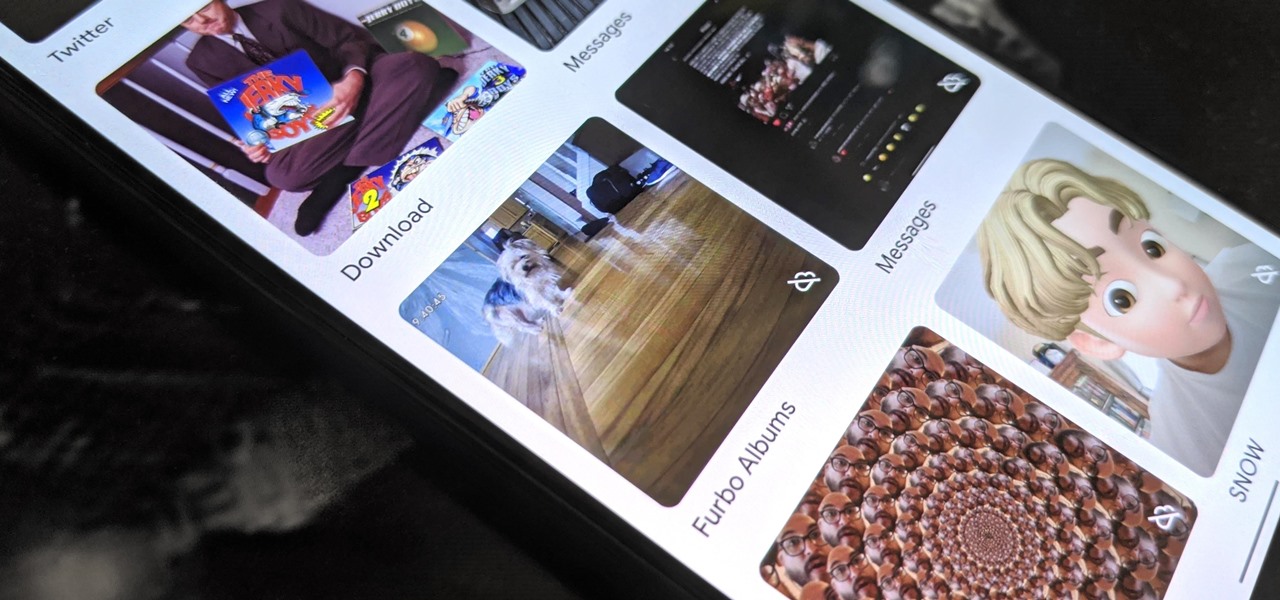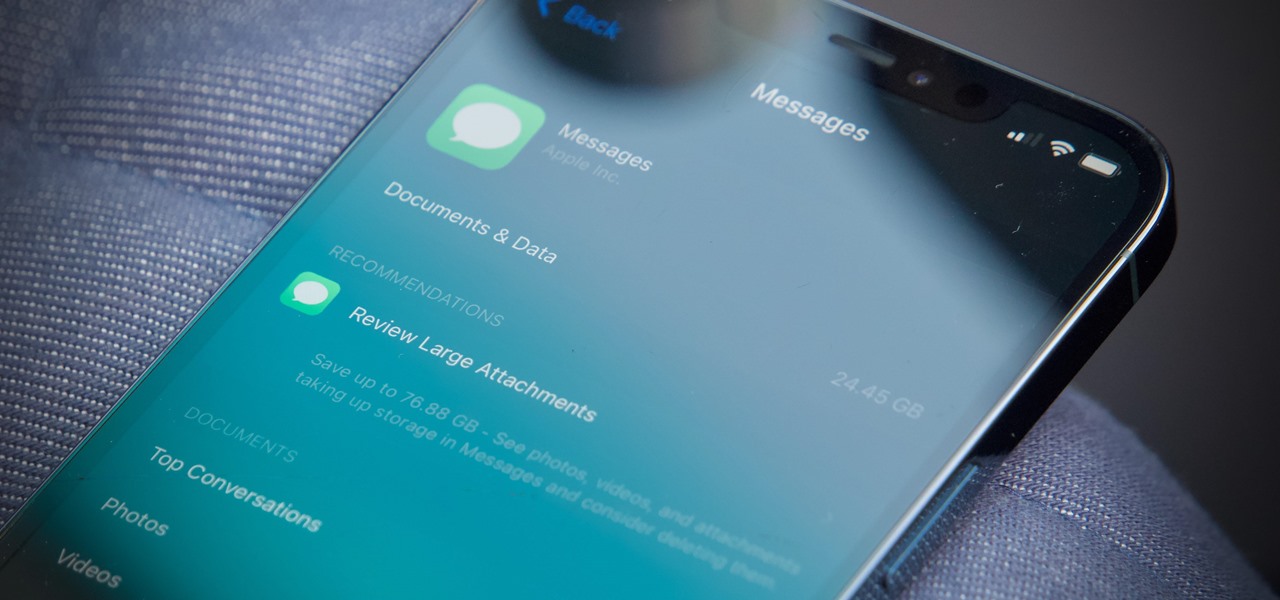
When iOS starts barking at you that you've run out of iCloud or iPhone storage, a quick trip to your settings to see what the culprit is may show that Messages is one of the worst offenders. But if deleting message after message doesn't free up your storage much, it's likely because "Messages" doesn't really mean messages.

A good smart TV can be your one-stop shop for entertainment. Netflix, HBO Max, Apple AirPlay — all the major players have apps or services for most TV operating systems. But for those of you who have or have been wanting to upgrade to a Samsung Smart TV, one big service was missing: Movies Anywhere.

Based on recent reports, we've got a pretty clear picture of what to expect from Apple's rumored augmented reality headset expected to arrive next year, but the outlook is more opaque concerning its consumer-grade AR smartglasses.

TikTok has grown to be one of the most popular social media platforms in the world. The video-sharing app is a driving force for viral content, spurring various popular movements in dance, pranks, comedy, and more. And as one might assume, videos on TikTok don't stay on TikTok — they're shared on Instagram, Twitter, and other services where millions of people get the chance to also view them.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

Waking up to buzzing alarm clock is so 20th century. Wouldn't it better if the first sound you heard in the morning was your favorite song? Whether it's a track to get you motivated or something to put a smile on your face, a song can do wonders for your mood and help you start the day right.

After shipping a redesign of Google Photos and adding a neat new Map View feature for exploring photos, Google has made another change to manage the volume of photos and videos the app is handling during the Social Distancing Era.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

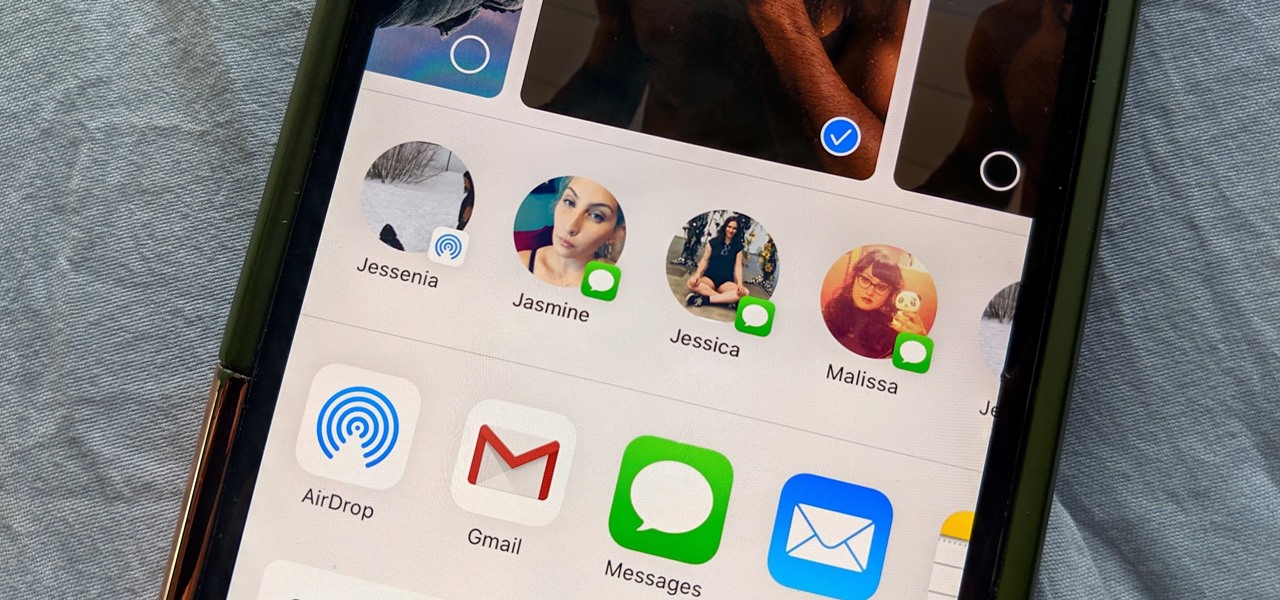
The share system on your iPhone serves as a hub for actions and share extensions, streamlining the process of saving files, sharing photos and videos, and other important tasks. On iOS 13 the Share Sheet has received a considerable upgrade, including the ability to more easily share content with your favorite contacts.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

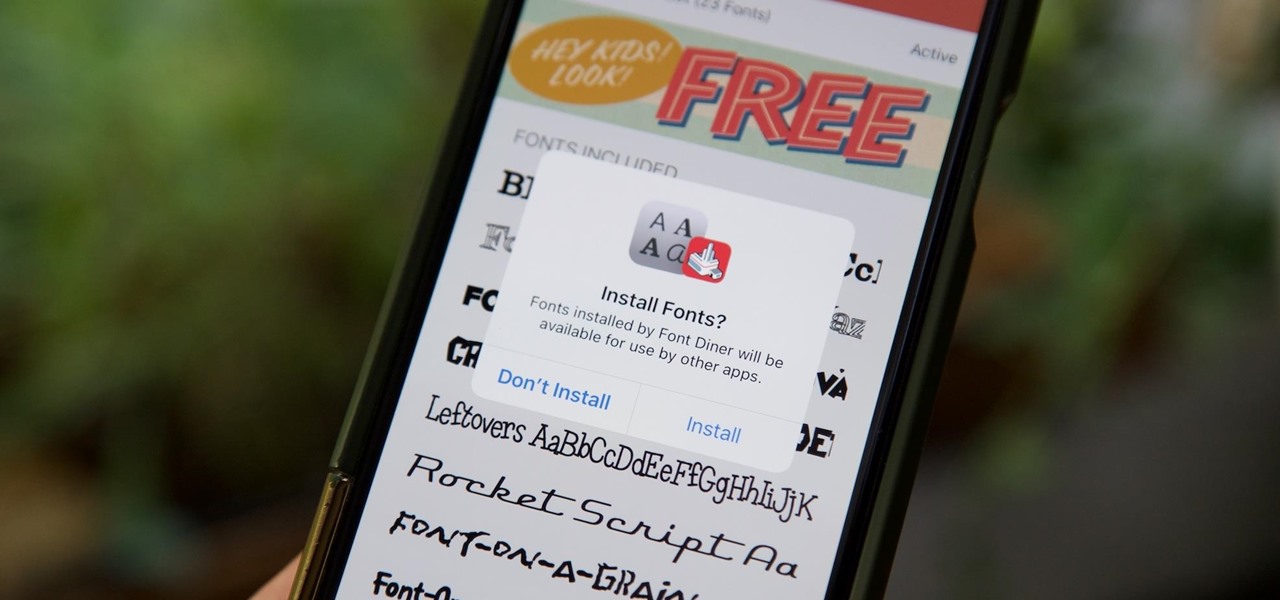
Apple added the option to install custom fonts and use them in different apps on iOS 13. The rollout has been a bit confusing, with Apple announcing partnerships with vendors such as Adobe, but also limiting the feature to work with only certain apps. Nonetheless, you can now download and install custom fonts on your iPhone.

For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

While iOS 13 introduces over 200 new features for your iPhone, one of the biggest focuses this year is Photos and Camera. The update completely overhauls the Photos app, creating a more organized and natural way to interact with your pictures and videos. You'll also find a few new tricks in the Camera app. In all, Apple has added over 30 new features to your shooting, editing, and viewing experience.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

You may not know it, but the IPv4 address of your computer contains tons of useful information about whatever Wi-Fi network you're on. By knowing what your IPv4 address and subnet mask are telling you, you can easily scan the whole network range, locate the router, and discover other devices on the same network.

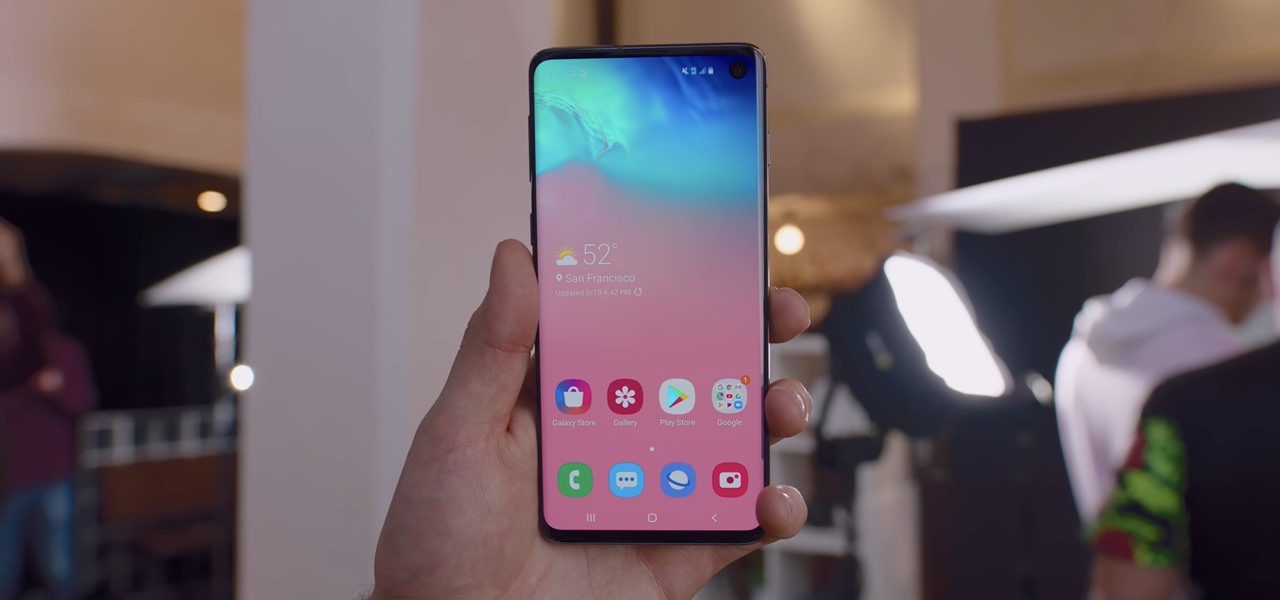
The Galaxy S10 has finally been revealed to the masses, and it certainly doesn't disappoint. As the flagship to herald the tenth anniversary of the venerable Galaxy S line, the S10 has kept popular and familiar design elements like the immersive Infinity Display while employing new features like more advanced cameras to set a new standard for other OEMs to follow.

On the surface, Instagram is pretty intuitive, so you might think that you already know everything there is to know about using it on your iPhone or Android phone. But this photo and video-sharing app is constantly adding new features, some of which don't make the press releases. Even if you're an Instagram guru, chances are you've missed one of these hidden goodies.

When it comes to attacking devices on a network, you can't hit what you can't see. Nmap gives you the ability to explore any devices connected to a network, finding information like the operating system a device is running and which applications are listening on open ports. This information lets a hacker design an attack that perfectly suits the target environment.

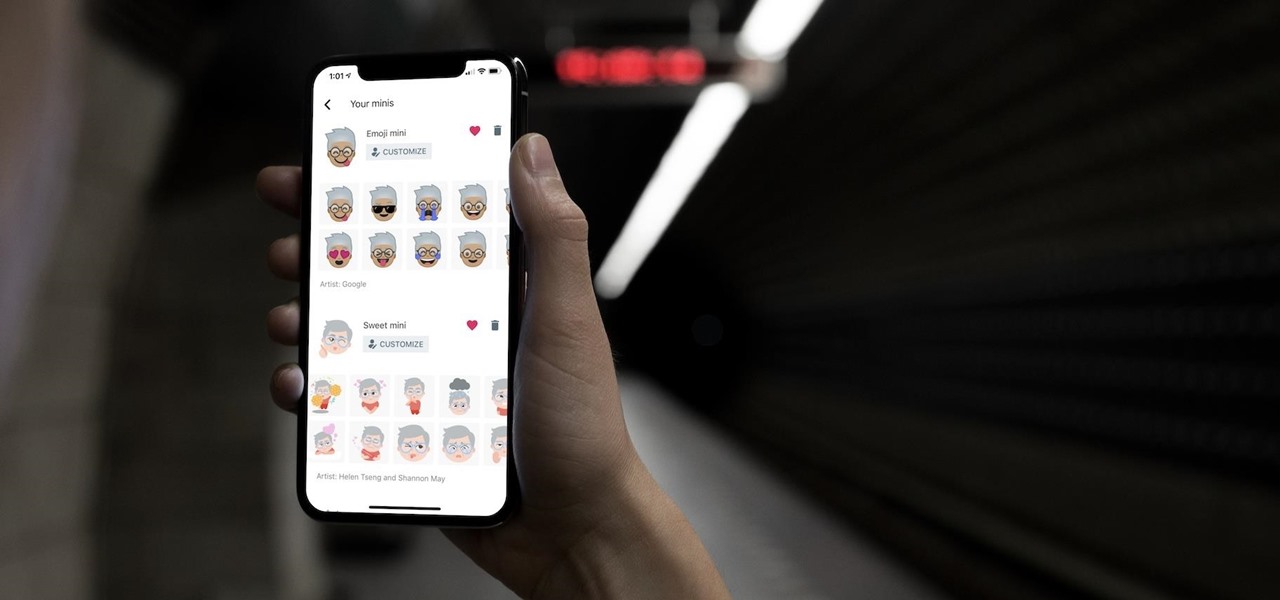
Expressing yourself during chats is much easier these days thanks to the steady rise of emoji. Now, products like emoji Minis for Gboard are taking the craft to an interesting yet familiar new level. With emoji Minis, you can automatically create stickers based off your own face. From there, you can further customize the stickers by adding key features such as glasses, earrings, and facial hair.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

While there are over 100 cool features iOS 12 has to offer, there are some things Apple has made more annoying on iPhones or just has not addressed yet.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

The calendar app is one of the unsung heroes found within your iPhone. It's the ultimate personal assistant that you've come to rely on to keep track of your schedule and ensure you never miss a class or meeting, all while reminding you of upcoming birthdays and deadlines to help maintain good relationships with loved ones and colleagues.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

Developers creating login systems know better than to store passwords in plain text, usually storing hashes of a password to prevent storing the credentials in a way a hacker could steal. Due to the way hashes work, not all are created equal. Some are more vulnerable than others, and a little Python could be used to brute-force any weak hashes to get the passwords they were created from.

Electronic warfare tactics work by jamming, disrupting, or disabling the technology a target uses to perform a critical function, and IoT devices are especially vulnerable to attacks. Wireless security cameras like the Nest Cam are frequently used to secure critical locations, but a hacker can surgically disable a webcam or other Wi-Fi connected device without disturbing the rest of the network.

We're all aware that Google collects a notable portion of our data. Thanks to the increasing awareness, Google has added a number of privacy controls to limit data collection. But Google doesn't just collect personal data for no reason — many of your favorite apps will use this info to improve their services and add new features.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

After a hacker has configured Metasploit on a remote private server, created a resource script for automation, and created a simple payload, he or she can begin the process of remotely controlling someone's Windows 10 computer with just a few moments of physical access — even if the computer is off.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

In just a few months, Binance has experienced explosive growth, overtaking its rivals to rank among the top three cryptocurrency exchanges in the world by trading volume. Without a doubt, Binance is now among the best sites for trading alt-coins like Ripple (XRP), Stellar (XLM), and NEM (XEM) to name a few.

Koadic allows hackers to monitor and control exploited Windows systems remotely. The tool facilitates remote access to Windows devices via the Windows Script Host, working with practically every version of Windows. Koadic is capable of sitting entirely in memory to evade detection and is able to cryptographically secure its own web command-and-control communications.

The Play Store hasn't been the most secure place for apps lately. A quick Google search for "Play Store malware" will give you a taste of some of the malicious apps that snuck their way onto Android's official app store. Google is aware of the problem and they're tying to fix it, but their new Play Protect program doesn't have a great track record, so you might want to look elsewhere.