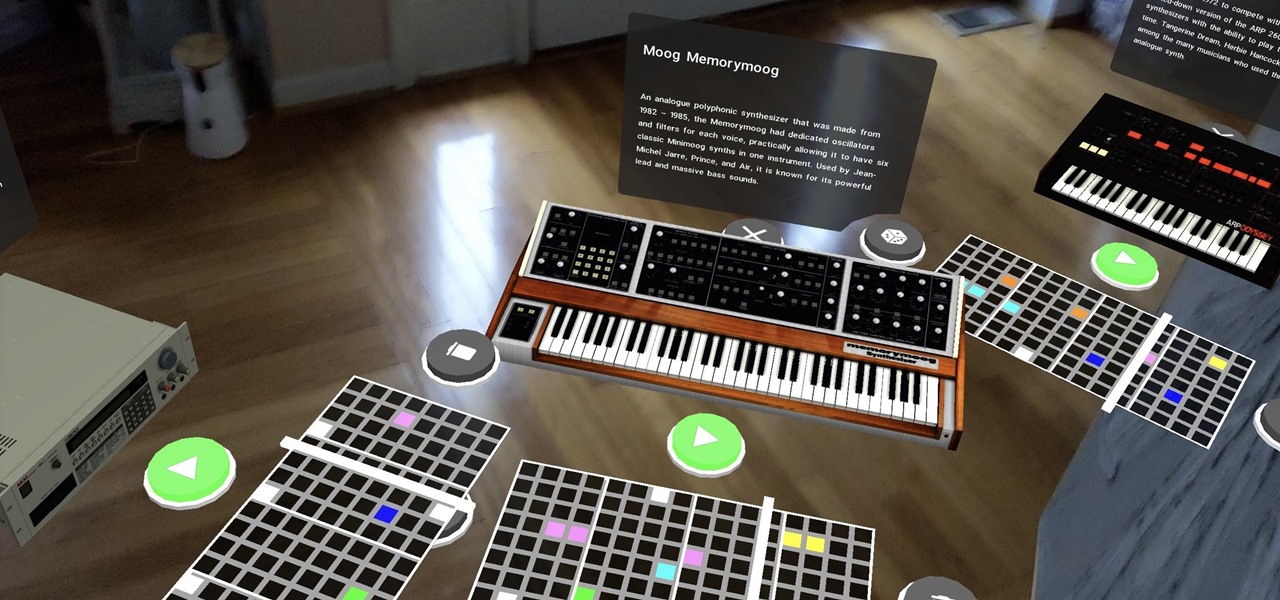
News: Google Arts & Culture Drops AR Synth Exhibit That You Can Play
Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.


Museum curators typically frown upon visitors touching paintings, sculptures, and artifacts, but not when those exhibits are displayed in augmented reality.
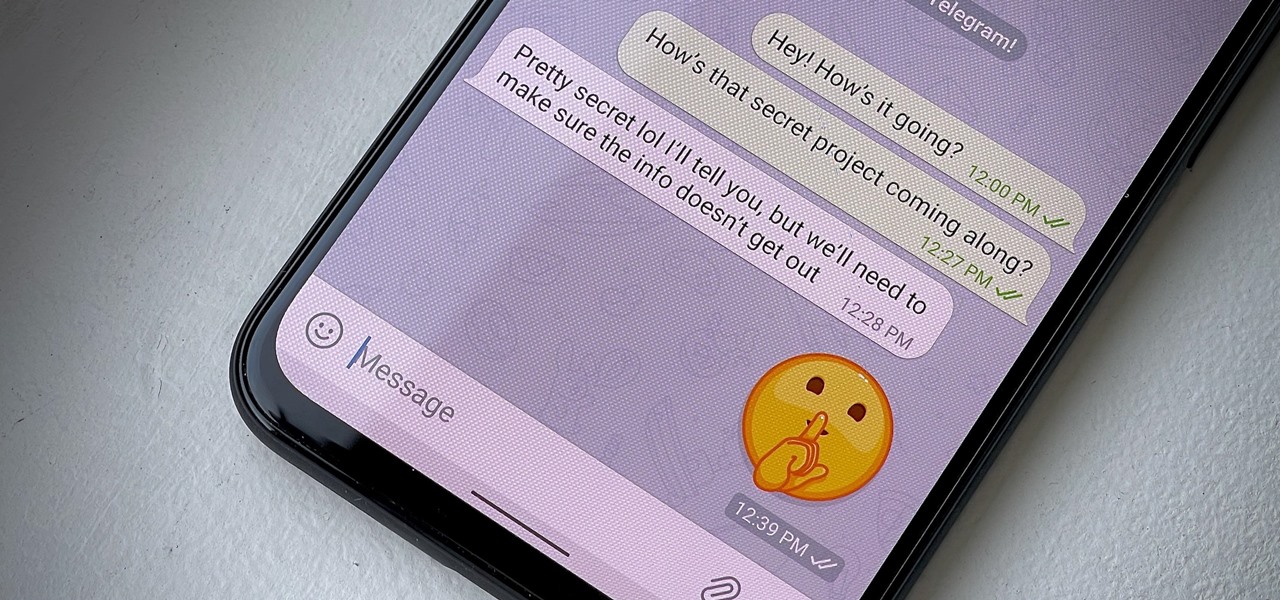
Have some sensitive information you need to share with somebody on Telegram but are worried it might fall into the wrong hands? You don't have to worry anymore because Telegram now sports a way to automatically delete all new messages in any chat of your choosing, not just end-to-end encrypted ones.

We all know how hard it can be to stay productive, especially when working from home. There are many distractions throughout our day. Organizing your workflow is necessary for getting anything done.

Amazon Web Services (AWS) is the premier on-demand cloud computing platform. Offering a wide range of APIs to companies, governments, and individuals on a pay-as-you-go basis, this Amazon subsidiary pulled in over $35 billion in revenue in 2019 alone.

You might be using Zoom on your iMac, playing a Steam game on your MacBook, or completing a work assignment on your iPad, when suddenly you get a phone call on your iPhone. If the same Apple ID is used on all of your Apple devices, the call won't ring on your iPhone only — it'll ring on every damned device.

Every home is a little different, and for a smart home app to work, it has to be able to be customized to work with each person's unique setup. With the iPhone's Home app, everyone can set up a smart home just how they want, including the number and names of rooms, and where those rooms are in the house.

SSH, or the secure shell, is a way of controlling a computer remotely from a command-line interface. While the information exchanged in the SSH session is encrypted, it's easy to spy on an SSH session if you have access to the computer that's being logged in to. Using a tool called SSHPry, we can spy on and inject commands into the SSH sessions of any other user logged in to on the same machine.

For enterprise augmented reality platform makers, remote assistance apps represent one of the greatest opportunities to show off the power of immersive computing. These apps enable experts to guide front-line workers or customers with AR prompts and other content in the field of view of their smartphones or smartglasses.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

What could Apple be planning here? Are we going to see some revolutionary new features for the iPhone? Will we see mostly bug fixes and security patches? It's time to find out, as Apple just released the first developer beta for iOS 13.4.

When filtered through the prism of the top stories of the year, the business of augmented reality 2019 was defined as much by epic failures of AR startups as it was by the promising developments that propelled the industry forward into 2020.

There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much everything on your device without even touching it.

After facing reports of financial troubles over the past month, Magic Leap came out swinging this week with a big push for the enterprise segment of AR, including a repackaged Magic Leap 1, a suite of enterprise apps, and updates to Lumin OS and its supporting development ecosystem. Oh, and its AR headset managed to win a starring role in the marketing juggernaut for the forthcoming Star Wars movie.
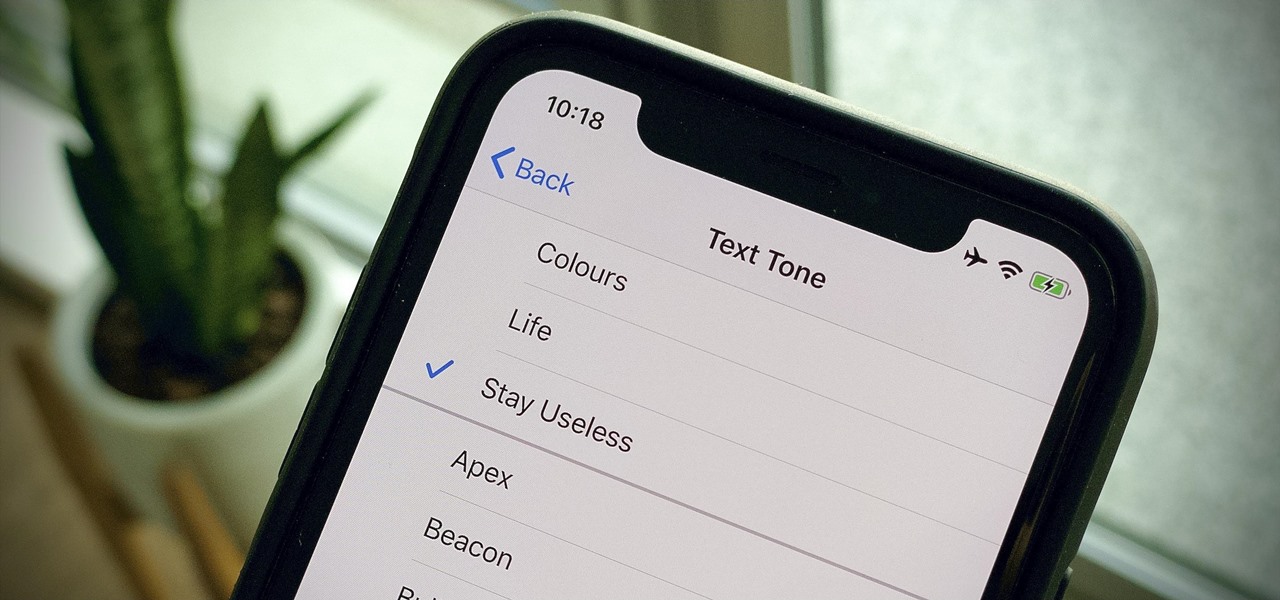
Apple hasn't refreshed its text tones on iPhones since iOS 7. That's six years of the same sounds. And while text tones like Bamboo and Hello have undoubtedly aged like fine wine, that's still too long to live with the same old sounds day after day. Let's take matters into our own hands — let's make our own text tones, right in Music on macOS 10.15 Catalina.
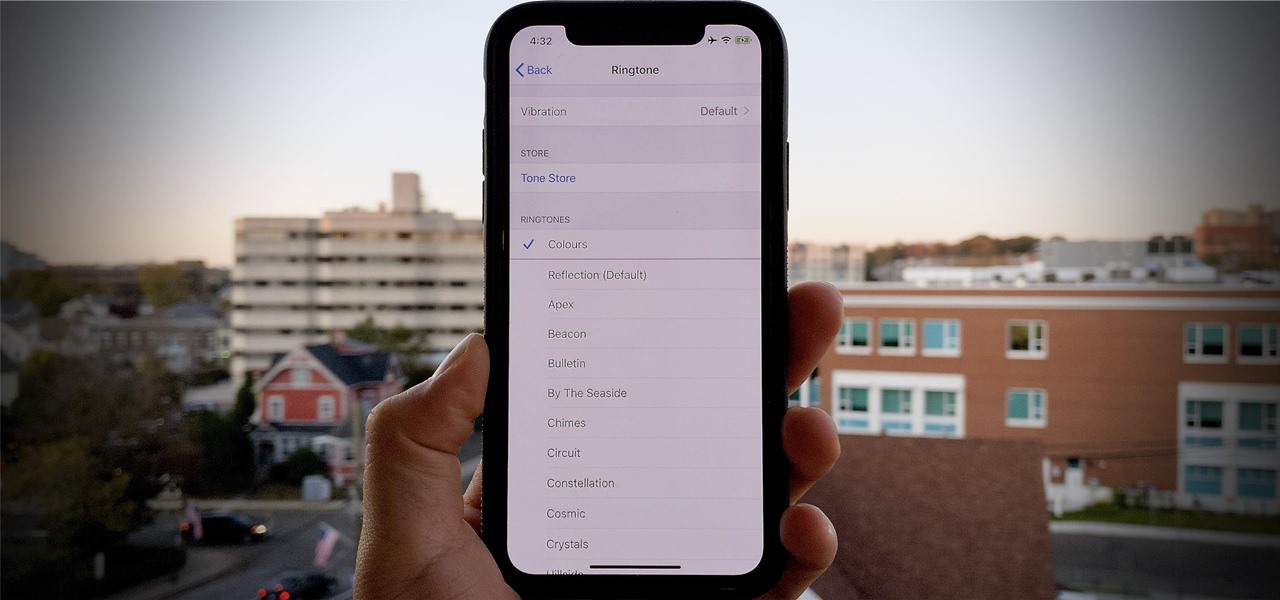
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can create your own custom ringtones right on your Mac.

Businesses leave paper trails for nearly every activity they do, making it easy for a hacker or researcher to dig up everything from business licenses to a CEO's signature if they know where to look. To do this, we'll dig into the databases of government organizations and private companies to learn everything we can about businesses and the people behind them.
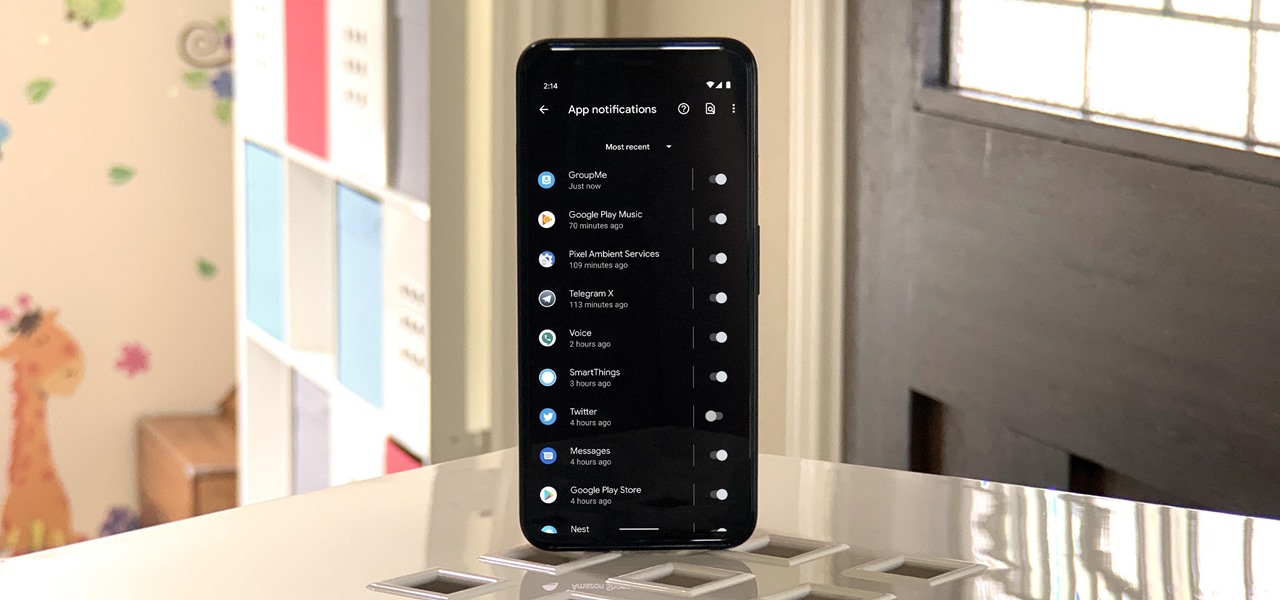
Sometimes you might find that a certain app keeps sending you notifications. What are you to do? There are plenty of useful apps that might send one too many push notifications, but that doesn't mean you should dump them. Luckily, Android gives you complete control over how each installed app handles notifications.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

Indian startup Dimension NXG is launching augmented reality headsets into India's consumer market with a bold idea: focusing on immersive computing in education on the high-end. The plan is to give a new kind of AR headset to schoolchildren in remote Indian villages, starting from class 5 (age 10) until graduation.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.
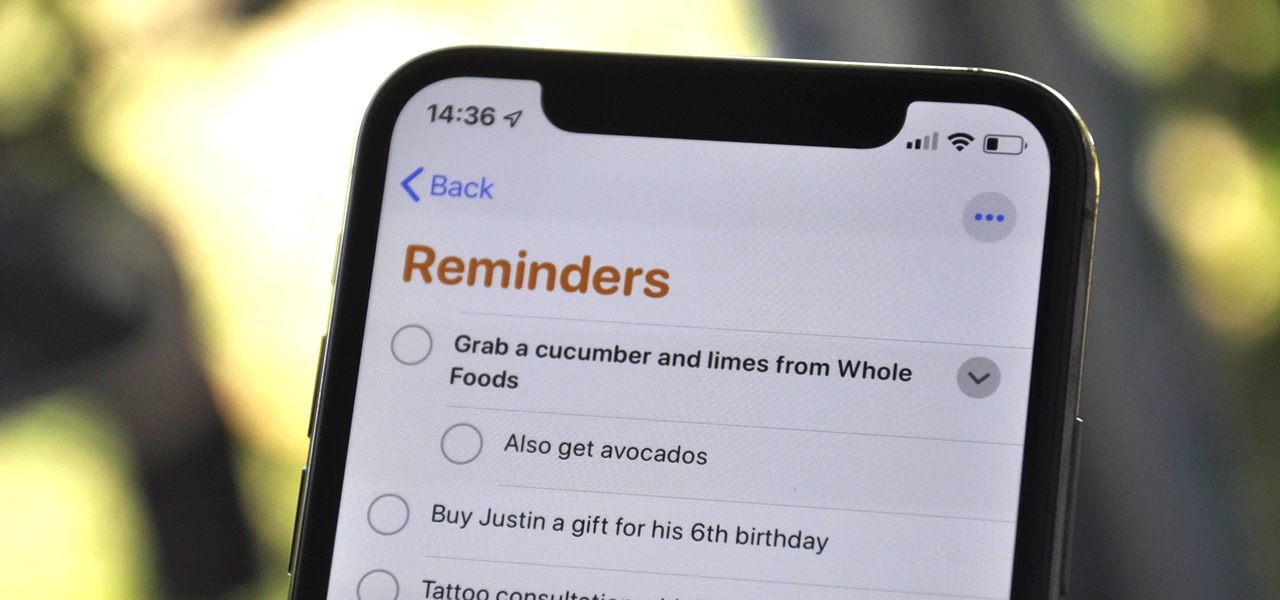
Things are a bit more organized in Apple Reminders, so the cluttered mess that it once was is no more in iOS 13. The slapped-together feel in older iOS versions was the main reason I never used it that much, but the updated version for iPhone has finally got me hooked.

Safari has always done a great job at letting you browse the web, but it has never so much as offered a way to download files locally. Other apps have stepped in to help fill the gap, but they never felt as integrated into the iPhone as a native downloads manager would. They aren't needed anymore though, because Apple added one in iOS 13, pushing Safari on the iPhone closer to its sibling on the Mac.

Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.
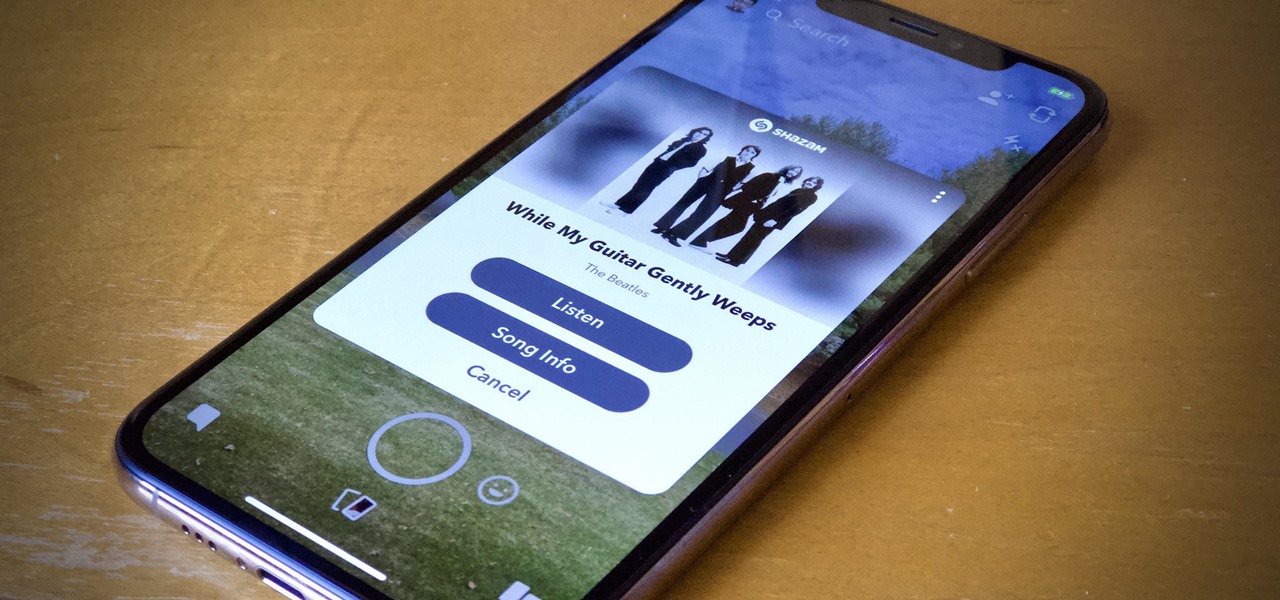
Say you're sending a snap to a friend at a restaurant, bar, store, what have you, but you're curious about the song that's playing in the background. You could leave the app to Shazam it, or you could ask screen-hogging Siri or Google Assistant what the track is, but why not just have Snapchat do the work for you? With its built-in scanner, you can discover a song without ever leaving the app.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.
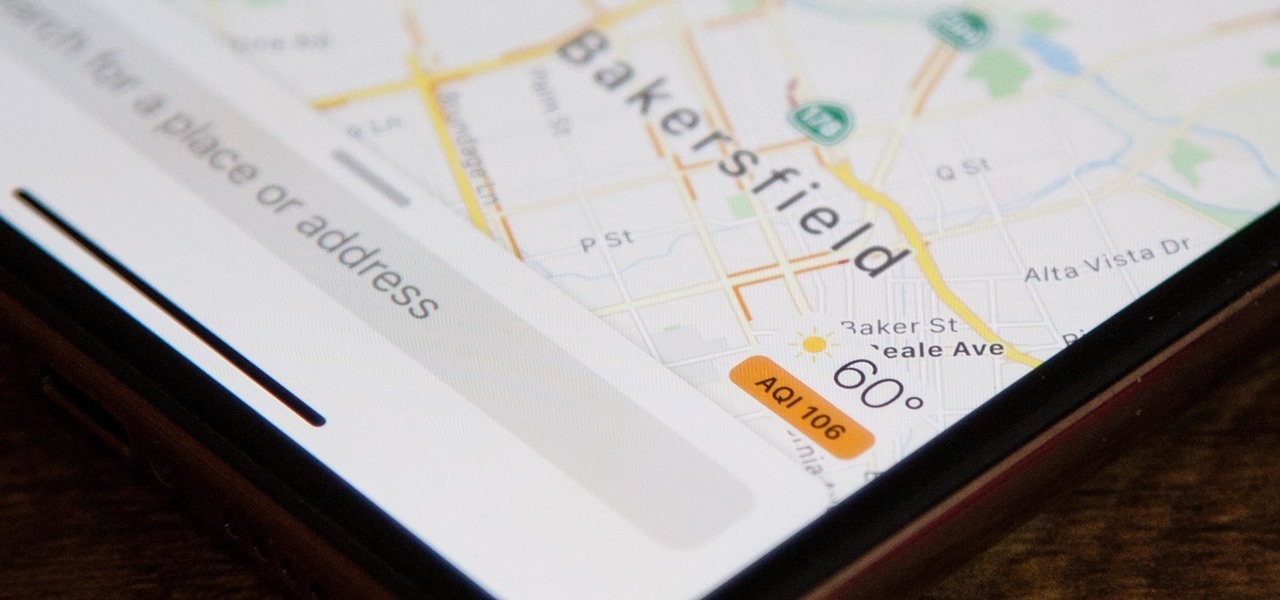
While the United States, in general, doesn't have the worst overall pollution, the air quality can drastically change from one day to the next. If you're particularly sensitive to pollutants in the air, there are apps that show how clean or polluted the air is in your area, as well as in cities you plan on traveling to, but Apple's making those apps less relevant with a new feature in Apple Maps.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.
Your iPhone is just that — yours. Why should your home screen look like everyone else's? While iOS, and by extension, Apple, famously locks its users into its way of doing things, there's a lot more room for customization than you'd think. Before you make the switch to Android, you might want to see what you can do with the iPhone you already have.

In 2018, augmented reality went from the vague promise of interesting things in the near future to tangible developments in software and hardware, proving that immersive computing is indeed the future.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.

If you store important, sensitive information on your iPhone in Notes, you'll want to be more careful. When Notes syncs across your iPad and Mac via iCloud — devices that family members or coworkers may share — you run the risk of having your notes read, edited, and deleted by other people. Such a catastrophe is easily avoided.

This week, Next Reality released the fifth and final set of profiles on the NR30 leaders in augmented reality, with this chapter focusing on the influencers in the industry.
The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.

Nmap is more powerful than you know. With a few scripts, we can extend its functionality beyond a simple port scanner and start to identify details about target servers sysadmins don't want us to know.