unless we want them to be valuable, to mean something.
Welcome back Hackers\Newbies!

One of the best things about Christopher Nolan's Batman trilogy is how realistic he makes the caped crusader feel. Unlike the Joel Schumacher or even the Tim Burton versions, Nolan's world seems grounded in some level of scientific fact. But just how close is science to actually being able to replicate some of the Dark Knight's gadgetry?

To some, SCRABBLE is just a board game to play during family game night or during a casual get-together. Others think of SCRABBLE as a mere hobby. But with any activity, there will always be fanatics—the ones who would rather sell their soul than stop—the ones with a constant yearning for self-improvement—the merciless.

The biggest update to arrive since iOS 18 and iPadOS 18 just came out, and it's packed with new features and changes for your iPhone or iPad. From new Apple Intelligence capabilities to Game Center improvements and new calling tools, there's a lot going on in iOS 18.1 and iPadOS 18.1.

What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underrated gem in iOS and iPadOS can offer you.

With iOS 17, Apple News integrates more deeply with Apple Podcasts and Apple Stocks and has become a bit more fun thanks to new crossword puzzles. But that's not all that appears in the updated News app.

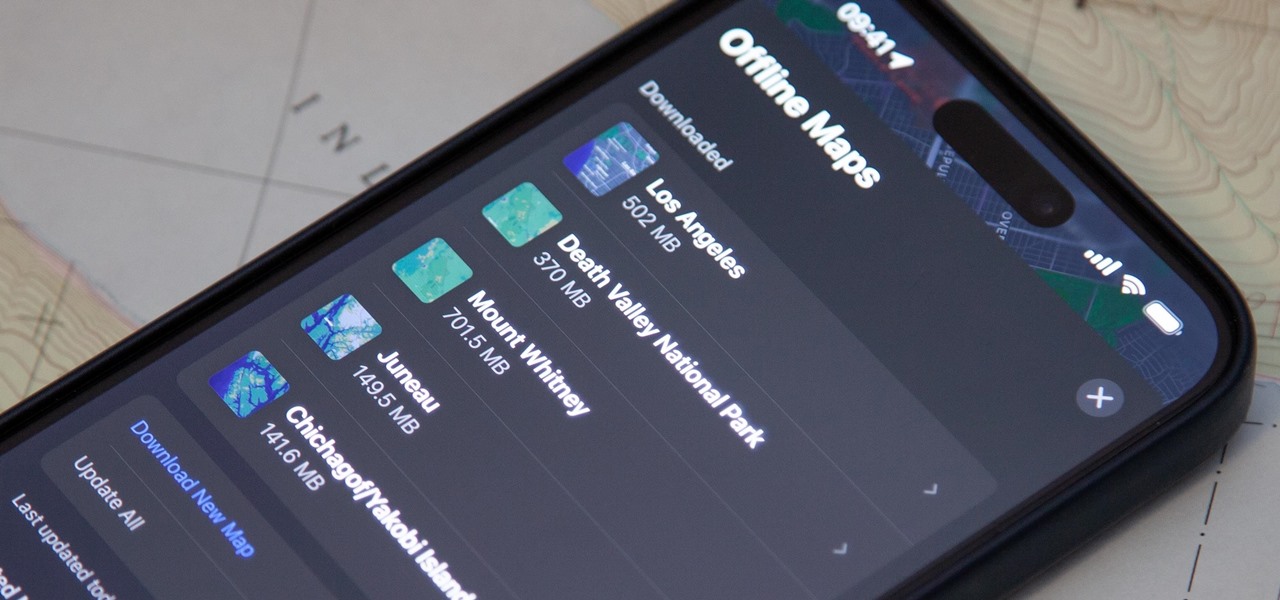
Offline maps help you get around an unfamiliar area whenever you anticipate encountering bad cellular reception and no internet connectivity. Google Maps and other map apps have had offline maps for a while now. But Apple Maps only had a little-known caching workaround to produce something even remotely similar to full offline maps — until now.

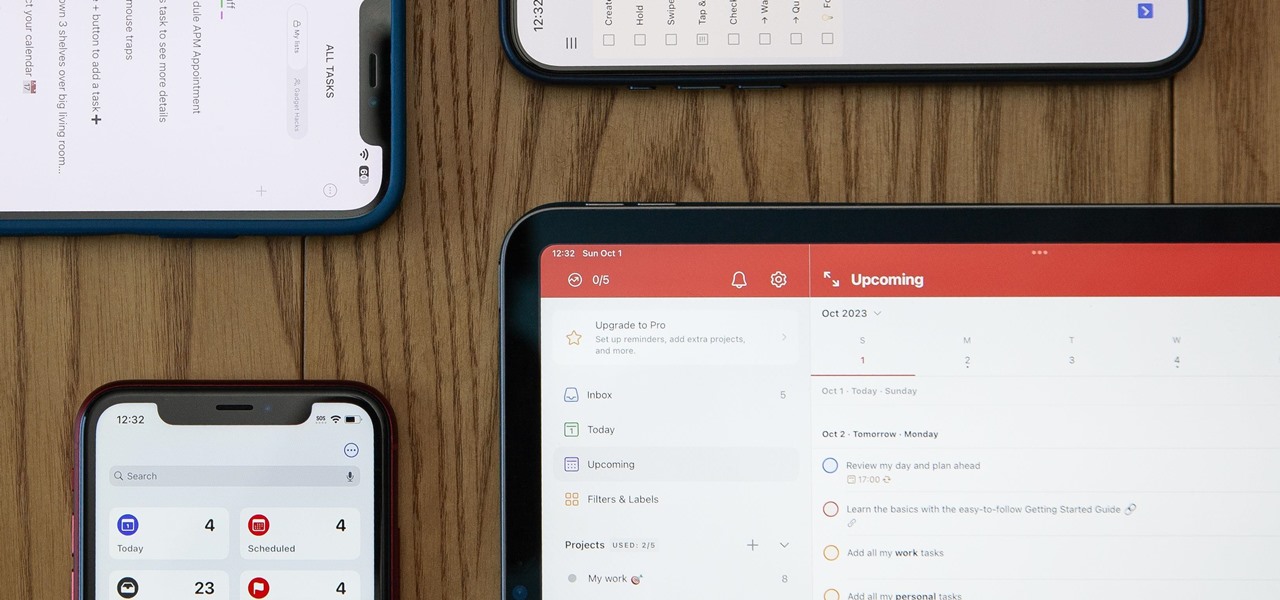
When you want a helpful task manager on your iPhone or iPad, any of the nine apps in this guide should be at the top of your list. But we'll review each app's features to help you determine which one might be best for your workflow.

You might have missed it, but the virtual keypad you use to enter phone numbers in your smartphone's dialer and contacts app isn't all numbers. Take a closer look, and you'll notice a few mysterious buttons you've likely been tuning out unconsciously. But it's time to stop ignoring them because each has a particular purpose that could come in handy one day.

While the iPhone came before the first Android smartphone, every new iOS version seems to include a wealth of features already existing on Android, and iOS 17 is no exception.

While the Maps app hasn't received as big an update in iOS 16 as Books, Messages, Photos, and Weather did, there are still quite a few exciting new features to enjoy on your iPhone.

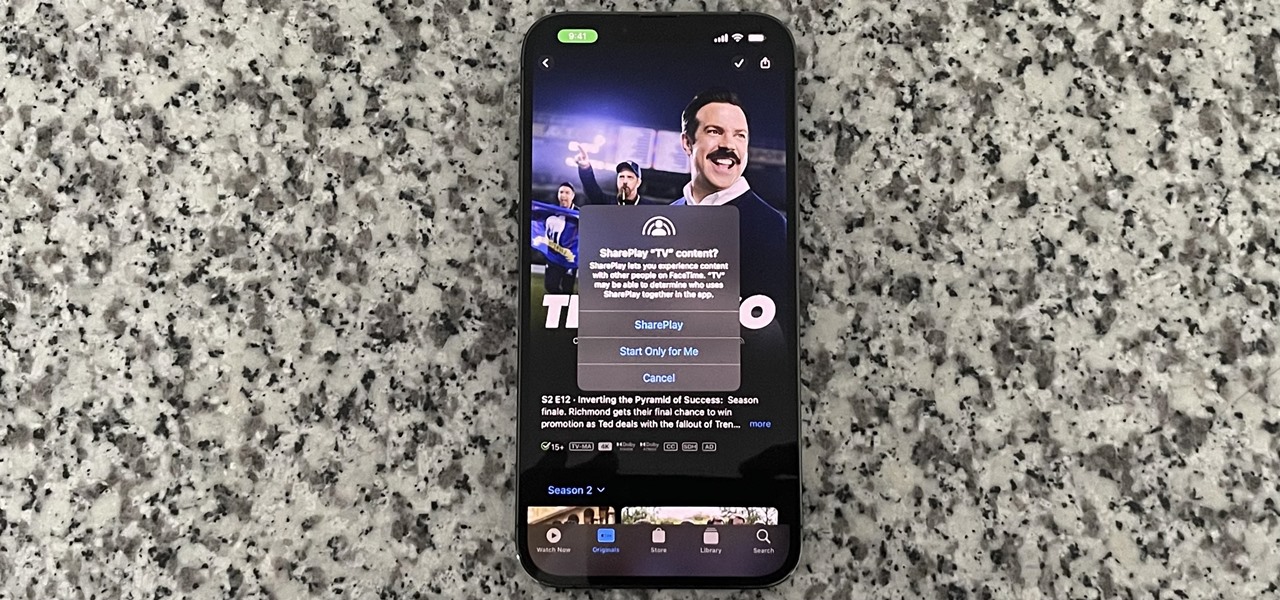
SharePlay is arguably one of the most significant features to hit FaceTime since group calls, and it's still hard to find apps that support shared experiences in FaceTime. Apple does list a few apps, but there is no official index of all the apps with SharePlay integration. That's where we come in.

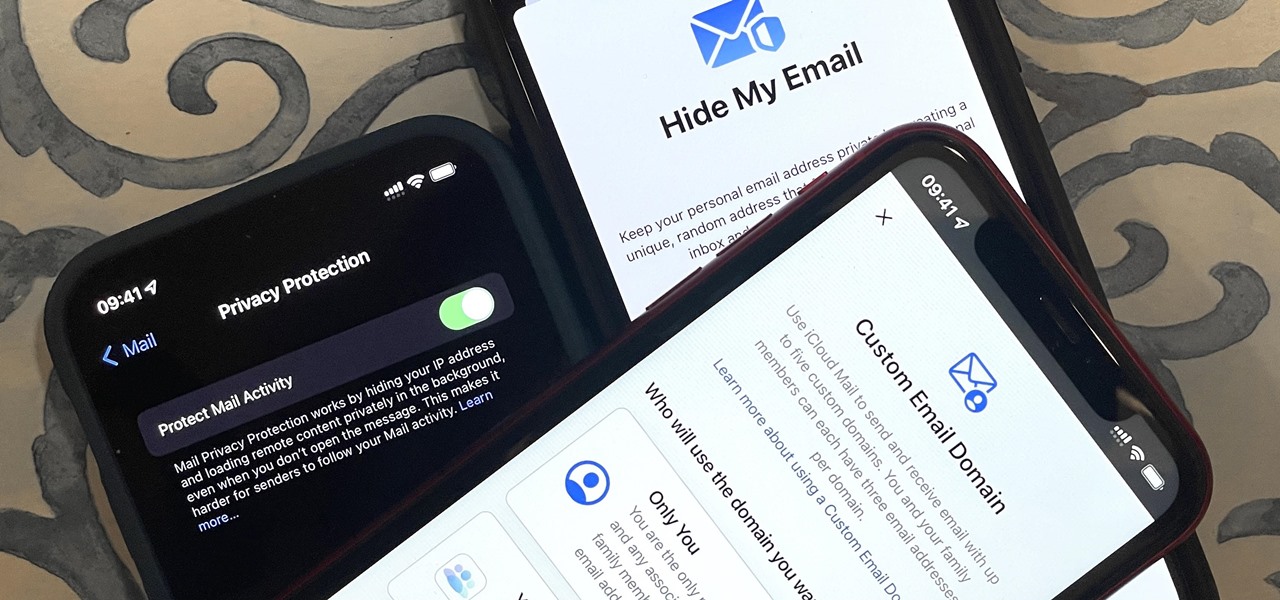
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

The iPhone has included a real-world magnifying glass called "Magnifier" since iOS 10. Still, it remained relatively obscure until iOS 14 when it received significant upgrades such as a new interface, hideable controls, a customizable toolbar, improved filters management, multi-image shooting, and people detection. But one of the best things about the update is that you can open it more easily.

Android 12 was released to the Google Pixel devices on Oct. 19, 2021, so anyone with a Pixel 3 or newer model can install the new operating system with an over-the-air update. The AOSP version of Android 12 was released a few weeks earlier on Oct. 4, so OEMs could use or modify the source code on their smartphones. So, what devices have or will have Android 12 then?

It's already been a banner year for mergers and acquisitions in the augmented reality industry, with WaveOptics and Ubiquity6 among the notable companies acquired. Two of the more active M&A players, Snap and Epic Games, continued their respective buying sprees this week with major deals supporting their AR strategies.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

Facebook's annual earnings call on Wednesday didn't come with any big surprises, that is, if you took everything at face value.

Your iPhone keeps track of every single place you go, especially those you frequent most often, and syncs those locations across all your iCloud-connected devices. People who gain access or already have access to your iPhone, iPad, iPod touch, or Mac may be able to view all of these locations to see where you've been and where you might be. If this worries you, there are things you can do.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

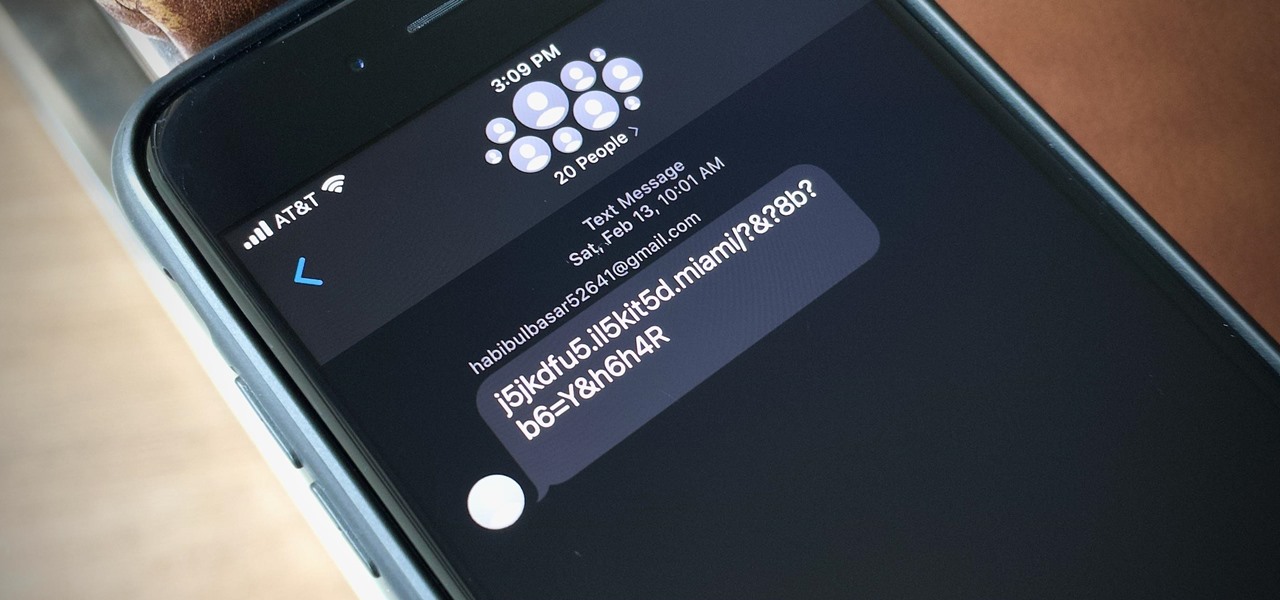
Next to spam calls, few things are more annoying than being inundated with spam, scam, and smishing texts. Your iPhone's Messages app should be a place for your friends and family to stay in touch, not a minefield of phishing attacks, malicious links, and viruses. Luckily, there are quite a few methods to block and report your way to a more spam-free iPhone.

Most packages sent to you via delivery services include a tracking number that allows you to track it from the creation of the shipping label all the way to your doorstep. The U.S. Postal Service includes tracking information with many of its mailing services, but not for first-class mail or periodicals. Luckily, there's a workaround to that limitation that you can set up pretty quickly.