Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.
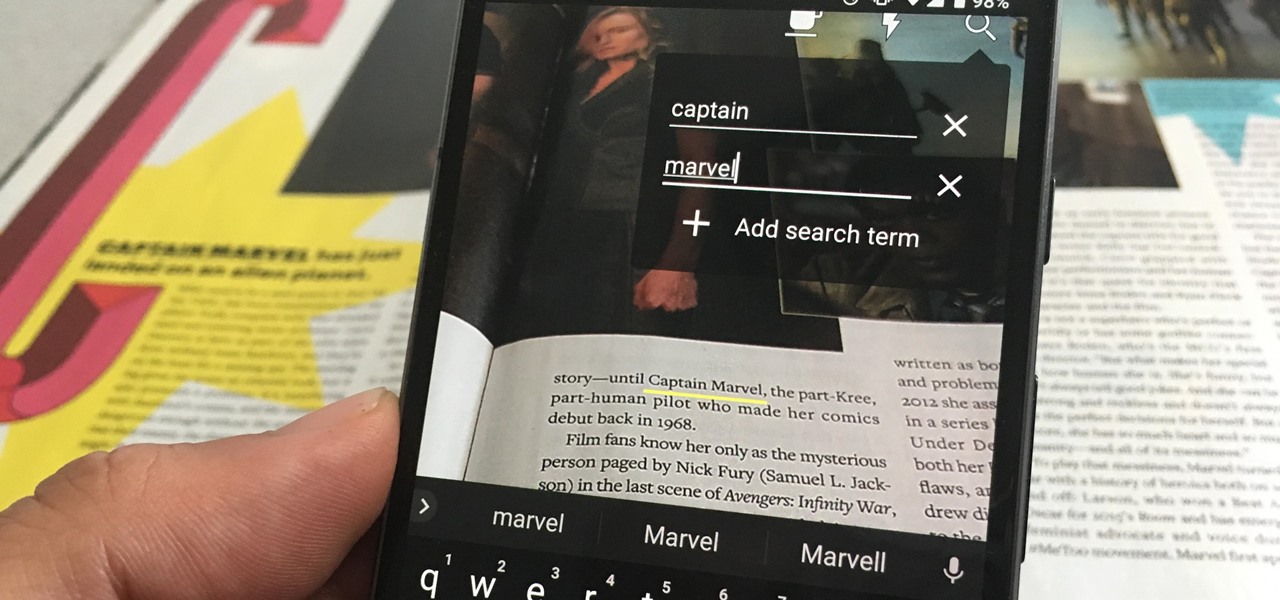
One of the neatest tricks available in Google Lens, an app that can identify and interpret real world information, is the ability to copy text from the app's camera view and paste it into a digital document.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

The spirit of Google's Tango augmented reality platform lives on at Vivo, a China-based company that has developed its own 3D sensor for mobile devices.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

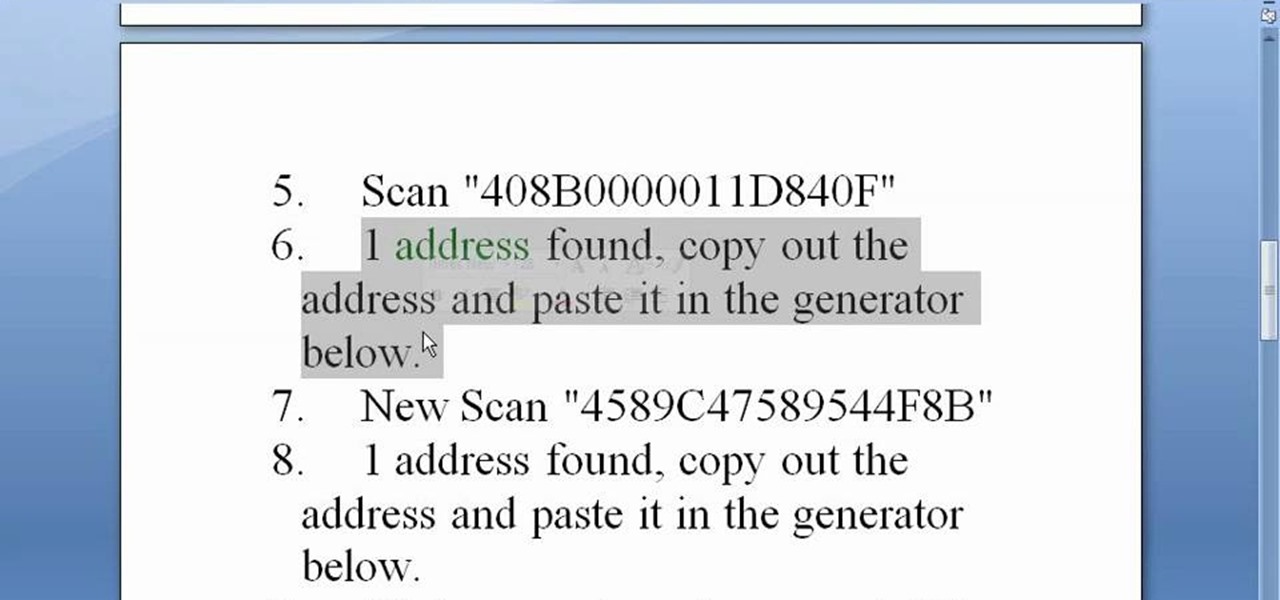
Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

Thanks to Apple's beta preview of iOS 11.3 released last week, app developers are already experimenting with the ARKit capabilities that will be available to regular users this spring.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

When it comes to your security, you want the best of the best. Why settle for mediocre service with something as valuable as your protection? Malware continues to make its way onto the Play Store, leaving millions of devices vulnerable. You need an app that will shield your devices from both the latest malware threats and threats nearby. And when it comes to antivirus apps, there is only one choice.

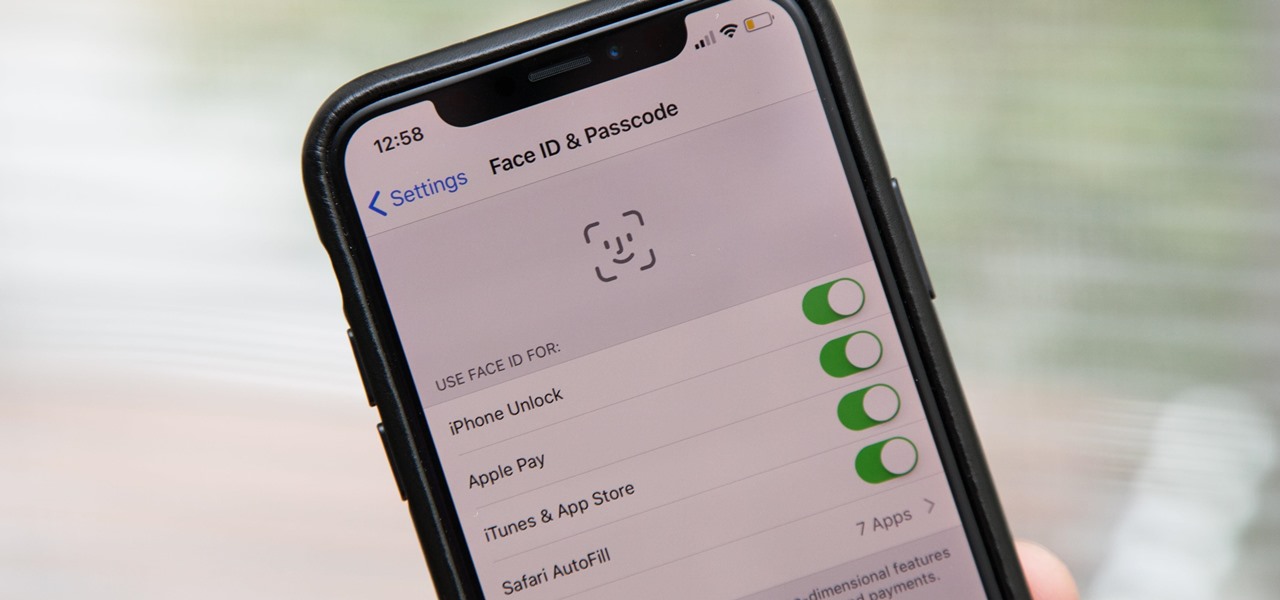
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

A partnership between augmented reality company Zappar and IoT services provider EVRYTHNG will bring AR experiences to consumers while supplying market data to brands.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

The large, dome-shaped LiDARs that have become a fixture on driverless car prototypes are expensive and notably ugly. And yet, these unsightly devices should remain planted on driverless cars, even when they become available in commercial fleet services across the country in a couple of years.

Devastating and deadly, land mines are a persistent threat in many areas of the world. Funding to clear regions of land mines has been decreasing, but new research may offer a less dangerous method of locating hidden, underground explosives by using glowing bacteria.

The mysterious Magic Leap just partnered up with Lucasfilm's ILM xLAB to bring Star Wars to their mixed reality headsets. Based on the video demo making its way around the internet, it looks pretty impressive.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Fewer and fewer Android phones are being released with SD card slots, so it's always a struggle to make sure you have enough free storage space for your photos, videos, and music. Things like app data and cache slowly build up as you use your device, which means your available storage number gradually decreases over time.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

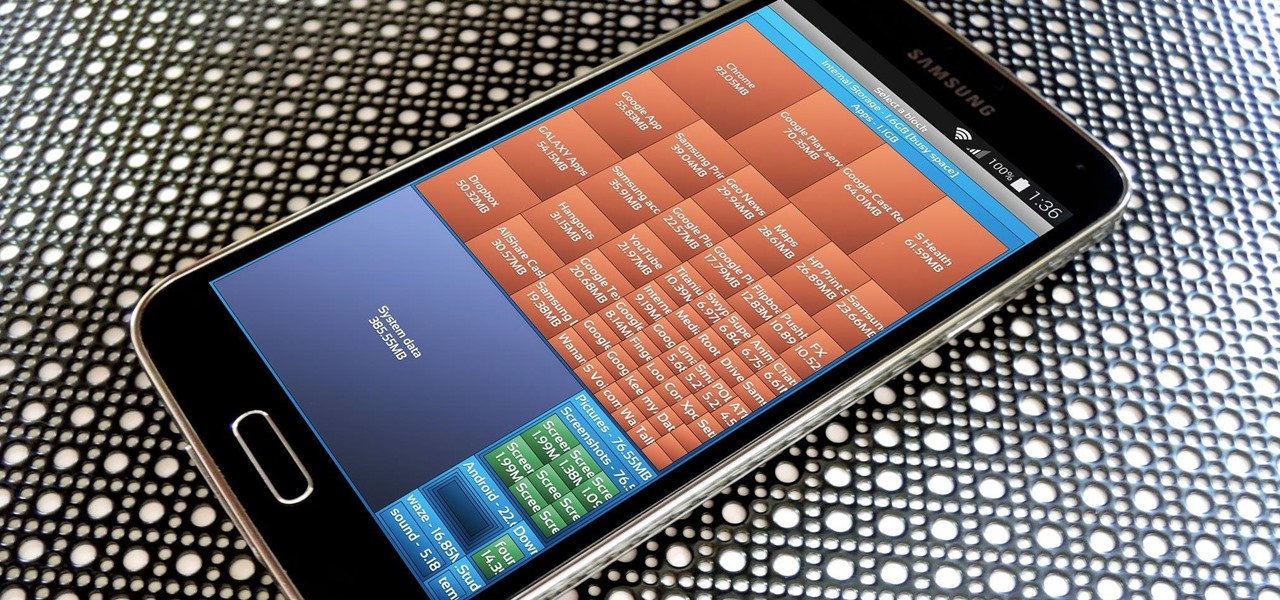
The more we use our smartphones, the more storage space becomes occupied—it's an inescapable fact. But as the data accumulates and chokes off our storage, it can become difficult to identify exactly which files are occupying the most space.

The Touch ID fingerprint scanner on the iPhone 5S was one of the phone's biggest selling points. Now, the Touch ID system can do more than just unlock your phone, like pay for stuff, and is even present on the new iPads (as well as iPhone 6 models, of course).

Welcome back, my aspiring hackers! Those of you who've been reading my tutorials for some time now know that I am adamant regarding the necessity of learning and using Linux to hack. There is no substitute, period.

According to Nielsen, the average American spends about 34 hours per week watching television. That may sound like a lot, but when you factor in multi-screen viewing, it could be even higher—81 percent of Americans use their smartphones or another device while watching TV. It's the new picture-in-picture.

In this how to video, you will learn how to serve a tennis ball. Start off with an eastern forehand grip. You can pretend to shake hands with the racket to find this grip. The knuckle of the index finger should be on top of the handle. Make sure your stance is sideways to the net and the feet are shoulder width apart. Your foot should point at 1 o'clock. The back foot should be parallel to the base line. Your racket should start at pointed towards the net. The first step of the swing involves...

When putting in your hair extensions you will need to take into account that there are eight pieces four large ones and four small ones, you can use all of them or a couple depending on what you want. The first thing you will want to do is with your two index fingers is move them right above yours ears to the back of the head and grab the top potion of your hair in a part or ponytail. Use a clip or tie to keep this out of the way. The hair extensions have clips on them that open when you pres...

Want to be the John (or Jane) D. Rockefeller of Restaurant City? Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine 5.5 (02/04/10).

Make the perfect sushi. These sushi rolls are delicious and surprisingly easy to make. Food Safari presents this awesome Japanese recipe on how to make sushi. This particular sushi roll is called Norimaki.

This is a jumprope hack for Pet Society. It's called the Auto Jump + Coin hack, and involves your jumprope, Cheat Engine, and a little code generator.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

Several recent research studies have pointed to the importance of the microbes that live in our gut to many aspects of our health. A recent finding shows how bacteria that penetrate the mucus lining of the colon could play a significant role in diabetes.

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Welcome back, my neophyte hackers! Digital forensics is one of the fields often overlooked by aspiring hackers. In a rush to exploit every and any system they can, they often ignore learning digital forensics—the field that may lead to them being traced.

Since its introduction on the iPhone 5S, Touch ID has made unlocking Home button iPhones quick and secure. The second-generation iPhone SE brought back the beloved feature in 2020 but didn't take any steps to improve on the technology. So if you're rocking Touch ID and having trouble getting it to read your fingerprints, there are some things you can do to fix it.

Watch this video to learn how to edit the Windows Experience Index. While it may not be apparent from the video, but it is really quite simple. Browse to C:\Windows\Performance\WinSAT\DataStore

This is an awesome trick that will impress any bar patron you run into. Follow along with this tutorial and learn how to use an ordinary piece of paper as a bottle opener! That's right!

Lee T. Dresang, MD of the University of Wisconsin School of Medicine and Public Health from the Deaprtment of Family Medicine give a discussion and demonstration of suturing techniques. Before beginning a procedure, you will need consent. One should irrigate lesion before beginning. A simple interrupted suture is easy to learn and fast, but unable to withstand stress. Vertical mattress sutures provide a good eversion of skin edges, closure of dead space, and strength, but also lead to scarrin...

Michael Lynch gives a second tutorial on how to play three different chords on the ukulele, C, Am, and F. First, start by bracing the ukulele against your chest, cradle it in your right arm, and make sure that your left hand is correct on the neck of the instrument. Make sure your left thumb is also correctly placed. Make sure your fingers are arched high so you get the best sound. Do not allow your fingers to touch other strings or you will get the wrong sound. To play the first chord make s...

In this video Dave shows his unique way to grill fillet mignon. Dave begins the video with a brief history of fillet mignon. Dave says his unique way is easy as long as you follow his simple steps: 1) Allow steak to come to room temperature before putting it on the grill. This allows the cooking time to be a lot more consistent, and you won’t have a very cold middle with an overcooked outside. 2) With a great fillet mignon cut, do not over season. He adds just a little salt and coarse groun...

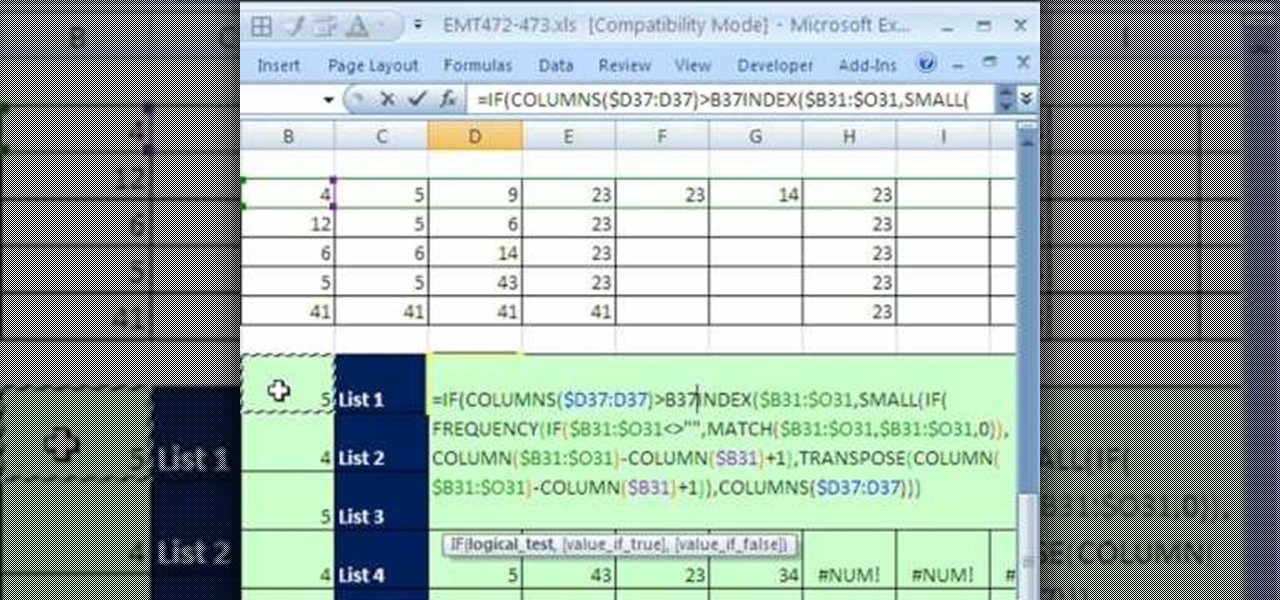
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 473rd installment in their series of digital spreadsheet magic tricks, you'll learn how to extract a unique list from a group of individual rows.

The video shows us how to throw a curve ball like a college pitcher. There are actually keys to throw a curve ball. Number one is the grip, number two, your arm speed and number three is the position of your hand when you throw the ball. First step is to focus on the grip and here it is going to be on a two seam and your index finger and your middle finger is placed on the right side for right hand throw and on the left side of the ball for left hand throw for the exact gripping. Number two i...

Mark Montgomery is an award-winning yo-yo artist and a former member of Team Buzz-On and Team Omega. In this video, you will get step-by-step instructions for how to do an impressive chopsticks trick that Montgomery introduced in 2006, then you'll learn "The Wave", a new trick inspired by Montgomery. These tricks aren't for beginners, so pay attention!