Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

I already know what you're thinking: this guide is blasphemy. I am showing you how to turn a Galaxy Note 10 or 10+ into an iPhone 11 Pro Max. And while I'd usually agree with you, hear me out. How can you know you don't like something until you try it? So here is your way of trying out an iPhone using your Galaxy Note 10.

Leaked databases get passed around the internet and no one seems to notice. We've become desensitized to the data breaches that occur on a daily basis because it happens so frequently. Join me as I illustrate why reusing passwords across multiple websites is a truly awful practice — and compromise hundreds of social media accounts in the process.

With the release of the Pixel 2 XL and the iPhone X, smartphones have hit a new high not just in price, but also raw processing power. These new flagships not only cost more than twice as much as an Xbox One or PlayStation 4, they have also become almost as powerful as far as gaming goes. Because of this, a lot of games once reserved for consoles and PCs have made their way to our smartphones.
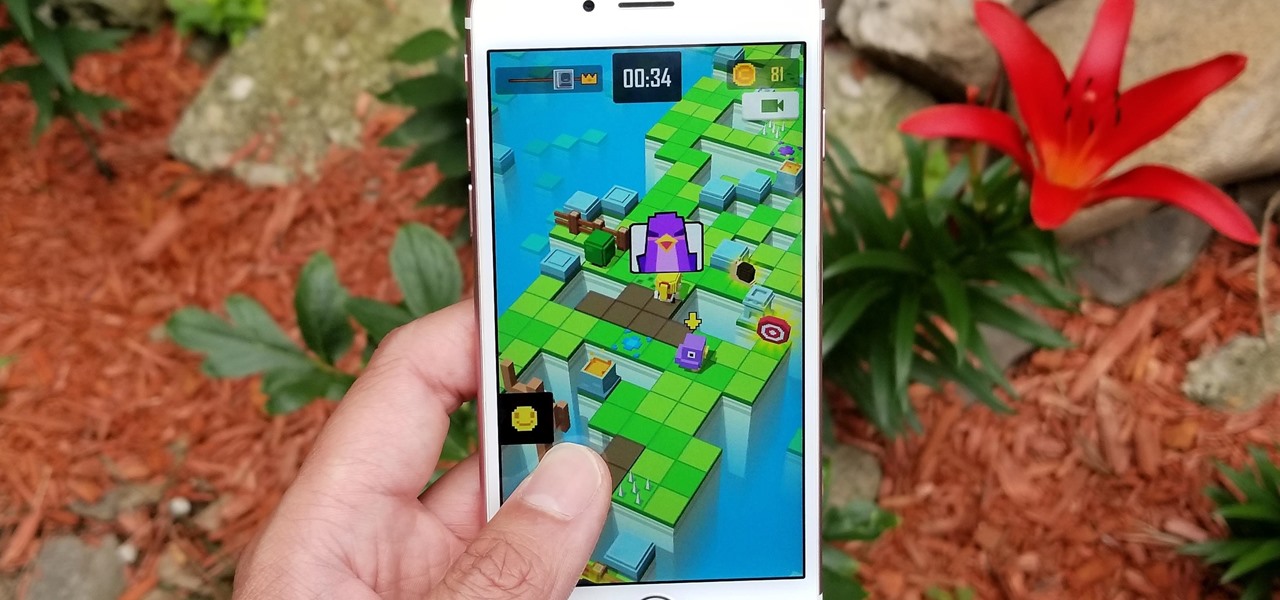
Puzzle games are a great way to kill time and exercise your brain in one fell swoop. They challenge you to think strategically and plan ahead, whether that's to create killer chain combinations for maximum points, or to plain old keep from getting killed.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

People say that money makes the world go 'round. And it's no different in the world of augmented reality.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

Throughout this NR50 series, we have talked about the incredible growth the augmented and mixed reality space has seen in the last year. More devices, software, developers, and use-cases seem to arrive daily. For this growth to have occurred, it took the work of many people, from many different backgrounds and skill sets — and Next Reality wants to recognize them for all that they have done and are doing.

Welcome back, my fledgling hackers! Hacking has a long and storied history in the U.S. and around the world. It did not begin yesterday, or even at the advent of the 21st century, but rather dates back at least 40 years. Of course, once the internet migrated to commercial use in the 1990s, hacking went into hyperdrive.

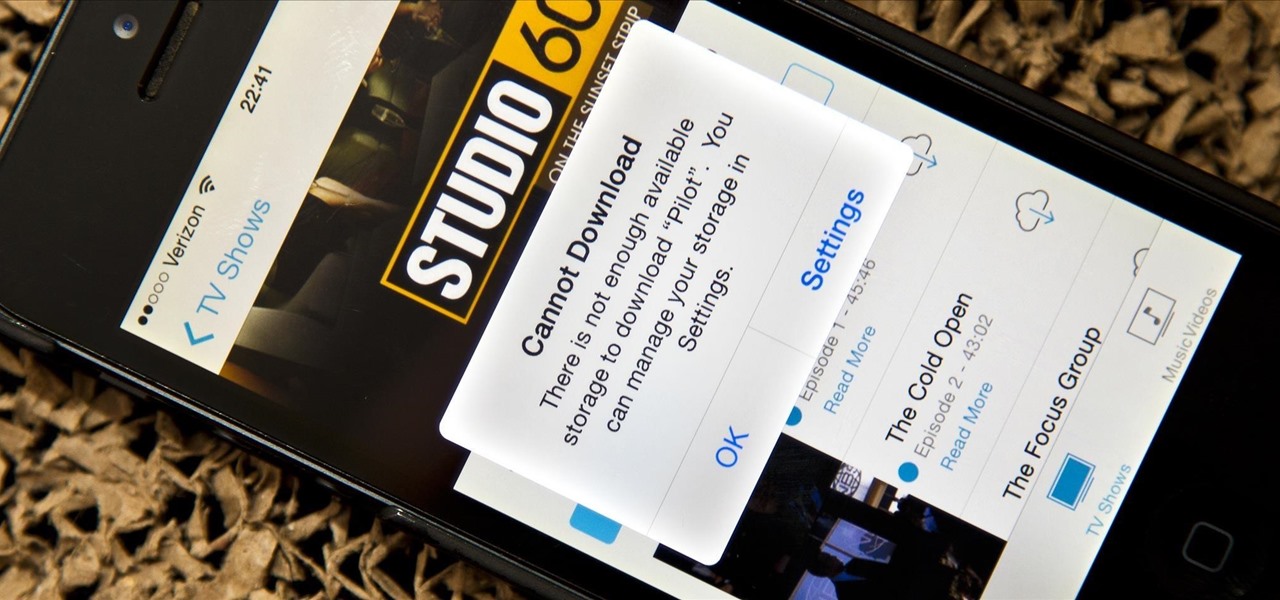
Running out of storage space on your iPhone is annoying, but trying to free some up is downright aggravating. Until they figure out a way to throw a terabyte of flash memory in there, you're going to have to do some spring cleaning every now and then, especially if you're trying to update to iOS 8.

After years of complaining about rising prices, OEMs are finally listening to consumers. It couldn't have come at a better time thanks to potential recession due to COVID-19. As evident with the poor sales of Samsung's Galaxy S20 series, consumers are not looking to spending $1,000+ on a smartphone just for the latest specs.

With a cheap computer, smaller than the Raspberry Pi, an attacker can create a remote hacking device. The device can be attached to a target router without anyone's knowledge and enable the hacker to perform a variety of network-based attacks from anywhere in the world.

While Apple and Samsung have started integrating depth sensors into the iPad Pro and Galaxy smartphones, more advanced AR experiences are arriving for standard smartphone cameras on Android devices.

Hi, everyone! Recently, I've been working on a pretty interesting and foolish project I had in mind, and here I'm bringing to all of you my findings. This guide's main aim is to document the process of building an Android kernel, specifically a CyanogenMod kernel and ROM, and modifying the kernel configuration to add special features, in this case, wireless adapter Alfa AWUS036H support, one of the most famous among Null Byters.

If you're an AirPods owner, you know the sound — that decrescendo of little beeps and boops means imminent "death" for your wireless earbuds. Other than that infamous chime, however, it's not overly clear how to check your AirPods, AirPods Pro, or AirPods Max power levels. That's why we've listed all the ways to do so.

After an update on Sept. 22, 2020, the Checkra1n jailbreaking tool expanded its compatibility to include iOS 12.0 to iOS 12.2, as well as iOS 13.5.1 to iOS 13.7. More importantly, however, it now can jailbreak iOS 14 on select iPhone models, with more support coming soon.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

The iPhone doesn't stop at last year's excellent iPhone 12 lineup. Apple's been developing its iPhone 13 models for a while now, and there are a lot of rumors already with eight or nine months still to go until a release. This year, we're expecting four new models with similar sizes and features to 2020's offerings. If you want to know what makes the 2021 iPhones so different, we've got answers.

Calling all "Star Wars" fans and artists: this quick video will show you the basics of drawing the infamous Death Star from Star Wars. It's just like draw a planet, except more detailed and intricate, but anybody should be able to draw this cartoon version of the Death Star. It doesn't take a professional cartoonist to get it done. See the full step-by-step instructions at DragoArt.

It may a couple of painful tries, but this instructional video can teach you how to perform the infamous, "Jonas Snap." If you are a dedicated fan of the Jonas Brothers, the pain will be worth the effort. Let them know how much you care.

Learn how to model the infamous drive-by shooter, the Mac 10, in MAXON Cinema 4D. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, including complete instructions, watch this 3D modeler's guide.

Antique store owner Jan Braunstein has seen her share of rare records. In this series, she shows you her very own copy of one of the rarest, the infamous “butcher cover” of the Beatles’ “Yesterday and Today” album. She gives you an overview of record collecting in general and talks about some albums by Bob Dylan, Elvis and the Beach Boys which you should snatch up whenever you see them.

Learn how to solve the infamous Rubik's Cube. Yes, that's right, watch this three-part video tutorial to see how you can solve Erno Rubik's Magic Cube, now known as the Classic 3x3 Rubiks Cube. Learn the notation and the algorithms involved.

Darth Vader is the legendary sci-fi character from the Star Wars movies. Everyone has heard of the Star Wars Trilogy, right? The older ones from the 70's? Darth Vader is the primary antagonist from those intergalactic space flicks. DragoArt has this video tutorial on how to draw Darth Vader from "Star Wars". Get more detailed instructions on the step-by-step cartoon drawing here.

Card tricks are among some of the most popular and infamous illusions used by magicians. In this free online video series, learn about card forcing. Our expert illusionist will reveal the secret to this magical technique with tips on how to use force cards and how to perform magic tricks based on forcing.

Vampire Wars is a Facebook game that allows you to erect the best theme park in the world! Get Vampire Wars hacks, cheats, tricks and tips! Watch this video tutorial to learn how to get Pyro's quickly in Vampire Wars (05/24/09).

Have you ever had a problem with a Xbox 360 and the infamous ring of death? Learn how to fix with problem by overheating the system and letting it cool down. This should alleviate the problem and allow you to play games worry free. Fix the 'ring of death' on the Xbox 360 with a towel.

Make this Valentine's Day one to remember! Well... because you forgot. But don't worry, you can still make that heart pitter-patter for your love by saving face and getting some last minute Valentine gift ideas on the cheap. There's no reason to shop at Hallmark or buy expensive jewelery—just use your heartwarming ingenuity to make those cheeks blush.

Martha Stewart demonstrates how to make an exquisite almond apricot wedding cake. This video shows Martha before she was famous and infamous. Make wedding cake.

You're lost. You're cold, thirsty— you're hungry. What if you're not much of a hunter? Maybe you're a gatherer. So, then you'll eat plants. But what if you eat something poisonous? What if you're allergic to it?

Amazing lego version of the now infamous taser scene in the Warner Brothers movie "The Hangover"

From the man that brought you the infamous Iron Baby... The talented self-taught filmmaker and SFX guru Patrick Boivin is back with another beautifully done baby-geek short. This time Boivin shows a typical day in the life of a pet AT-AT.
Call it World Cup fever. Someone or someones decided to make a whole bunch of reenactments of LEGO soccer games, including the infamous US vs England draw. Via MetaFilter.

To many Photoshop beginners the pen tool is a hard-to-grasp mystery. What they do not know is that pen tool offers the most flexible way to manipulate lines and images. This video tutorial will try to demystify the infamous Pen tool. Get started with Photoshop's pen tool.