I've been a fan of potatoes ever since I can remember... but mainly because they weren't a big part of my daily diet (which usually consisted of rice). And because my experience with potatoes was so limited, I only knew of two varieties growing up: big, brown Russets and sinewy sweet potatoes. As for cooking with potatoes—well, I'm embarrassed to admit that the only time I cooked potatoes when I was a kid was with the instant kind.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.
How to do an NMAP scan on Armitage to find IPs within a certain range. Armitage is a gui interface of Metasploit, and advanced hacking/exploiting program. It can be downloaded from http://metasploit.com/ and http://fastandeasyhacking.com/ and you will need NMAP. http://www.nmap.org/

Hello fellows nullbyters, first of i will start saying that im addicted to this community, i feel the challenge growing up so fast, all the newbies, amateurs,advanced and professionals hackers around trying their best to help the community, badly but we got some script-kids too but anyway, today we are going to learn how to install and use clanAV in kali linux.. INTRODUCTION

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...
Before I start a series on remote exploitation, I think we should learn the basics of Perl. Perl, Ruby, C, C++, Cython and more are languages that some penetration testers just need to learn. Perl is a great language for multiple things, sadly, like many other scripting languages, it is limited by the environment in which it is designed to work in.

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"

Like the majestic mountain structure it's named after, Apple's latest version of OS X, El Capitan, goes a little deeper to expand on the foundation laid by Yosemite. While the update may not be as monumental as some have hoped, it is an improvement and includes tons of useful new features you don't want to miss.

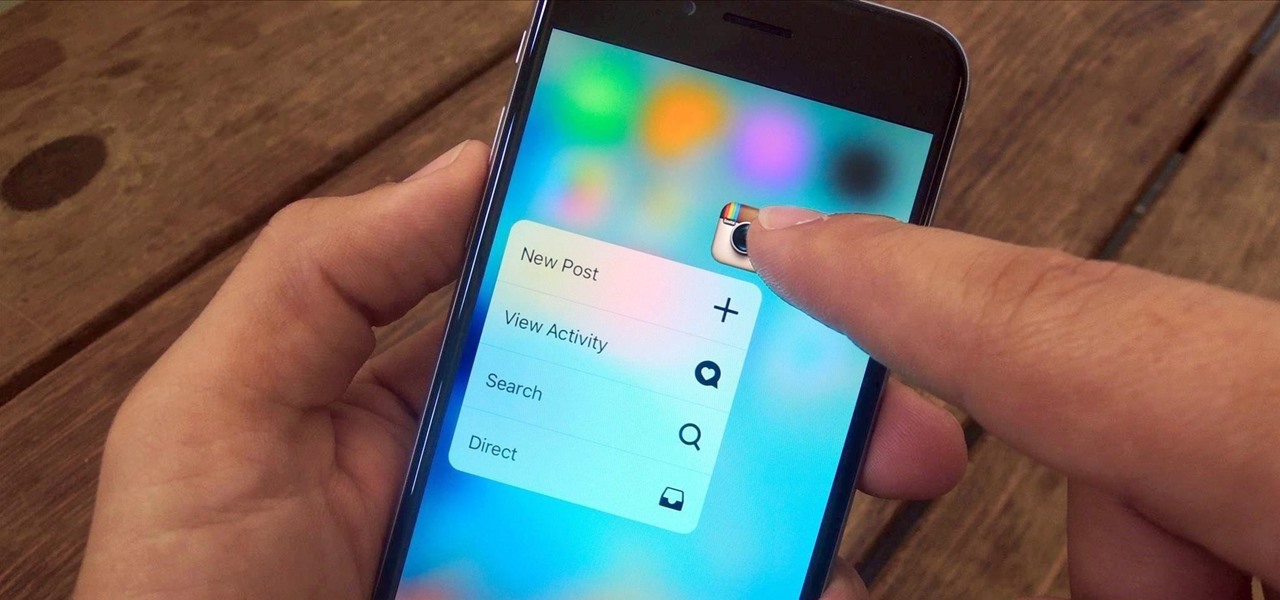
3D Touch is a new feature on the iPhone 6S and 6S Plus that's reinventing the way we interact with our smartphones. With just a little bit of added pressure when tapping on the display, you can perform Quick Actions from an app's home screen icon, "Peek" at emails, stories, and photos in-app, as well as perform other app-specific gestures. Since 3D Touch is such a new concept, here are some of the apps that currently support it, along with the shortcuts you can use.

Recently, I've been experimenting with BeEF (Browser Exploitation Framework), and to say the least, I'm hooked. When using BeEF, you must "hook" the victims browser. This means that you must run the script provided by BeEF, which is titled "hook.js", in the victims browser. Once you've done that, you can run commands against the victims browser and cause all kinds of mayhem. Among these commands, there is an option to use the victims webcam. This is what we'll be doing here today, so, let's g...

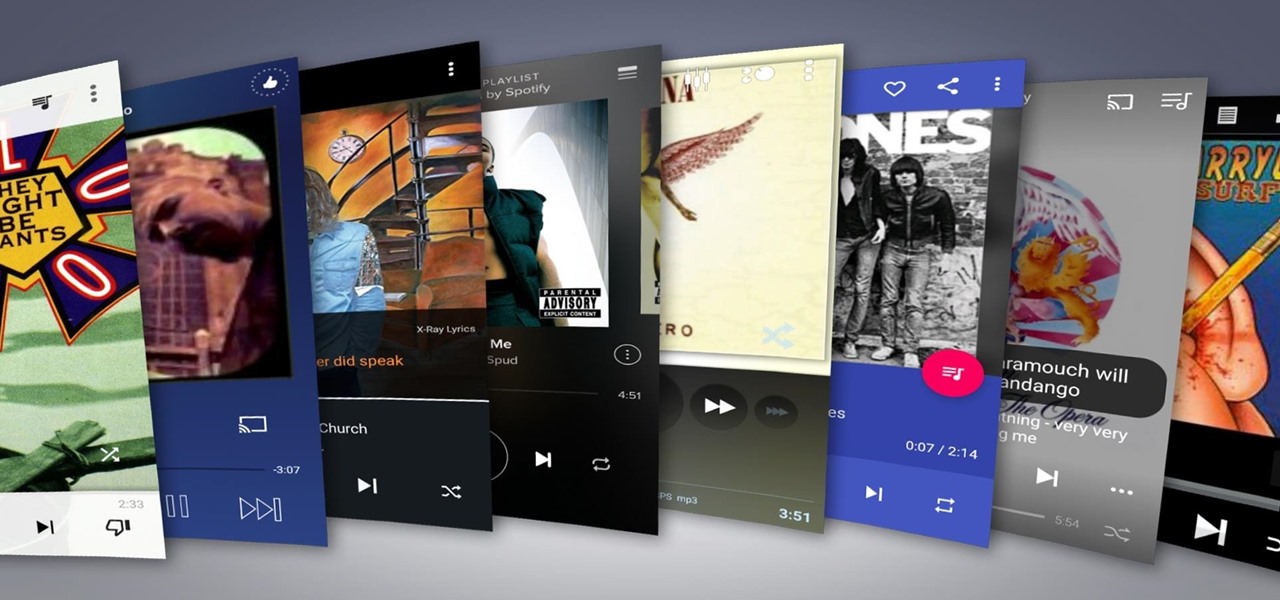
Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

When I tried to set up an eviltwin for a MitM-constelation in kali 2.0, I couldn't provide internet to the victim. The origin was the brctl bridging. I have read many tutorials but all of them where explained in backtrack and older versions of kali. So i was searching for a solution without using brctl and this solution will be explained now. This will just work on unencrypted wireless-environments.

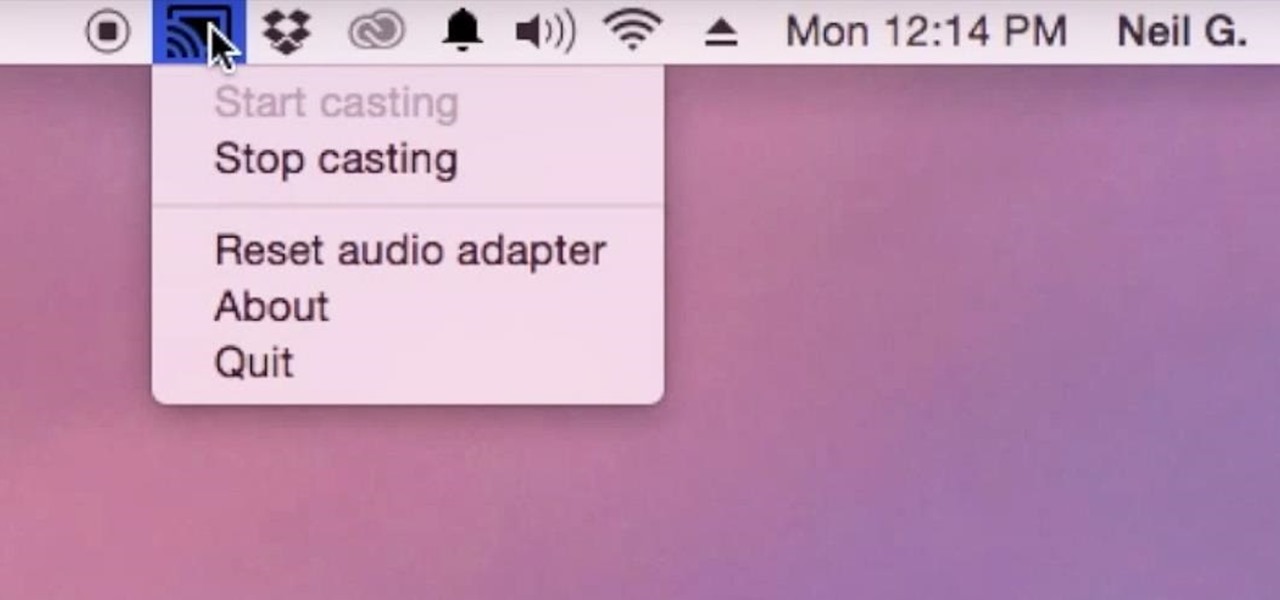
Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

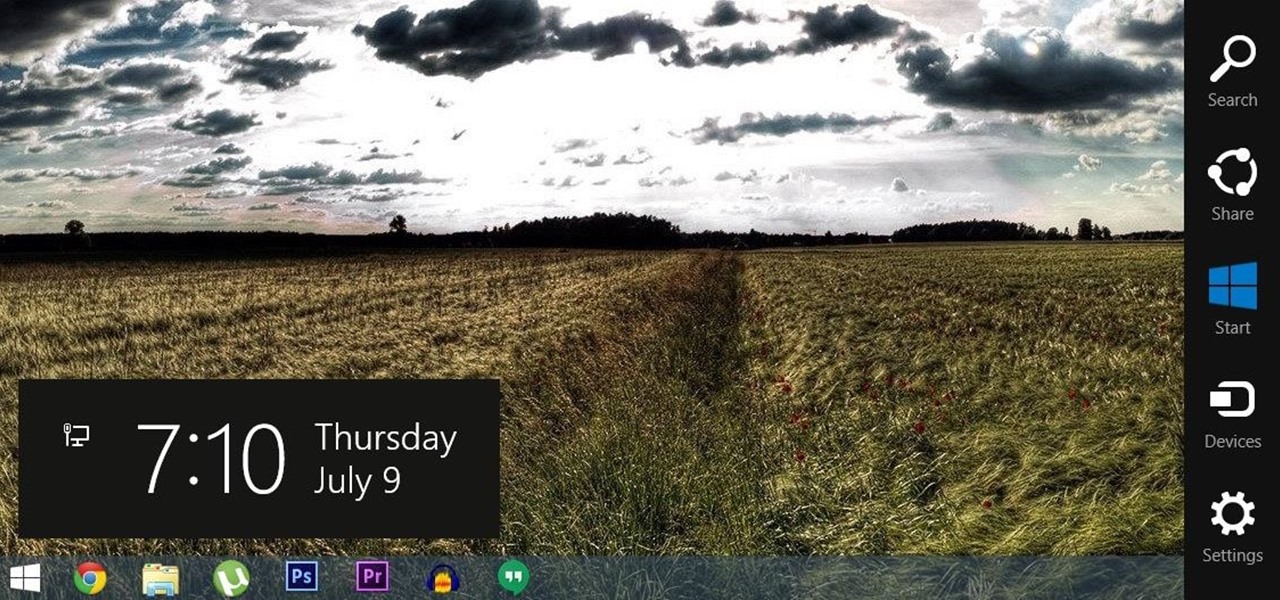
For all of the flak that Windows 8 received from desktop users, it certainly had some interesting and unique features. For instance, the "Charms" bar allowed you to easily access several key menus by simply hovering your mouse pointer in the top- or bottom-right corner of the screen.

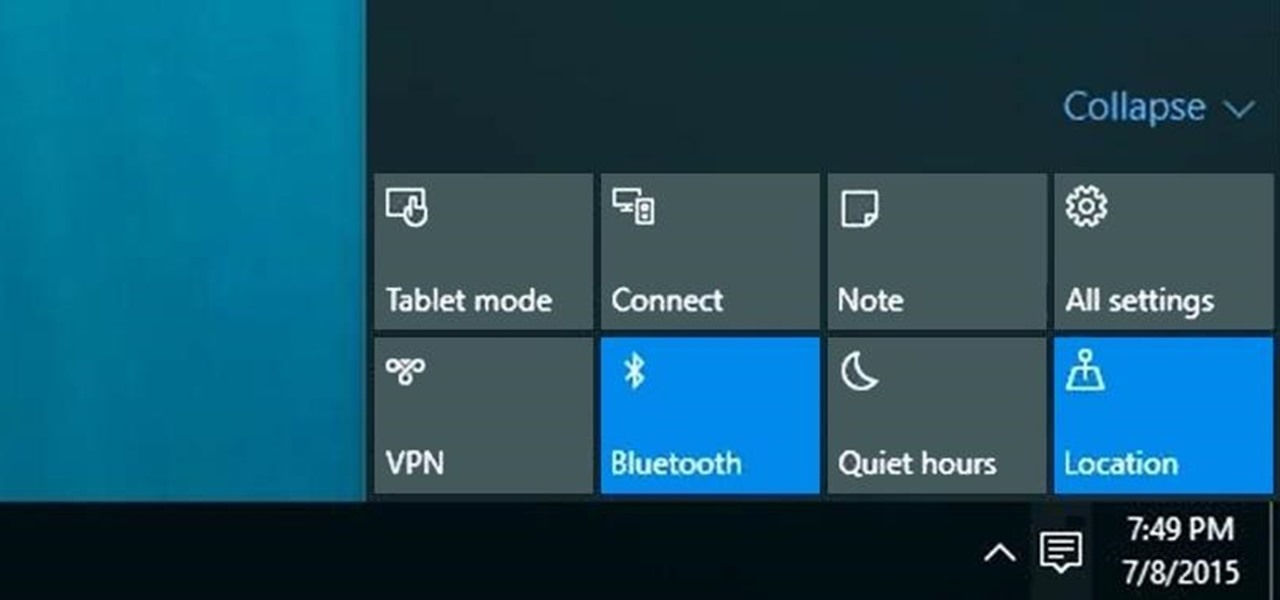
The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

If you've noticed a tiny discolored spot on your computer screen that just doesn't seem to go away, chances are you have a stuck pixel. With modern LCD and OLED screens, there are millions of incredibly small dots (pixels) that make up all of the contents of your display—and within these pixels, there is a set of red, green and blue subpixels. These mix together at various levels to create all of the different colors you see.

Long time reader, first time 'How To' poster. This tutorial has been highly requested. Here are the steps to perform a Pixie Dust attack to crack a WiFi password that has WPS enabled.

Apple announced the release of their newest Mac OS X version at this year's Worldwide Developer's Conference, and it's called "El Capitan." Like the majestic rock formation it's named after (located within Yosemite National Park), El Capitan promises to emphasize and expand on some of the great features we used on 10.10 Yosemite.

Android M doesn't even have an official name yet, but that doesn't mean you can't test out of some of its new features today.

At last, what you all finally waited for! Hi! Fire Crackers,

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

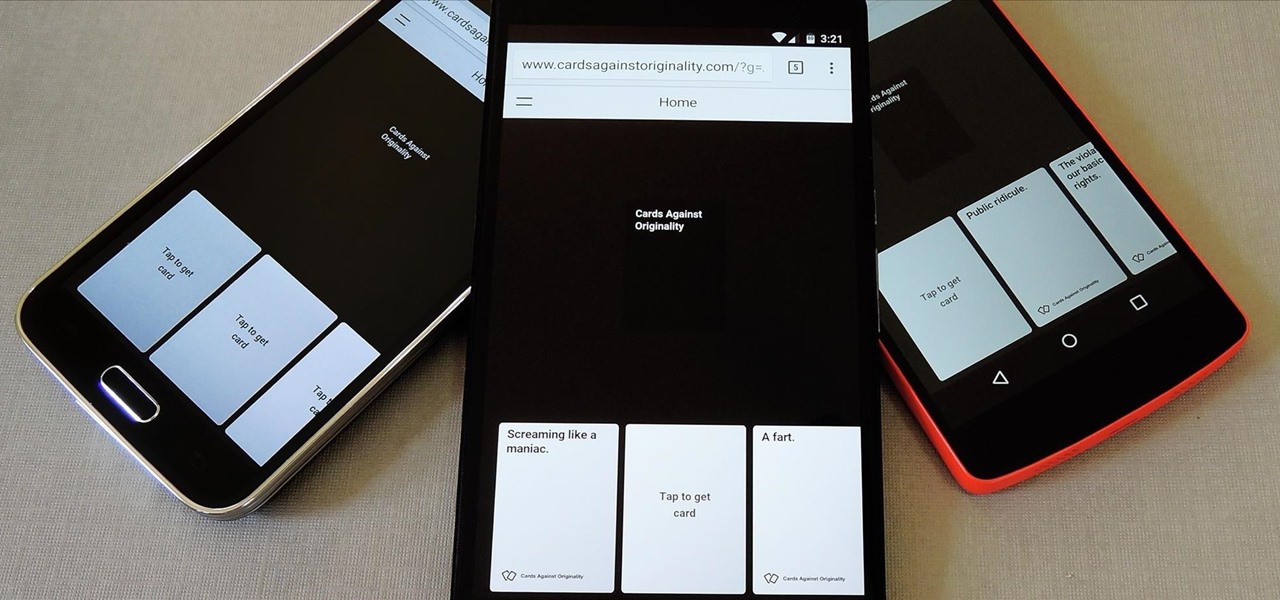
Cards Against Humanity is a popular party game with good old-fashioned raunchy adult themes that go quite well with a few alcoholic beverages. Up until now, though, you had to either print out a set of cards or order the official deck to play—unless, of course, all players happened to have devices that sported the same operating system.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.

With the new year just around the corner, it's a time we all reminisce about the year that was. In the midst of families fighting over white elephant presents and the financial stress that comes with holiday gifting, you may also be dealing with the stress of hosting parties and get-togethers as well as the decorating that goes with it.

One of the main reasons to buy a Nexus device is the fact that they're always the first to get new Android updates. Another great selling point for the Nexus series is that the devices are amongst the easiest to root and mod. Unfortunately, though, these two features are somewhat mutually exclusive.

Apple has been one of the biggest trolls when it comes to adding new features to their software. Whether its adding a new boot screen and not letting all devices use it, or adding Dark Mode and making it a hassle to toggle on and off, there is always to be a caveat attached to each new addition.

Are you someone who always struggles to wake up in the morning, no matter how much you've slept? For most, the thought of getting out of bed any earlier sounds horrific. Yet dragging yourself out of bed and towards the coffee maker a few hours earlier each day can have benefits you've never realized. Here are six reasons that make a compelling case for ending our bad habit of sleeping a little too long.

You can find chili peppers in practically every cuisine. From the sweet Italian variety to the spicy Thai bird's chili and the smoky Mexican chipotle, peppers are ubiquitous and universally loved. But if you find the range and scope of these little fireballs overwhelming, you're not alone.

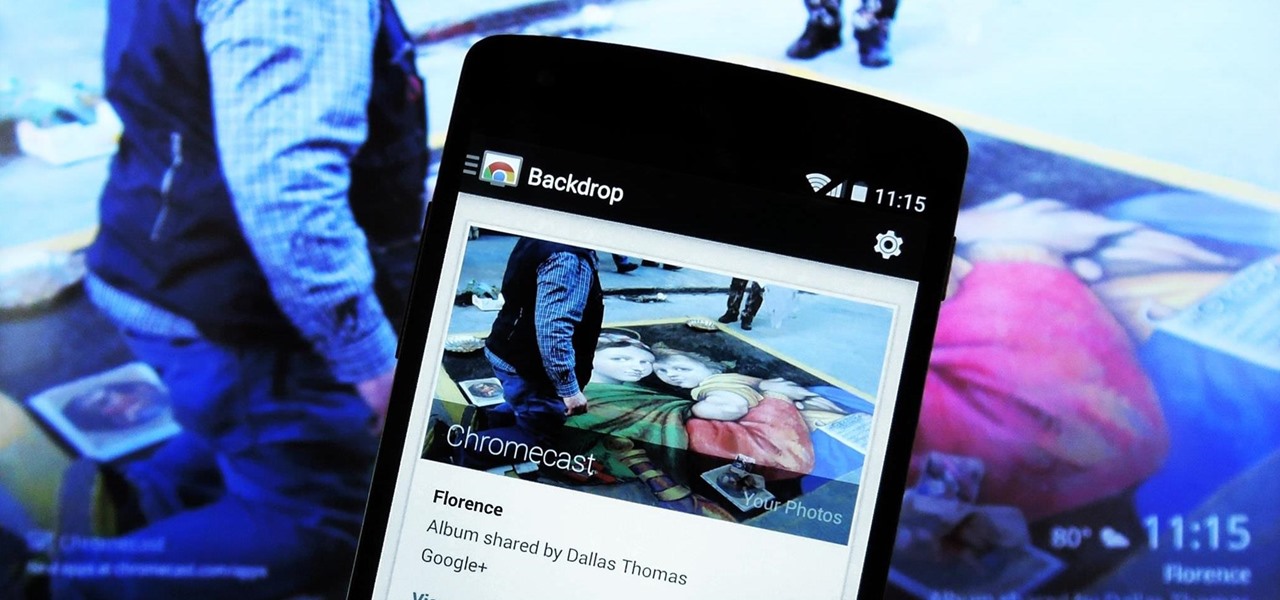
It's been a long-awaited feature since being announced at Google I/O in June, but Backdrop for Chromecast has finally started rolling out. With an update to the Chromecast app for Android and iOS, users will be able to personalize the background images that appear when Chromecast is idle.

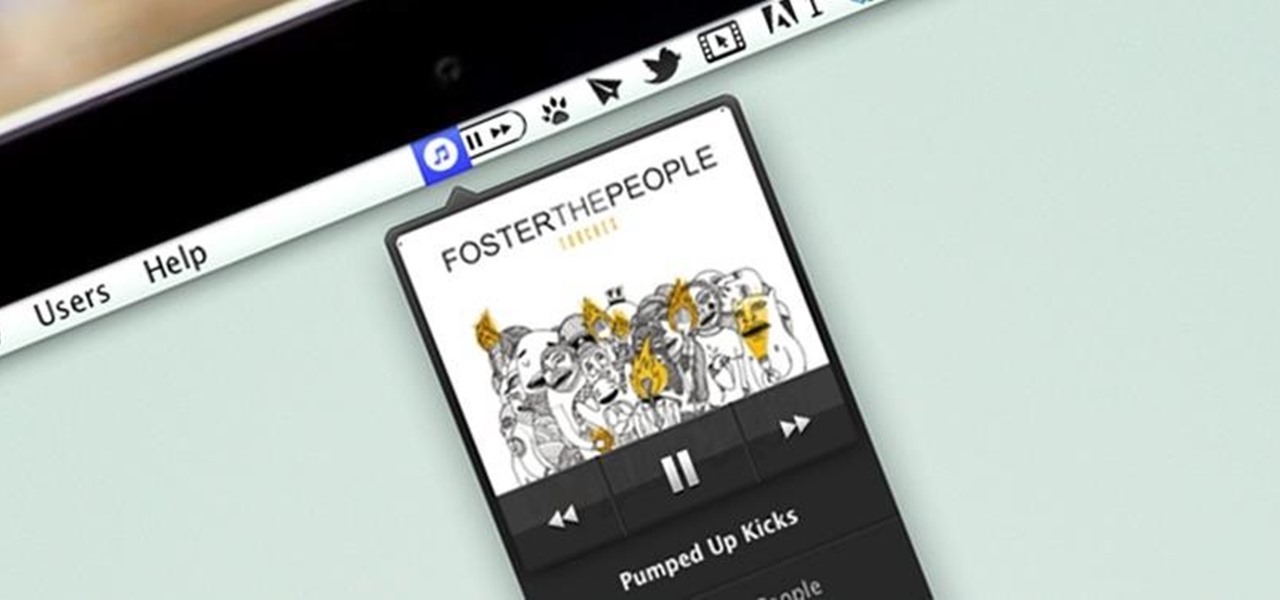
I consider myself a lover of music from all genres, but sometimes a song comes on and I just have to press next. That could be a tedious task, since I often in another app that I'm highly engaged in. Other times, my MacBook is across the room from me without easy access to keyboard shortcuts.

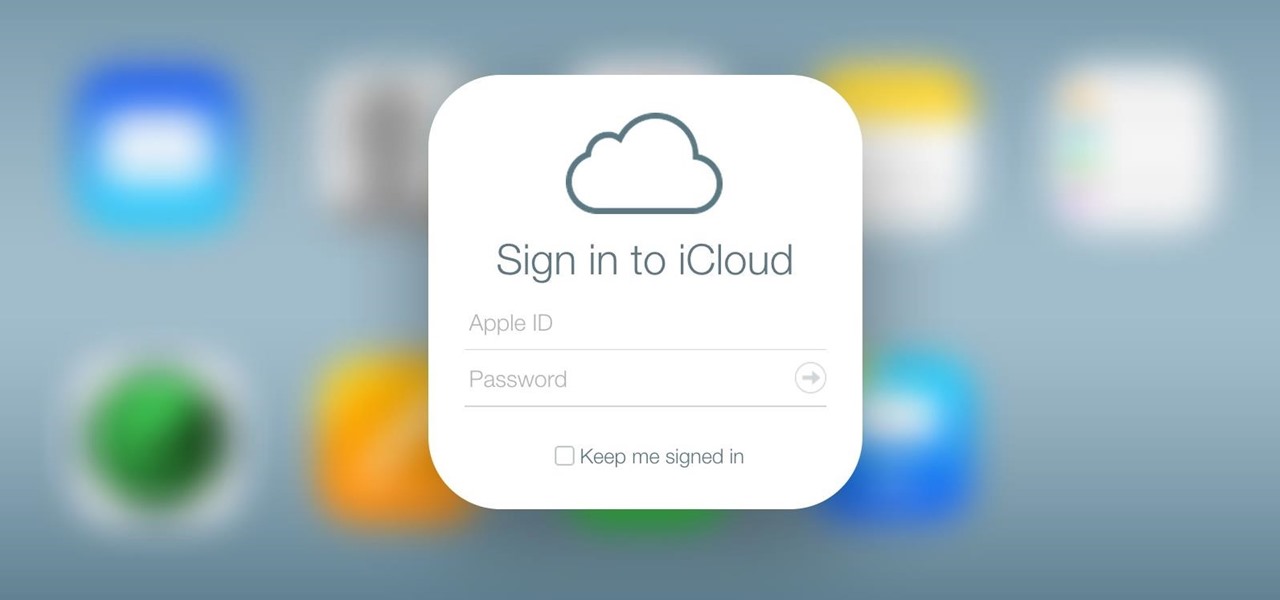
We've already shown you how to free up internal space on your iPhone, and now it's time to tackle another problematic storage issue—your iCloud account.

Whether you are just starting or returning to college, or have already been out in the real world for some time, it's always a good idea to stay on top of your game by keeping your intellect sharp. While it may be easy to just sit in front of your TV, watching reruns of The Big Bang Theory, why not use that time to brush up on some chemistry, calculus, or general learning strategies?

The camera on the Amazon Fire Phone is simple and easy-to-use, with a 13-megapixel rear shooter with optical image stabilization, but there are a couple of features that makes this camera stand out from others.

Remember when MITMing people to pentest webapps and log-ins you had to fire Ettercap,Arpspoof, SSLstrip, then look for credentials in the captured packets?

Unlike the suave 007 that Daniel Craig portrayed, I am not a spy, nor am I that charming, but I do occasionally enjoy taking a stealthy video. Maybe I'm a jerk, but I often catch people doing ridiculous things and just think, "Aren't you embarrassed?"