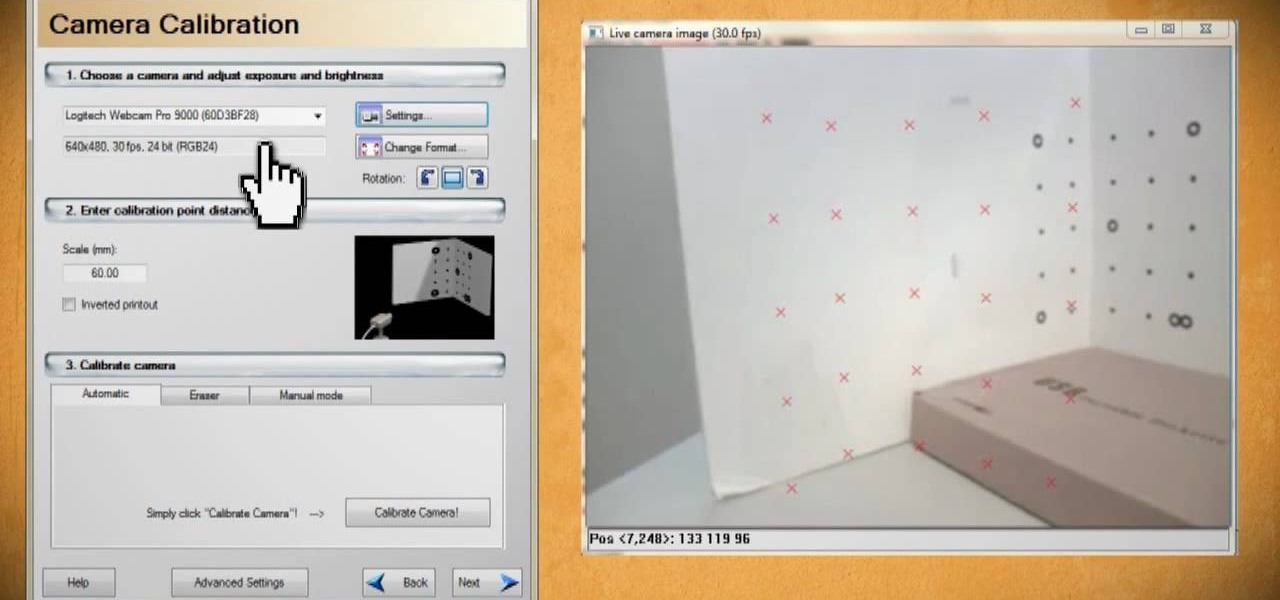
Scanners have been around for a while. They allow us scan photos and documents into digital versions that are a lot less susceptible to damage over time. But what if you want to digitize the memories of something that isn't 2D? With this hacker's how-to, you'll learn a method for making a 3D scanner. To follow along, you'll need a computer, a printer, a web cam, white foam board and a laser pointer.

ProjectKinectMagicMirror combines augmented reality and CT-scan imagery to create a virtual "X-ray machine." Another amazing Microsoft Kinect hack to add to the vault. The ingenuity is infectious... Get inspired. Make-your-own.
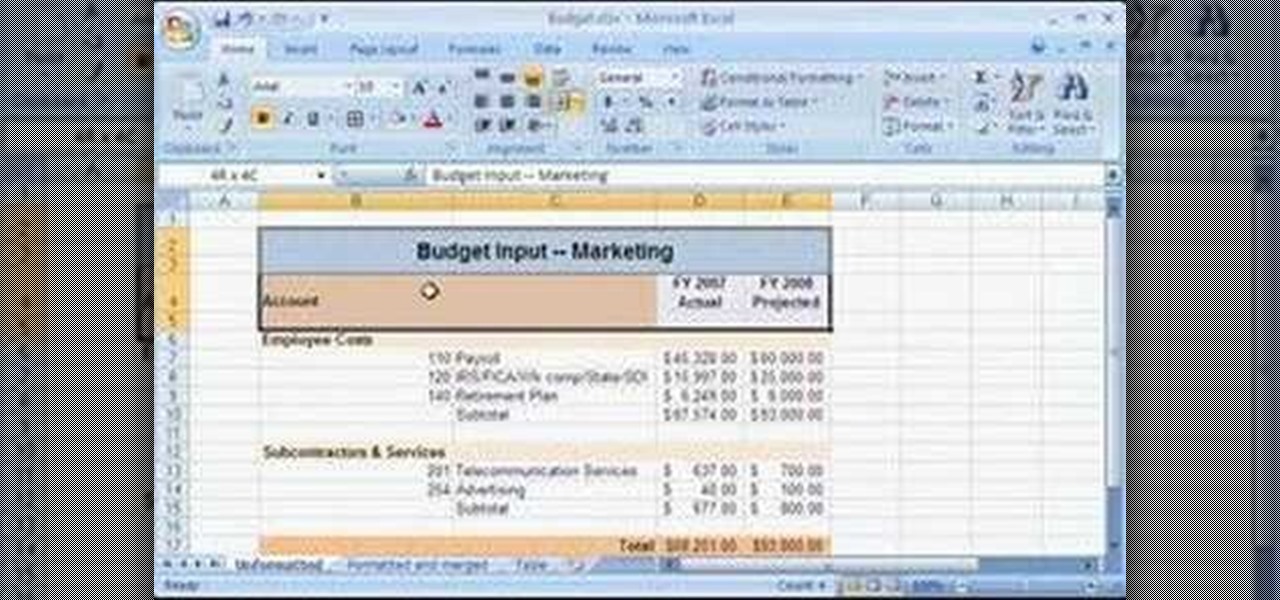
Using the Merge feature in Microsoft Office Excel 2007, you can quickly turn that worksheet into an easy-to-scan, appealing report. When you merge cells, you join several adjacent cells into one larger cell. Check out this tutorial and learn how to adjust the position of the contents of the merged cell and add borders and background colors.

Sometimes you need to add things to your photographs and scanned documents. Usually we add text and that's cool. However, in this tutorial we'll go beyond text and learn the differences between shape layers, paths and pixel filled shapes.
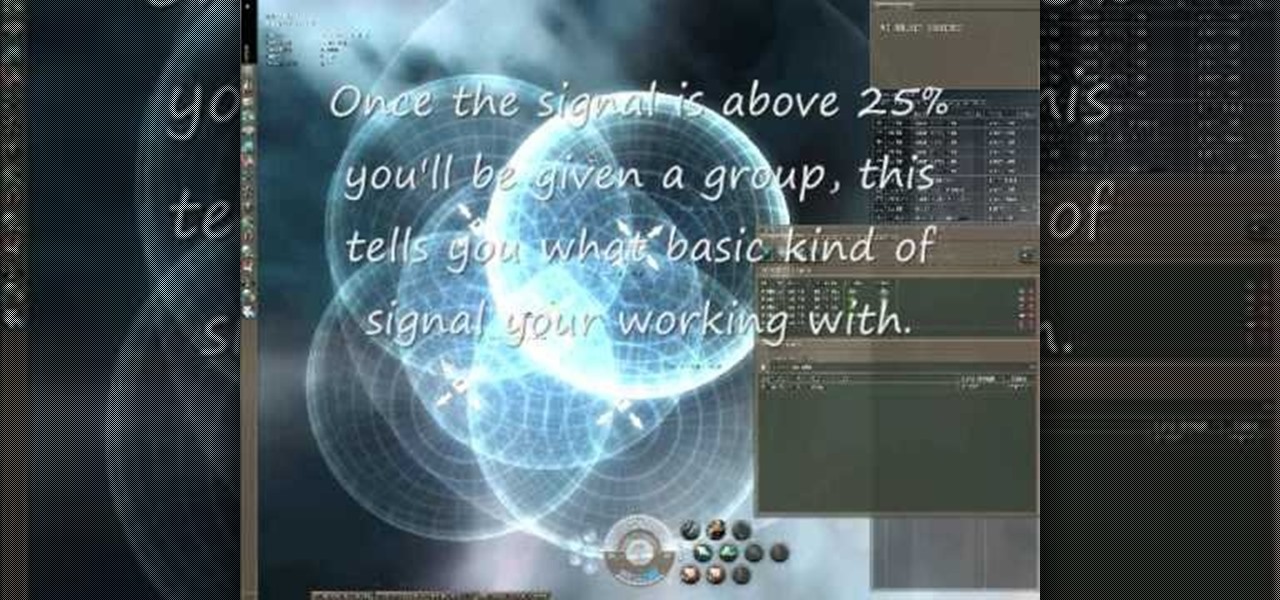
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.

Have you ever heard of tradigital art? Tradigital art incorporates traditional materials with digital media. This is a combination of such techniques as illustration with Decocolor Markers, Prismacolor Markers, pencils, and Photoshop. Watch this tutorial to learn how to enhance traditional art methods with digital media. It illustrates the tradigital process step-by-step. Make sure to pause the video after each step and look at the screen every few seconds while you are drawing.

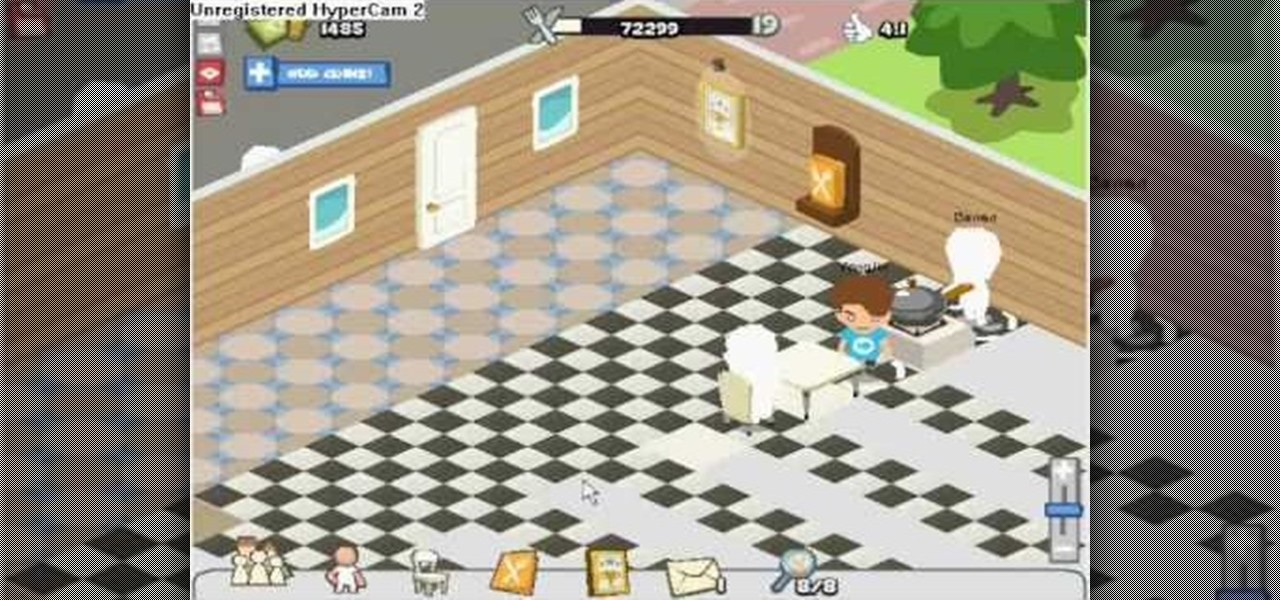
This is a Restaurant City 3 in 1 Hack (Working From 12th May 2009).

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.

While other devices are moving away from fingerprint scanners (cough, iPhone X), for many, a fingerprint scanner provides the best balance between security and speed. Typically, the rear fingerprint scanner on the LG V30 is quick and accurate, but every so often the phone will not recognize a registered fingerprint.

With iOS 11, Apple's very own Notes app will now come standard with a number of new features that aim to make it significantly more user-friendly and help it compete against more popular notepads like OneNote and Evernote.

There are a ton of new features in iOS 11, but some of the best ones, in my opinion, are in the Camera app. They're not huge features, but they're much appreciated to anyone who's ever taken a Live Photo or portrait, or even to those who've needed to scan a QR code quickly.

This method can be used on any kind of scroll saw pattern. Animals, people, inanimate objects, etc. Done on paper and scanned onto my computer only to clean them up and color them in to display. Three part series.

This video will show you how to install and clean your PC with PC clean tool winutilities. This will help you scan your PC for deleting temporary files and make your computer faster.

Welcome back, my novice hackers! My recent tutorials have been focused upon ways to NOT get caught. Some people call this anti-forensics—the ability to not leave evidence that can be tracked to you or your hack by the system administrator or law enforcement.

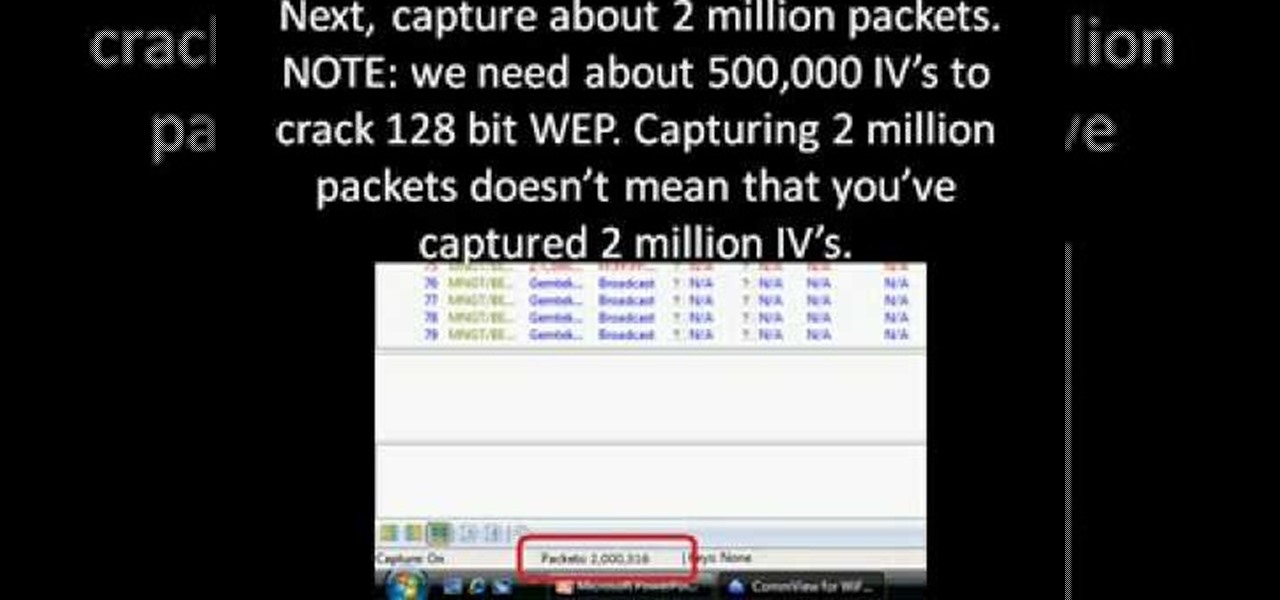
First you need to download Aircrack-ng and Second thing you need to download is CommView for Wi-Fi. Now you have to install CommView for Wi-Fi and then install the right driver.

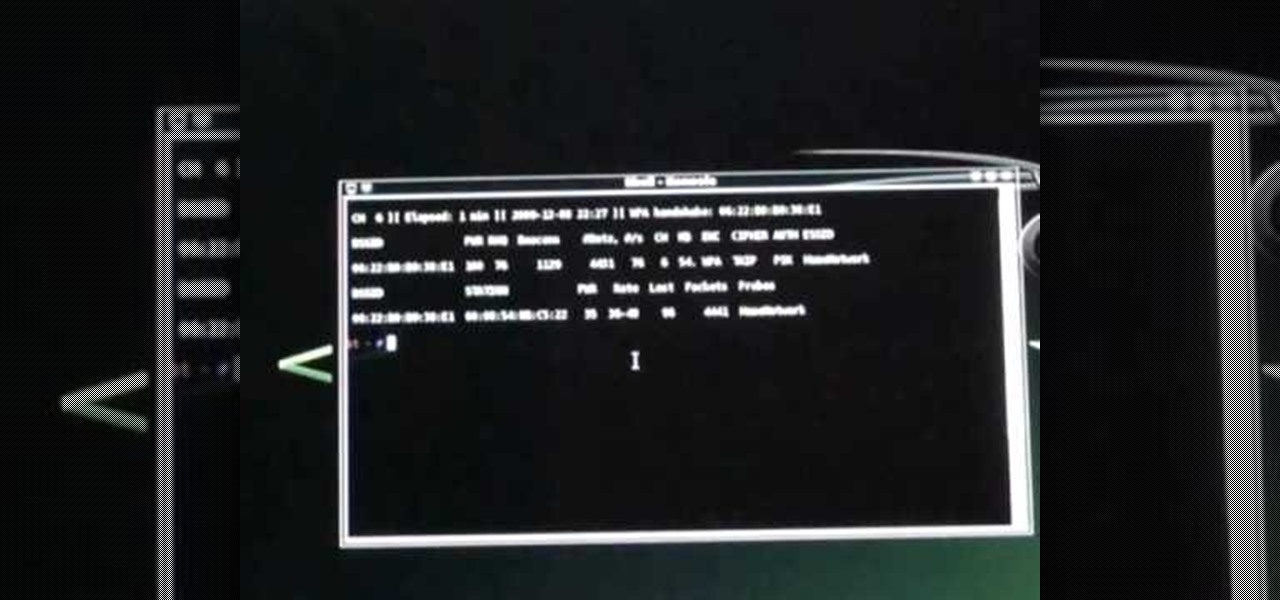
In this video we learn how to crack WPA using Back Track. The first step is the boot into Back Track using a VMware Virtual Machine Image. Next you need to open a shell console. In the console you will type "airmon-ng" and press enter. This does a check to find the wireless guard interface name. Next, type "airodump-ng wlan0" and press enter. This will tell it what wireless card to use and scan for wireless networks. You are looking for the one that comes up WPA. Copy the MAC address then typ...

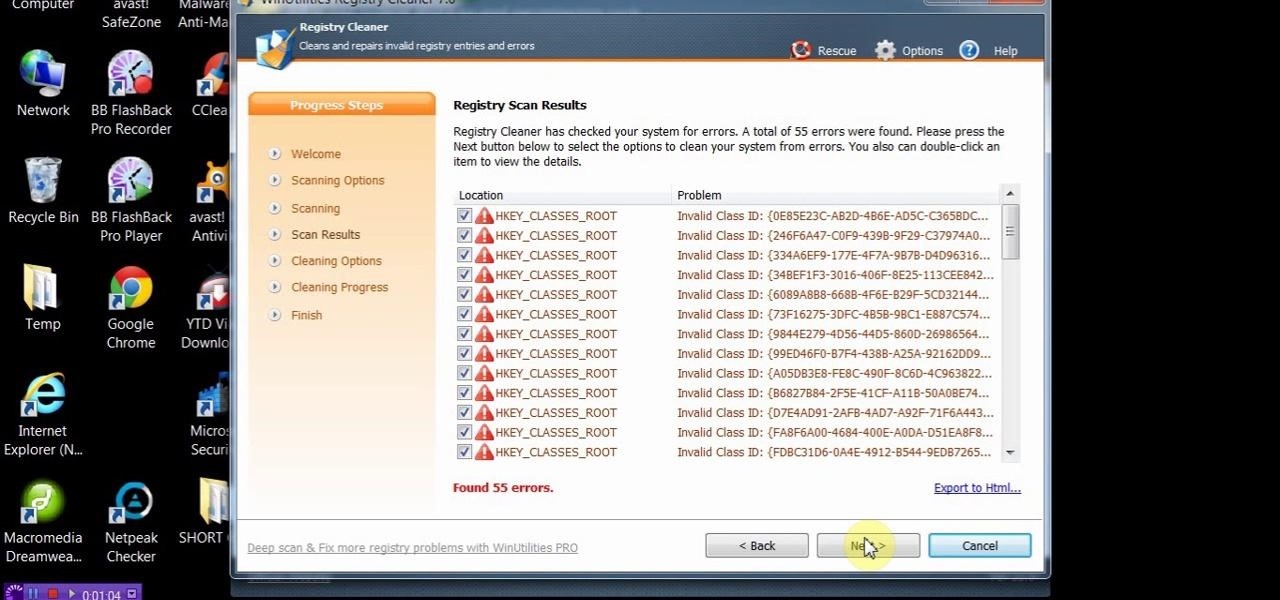
Some times malicious programs can infect your registry and fill it with lots of unwanted information. You may need to clean it to prevent the virus from causing any further damage to your computer or to even disable the virus. It is a very lengthy and complex process to do this manually. So you will need to use one of the powerful free tools available online. Hijack This is one of the most powerful program that can be used for this purpose. So go the website and download this free tool. Insta...

Cheat Engine will help you win on Fish World! A little hacking never killed anyone, but it has made them richer, so see how to hack Fishworld now with this awesome Facebook Fish World cheat.

Are your fish starving? If they are, you need to do something about it, and quick. Well, there's no quicker solution to feeding your fish than hacking Happy Aquarium with Cheat Engine.

As Shakespeare said, "All the world’s a stage" – step on up and play your part! You Will Need

How to hack Pet Society! Pet Society cheats, tricks, hacks. Watch this video tutorial to learn how to hack gold in Pet Society (09/29/09).

This might be an old hack for Happy Aquarium, but for some of you it may still work. Most of you will not be able to do this, but it's always worth a shot, right? It's a cheat from 9/29/09 (wow!—retro hack) for which you need Cheat Engine 5.4. Newer versions of Cheat Engine should work, too.

Here is a cheat guide to having more pupils or faster levels in MyBrute. You can play this game at least 5-10 minutes a day!

Animate drawings by scanning them and painting them on the computer. Learn how to scan and color hand-drawn animations using Adobe Photoshop and Flash in this free computer art lesson from a professor of animation and interactive media.

Watch this automotive video tutorial to see how to scan your automobile for diagnostic trouble codes.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Websites are often misconfigured in ways that allow an attacker to view directories that are not ordinarily meant to be seen. These directories can contain sensitive information such as private credentials or configuration files that can be used to devise an attack against the server. With a tool called Websploit, hackers can scan targets for these hidden directories without difficulty.

From day one, my favorite thing about the Magic Leap One has been its portability. It's so well designed that it just screams to be taken out for a walk through the city. Alas, Magic Leap says the device is (currently) designed to be used indoors, preferably in settings containing few windows or black surfaces.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome Back !! TheGeeks. SQL Injection (SQLI) Part-1

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.

Your heart is constantly work for you, yet you think nothing of it—and Samsung wants to change that. They stuck a dedicated heart-rate monitor on the Galaxy S5, they're putting one in the upcoming Note 4, and they're bound to slap one in every Galaxy device thereafter.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

How to use Teflon tape for plumbing applications. I know it sounds simple but there are a few tricks to applying the Teflon tape. Teflon tape is also known as PTFE Tape.

Video: . How To Use a Tampon

If you're a medical student, you'll learn a lot from this video lesson on examining your patient's eyes. If the patient is having trouble seeing, like double vision, blurred vision, pain or any other problem, a proper eye examination is detrimental to properly diagnosing and treating him/her. You can also determine and potential problems which may arise bases on your family history. Watch to see the complete procedure outlined, which is great for any med student or doctor. Even nurses can ben...