Don't throw away your dead light bulbs, they may come in handy one day. This video will show you how to start a fire using a dead lightbulb. And no electricity. The tricky part is emptying out the insides, but this can be done with sticks and stones, assuming you're in a survival situation and just happen to have a light bulb with you for whatever reason.

Trying to explain something difficult over the phone can be pretty frustrating if the other person doesn't understand you. Using text messages can be useless for auditory learners, and a phone call won't do much good for a reading or visual learner.

Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

For quite some time, Netflix and Verizon have been duking it out, and it seems that things have just a little saltier between the two:

As a species, our cells are designed to use sugar for energy. Is it any wonder that as humans evolved, we grew to love the taste of sugar?

Online gaming is nothing new, and with live YouTube streams becoming ever more popular, there always seems to be a way to watch people play video games. Twitch TV offers the same spectator experience you've come to know and love, but the people over at TwitchPlaysPokémon have gone a step further and made it so that the spectators are the ones playing the game.

It's easy to take the food we eat for granted, but the truth is, there are a lot of bizarre, wonderful, and just plain weird things about what we eat and drink, the effects it has on our bodies, and vice-versa. Read on to learn how bugs provide food dye, the Japanese grow square watermelons, and more.
What is Programming? Why need to learn? How to get started? Which language to choose? While surfing web, you must be encountering various softwares, games, etc. and might be thinking to make one, but don't know where to start. Here, I am starting series in Programming.

Ever since its introduction back in iOS 6, AirPlay has been helping us iOS and Mac users stream content over to an Apple TV or third-party speaker system. It's an incredibly useful feature. However, it's also severely limiting. The few compatible products out there are extremely expensive, making wireless streaming a not-so-easy task.

Bridal Bun Hair Style Tutorial For Beginners!!!! For the ultimate look of an elegant bride, this super cool yet graceful Bridal Bun Hair Style is an ideal adornment. Make your most special day your most cherished one by following these simple and easy steps Step 1:

How to make Super fast and Easy friendship bracelet: This bracelet can make each person. Tie 3 strings together creating a loop. Put your beads in each string. Tie the ends of each string so that your beads dont slide off. Start making a braid and braid at least 2-3 inches before you start adding the beads. Add your beads on the outside string and braid till you get your desired lenght. You can also use different color beads or cords and make more colorful bracelets. This will allow you to qu...

What kind of music do you like? It's a classic first date question that reveals so much about the person answering, but when it all comes down to it—everyone likes or listens to music. We may each have our own unique tastes and interests, but music is usually something almost anyone can get behind.

This year, like every year before it, Black Friday sales are starting earlier than ever. A lot of stores will be opening their doors as early as 5pm on Thanksgiving to get a head start on the madness (and it really is madness). As we've discussed in the past, one of the keys to emerging victorious on Black Friday is to plan, plan, plan. So, we've compiled some of the best deals in tech, gadgets and appliances to help you prepare for battle.

Now that iOS 7 has rolled out to the general public, with an overwhelming fit of mass hysteria, it's only custom for people to start bitching about battery drain—and I don't blame them. I was experiencing some rapid battery drain after first updating my iPhone 5, as well.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

If you're going out in the evening, your makeup is incomplete without enhancing your eyes. Just because you're not sure of the colors that will suite your brown skin tone doesn't mean you won't beautify those eyes. Follow along with this eye makeup tutorial for beginners to see how to get evening eye makeup for dark skin.

We use ADB and Fastboot for so many things in our softModder tutorials, and to get them, you normally have to download the entire Android SDK and install them. But not anymore.

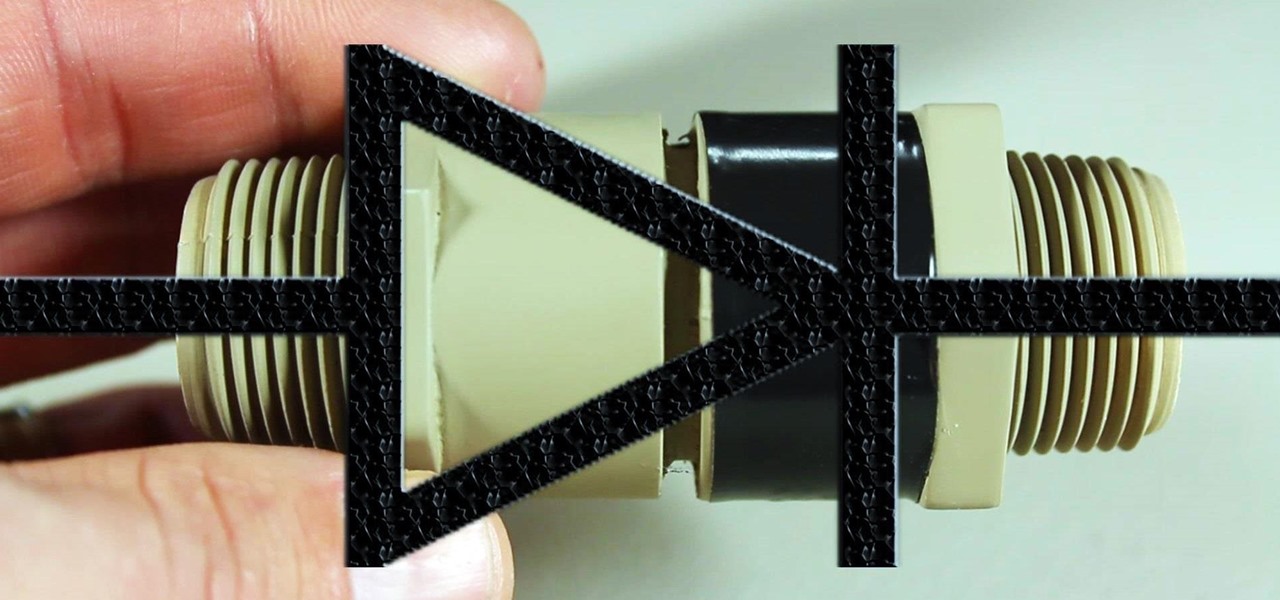
If you're going to build yourself a water gun to cool down this summer, or maybe just a useful water pump, you'll need some check valves. However, the most expensive parts of a water pump or DIY super soaker are usually the check valves. So, let's make some from scratch for as little as $0.35 each.

"What is dead may never die." That's easily one of the best lines (and episode title) from HBO's Game of Thrones series. While the saying may ring true for the Ironborn, it's not quite as catchy when it comes to batteries.

Theming and modding are a big part of the softModder community, but there are endless ways to customize our Android devices. Which ones should you download? Which ones should you avoid? It's extremely frustrating to find them all—and pick and choose.

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it

It's known that during the Thirty Years' War that took place in Europe between 1618 and 1648, soldiers used Swedish fire torches (also called Canadian candles) for heating, lighting, and cooking meals.
Your company is deciding on starting new projects but there is a lot you need to do to make sure these projects are right for your company and will be financially rewarding to the bottom line. Before you begin you and your project management team will need to go through a Project Evaluation Process.

This tutorial is for those who are new to Windows 8.

I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

Thanks to its open-source platform and easy-to-use hardware and software, there's literally thousands of Arduino projects detailed online for anyone to make—a magic mirror, DIY polygraph machine, and hotel-hacking dry erase marker just being a few examples. Hell, you can even make the Daft Punk helmet.

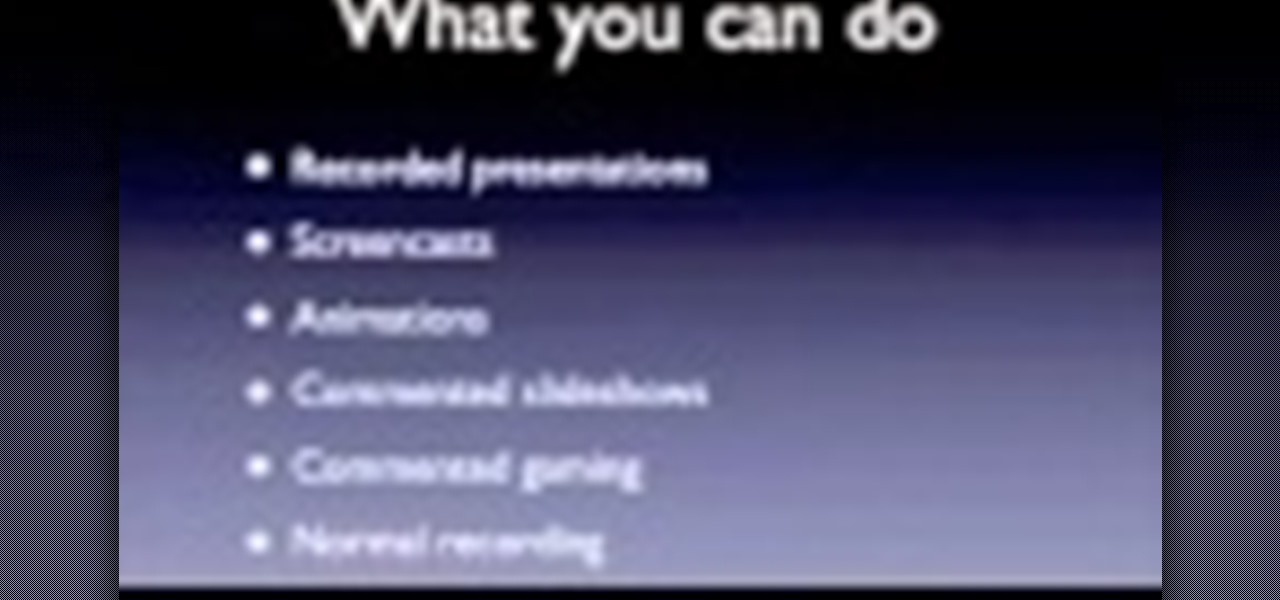
THis video shows you what types of videos you can make, why you should make videos and exactly whant you need to get started.

There are tons of remote controlled cars and boats out there that you can buy or build, and you can add remote control functionality to almost anything. But if you really want to stand out, there are few things more attention-grabbing than this radio-controlled watermelon boat by the folks over at Starting Electronics. The body, obviously, is made from a hollowed out watermelon with a propeller and the parts from a remote controlled airplane mounted on a wooden block. A servo allows the prope...

Clearing the cache on your computer is (usually) a quick and easy way to help speed it up. Deleting those temporary files frees up space, helping you computer run smoother, especially if you have not cleared the cache for a extended period. However, finding the different caches in Windows 8 is a little trickier than in previous Windows systems.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

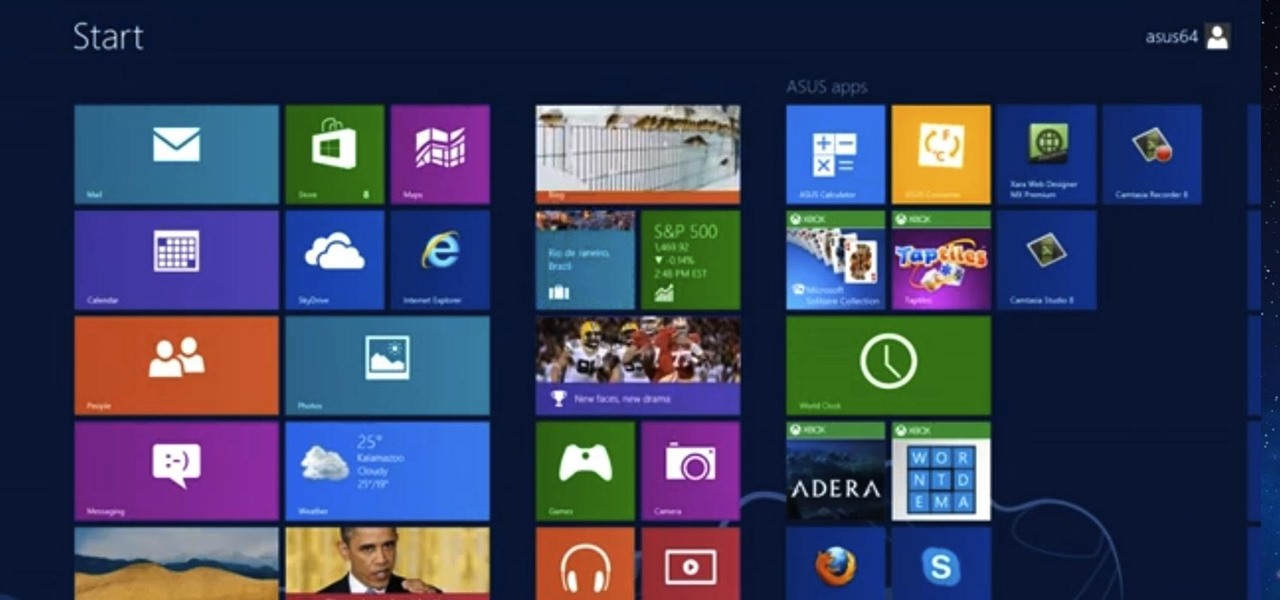
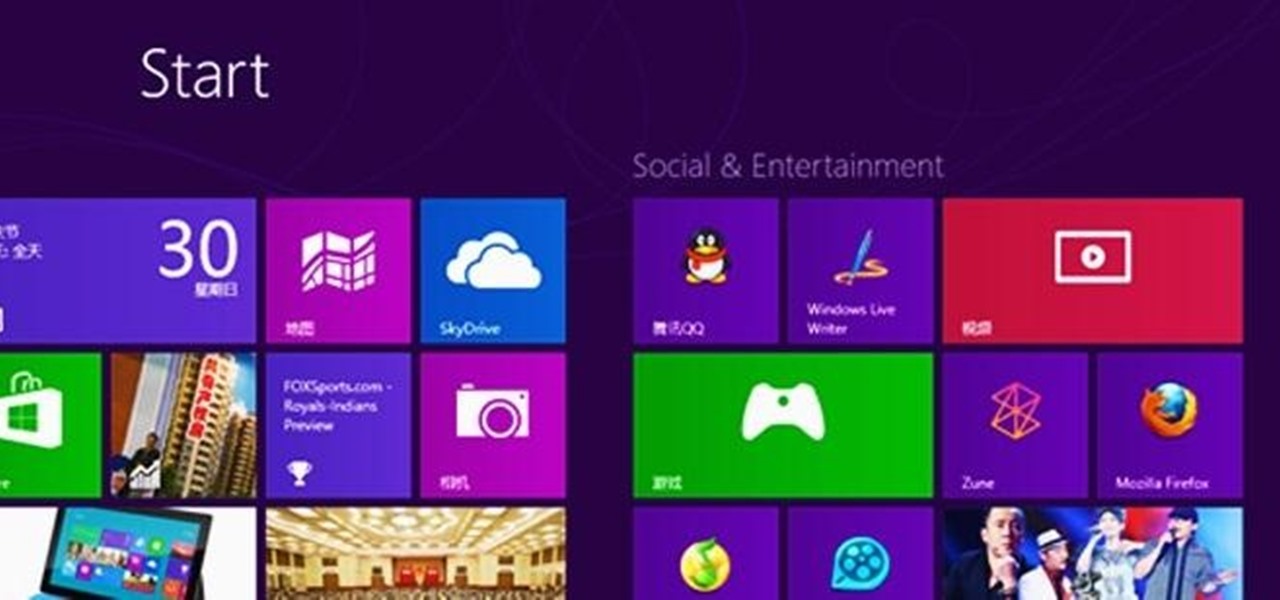
Keeping your computer organized and your desktop clutter-free can be pretty difficult. And with last week's official release of Windows 8, users have another screen they need to get used to organizing—the new Metro-style Start Screen. It uses large rectangular or square tiles in place of the standard icons you've seen on older Windows operating systems. For better organization and grouping, you can group similar items onto a page (similar to many smartphones), you increase or decrease the siz...

Summer is over and autumn is here. Serotonin levels are dropping and people don't have the motivation to be outside as much anymore. So we play Minecraft instead. But walking is cumbersome, so we want minecarts. Remembering to carry one in your inventory or placing one on the tracks might be a bit much to ask for, and don't even get me started on bothering to press a button to make it go.

For people that live outside of the United States, how many times has this happened when surfing through U.S. streaming services? If you're outside of the U.S. market and want to stream stateside services like Hulu, MTV, CBS, Pandora, and others—you're in luck. Tunlr is an application that re-addresses certain data envelopes, tricking the receiver into thinking the data originated from within the U.S. by using its own DNS server's IP address. You can even watch some non-US shows stateside, li...

Programs that run automatically every time you start your computer can slow down your boot time—or just be plain annoying. Many of these programs are rarely used and don't even need to be running for your computer to function properly. So, if you want to disable these auto-run programs and increase your computer's startup speed, here are a few ways you can do it in the new Windows 8.

Video: . You don't have to know how to read piano chords or piano sheet music,- start playing piano right away!

You know how sometimes you accidentally send a minecart shooting out down your tracks, and you can only watch helplessly as it fades into the distance? And then you know that you have to go find it and break it, so that it doesn't stop up your cart traffic on your tracks.
Part of the process to answer the topic question is to discover the answer to three other questions, which are: (1) Who am I? (2) Who do I want to help? (3) How do I want to help?

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

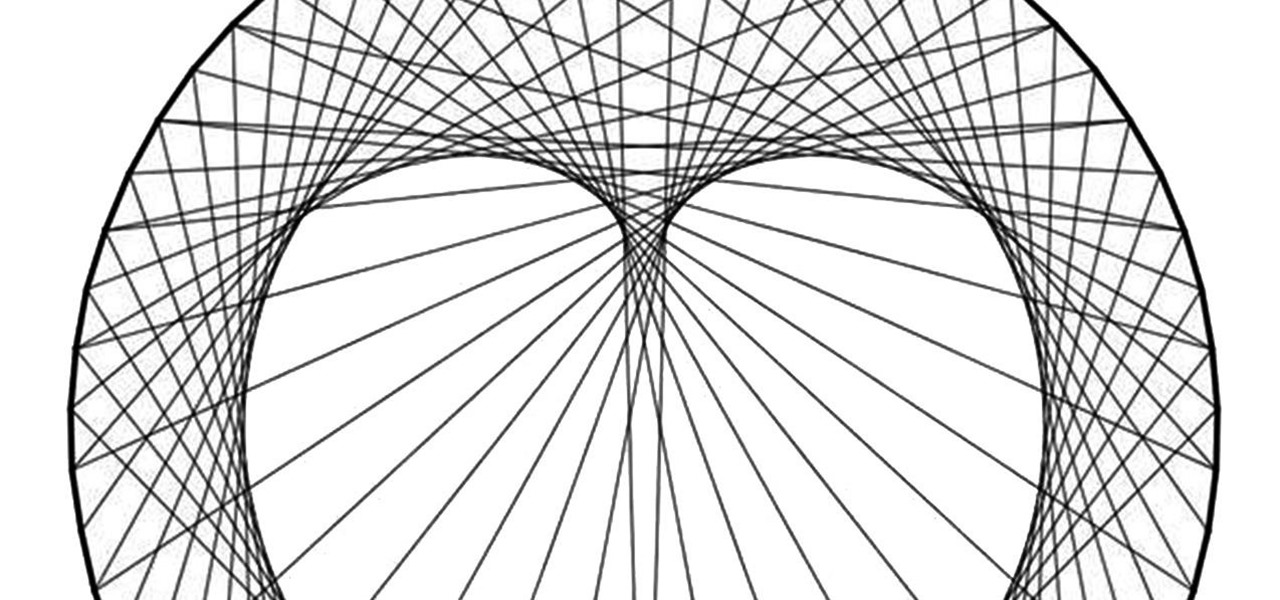
Using only a circle and straight lines, it's possible to create various aesthetic curves that combine both art and mathematics. The geometry behind the concentric circle, ellipse, and cardioid dates back centuries and is easily found in the world around us. From an archery target to an apple, can you name these geometric shapes?