
How To: Float when swimming
Floating is a swimming skill needed in a survival situation. Floating can be done on the back or front. Get expert tips and advice in this swimming video tutorial.


Floating is a swimming skill needed in a survival situation. Floating can be done on the back or front. Get expert tips and advice in this swimming video tutorial.

Holding breath underwater is an important part of learning to swim. Knowing how to hold breath underwater can prevent choking and drowning. Get expert tips and advice in this swimming video tutorial.

Knowing how to prevent drowning is important for all who swim. There are simple safety steps available that can help prevent drowning. Get expert tips and advice in this swimming video tutorial.

Hypothermia can be a real danger when swimming in very cold water. There are both emergency and non-emergency steps the swimmer can take to prevent hypothermia. Get expert tips and advice in this swimming video tutorial.

The streamline kick can reduce drag while swimming. The streamline kick is a good drill for style swimming. Get expert tips and advice in this swimming video tutorial.

Swimming in ocean currents requires preparation and understanding. There are definite do's and don'ts when trying to swim in currents. Get expert tips and advice in this swimming video tutorial.

Swimming in the ocean requires a few unique considerations. Ocean swimming is more unpredictable than swimming in a pool or lake. Get expert tips and advice in this swimming video tutorial.

Kick drills are important in swimming because they improve technique and build strength. There are unique kick drills for each of the swimming strokes. Get expert tips and advice in this swimming video tutorial.

The butterfly is the most difficult strokes in swimming. However, the butterfly stroke is also one of the most beautiful. Get expert tips and advice in this swimming video tutorial.

Teaching a child to go underwater may be easier than it sounds. Children have a natural reflex to go underwater but can lose it. Learn how to teach a child to go underwater in this swimming video tutorial.

The backstroke is a great swim stoke that is best learned gradually. Get expert tips and advice in this swimming video tutorial.

The breaststroke is a great swimming stroke for beginners. Many swimmers prefer the breaststroke over other swimming strokes. Get expert tips and advice in this swimming video tutorial.

Breathing is a skill to master before trying advanced swimming strokes. Learning to breathe while swimming will enable rapid progress. Get expert tips and advice in this swimming video tutorial.

The flip turn is a swimming skill that takes a bit of practice to perfect. The flip turn increases speed when swimming laps. Get expert tips and advice in this swimming video tutorial.
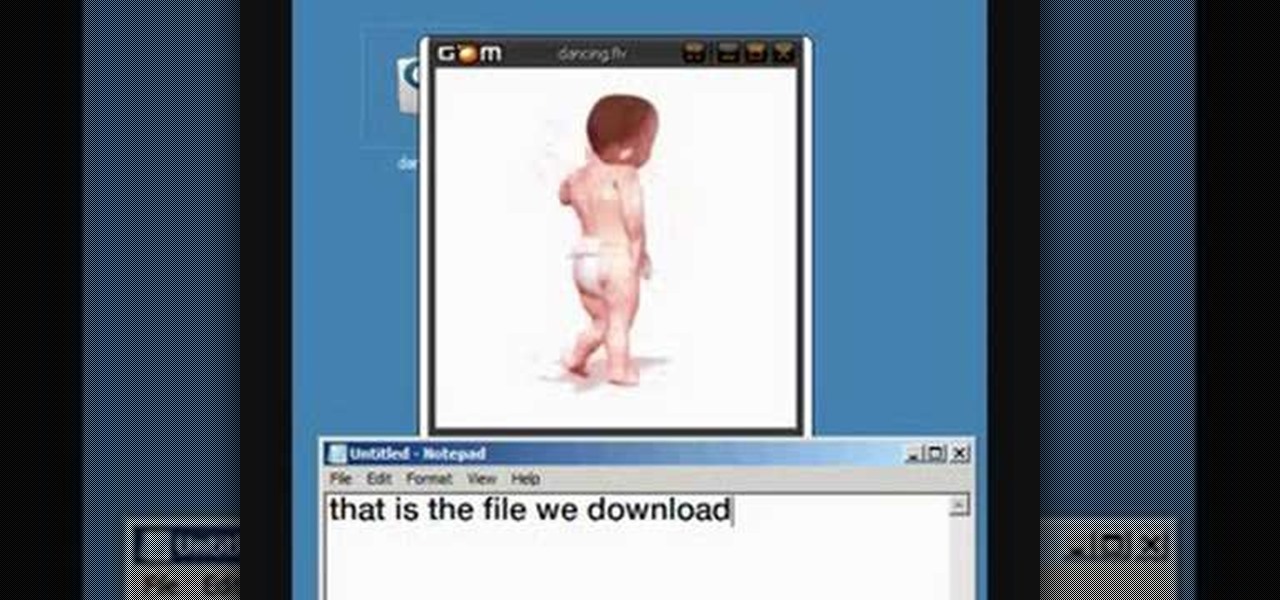
Have you ever wanted to add animated pictures or GIFs to your website or blog? Two free software programs, GOM Player and GIMP, both allow you make your own GIFs. This tutorial shows you where to get them and how to use them.

It can be a real challenge to plant your seeds in evenly-spaced lines. In this episode of Growing Wisdom, Dave Epstein will show you how to use a four-row pinpoint seeder to plenty your seeds. Using devices like this, planting seeds in even lines will be a whole lot easier.

See how to hack Pet Society from Playfish! Pet Society is the popular online game where you can design and take care of virtual pets. Check out this video tutorial to learn how to cheat Pet Society: Coin hack (11/15/09).

While Apple was one of the first to integrate LiDAR into mobile devices for depth sensing, headset maker Varjo has developed a truly remarkable feat with its implementation of the sensor.

It's open season on Zoom, the video conferencing platform that has grown in popularity during the COVID-19 pandemic but has come under fire due to privacy issues.
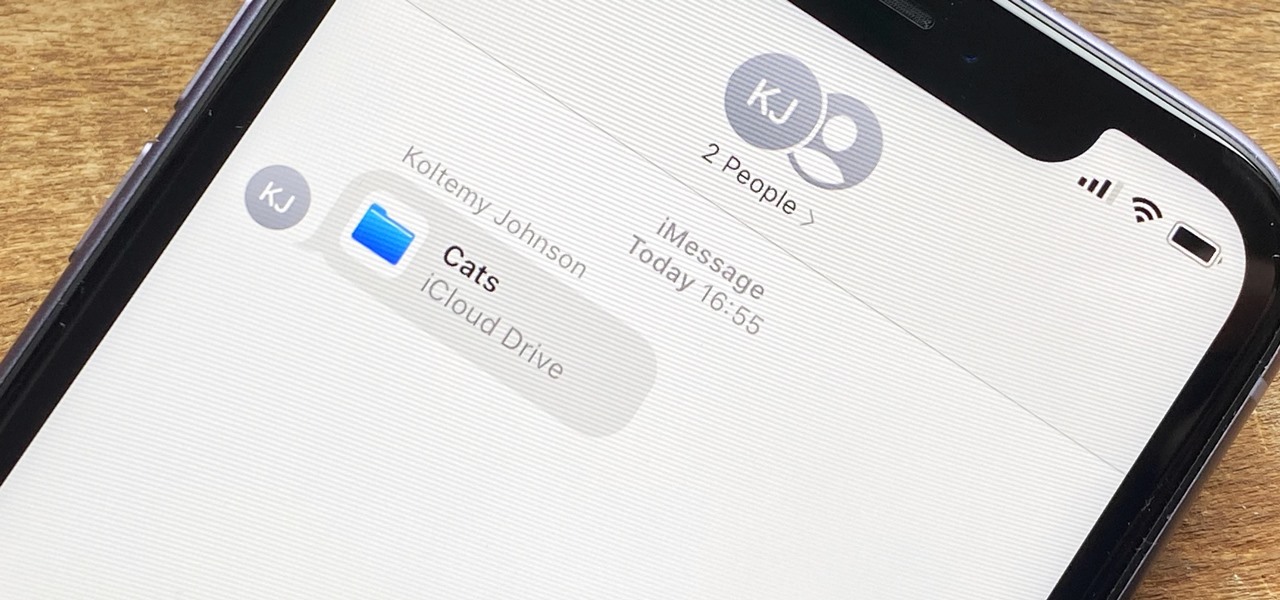
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

It seems like each day our phones become more integrated into our lives. School, work, shopping — so many tasks either require a phone or heavily benefit from one. But our phones are a double-edged sword that can easily distract us and harm our mental health as well.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.

Apple's latest update for iPhones, iOS 13, introduces over 200 new and exciting features. Many of those changes come to Siri, resulting in a better, more useful version of the digital assistant we've known for years. If you simply look at iOS 13's webpage, however, you wouldn't realize just how much Siri has changed this time around. We're here to fill in the blanks.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

You're minding your business when your Apple Watch taps you. To your surprise, the watch claims your heart rate dipped abnormally low. The news might come as a shock — especially if you have no history of a heart condition — but before you panic, you should take the time to fully understand what this alert is really saying and what you can and should do about it.
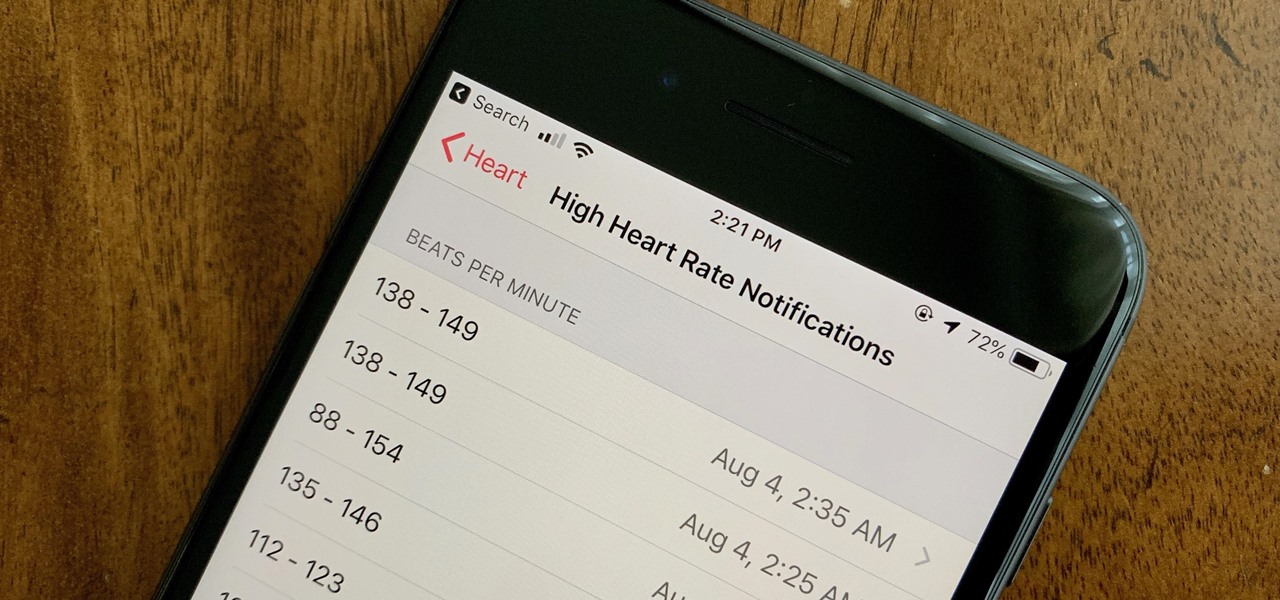
Your Apple Watch sends you notifications from friends, family, and the apps that are important to you. Occasionally, however, the watch may scare the heck out of you with a notification warning of an abnormal, elevated heart rate. If you have no history of heart conditions, this alert might come as a shock. Why do you have a high heart rate, and what are you to do with the information?

In case you hadn't heard, Google is now a legit cell service provider. Google Fi has its pluses and minuses, but the biggest upside is in the pricing. Depending on how much data you typically use, there's a good chance you could save a lot of money without sacrificing coverage by switching to Fi.

You can never replace the skills and expertise of a professional graphic designer, but Canva comes pretty damn close. It's ridiculously easy to use the drag-and-drop design tool for both professionals and people like me who don't have the need (or knowledge required) to use more advanced graphic design software.

A new study published by American University demonstrates how Pokémon GO and other augmented reality games can help city governments bring communities closer together.

We need to take our privacy and security much more seriously. Whether it's malware-infected apps or the mishandling of our data by companies like Facebook, there are threats all around us in this digital world. Fortunately, some smartphones are simply designed to protect us better.

Apple knows their products can be addicting, and with iOS 12, they are doing something about it. With the help of Screen Time and few other new tools, it should now be a lot easier to get off your phone and enjoy life in the real world.

Your email inbox is a treasure trove of personal data. The people you contact, your writing style, which messages you flag as spam — all of this information and more can be used to paint a clear picture of you. Google knows this as well as anybody, so they use this data to constantly improve your experience in Gmail.

Deleted bank statements and private photos are still within an attacker's grasp, so don't think that emptying your recycling bin is enough to keep your files from coming back to life. It's possible for a hacker to recover compromising files and images from a backdoored computer completely without the victim's knowledge.
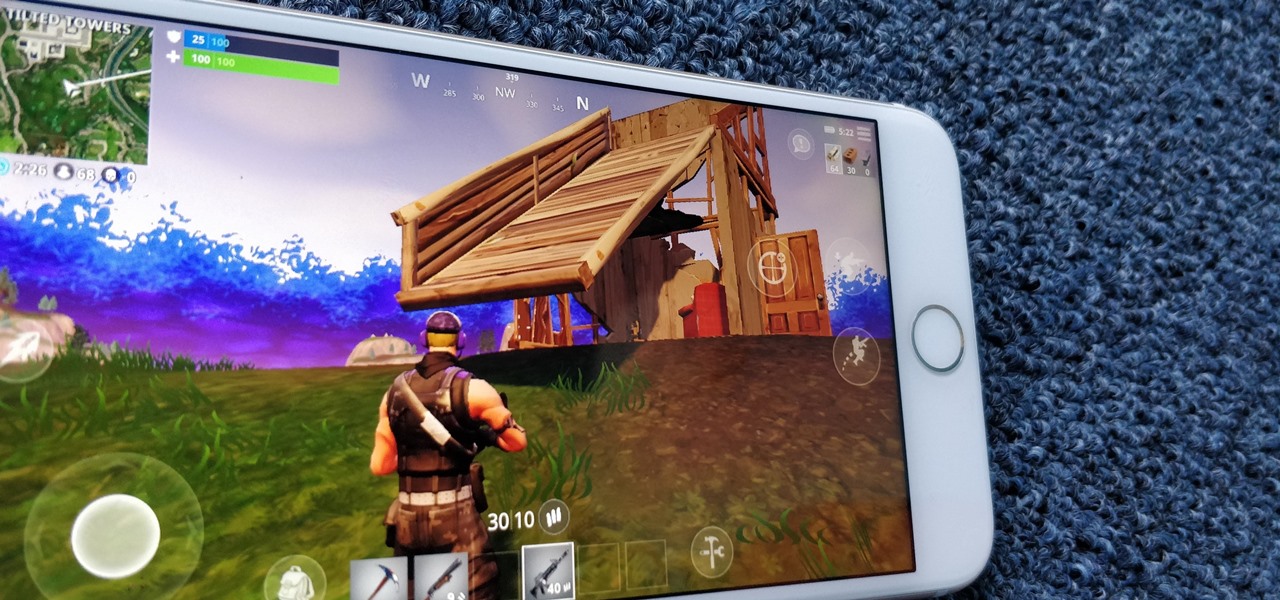
One of the more unique aspects of Fortnite Battle Royale is the ability to create structures. Using in-game materials, players can create walls and ramps for cover and to extend mobility. But creating isn't limited to just the basic generic structures. To really maximize their benefits, great players edit their creations to fit their needs.

After setting up your phone, there are a number of things you should do immediately before download your favorite apps. Specifically, now that your data is on the device, you need to take steps now to ensure it's both protected and retained. Fortunately, most of these steps are a one-time process.
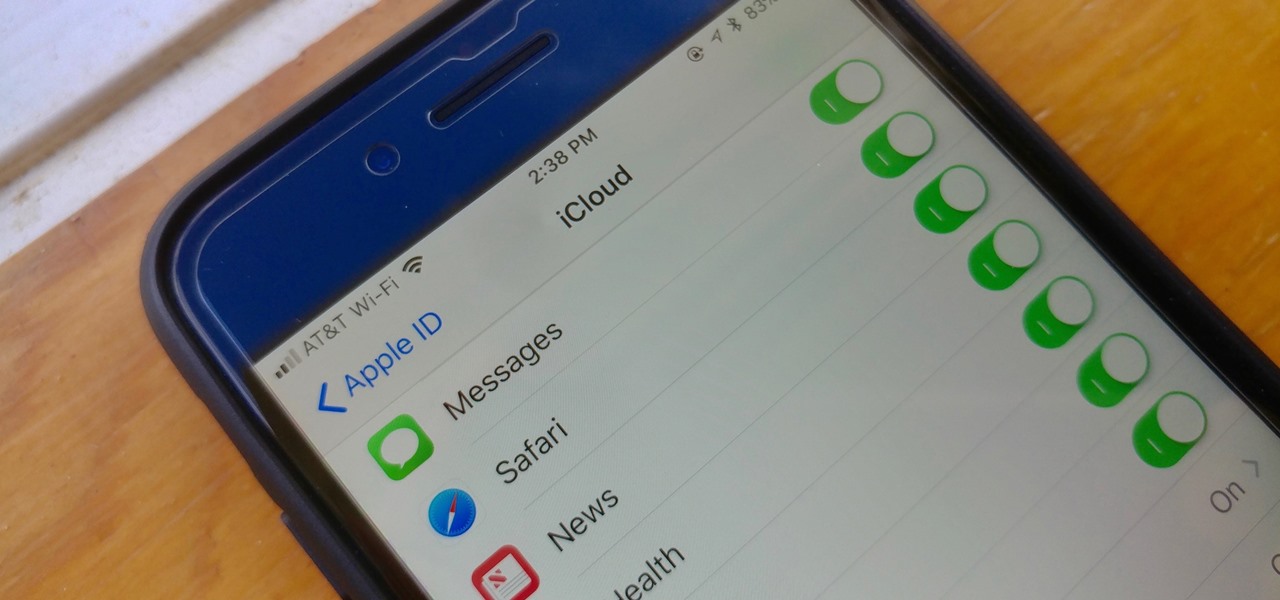
One major problem in previous iOS versions is that there was no way to keep messages in sync between an iPad, iPhone, iPod touch, and Mac. If you deleted a message in the Mac app, it would not be deleted on your iPhone, and vice versa. Apple finally fixed this issue in iOS 11.4 by storing all of the messages in iCloud, not on individual devices.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

With the recent launch of the LG V30 and the Pixel 2 XL, LG has reintroduced the world to POLED. This display tech was showcased at CES 2015 and billed as a rival to Samsung's AMOLED displays, then promptly disappeared from the market for two years. But now that two of the biggest flagship phones this year are using the technology, many folks will be wondering what makes POLED different.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.