In this video we learn how to use EyeTV to stream live TV on your iPhone. This will allow you to watch TV on your Mac and your iPhone as well as on a 3G network for free. To get started, plug one end of the EyeTV into the USB plug and then into the jack on the hybrid with a cable line. Now, download the most recent version of the software from the update menu. Then, go to preferences and select iPhone. After this, make sure all the buttons are selected, then exit out. Now go to your iPhone an...
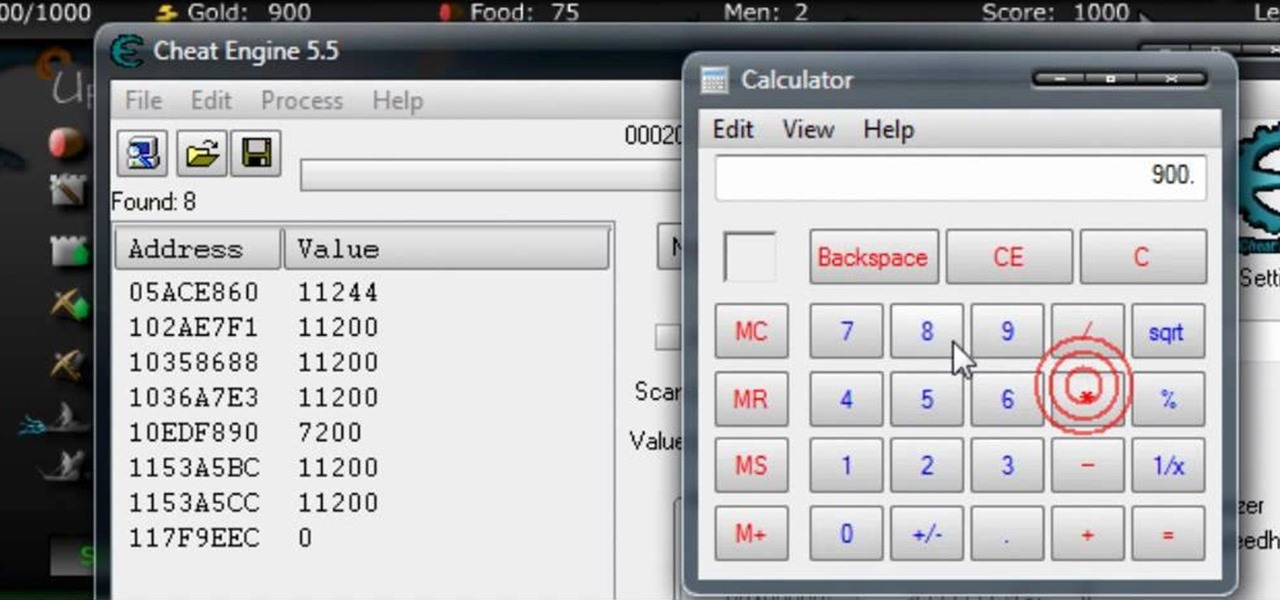
Users will need to use Cheat Engine version 5.5. This hack will increase the gold and food amount. Begin the game and play at least 2 levels to earn some gold and food. Open Cheat Engine, click one the computer icon and select the internet icon. Multiply the amount of gold or food by 8. Type the number in the Value bar and click First Scan. Buy anything in the game, multiply the new amount by 8 and put the number in Values. Check the frozen box below and add a new value (should be a divisible...
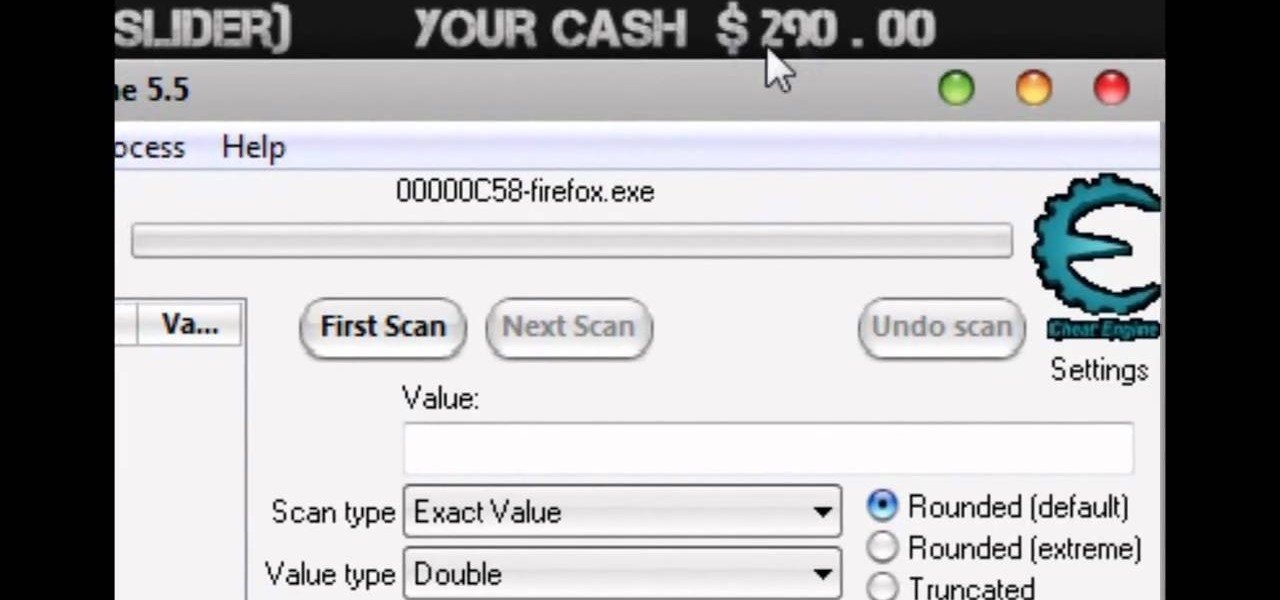
In this video tutorial, viewers learn how to hack the flash game, Palisade Guardian 2: Modern Combat with Cheat Engine. Begin the game by entering your name and play the first level. After that, open up Cheat Engine and select your internet in the process list. Change the Value Type to Double and Truncated to Rounded (default). Enter in the value of your cash and press First Scan. Then buy something to lower your cash and enter in your new value. There should be only 1 address. Check the froz...

Studying to be a nurse? Then here is a nursing how-to video that teaches you how to check a patients blood sugar level at their bedside. Every nurse should know the basics of this technique, follow along and see how easy it is to check blood sugar levels with a Life Scan monitor. Monitoring a patient's blood sugar level is important to their health, and it is very simple to do at their bedside. These medical tips are sure to help you pass your nursing exam with flying colors.

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).
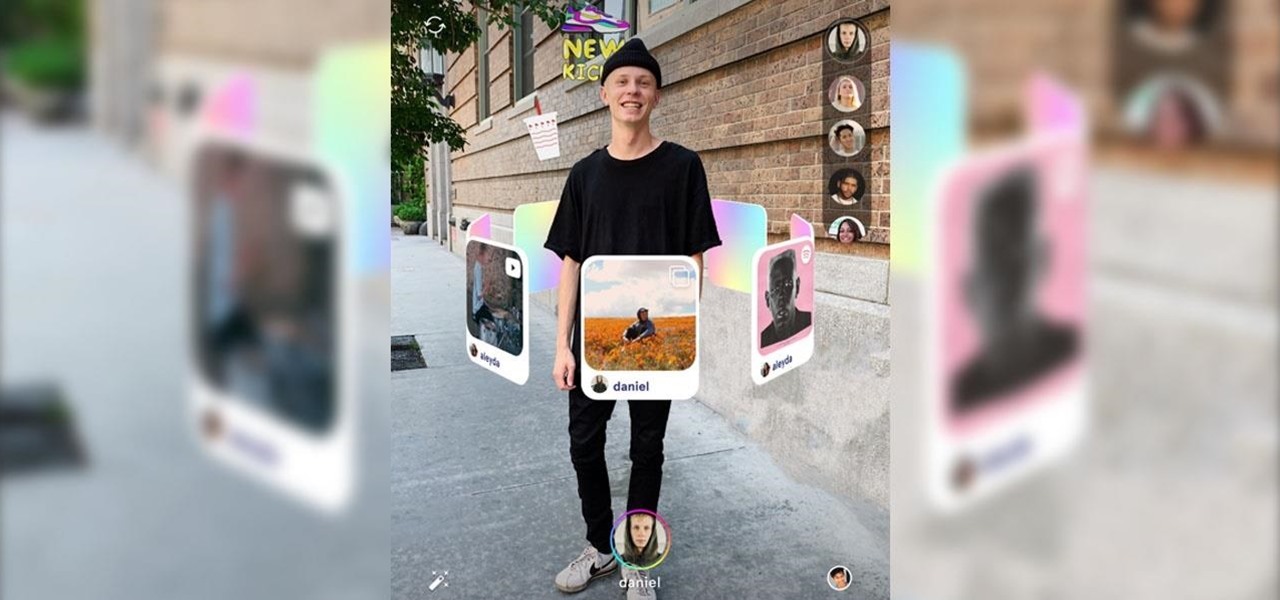
In a world full of augmented reality camera effects apps, one app is going in a more social direction.

Pokémon, Google, and augmented reality go together like wasabi, soy, and ginger, and the trio has come together again for the release of the latest game from the Pokémon universe.

After getting its start with models of augmented reality planets that serve as targets for augmented reality experiences, AstroReality is diversifying its portfolio by paying tribute to one of the space agencies that made its products possible.

Face ID does an excellent job with keeping your iPhone safe, boasting a million-to-one odds against unauthorized access when compared to Touch ID, which is 20 times less secure. However, it's far from being truly hands-free, as you still need to swipe up the lock screen once it detects your face to access apps. But if you have a jailbroken iPhone X, this issue can easily be remedied.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

When traveling or sightseeing, you may come across a landmark you can't quite identify and want to know what exactly it is and the history behind it. It could be a building, waterfall ... anything. If there are no signs around or they're in a different language, you'll have no idea what you're looking at. Fortunately, Google Photos can be your personal tour guide with the power of Google Lens.

Badges? We don't need no stinkin' badges! That is, unless they have augmented reality content embedded in them and give us full access to Facebook's annual F8 developers conference — in that case, yes, we'll take all the badges.

Instagram is no stranger to stealing features from Snapchat. Stories, originally a Snapchat invention, feels more at home with Instagram today. Now, Instagram is attempting to repeat this feat with nametags, a way to quickly add new friends akin to Snapchat's Snapcodes.

If you're playing word association with the terms "augmented reality" and "automobiles," your first thoughts probably center on navigation displays in cars or virtual models of exotic vehicles.

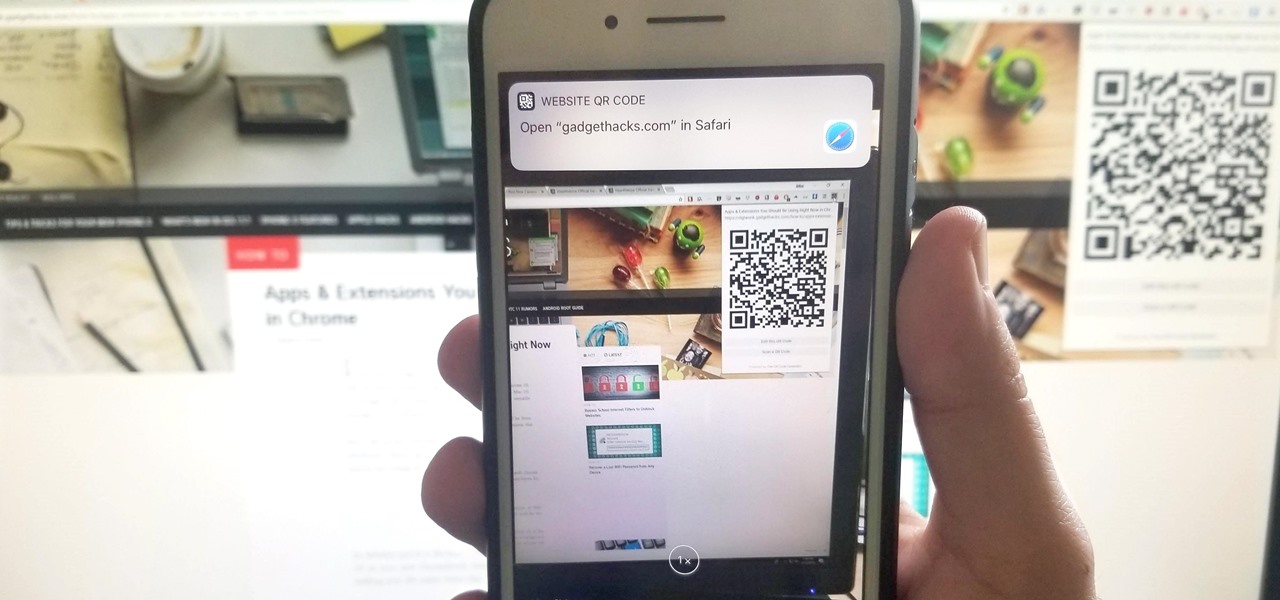
If you have a Mac, you can use Apple's Handoff feature to open one of your Safari desktop tabs in Safari on your iPhone. But if you prefer to use Google Chrome as your desktop browser, whether or not that's because you have a Windows PC, you can't "hand off" open tabs from Chrome desktop to Safari on your iPhone. There is a cool workaround, however.

When Apple unboxes the next major update to its mobile operating system this spring, iPhones and iPads will gain some significant new features for augmented reality experiences: verticality.

Fans of The Walking Dead can now kill time until the series returns from its winter hiatus by raising walkers from the labels on bottles of wine influenced by the show.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

On Friday, game developer PreviewLabs released the first online multiplayer game for the Microsoft HoloLens.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.

Japanese footwear brand Onitsuka Tiger and fashion label Anrealage have teamed to produce the world's first augmented reality sneakers. The shoes — called the Anrealage Monte Z — look like a regular pair of sneakers until you view them through Anrealage's new AR app. Once viewed through the app, they become unlike any pair of sneakers that have ever existed.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

If you thought the selfie would only ever be used to bombard your feed on Instagram, you were wrong. Dead wrong. JetBlue is looking to take those selfies and use them to check you in for your next flight.

Over a billion people use WhatsApp, which makes it the most popular standalone messaging service out there. But if you're one of the many people whose group of friends relies on WhatsApp for all communication, chances are, you have several years-long messaging threads with all sorts of random pictures and GIFs cluttering up the place.

With Touch ID enabled, your iPhone needs to scan your fingerprint before you can access your home screen or last app used. Before it unlocks, your iPhone might request that you press the Home button, adding an unnecessary step between you and your data. However, you can turn the feature off so that you don't need to click any buttons to unlock your device.

When Google released the Nexus 5X and Nexus 6P, they added official support for fingerprint scanning to Android's main code base. On the surface, this was done to ensure that the fingerprint scanner in their own devices could be used to its full extent, but because it was added to AOSP, this meant that the new Fingerprint API could be used by any Android manufacturer.

Welcome back, my hacker novitiates! Often, to hack a website, we need to connect to and exploit a particular object within said website. It might be an admin panel or a subdirectory that is vulnerable to attack. The key, of course, is to find these objects, as they may be hidden.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

In general, the fingerprint scanner in Samsung's 2015 flagship phones is quick and accurate, but when you get that "No Match" message while trying to unlock your phone, it can be incredibly annoying. To help curb these issues, I'll go over three tips for speeding up the unlocking process that should work wonders on your Galaxy S6, S6 Edge, S6 Edge+, or Note 5.

If you have a specific app you want to lock so that others can't access it, the most secure way of doing so is with biometrics. While there are options to lock apps with either a PIN or pattern, these can easily be figured out with a simple glance over your shoulder. It's much more difficult for someone to crack your fingerprint ID, unless they chop off your finger, of course.

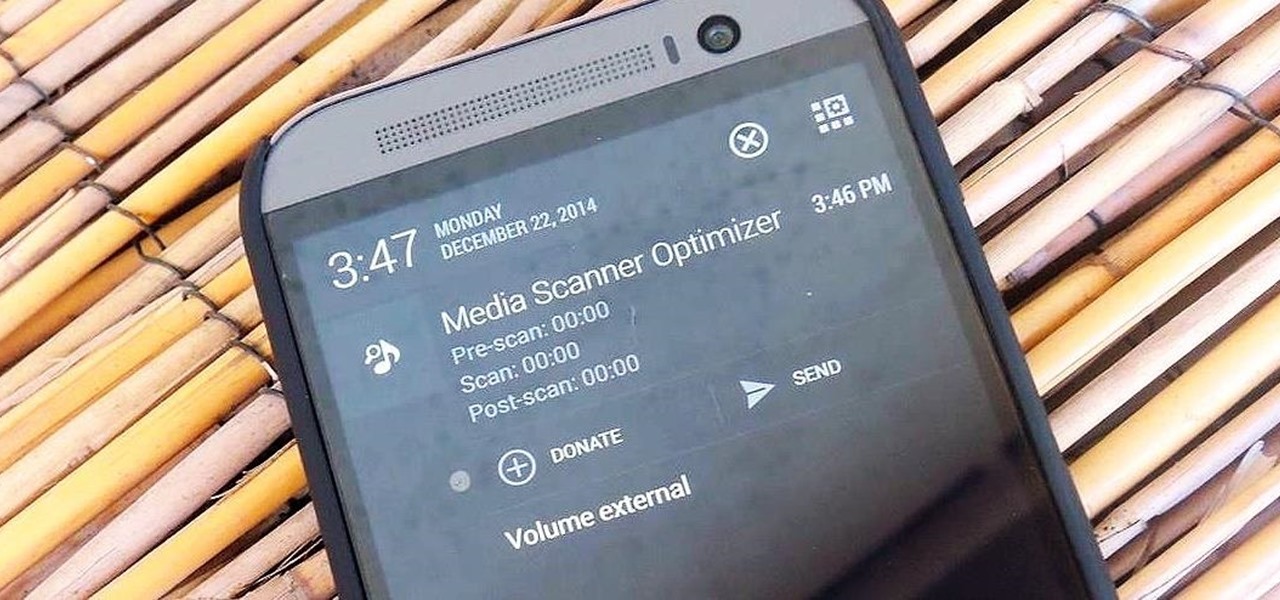
Battery life is extremely unpredictable on an Android. Finding the right ROM and kernel combo can make or break having the kind of battery that will last you all day long. Even if you do find the perfect pair, you then have to worry about apps, widgets, and other processes constantly waking your phone and draining your juice. While your media scanner isn't the biggest battery hog out there, it can definitely take a chunk out of it.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

Unless you've been living under a rock with no internet connection, it's safe to say that you've heard of the Heartbleed flaw that allows practically anyone with the right knowledge to steal your personal information, such as passwords, credit card numbers, and e-mail addresses using OpenSSL.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

Most of us have some sort of malware scanner or antivirus program on our computers, but what about our smartphones? A lot of people don't realize that computers aren't the only devices that are susceptible to malicious software and apps—they can follow you on your smartphone or tablet, too.

Peggy Erbison shares her knowledge of palmistry in this video. The heart line starts under the pinky and moves across and up towards the middle and index finger. The next line she talks about is the head line. This line is the center line that explains how your thinking is. The line that rounds out and wraps around the base of the thumb is the life line. This line connects to the head line at the beginning. These are the 3 main lines on the palm. Contrary to popular belief, the life line does...

In this Autos, Motorcycles & Planes video tutorial you will learn how to Read a tire sidewall. By understanding the information on the tire sidewall, you will come to know what is the tire size, speed rating and when it was manufactured. First look for a combination of letters and numbers. For example, P205/55R16 89V. ‘P’ implies passenger car tire. Some light trucks may also have ‘P’ or ‘LT’. if there is no letter, the tire is designed to Euro standards. 205 is the overall width of the tire ...

In this tutorial, we learn how to access XM satellite radio in a 2010 Prius. To access this feature, press the "sat" button the dash or the "sat" button the steering wheel. You can also use the voice recognition button on the steering wheel by saying "satellite radio" out loud after pressing it. You can search for music by channel or use the type scan button while in audio mode to find the type of music you prefer. There are a variety of channels offered, look at your channel guide to find th...

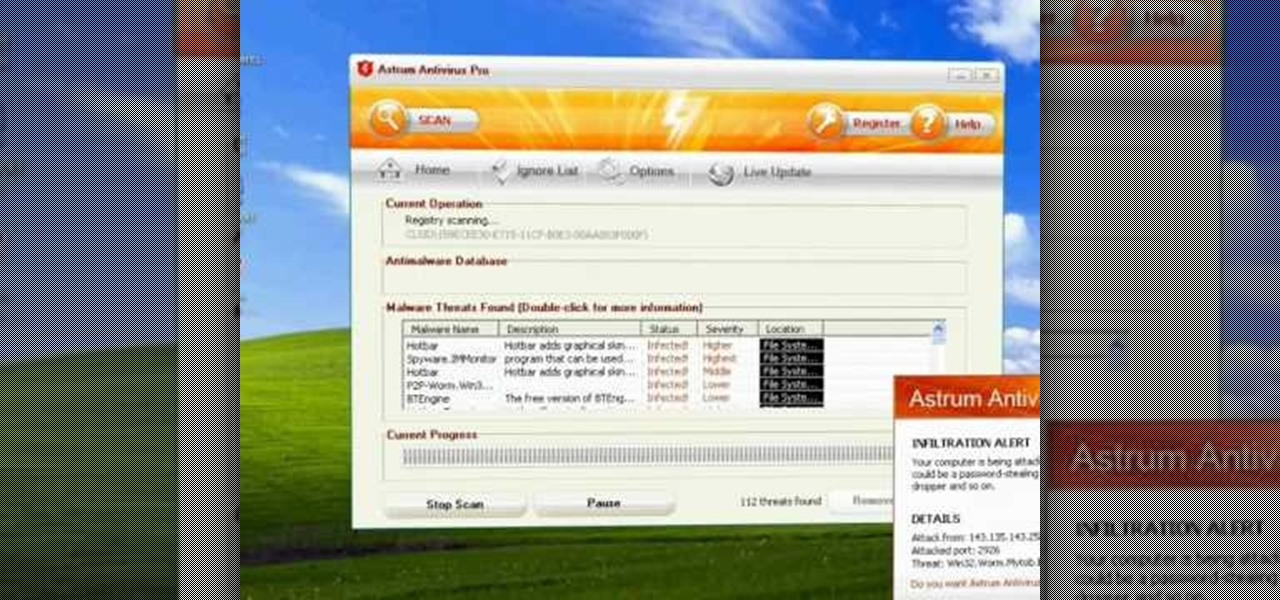
Astrum Antivirus Pro is a rogue anti-spyware application and a clone of VirusTrigger and Antivirus Trigger. Astrum Antivirus Pro is often downloaded and installed by a Trojan or through browser security holes. Astrum Antivirus Pro may generate large numbers of popup adverts. Astrum Antivirus Pro will also display notifications of imaginary security risks in its attempts to get the user to purchase the full version. Astrum Antivirus Pro may run a fake system scanner and then display fake syste...

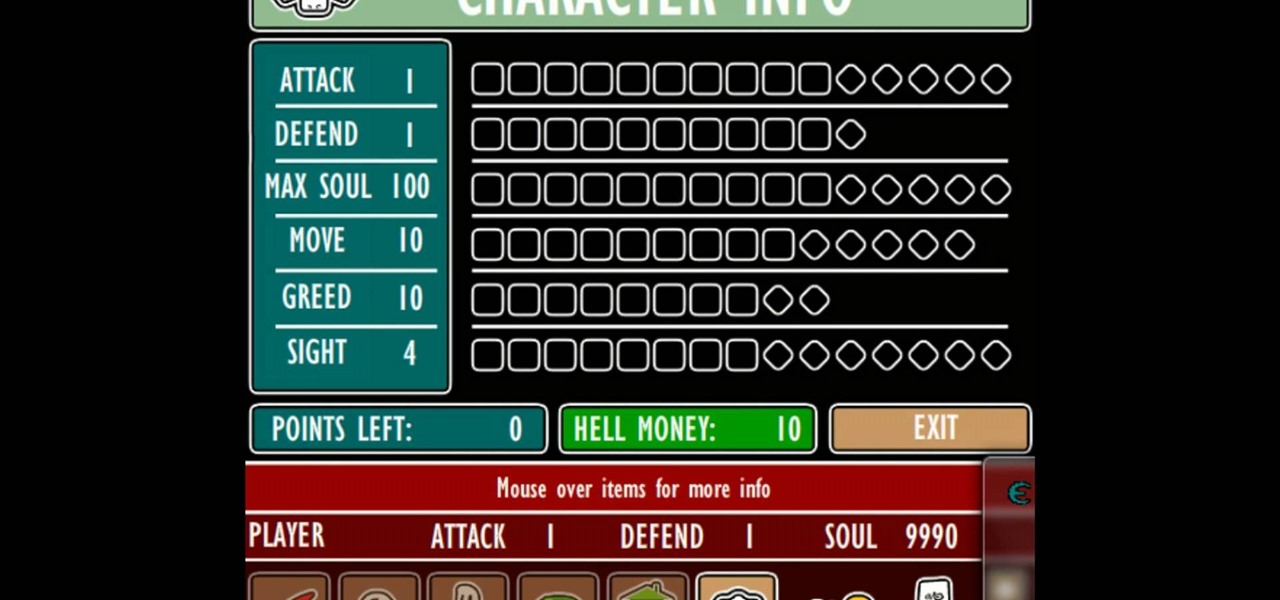
Trevor4Ever595 shows us how to hack Hell Tour on Kongregate tours. First start the game by clicking 'New Game'. Complete the first level. Once you're on level two complete it as usual, and at level three you can start doing stuff. Open the cheat engine, click the process list, and click on your browser. Multiply your souls by 8 and put it into first scan. Go back to the game use some of your soul and then open cheat engine and multiply it by 8 again. Go down and click the frozen box on your c...