In this video tutorial, viewers learn how to hack the flash game, Age Of War 2. Users will need to download the Cheat Engine program for this process. Begin by starting the game. The game should start with 2500 gold. Then pause the game and open Cheat Engine. Click on the Process computer icon and select the current web browser. Now type "@500" into the Value box and click First Scan. Then deduct your amount of gold, type in the new value and click on Next Scan. There should only be 1 result ...

Interested in scanning QR matrix codes with an Android phone? This clip will show you how it's done. It's easy! So easy, that this video tutorial can present a complete, step-by-step overview of the process in about two minutes. For more information, including detailed, step-by-step instructions, watch this video guide.
Ian Brown shows us how to use Avast to remove viruses from your computer. First, go to Avast.com and download their new and free edition of their virus protection. After you have installed this program, you will receive an email with your product key to access the program. Now, change the settings on the program so it scans your computer at least once a day for viruses. Now, reboot your computer to save settings and scan your computer automatically for viruses. When you see a blue screen with...

In this video, you will learn the best way to throw cards. This takes practice, as many people who first try to throw card do not have the right grip. In order to throw the card properly, you will need to place your thumb on the center of the top side and the index finger on the corner. When you throw the card, use your index finger to create spin. You can use your wrist to add more power, or put your entire arm into it to increase throwing distance. You must work up to using your entire arm....
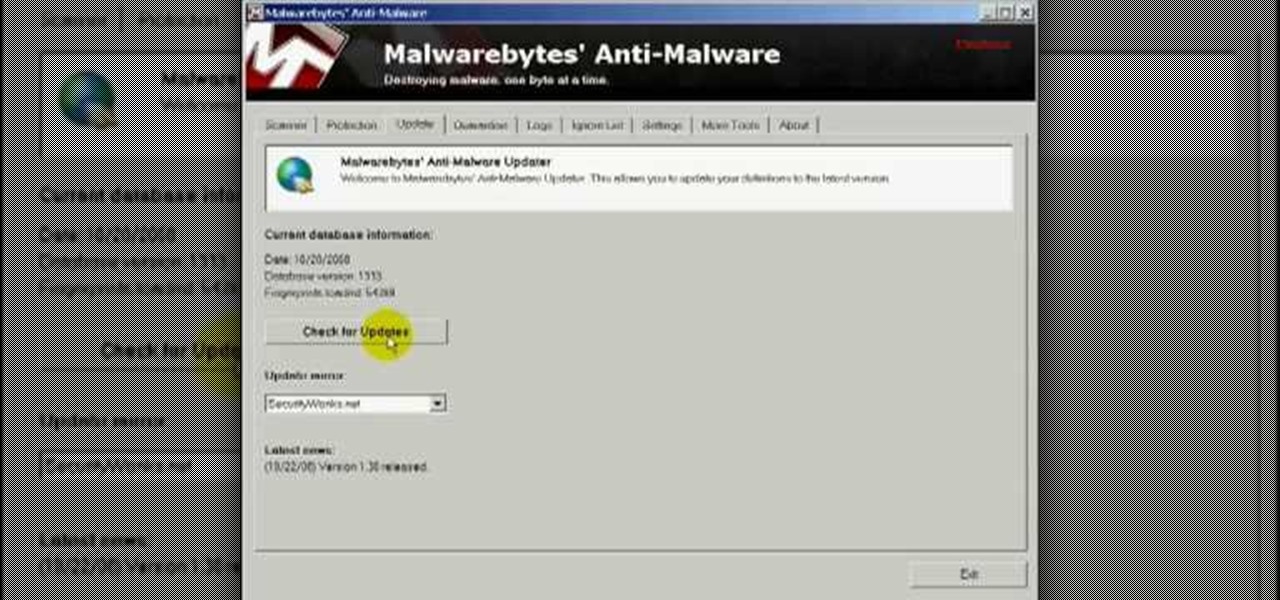
In this video you will learn how to remove the Trojan .dnschanger virus with Malwarebytes. To see if you got a Trojan .dnschanger virus go to your network connections right click on Local Area Connection, select proprieties, click ok internet protocol, click again proprieties and if you got an ip address at preferred DNS server that means that the Trojan entered a fake ip address. You can remove the Trojan. To do this first run the Malwarebytes application, click on the update tab, click on c...

Be prepared next time you go out by having a great new bar trick to entertain your friends. The bar is a perfect place to perform this trick because you'll have everything your need which is simply bottles and money.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

Here is a short video tutorial which demonstrates how to debind books using a hair dryer. You may need to take books apart for detailed scanning projects. However, this is a destructive process which will destroy your book. The hair dryer method is a fairly failsafe method of removing binding from books.

In this scroll saw woodworking pattern making tutorial you will learn how to get the clip art you find off the computer, into the computer and into Corel Draw X3 so you can use it for your scroll saw patterns. Watch and see how easy it is to scan clip art into Corel Draw X3 and start making new scroll art patterns.

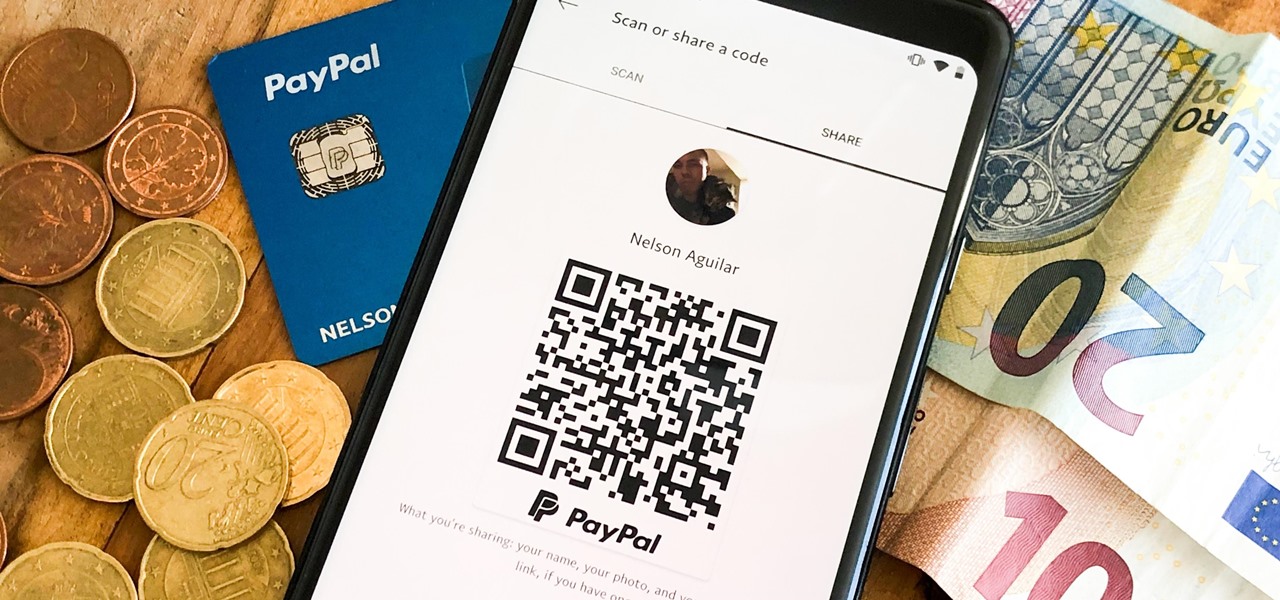
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Complex games in mixed reality require a pretty detailed scan of the room, and getting this process right can be both time-consuming and annoying. Computer science students at the University of Washington decided to fix that by turning it into a game.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

Welcome to my very first tutorial ever. Today I will be teaching you how you can use Arachni to scan vulnerabilities of web applications. I welcome all criticism good or bad as a teaching method for myself.

How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

It's Christmastime, so what better of a game to play than the winterized Icy Tower? And what better game to hack with Cheat Engine?

In this Adobe Photoshop tutorial the instructor shows how to prepare pan and scan images. To prepare an image by panning and scanning is quite different than preparing an image normally for using in your video. These images should be extra sized as you would perform special effects on the image in your video. This is also called as "Ken Burns" effect. Now go to the file, new menu and select the video format that you want to use according to your requirement. Enable the correct pixel aspect ra...

Like other popular social media apps, TikTok features a tagging system — dubbed TikCode — to follow people in your immediate vicinity. Instead of searching for their username, you can scan their TikCode, and TikTok will launch their page immediately. Of course, you have a TikCode of your own, so you can share yours with others in the same way.

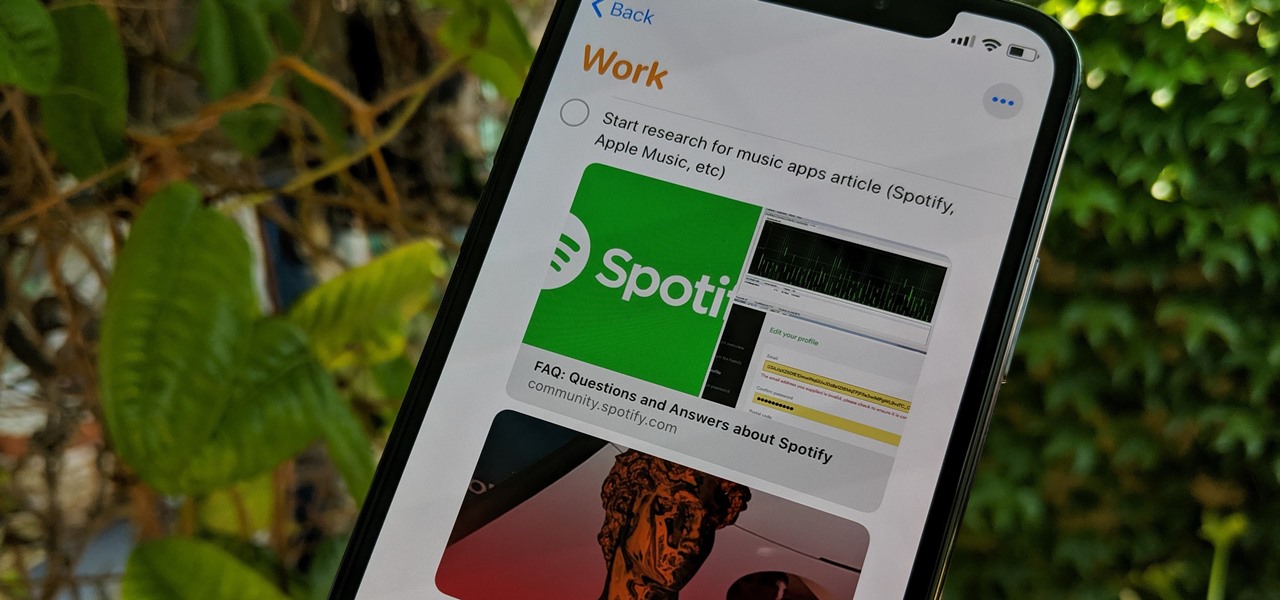
Apple's Reminders app has always been an underrated yet useful productivity tool for iPhone. It's not as powerful as many third-party to-do apps, but it makes it easy to keep track of a few basic tasks, and it's integrated deeply with iOS, macOS, and watchOS. In iOS 13, it's even better since you can now add attachments to your reminders, such as photos, documents, and webpages.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

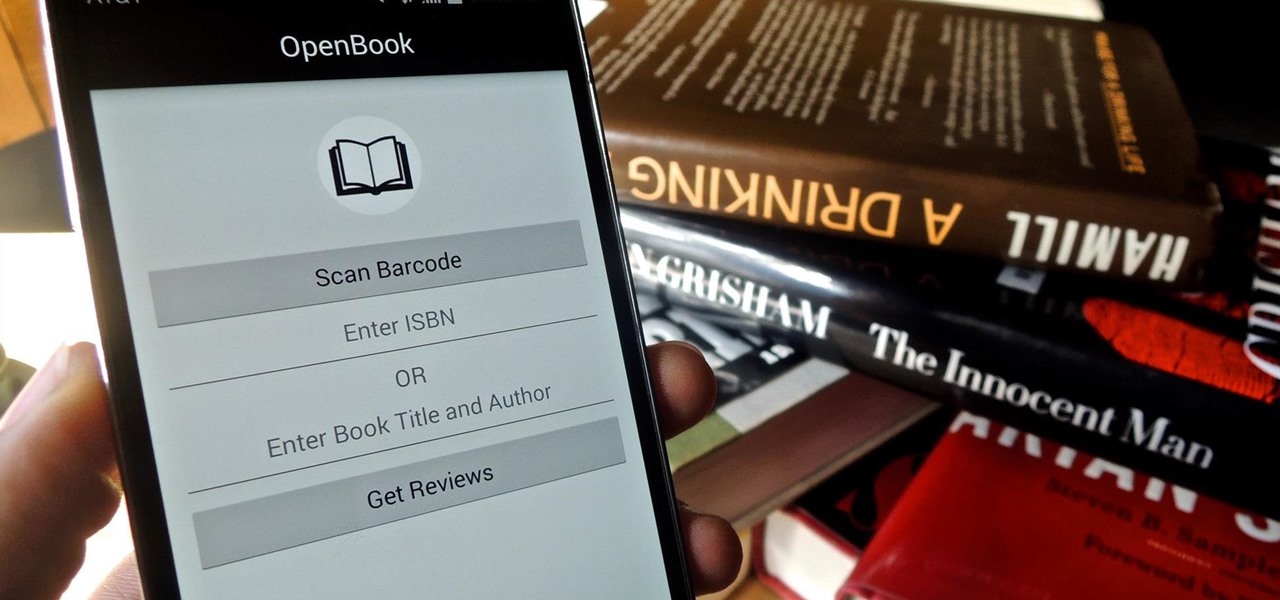
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Former Vice President Dick Cheney was so fearful of attacks, he had his heart defibrillator re-calibrated to block incoming wireless signals so that highly skilled hackers couldn't send him into cardiac arrest.

Interested in having your VCI-100 feel more like a CDJ-1000 when pitch bending? Jog Grips have been designed so that your hand naturally falls half on, half off the grips when you grab the wheel. So one of your fingers activate the touch sensor while the index finger benefits from from the grip and added tactility. For step-by-step instructions on the Jog Grip installation process for VCI-100 controllers, take a look.

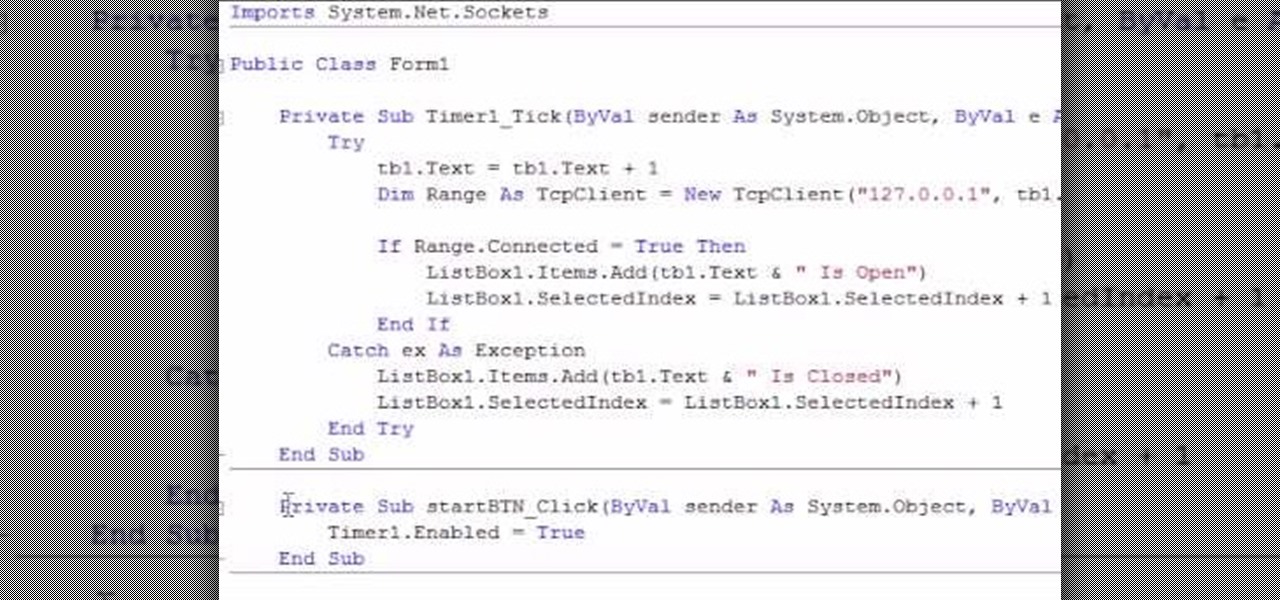
This is a Computers & Programming video tutorial where you will learn how to make a simple port scanner in VB.Net. It detects all the open ports on your network. Open up a Form1 and you will have a ListBox1, a ‘Start’ and a ‘Stop’ button and a blank text box. There is also a Timer1 button at the bottom. Thereafter, the video shows the various parts of the code on the screen. Then click on Debugging, and click ‘Start’. The system starts scanning ports starting with port 1. In the video it show...

Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

The company that pioneered music scanning for mobile devices is moving into the augmented reality advertising arena. Included in an update of their iOS and Android apps last week, Shazam can now scan special codes to immerse users in 3D animations, 360-degree videos, mini-games, and other AR content.

Jostled in the airport, someone is coughing in line. The air looks empty but it is loaded with microbes that make their way into your body. You get sick. You give it to your family, and that's pretty much it. But what if you were so contagious that you spread it to your entire community and beyond?

Welcome back, my tenderfoot hackers! Generally, you will want to perform a vulnerability scan before doing a penetration test. Vulnerability scanners contain a database of all known vulnerabilities and will scan your machine or network to see whether those vulnerabilities appear to exist. If they do, it is your job to test whether they are real and can be exploited.

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

This video is teaching you how to have proper Risk Management when trading. Not managing your risk will eventually kill your capital, whether you are trading stocks, forex, futures or indices. After explaining the concepts instructions are provided for you to adopt the principles mentioned.