For some, drinking raw milk is a way to get back to nature, improve family nutrition, and hedge against asthma and allergies. However, according to public health authorities, drinking raw or unpasteurized milk is a big mistake—even fatal. So what's the story?

Bacteriotherapy sounds a lot more amenable of a term than "fecal transplant," yet they're both treatments that use bacteria itself to cure or treat infections. Fecal transplants, specifically, are an up-and-coming treatment option for a potentially deadly and difficult-to-treat diarrheal infection called Clostridium difficile.

Even when no one is in your kitchen, it is crowded. The refrigerator, sink, and counters are all covered with microbes that are just hanging around. They are inadvertent remnants from the raw chicken you used in that recipe last night, brewing a bacterial cocktail in your Nespresso machine, or just growing their merry little colonies on your leftovers.

With all of the bare-bones setup out of the way in our Mac for Hackers series, your Apple machine should be ready to run a significant amount of pentesting tools. We can pull tools from GitHub and compile them, we can pull dependencies or tools from Homebrew, we have both Python and Ruby. Everything is ready to go and now it's time to start building a toolbox on our local host.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

Getting files from an Android device to a Mac or iOS device is not always easy or convenient, and the same goes for transferring content from a Mac or iOS device to an Android device. But we're here to tell you there is a better way than using USB cables, email, and cloud storage, and it gives you the look and feel of AirDrop.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Because of the way Google Play works, Android has a "bad app" problem. Google allows any developer to upload an app to the Play Store, regardless of if it works, how it looks, or whether or not it can harm users. Malware scanning happens primarily after apps are uploaded, and though Google has recently taken steps to safeguard users with its Play Protect program, you don't have to depend on them.

There are more than 2 billion Android devices active each month, any of which can be hacked with the use of a remote administration tool, more commonly known as a RAT. AhMyth, one of these powerful tools, can help outsiders monitor a device's location, see SMS messages, take camera snapshots, and even record with the microphone without the user knowing.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

Minor mishaps occur all the time in the kitchen, whether you cut your finger while dicing an onion, scorched your hand in a grease fire, or burned the roof of your mouth because you were to eager to taste-test your killer pasta sauce.

Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

If you're marginally inclined towards computers, you've probably been approached at some point by a family member who wants you to "fix" their system during a visit home. With the holidays coming up, these opportunities (or ambushes) are even more likely.

One of the biggest problems in data security is authentication of data and its source. How can Alice be certain that the executable in her inbox is from the venerable Bob, and not from the not-so-venerable Oscar? Clearly Alice wants to know because if this file is actually sent to her by Oscar, the file might not be a game, but a trojan that can do anything on her computer such as sift through her email and passwords, upload her honeymoon pictures, or even turn on microphones and webcams. Thi...

Coinhive, a JavaScript cryptocurrency miner, was reportedly discovered on the BlackBerry Mobile website. It was placed there by hackers who exploited a vulnerability in the site's e-commerce software that allowed them to anonymously mine cryptocurrency every time the website was viewed. There's no doubt Coinhive, an innovative mining method, is being abused and exploited by hackers in the wild.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

Despite legends to the contrary, it appears that the saliva of a Komodo dragon is not teeming with pathogenic bacteria that kills their prey. Its reputation to survive while colonized with lots of horrible disease-causing bacteria, true or untrue, has made it the subject of research in pursuit of natural antimicrobial agents and led scientists to some remarkable findings.

Even though most phones don't have Oreo yet, Google has released Android 9.0 Pie. It's available on Google's own Pixel devices, and updates should soon be available to partnered devices from Essential, Nokia, Oppo, Sony, Vivo, and Xiaomi. We're already digging into it to highlight all of the features and changes.

This is a really serious video. This video tell us about how to get rid of virus/spyware. It is based on JNBJABNK's own experience. She describe some step to destroy the virus which affected the computer. First of all make sure to confirm your system have spyware. Then open my computer folder and trace as quick as possible the infected file. Then run a full virus scan on that file. Delete the virus using the spy ware you have in your computer. On completing that you should restart your comput...

If you’re a dancer, athlete or just breaking in a new pair of shoes you know that blister can add pain and discomfort long after they’re formed. By keeping a blister sterile and away from further friction you can get your blister to heal quickly.

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

The executable file association virus deletes the "Regkey" that associates ".exe" files with the proper Windows execution. The virus can be contracted while browsing the web, from an infected file, or even from pictures and documents. Once the damage is done, Windows will show a window similar to the one below, and will ask you for the correct program with which to open the file.

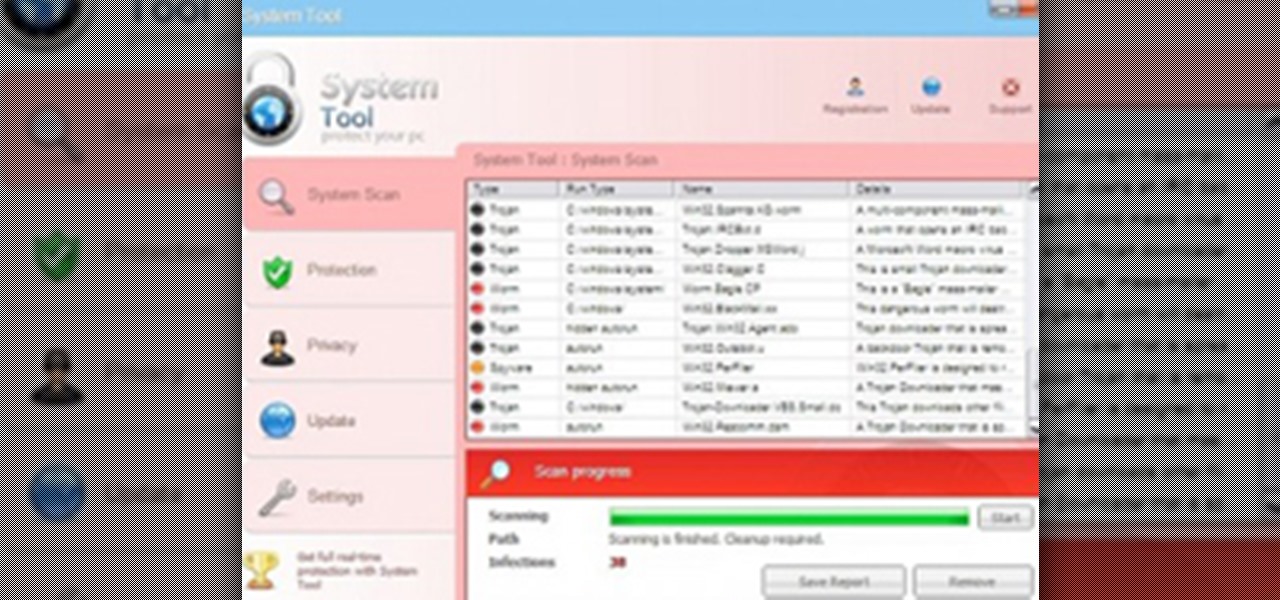
System Tool. It sounds like something your Windows computer might need, but it's the exact opposite.

This is an intermediate guide on how to easily fix or retrieve data from a bad hard drive. What we're trying to do:

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

WikiLeaks. In recent weeks, it's been the hottest topic on the web. It's been attacked on a multinational level by political influence peddling.

Health, safety and security are three main issues which determine if your cruise is a successful vacation.

Antivirus programs usually aim to prevent malicious software from crashing your system, not ARE malicious software that crashes your system. Except, that was the case with AVG Anti-Virus yesterday when they released a software update that rendered 64-Bit Windows 7 systems useless. It affected both free and paid AVG owners.

Plantar warts are non-cancerous growths that can be found on the heel or ball of the foot, and in some cases, even on your fingers. They most often are very painful and are hard to get rid of. Most removing methods can be very painful and uncomfortable.

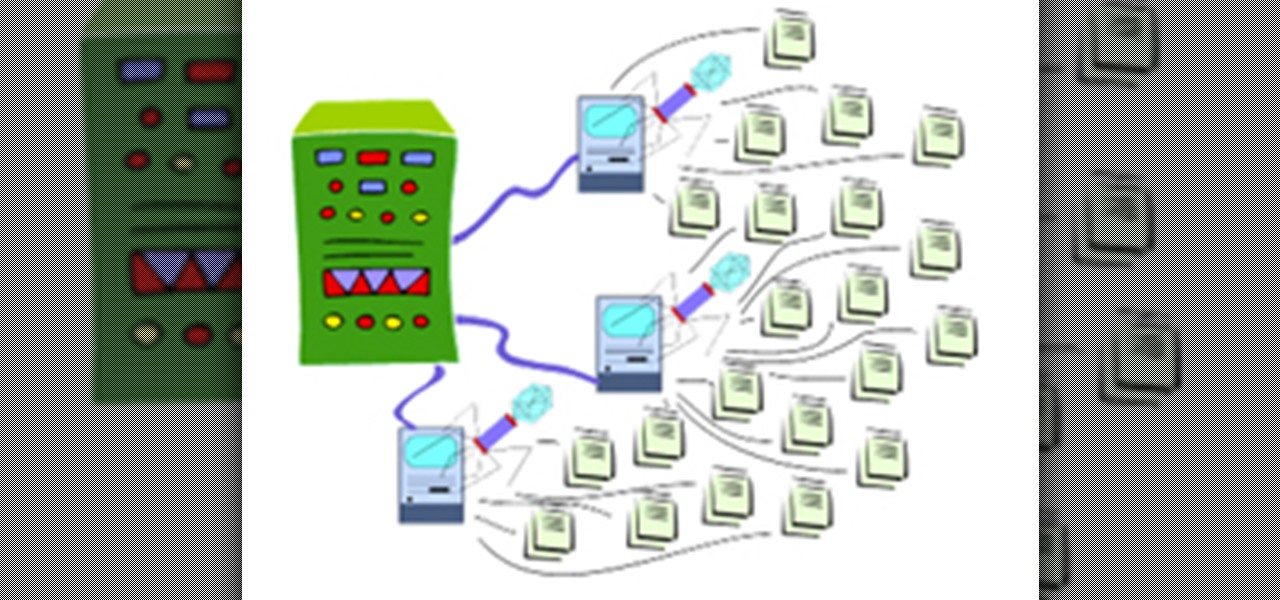
Watch out Macs. Flashback is back. Variations of the trojan have reportedly infected 600,000 Mac computers around the globe, with about 57 percent in the U.S. and another 20 percent in Canada.

Are your sinus problems getting in the way of your life? Dr. Oz of Real Age Videos provides an informative, animated video that unravels the mysteries of infected sinuses. He explains the physiology of the sinuses, and details the possible causes of sinusitis and its common symptoms, including colds and allergies. This video offers a few suggestions about current methods of medical treatments to alleviate this troublesome malady. It explains how the Balloon Sinuplasty procedure can provide ef...

In terms of internet, faster = better. We all want faster internet, but how exactly do you get a fast wireless connection? Believe it or not, the answer is quite simple.

As a follow-up to an earlier post on surviving deadly animal attacks in the wild and another one on relieving a jellyfish sting, listed below are things you should do (and shouldn't do) if you are ever bitten or stung by potentially poisonous wild animals.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

The immune system is not as simple as you might think. Simply, it's formed of two main groups of cells:

Diseased Pariah News is a zine for and about people with HIV. It is "a patently offensive publication of, by, and for people with HIV disease (and their friends and loved ones). We are a forum for infected people to share their thoughts, feelings, art, writing and brownie recipes in an atmosphere free of teddy bears, magic rocks, and seronegative guilt." Started in the 1990s, it's up to 11 issues, 8 of which are viewable and downloadable online. It's marked by its trademark dark humor and hon...

This is a two-part series to locking down the computer to provide maximum protection. Even though this guide will sound intrusive, we are talking about reality here. Extreme measures must be taken to protect our computers, especially when we have confidential documentation or do internet banking, which many people do. We all have to use electronic devices at some stage, whether it be for business or personal use.

Spam is everywhere and Facebook is no exception. In fact, spammers are constantly stepping up their game by tricking unsuspecting Facebook users to participate in quizzes, games, apps, or "new features" that are actually dangerous computer viruses, spyware, or other trojan horses in disguise. Their attempts even trick people into unknowingly becoming spammers themselves.