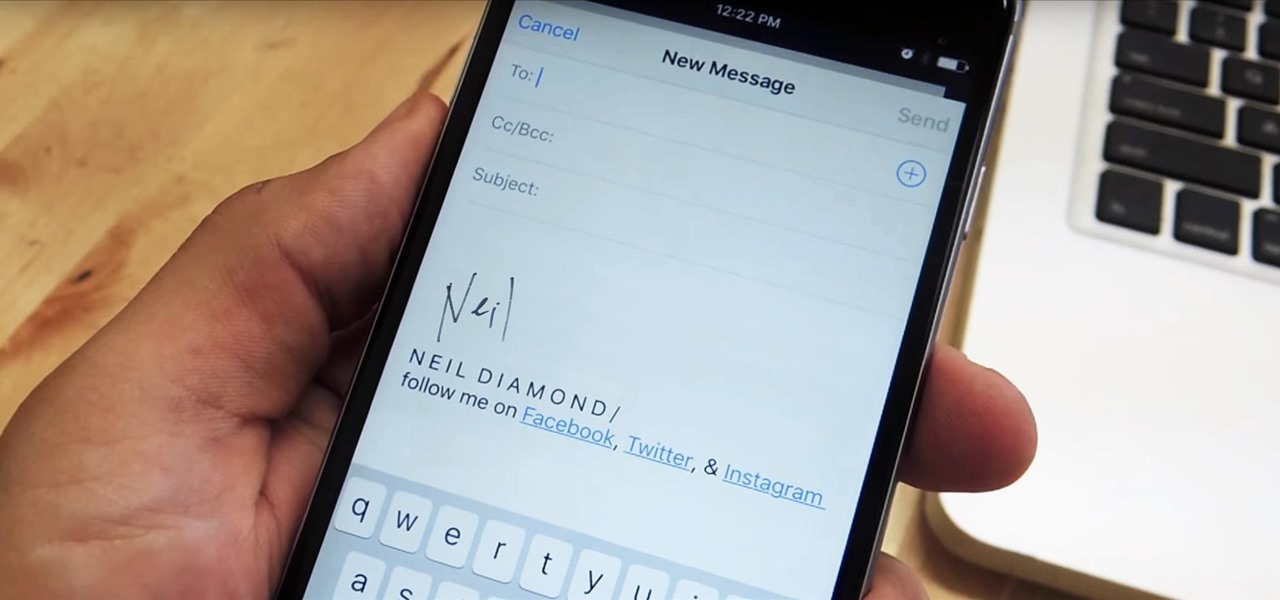
I often read ebooks on my iPhone while I walk, but being glued to my screen is a good way to get run over or cursed at. To save my physical and social hide, I use this trick to get my iPhone to read ebooks and articles out loud, turning my whole text library into de facto audiobooks.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

A sphere of clear gelatinous goo may not sound all that appetizing. But to food fad fans on social media, the raindrop cake—a soft and lightly flavored edible blob—has gone insanely viral.

We're so used to seeing things in particular ways that anything different just doesn't make sense to our brains. Culturally, we like to read things from left to right, and from top to bottom. Change that and our brains struggle to adjust.

Over the course of the past century or so, media consumption has gone from a few readers enjoying their local print publication to billions of users viewing countless hours of video across the globe each day. This was a gradual evolution at first, but recent advancements in mobile connectivity have sent us into a climb the likes of which we have never seen before.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

If Android is all about options, then iOS is all about new features. Every year without fail, Apple announces a cool software component that brings something new to the table, and this year was no different.

Do you ever thought that you can't control an Internet disconnected system? I saw a funny video in Chema Alonso's youtube channel (A well-known hacker of my country and creator of Fingerprinting Organizations with Collected Archives among other security tools), and decided to post something similar.

Nice people finish first—or is it last? Though you may have been told throughout your life that being kind pays off, there are some obvious advantages to getting mean. So whether you're driving towards a goal at work, or need to attack a task in your personal life, acting like a jerk just might help you get what you want.

So, how does someone keep their hacking life completely secret? What This Is:

Apple just sent out a new update to their iPhones, and while that normally wouldn't have any impact on Android users, the fact that they included 184 new emojis means that the text messages you receive from friends and family members with iOS devices might come across with blank or missing characters.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

In part one of this tutorial we found out that your English teacher is a paedophile, by using a Man in the Middle attack to intercept his internet traffic.

When it comes to news, updates, and arbitrary nonsense, it's hard to find a better source than Twitter. And for some of us, the best way to consume Twitter is through the web (versus a mobile app). But as much as I prefer the standard browser version, it's easy to make it better, faster, and more convenient using a few Chrome extensions—and here are my favorites.

Emails sent from an iPhone, by default, are signed "Sent from my iPhone," which almost seems like a disclaimer in case the email has spelling or formatting errors. If your goal is to look professional while corresponding with coworkers or potential employers, then you're better off removing the signature completely and just typing your name out.

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Windows 10 marks a new era for Microsoft with the return of the Start menu, the demise of Internet Explorer, and the introduction of the remodeled Windows Store.

There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

Hello fellow grey hat hackers, as hackers it becomes necessary for us to be able to send emails anonymously. Whether for whistle blowing or pranks or social engineering or whatever, it just is necessary for us to do that.

The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

Now that we have our vulnerable server, it's time to start up BeEF. Getting Started
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

When it comes to added features, no manufacturer out there can hold a candle to Samsung. Whether it's a remote control for all of your electronics, a heart rate and stress level monitor, or a seemingly-magical stylus, Galaxy devices always have as much functionality as possible packed in.

Although this century is still young, with little fanfare we may have just witnessed the "Hack of the Century." AV software developer Kaspersky of Russia recently announced that they found that some hackers have stolen over $1 billion from banks around the world!

What type of person are you in group settings? Are you the social butterfly, eager to get to know everyone and interested in the people more than the setting? Or are you a wallflower, afraid to catch anyone's eye out of fear?

Can't stand seeing your Facebook news feed full of peoples' good news and awesome accomplishments? Those oversharing friends are, in a sense, hampering their great news simply by sharing it. If you hold back and keep your accomplishments from friends, you might find even more success than if you'd shared with your support network.

The importance of body language is stressed from an early age: watch those around you, and you'll know what they're thinking. While you might be skilled at deciphering the messages of crossed arms, slouched sitting, eye movements, and hand gestures, the key to understanding those around you is a little less obvious.

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

Aside from the occasional "creative" collage, most of your friends on social media are content with pretty basic image and video posts. You can easily one-up them with celebrity cameos or awesome time-lapse videos, but to truly outshine them, try your hands at some creative double exposures.

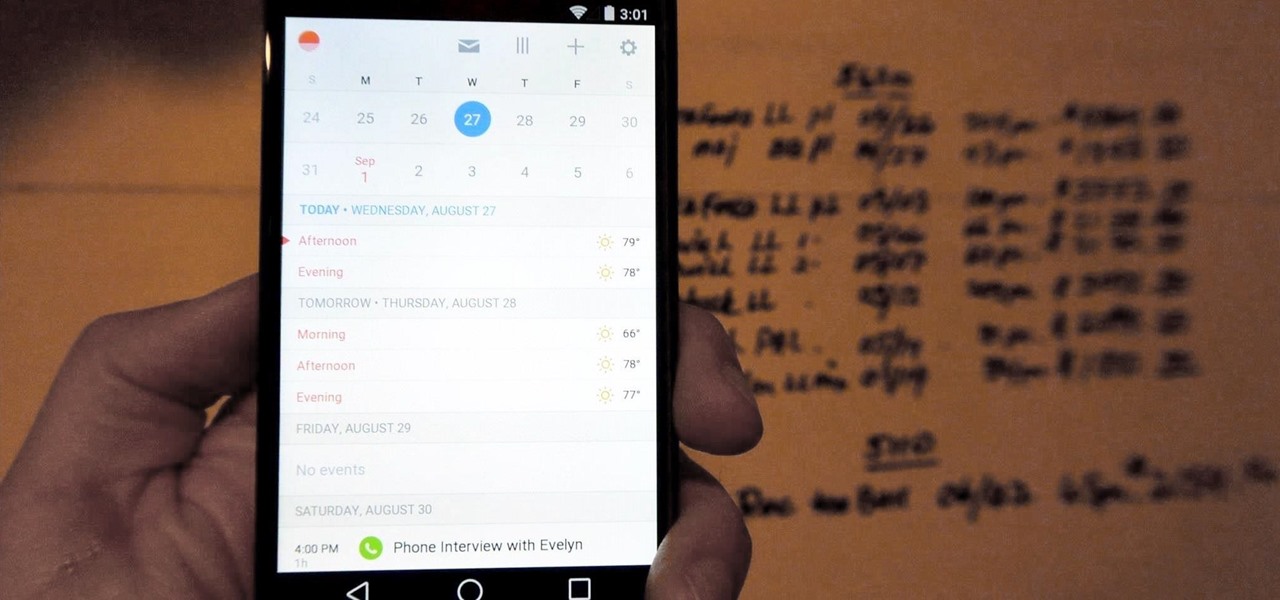
If you're anything like me, you rely heavily on your calendar to keep on track throughout the week, month, and year. While Android's built-in Google Calendar provides an excellent cloud-based solution for keeping our schedules properly maintained, it's not perfect.

Investing is like exercise—we all know we should be doing more of it, but we often just can't find the time. I mean, really, who's got the hours, inclination, and skill to pour through volumes of data and put together a balanced yet sophisticated portfolio of investment vehicles tailored specifically to optimize their returns while mitigating potential risks. Not me, that's for sure.

Ah, the age-old problem of sharing pictures with friends and family. Ten years ago, the best method available to us was passing around duplicate photos printed out at the local drug store. As easy as smartphones have made this act, you'd think we'd be satisfied by now.

In today's world of ordering food from your PC or hailing a cab with an app, it almost seems archaic when we have to actually use our vocal cords to contact a local business. It sure would be nice if we didn't have to use our smartphones as, well, you know...phones.

The level of customization that Android has to offer is insane. You can replace the stock keyboard and home screen with any third-party app of your choosing, allowing core experiences to be tailored to fit your needs.

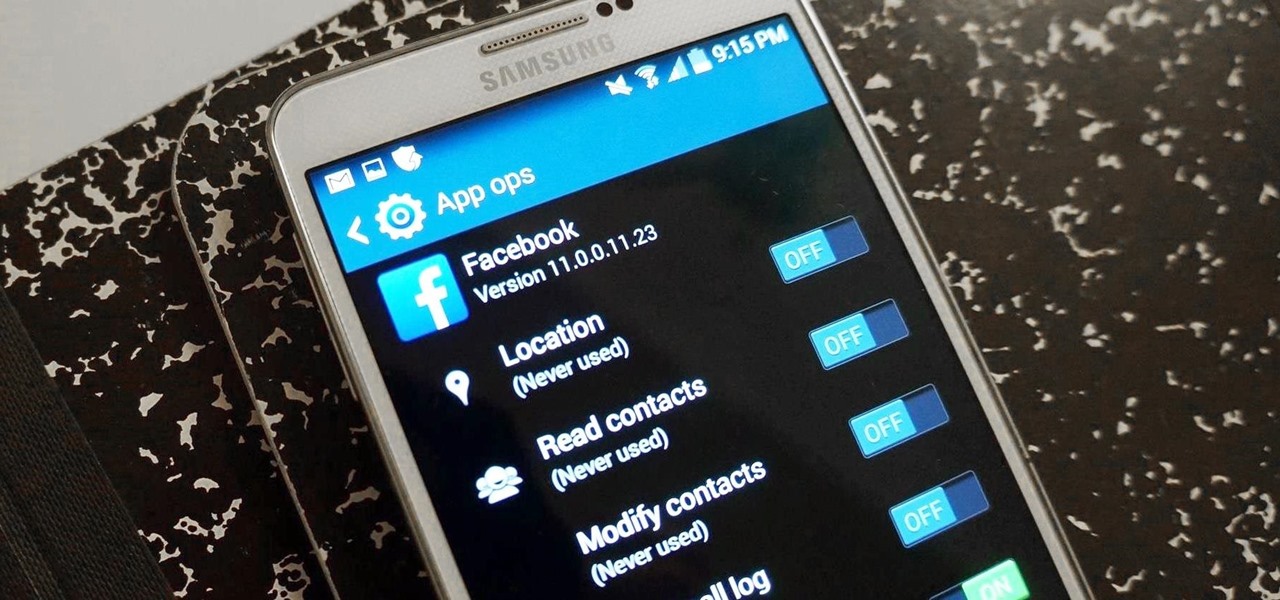
It's a modern day nightmare to accidentally reveal too much information on Facebook. I've inadvertently told the world my location more times than I can laugh off, and my friends haven't fared too well either. Just take a look at the requested app permissions next time you're about to click install and you'll quickly realize how much that app can reveal about you.

Instagram is not only a great platform to easily share some of your favorite moments with friends and family, it's a useful service for peering outside of your physical location. While you share a picture of your dog in Los Angeles, you can almost instantly view and like a picture someone posted of their breakfast in Tokyo.

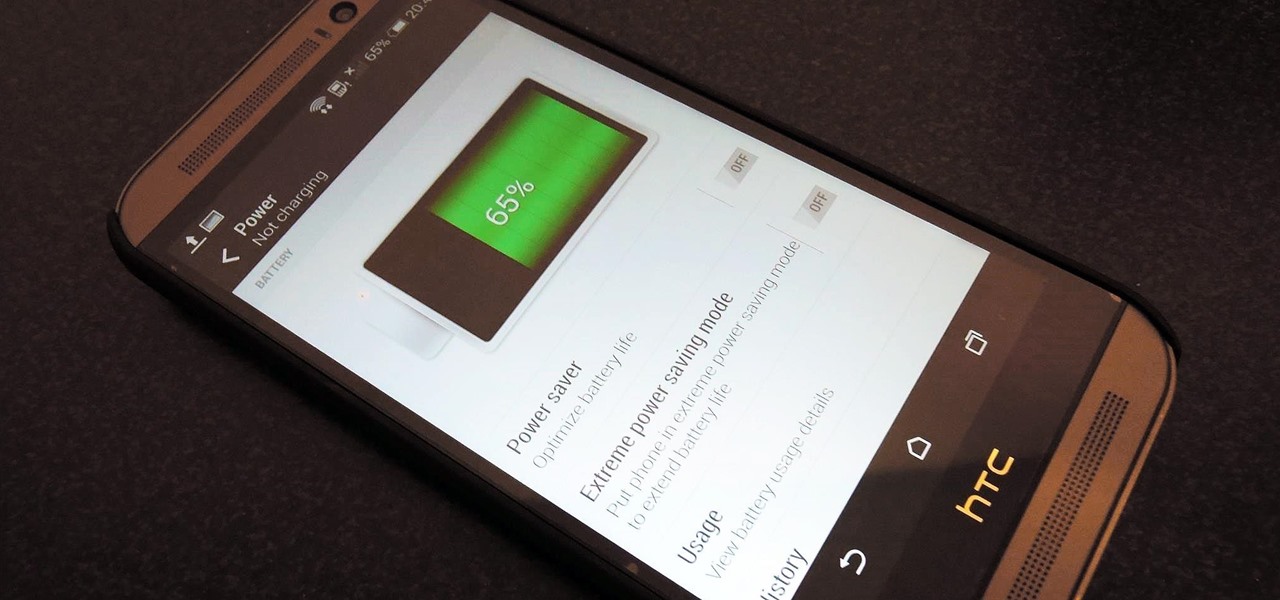
HTC claims to have improved the One M8's battery life by 40% over its predecessor, but there is always room for improvement.

The international hit Xperia Z2 may be headed to Verizon if a posted, and quickly erased, image is any indication. Take this information with a grain of salt—I certainly am—but this could be Sony's entrance into the non-GSM realm. The image above was posted to Sony's Xperia Google+ page, and very quickly removed. Compared to the Z2 that's currently on the international market (below), we can see that not only has the Sony logo shifted to the bottom, but a Verizon logo rests squarely along the...