This video shows you how to cook thick steaks of fish cooked with Indian curry. You get all the fantastic Indian masala seasonings to make a rich and flavor full curry sauce which you fish steak will cook in and completely saturate.
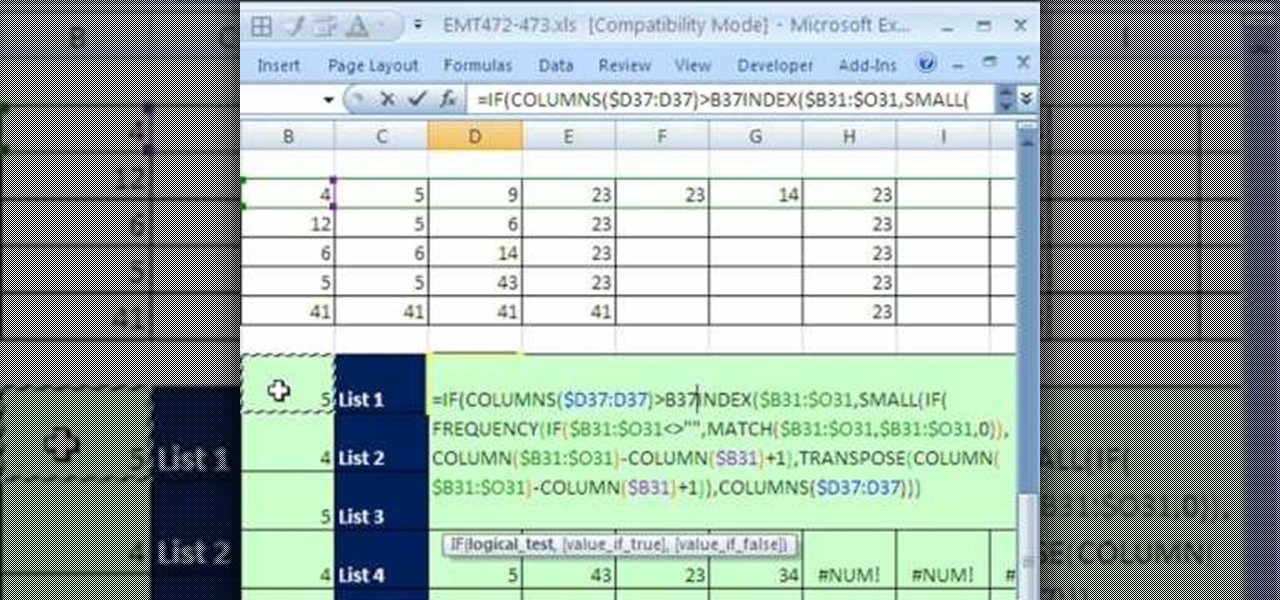
New to Excel? Looking for a tip? How about a tip so mind-blowingly advanced as to qualify as a magic trick? You're in luck. In this Excel tutorial from ExcelIsFun, the 473rd installment in their series of digital spreadsheet magic tricks, you'll learn how to extract a unique list from a group of individual rows.
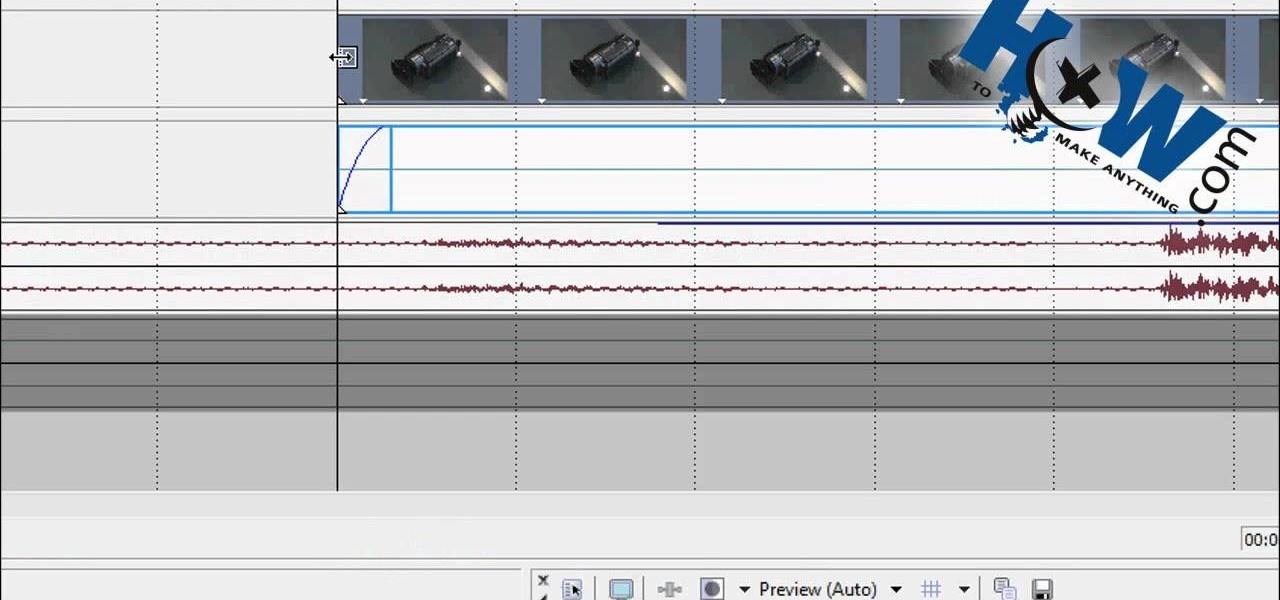
How to Make Anything demonstrates how to make a freeze frame in Sony Vegas. You can go to the preview window and click on save snapshot to file. The program will then create a jpeg which you can lay into your video to create a freeze frame. You can also use Vegas' velocity envelopes to create a freeze frame. First, zoom into your video in the timeline so that you see each individual frame. Make sure that quantize to frames is toggled in the options menu. Then, hit S to split the video. Right ...

Transform a piquant herb into a creamy, sweet paste by oven-roasting garlic with the help of these tips.

Tired of losing your gardening efforts to snails and slugs? Use these methods to banish the pests. You Will Need

People like Ralphige and The Jerky Boys have elevated prank phone calls to an art. Here’s how you can get in on the fun.

If you're record player doesn't work anymore, but it still turns, then this is the perfect solution for you. The video show you how to make a cone record player. It's also a neat trick for playing your records with out a record player, instead of a regular phonograph needle.

In this video tutorial, Chris Pels shows how to use the ASP.NET IIS Registration Tool to configure ASP.NET. First, see how file extensions are mapped to ASP.NET in the IIS Manager on a global and web-site-by-web site basis. These script maps provide the basis for configuring individual ASP.NET applications to run under a specific version of the .NET Framework. Next, see how aspnet_regiis.exe, the IIS Registration Tool command line utility, is specific to each version of the .NET Framework and...

Learn how to do Smith machine inverted palms down pull-ups with release/re-catch at top. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Smith wide inverted pull ups with a hold at the top. Presented by Real Jock Gay Fitness Health & Life.

Learn how to do Smith machine inverted pull ups. Presented by Real Jock Gay Fitness Health & Life. Benefits

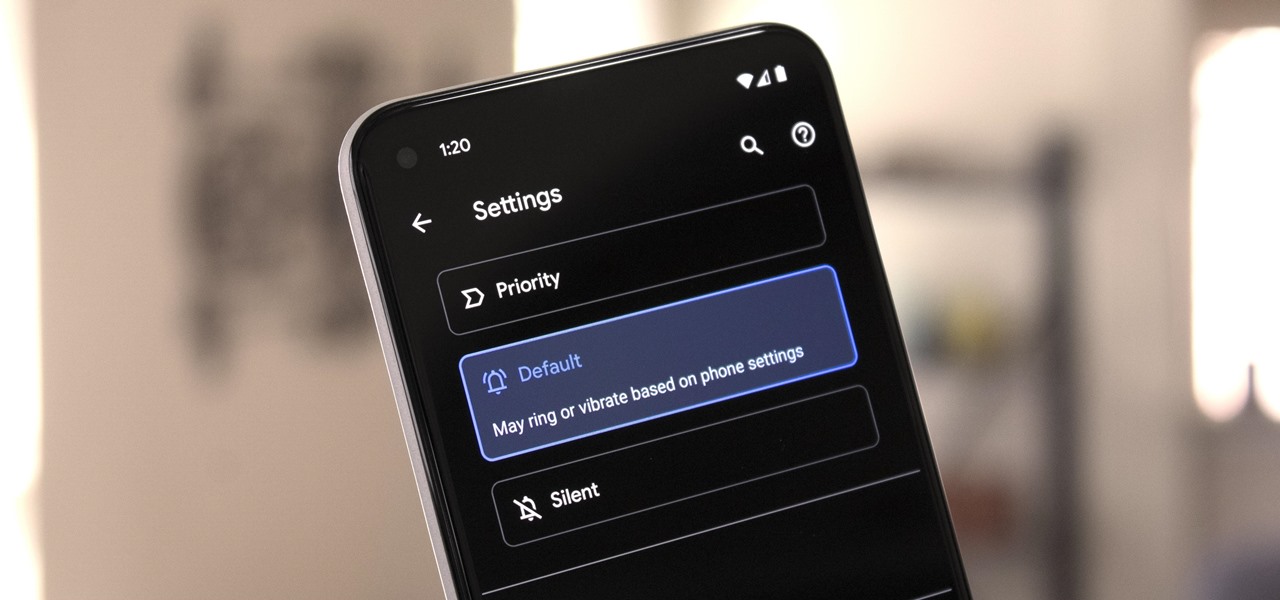
Things tend to get noisy when you're in a big group chat, which is why the notification sound for that thread shouldn't be your standard, attention-grabbing ringtone. But you don't want to set the default notification sound to something too subtle, otherwise you'd miss messages that actually matter.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

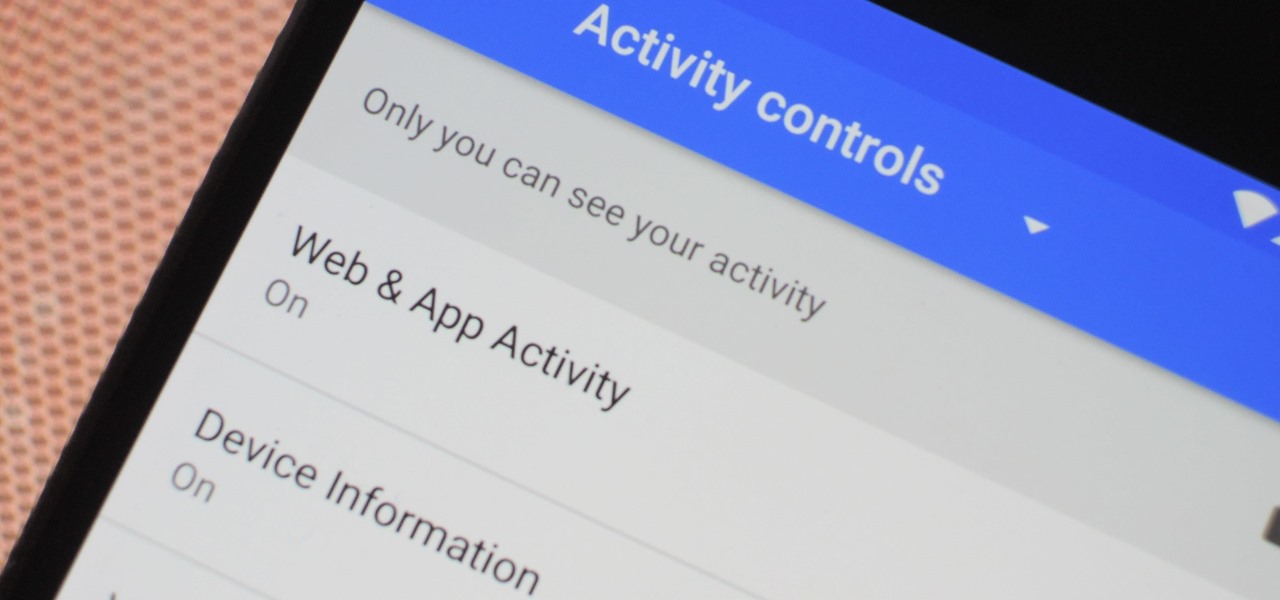
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

New research suggests the bacteria that causes listeriosis may be a bigger threat in early pregnancy than previously thought. Usually considered a danger to late pregnancy, scientists suggest early undiagnosed miscarriages could be caused, in some cases, by infection with Listeria.

Transmitted by a sandfly one-third the size of a mosquito, parasitic Leishmania protozoa are responsible for a flesh-destroying disease that kills an estimated 20,000 people per year. Two new studies offer understanding of how the parasite provides immunity through persistence and why some people suffer more virulent forms of the disease.

Lighthouses and signal fires may have been the first social media. Without the ability to share language, a distant light meant "humans here." A new study from the University of California, San Diego, finds that bacteria can also send out a universal sign to attract the attention of their own, and other bacterial species.

Locking individual apps on your Android device gives you an added layer of security by safeguarding app data from unwanted attention. I personally prefer using an app locker over a standard lock screen because my kids play with my phone, and they've completely disabled it after inputting the wrong PIN. So app lockers give me the right balance between giving my children access to my device, and the security of locking down my data from would-be intruders.

These days, if you walk through Best Buy, you will see an entire area designated to smart home technology. Thanks to the interest and growth of the Internet of Things (IoT), this exciting new technology has finally entered the mainstream. Appliances, thermostats, and even the lighting throughout your house can be controlled from your computer or smartphone. You could also use artificial intelligence; Simply tell Amazon's Alexa what you want your house to do, and she will do it.

For those of us that were blown away by the spatial mapping and user experience in Fragments and Young Conker, the version of spatial mapping that came stock in the HoloToolkit was lackluster at best. It became apparent really quick that to get an amazing presentation would require some heavy shader knowledge and some badass mesh culling skills, at the very least.

Keyboards and mice work fine for computers, but in a holographic environment you'll want to do more than just point, click, and type. While we can still benefit from these input devices, complex hand-tracking methods are necessary for the evolution of mixed reality user interfaces.

On Wednesday, Microsoft launched a chatbot on social media that learns from conversation, and trolls quickly taught it how to be a shameless, Nazi-loving bigot. Oh Internet, an opportunity for a Hitler joke never slips past you, does it? This Is Why We Can't Have Nice Things

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

In my last tutorial I very briefly introduced Zanti , but in this tutorial I will start to show its many features. The first step on hacking is recon . You could use Nmap , but the problem with Nmap on Android is that by itself, in order to gain full functionality your phone must be rooted. Thank goodness for a few geniuses in Zanti's dev team whom managed to implant full fuctionality of Nmap in Zanti without rooting your phone. With that being said, boot up your Android phone and lets start ...

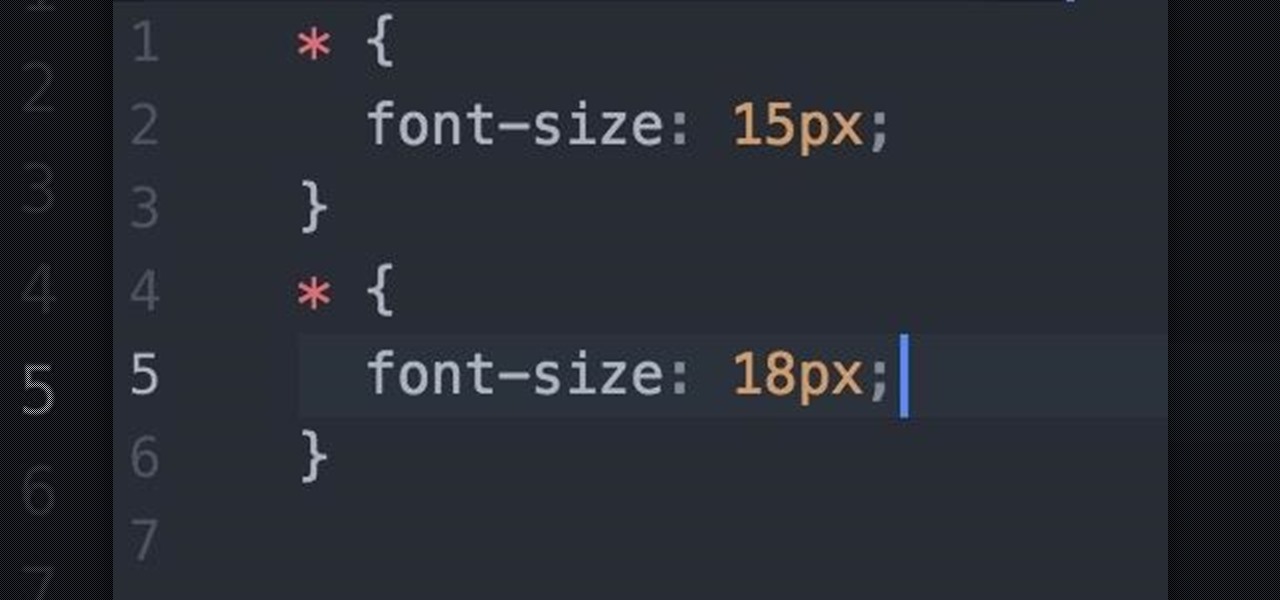
Welcome fellow Null-Byters! I would suggest you watch reading my last tutorial before we begin. In our last adventure, we began making a simple, ugly website. If we want it to make it look good, we should add some styling. But first, we need to understand the basics.

Your brain holds a lot of precious information and is capable of great feats. However, there's one quality that doesn't lie among its strengths—memory security. Yes, that's right, your brain can be hacked, and it doesn't take a psychologist to do it. Anyone with the right know-how can change your memories for their own personal benefit, and you can do so to others, too.

Welcome back, my nascent hackers! Although my favorite TV show, Mr. Robot, had completed its first season already, I have not completed demonstrating the hacks that Elliot used in the show. (By the way, I can't wait for season 2!)

Hello! I'm newbie at Null Byte and I want tho share some of my thoughts with you guys, hope you like it. I've been inspired by 3 facts for making this: 1- The post 'How to write better code', 2- A few illegible comments at some posts, 3- I myself have never written such a long text in English, this will be my first one!

Google made a huge splash this year in their annual Google I/O with an awesome announcement regarding their Photos app. Although I was primarily interested in the details surrounding Android M, my ears instantly perked up when Google announced that their Photos app will now offer free, unlimited, high-quality storage.

Android's permissions system is simple, transparent, and straightforward. When installing an app, you get a chance to review all of the permissions that the app has requested. These can range from accessing your location data to holding a "wakelock" in order to prevent your phone from entering sleep mode. But your only choice in this matter is to accept all requested permissions, or not install the app.

Last year, The New York Times wrote that certain restaurants in Manhattan and Brooklyn banned patrons from taking photos of their meals. That means no flash photography, no standing on chairs for a better angle, not even a quick pic for your Instagram followers before the first bite. Little do these restaurants know, this ban can actually make their customers' food taste worse, so to speak.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Communication is the key to any healthy relationship, and when I say any, I mean human and non-human. Previously, one of the biggest culprits for not understanding what you meant was Siri, but now it looks like it has some competition with the new Kinect system, which can control practically everything on your Xbox One—if it can understand you.

Go above and beyond tea bags and enjoy the spicy taste of a chai tea latte. It's a combination of spiced chai tea with milk that's usually steamed from an expresso machine, but there's no reason to get all fancy with your chai. This video will show you how to make some flavorful chai tea lattes without special equipment. You can easily adjust the spices to suit your taste buds.

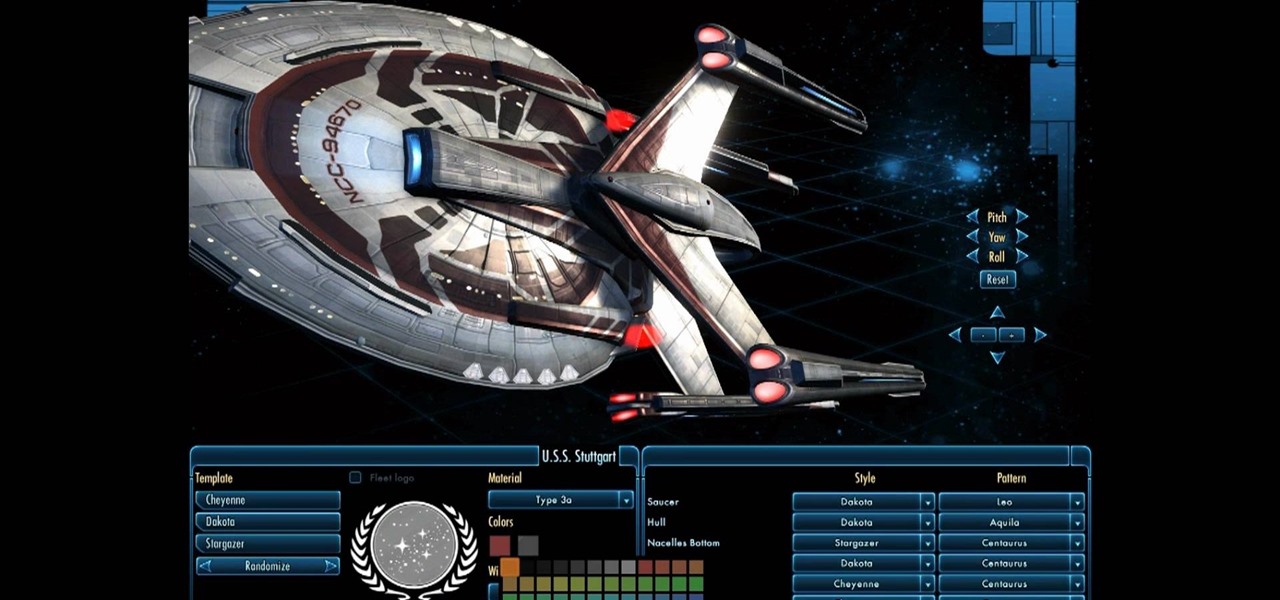
In Star Trek Online, not only do you play an individual character, you can also play your own ship while on space missions! And just as the characters are customizable, so are the ships! This tutorial shows you how to customize your ship to get it just the way you want it.

If you want to spike you hair like Sum 41. You should get some Got 2 B hair gel. First, you need to make sure your hair is dry before you sure you use the gel. Next, put a handful of the gel in your hands and slick the gel through your hair. Make sure you spread the gel around. Move your hands up through the back so it gives it a spike from the back. It does not take much to spike it. Just take your finger tips and pick at your hair into spikes. If you want big individual spikes, take a secti...