From media insiders to the halls of politics, news travels fast on Twitter, making it one of the most powerful social media channels for disseminating or collecting information. Now, for better or for worse, you can immerse yourself in the data firehose of Twitter in augmented reality.

These days, location-based augmented reality gaming pioneer Niantic is best known as the developer behind Pokémon Go, but the uber-popular mobile game was not its first foray into the AR gaming genre.

Drama seems to follow red smartphones. The internet nearly blew a gasket when Apple released a red iPhone 7 with a white front, and now OnePlus is taking some heat. The new Lava Red 5T comes with black bezels, not repeating Apple's mistake, so why are people mad at the Shenzhen-based company? Because Lava Red is only available in China.
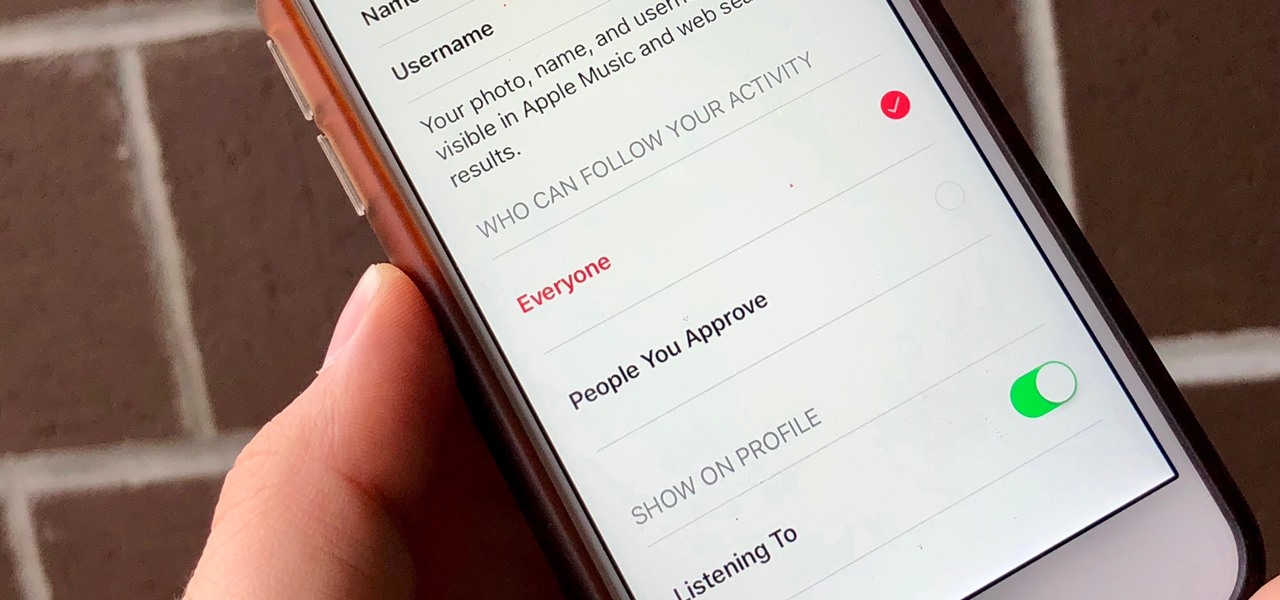
Apple Music, Apple's answer to Spotify, has many interesting features packed in to make that $9.99/month price tag as attractive as possible. One of those features is geared towards social listeners — those who want to follow other Apple Music users and who want to be followed back. But here's the thing: how do you know if your account is public or private?

One of the more meme-able characters from the animated series Rick & Morty will be able to beckon iPhone owners to "show them me what you got" thanks to ARKit.

More video content is making its way to Facebook as the social network relentlessly tries to get its video platform up to par with YouTube. Now, they seem to be making more of an effort to improve their video tab, as new features have started to appear on some Android phones.

Every morning I head on over to my gym to start storying away classes full of people dripping in sweat. This always makes me feel super awkward because it's not exactly the most photogenic time to take a picture, and if it was me, I would probably give that person a dirty look and hope they'd just eventually go away.

With the massive popularity of online clothing brands like Missguided and Fashion Nova, it seems that shopping in-store is a thing of the past. I admit that I love browsing from the comfort of my own bed, but there's something to be said for actually going to a store, speaking to people with similar tastes and penchants for shopping. Fortunately, with Frenzy — Shopify's new app for iOS — you get all of the convenience of online shopping, plus the opportunity to interact with other users in pe...

The way we tell stories is about to change. Imagine you're hearing a story when suddenly characters and images from the tale start to appear in your world. This immersive way of storytelling is in the not-so-distant future thanks to the Microsoft HoloLens and Rémy Martin.

What companies do you think have a unique and compelling take on social media? Wendy's is certainly confident, to say the least. But Lufthansa Airlines is taking a different approach than most — and it seems to be working — as they give passengers a look behind the scenes through Snapchat Stories.

Here's another workday distraction for all you social media lovers out there: Pasted, launching out of beta today on iOS, is a simple collage and photo editing app mixing iconic '90s imagery with a love of the The Shins.

ModiFace, the makers of Sephora's Virtual Artist app which allows users to try on multiple different combinations of makeup through augmented reality, has just bumped up its augmented reality strategy. The company is now including a live-stream option for all those personal makeup trials you've been secretly admiring from the comfort of your own phone.

In February, the popular Facebook-owned WhatsApp Messenger service jumped on the "stories" bandwagon and replaced their in-app, text-based "About Me" status (you know, those lovely little messages where you can say "Sleeping" or "Not Sleeping" under the tiny nub of your profile picture). Taking its place was a clone of Snapchat's Stories feature, continuing the social media giant's recent trend of shamelessly copying Snapchat.

With tools such as Reaver becoming less viable options for pen-testers as ISPs replace vulnerable routers, there become fewer certainties about which tools will work against a particular target. If you don't have time to crack the WPA password or it's unusually strong, it can be hard to figure out your next step. Luckily, nearly all systems have one common vulnerability you can count on — users!

If you really want to end your next big guitar solo with a bang, consider giving this shotgun guitar a try.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

Today I will show you how to make a metasploit exploit really quickly. This tutorial is mainly applied to stack based buffer overflows and seh buffer overflows exploits .There is a simple way for rop exploits too but I will dedicate a special tutorial on this subject.

Hello friends. This is actually my first how to.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.
Welcome back Hackers\Newbies!

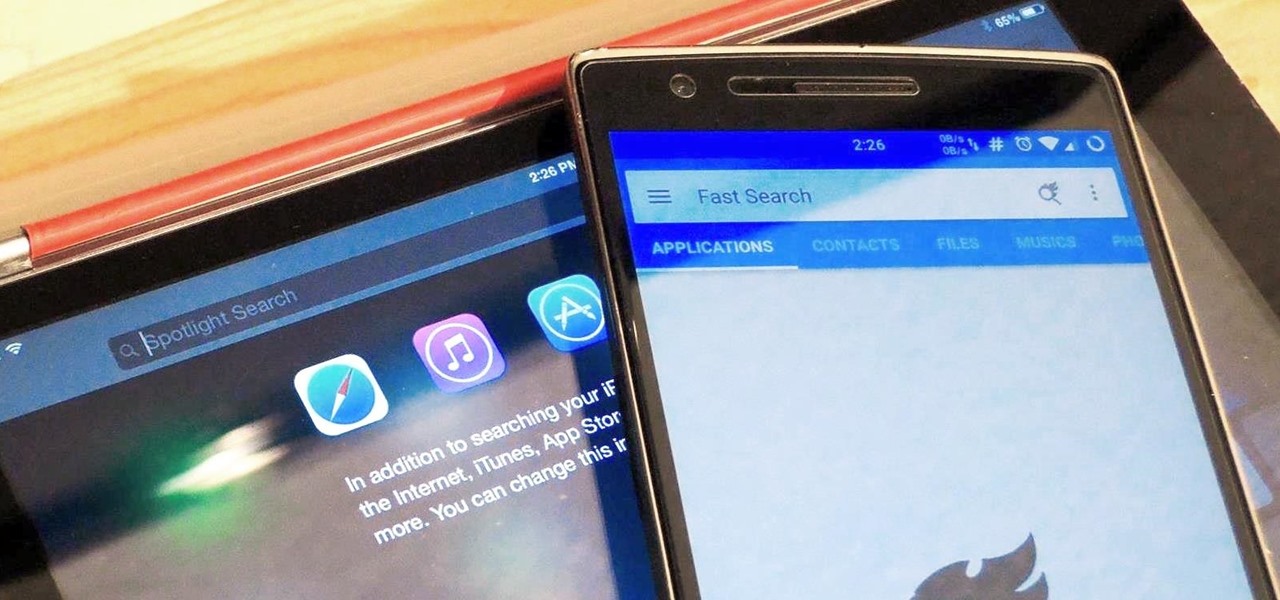
Google Now is great for looking up movie times or finding your parking spot, but if you need to track down a file you downloaded, you're relegated to using a file explorer and, depending on your organizational skills, this can either be extremely easy or a huge pain in the ass. Unfortunately I land in the latter category, which is why I started using Fast Search by developer Mohamad Amin.

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

With platforms like Facebook, Instagram, and Snapchat available for anyone to take advantage of, I'm all about differentiating from the mundane and repetitive images we see on social media everyday.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

With the gargantuan size of the Samsung Galaxy Note 4, it's no surprise that some of you might have trouble taking advantage of all the features using only one hand. One such feature is the newly-added fingerprint scanner, which allows you to swipe your finger on the Home button to unlock the device, among other things.

Spotlight is awesome for finding items in the stock Apple apps, but what if you want to search through the rest of the apps on your iPhone?

Fact: we live in a world where social media dictates our behaviors and shapes our perceptions. Maybe some of us are addicted more than others, but most of society uses some type of social media, whether it's Twitter, Instagram, Facebook, Snapchat , or something new that I've never heard of.

You've seen the Samsung Fingers and the Emoji Translator, and I know you spent a good part of the day catching Pokémon, but now that April Fool's Day is officially upon us, the flood of gags has reached a tipping point. Here's the best of what we've seen today.

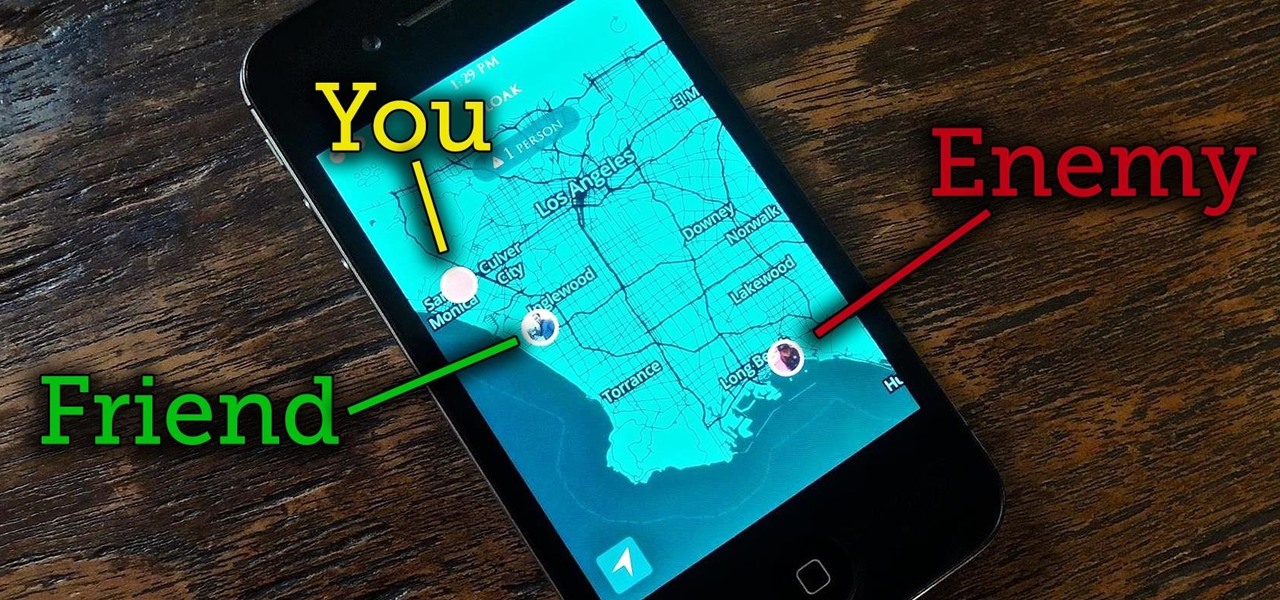
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

Since The Guardian published leaked documents exposing the depth of the NSA's spying powers, many people who've never put much effort into protecting their privacy are finally starting to pay attention. Evidence of public opinion concerning PRISM can be seen from the rise in traffic for pro-privacy sites like DuckDuckGo to the petitions demanding that the program be scaled back or done away with altogether. Some would argue that you waive your right to privacy by signing the terms of agreemen...

I get advice from my friends on a lot of things in life—cool video games, movie reviews, and feedback on my choices in women. Friends can be very helpful in filtering out some of the excess noise and are more likely to give you suggestions you can relate to.

Cheetos fingers is defined as the unpleasant (but mostly pleasant), oddly-colored residue left on the thumb, index finger, and middle finger after ravenously eating through a bag of—you guessed it—Cheetos. It can usually be cleaned up by licking your fingers (my favorite) or washing your hands (boooooo). For the folks who enjoy the latter, Cheetos fingers are an annoyance. As someone who enjoys this idiosyncrasy, I've never quite understood the disgust in getting your fingers all cheesed up.

A few weeks ago, Twitter announced that they would be creating an archive feature for its members, which they've been slowly rolling out to select users. After signing in today, I noticed the feature was finally available for my account, so I went to test it out.

The reason that Facebook is so popular is because it connects us to people that we could have never been connected to before. When people log on, they look for messages, comments, likes, and any other notifications that connect us to those people. These same notifications, though, distort our view of Facebook. We tend to appreciate statuses (I prefer stati) that have more likes. We're geared towards people that have more friends, so we tend to like pages that already have hundred of thousands...

Facebook is an awesome free online resource that is connected to billions of people around the world. These days, you won't meet many people who do not have a Facebook account. As a real estate agent, you can take advantage of social networking to promote your business and share your listings. By posting on Facebook and creating a page for your business, you gain free advertising to thousands of local buyers. Check out this tutorial and learn how to start uploading videos to Facebook to promo...

This video shows you how to perform the Bandaram trick. Things you'll need: deck of playing cards, elastic band. Select a card and show it to the spectators. Ace of Spades is chosen as the selected card. Return this card back to the deck. Do a table cut trick of the deck so that this selected card is brought to the top of the deck. After the selected card is placed at the top of the deck give it a few shuffles and cut but keep it on the top only. Do a double turnover so that another card come...

Inserting a tampon is a rite of passage for every teenage girl, so it's important to know how to insert a tampon the right way. It could seem tricky at first, but after trying several times, tampon insertion becomes as easy as putting on a glove. It just takes practice, & this video will show you the animated process. The key is to RELAX! Worrying about it may make you tense, making insertion even harder.

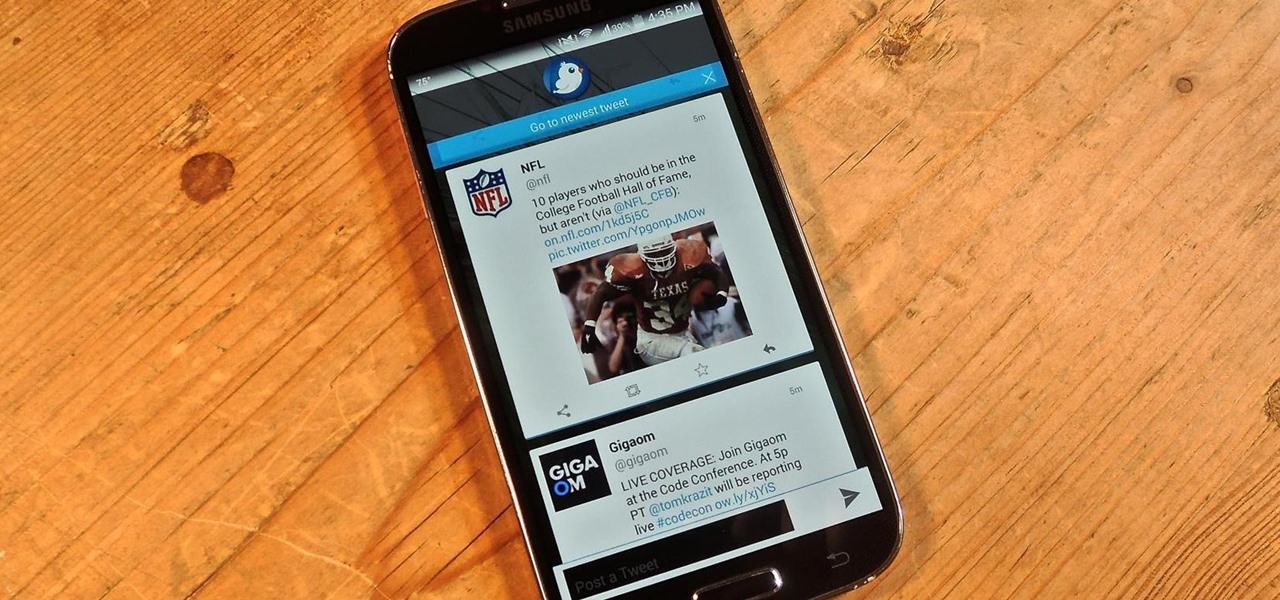
Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.

Gmail conversations, Facebook private messages, and personal photos can all be viewed by a hacker who has backdoor access to a target's Mac. By livestreaming the desktop or exfiltrating screenshots, this information can be used for blackmail and targeted social engineering attacks to further compromise the mark.