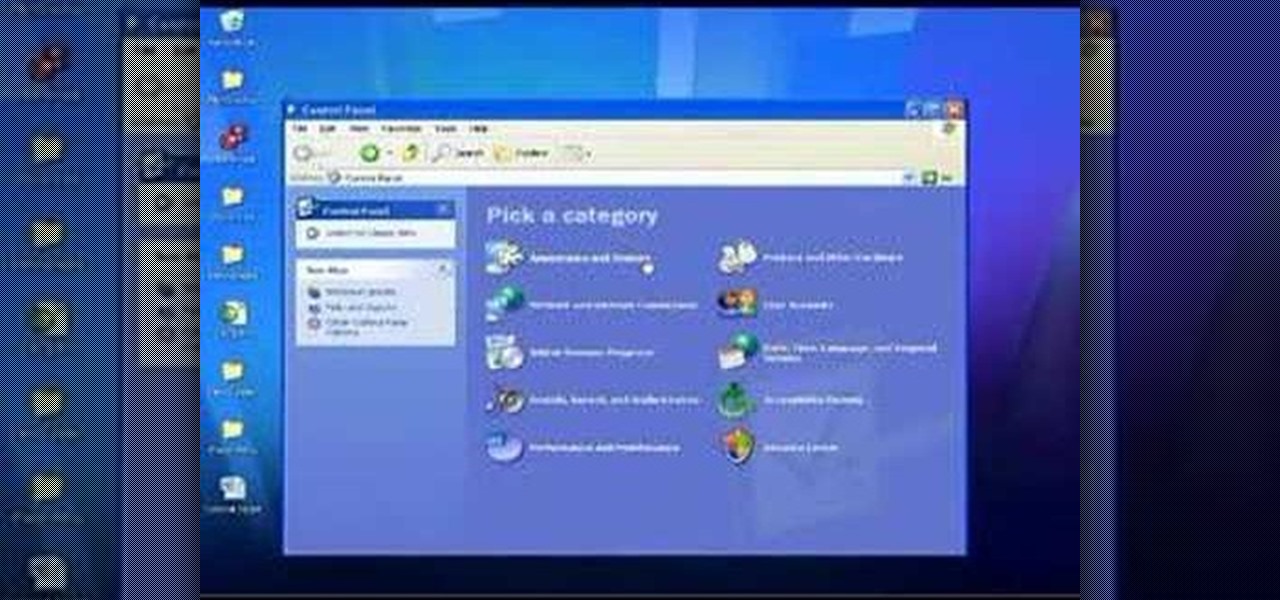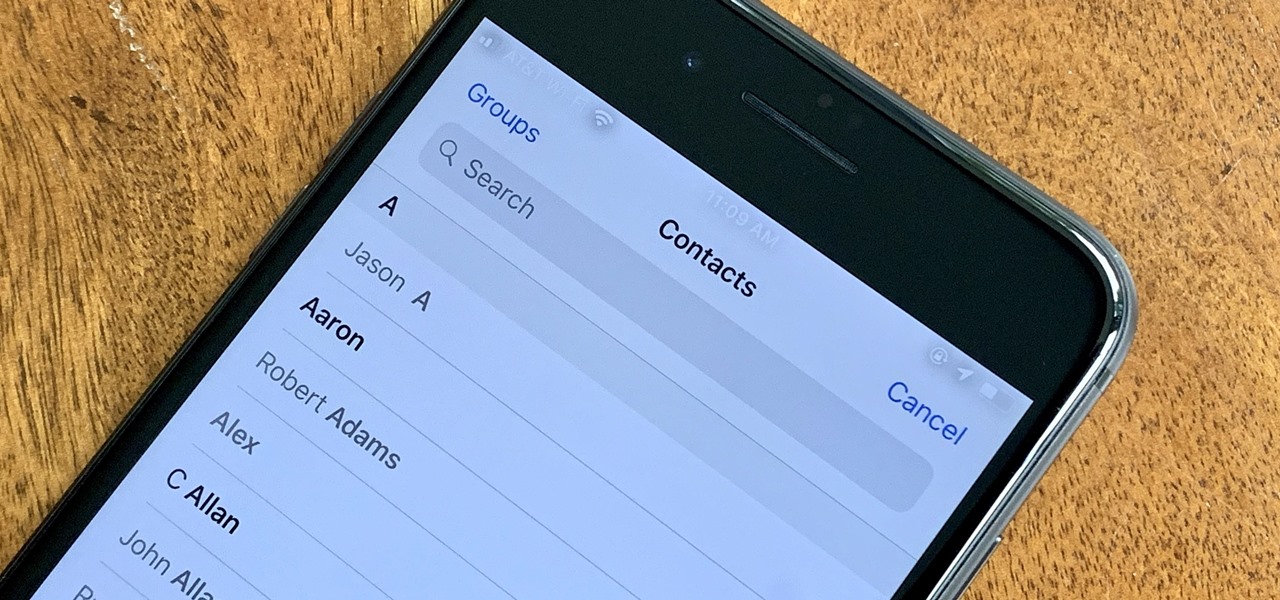
Check out this informative video tutorial from Apple on how to use the basics of the Mac OS X Finder. Learn about the Finder basics, the Sidebar, view buttons, and Quick Look. Mac OS X. It's what makes a Mac a Mac.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

If you'd like to have access to all your files at home without the hassle of spending money on expensive file hosting services or installing foreign software on your computer that could potentially harm it? Well Google has the answer for you, taking over the world one more computer at a time! In this video you will learn how to use your Gmail account and a Gmail Drive shell Extension to gain access to your files from any computer regardless of location!

In this tutorial, we learn how to open & utilize the trunk area of a 2010 Prius. To access the cargo area, open the rear hatch by pressing on the release above the license plate. To keep items out of sight, there is a sliding cover that you can pull back and hook into slots. To open, pull towards you slightly, then reel it in. There is additional space under the floor which can be accessed by twisting the locks and removing from the vehicle. Underneath this, there is a cargo bin, and undernea...

Google is the biggest and best search engine on Earth, and if you are a webmaster and want your website to be a big success it would really behoove you to know as much about how it works as possible. The Google Webmasters series of videos and website were created to teach webmasters, SEO professionals, and others how Google works by answering their questions and giving them insights into how they can best integrate and utilize Google's functionality to improve their business. This video will ...

Vince shows viewers hot to access the Chuck Norris trick on Google. First, you need to open your web browser and go to Google. In the Google search bar type in 'Find Chuck Norris' and click 'I'm feeling lucky'. Make sure you do not click enter but the 'I'm feeling lucky' button to the right. You will get a funny message that says 'Google will not search for Chuck Norris because it knows you don't find Chuck Norris, he finds you'! The suggestions should read 'Run before he finds you' and 'Try ...

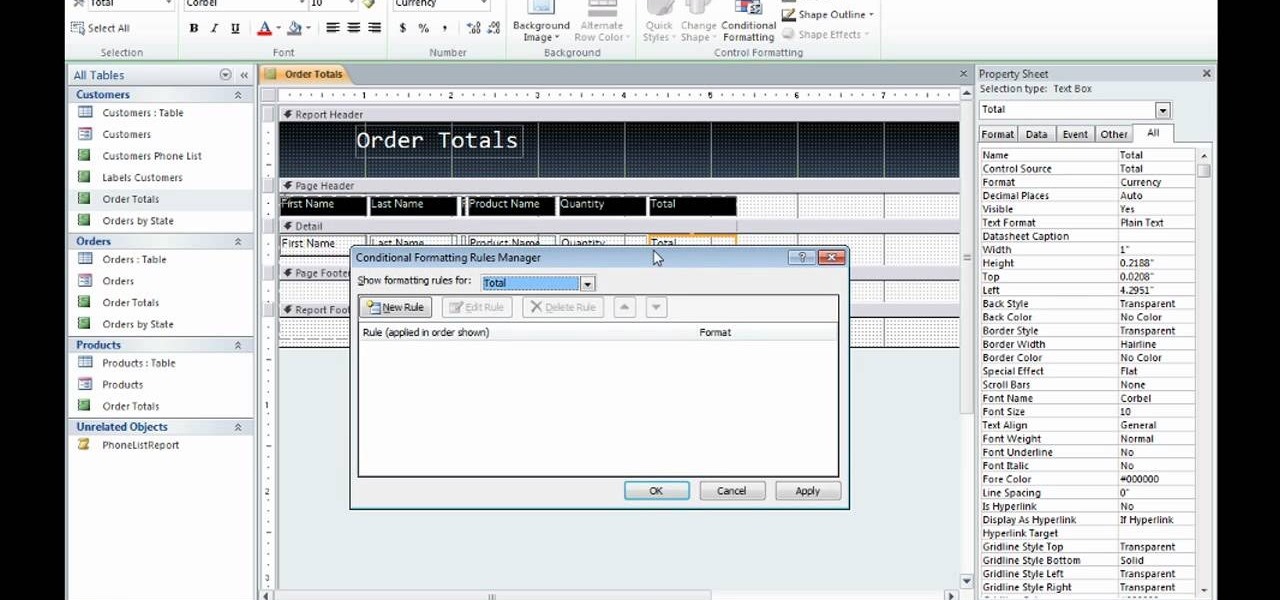
lyndapodcast teaches you how to apply conditional formatting withing Microsoft Access 2010. You click View - Design View. Click the Total tab and you'll notice some highlighted options above. Click Format and then Conditional Formatting. This where you will create rules. Click the new rule button. Now you will see the conditions with drop-down menus. Type in the numbers you want and then select the formatting you want when the rule is true. The preview below will show you how the numbers will...

This video instructs the viewer about the basics of cloud computing, using more than one computer and managing your computing needs online. The instructor explains, "Cloud computing is a metaphor for using the Internet for your computing needs." A program called cloudo, allows the user to store information online through an interface that looks like a regular computer desktop; then the information can be accessed via password from any computer with an internet connection. Other programs also ...

In this video tutorial, Chris Pels will show several aspects of defining and using master pages in an ASP.NET web site. First, see how to create master pages declaratively using the ASP.NET master page model and learn what information is best suited to a master page compared to an individual content page. Next, see how to programmatically assign master pages on-the-fly in an individual content page. Also learn how to create a base page class which assigns a master page programmatically for al...

Once you have access to the Detroit City Hub in Deus Ex: Human Revolution, it's possible to unlock a secret achievement dubbed 'Balls' on the Xbox 360 version of the game. This Giant Bomb walkthrough will help you locate the basketball hoop you'll need to earn the achievement with, and give you a little tip on how to easily get the ball through the hoop.

Clip Art from Microsoft Office allows you to insert stock photos into you PowerPoint, Word, Excel and Entourage documents easily. You can gain access to the Office Clip Art site easily in any of the mentioned applications. The Microsoft Office for Mac team shows you just how to download and use clipart from Office Online in this how-to video. You can get free stock images of low-priced professional quality photos.

In this tutorial, we learn how to make a popular sashimi salad with Kitchen Access. First, you will grab the salmon and slice it into strips, the thinner the better. Now, grab yellow tail and cut it into thin slices as well. Next, grab the tuna and cut it into thin strips too. From here, you will set these on the serving dish and put fresh lettuce into a mixing bowl. Then, add in pomegranate seeds, lemon, sea salt, and lemon oil. Toss this and then place on the serving dish. serve this to you...

In this video tutorial, viewers learn how to zoom in and out on a Mac computer. To access the zooming tool, begin by clicking on the Apple menu and select System Preferences. Under System, select Universal Access and check On under Zoom. In Options, users are able to set specific settings such as the maximum and minimum range of zoom. The keyboard shortcut for zooming in is: Option, Command and =. The keyboard shortcut for zooming out is: Option, Command and -. This video will benefit those v...

In this video tutorial, viewers learn how to use the Sticky Keys feature in Microsoft Windows 7. To use the Sticky Keys, click on the Start menu and open Control Panel. In the Control Panel window, double-click on Ease of Access and click on Change how your keyboard works under the Ease of Access Center. Then click on Set up Stick Keys and check the option Turn on Sticky Keys. This video will benefit those viewers who have limited dexterity and find it difficult to use complex keyboard shortc...

Learn how to adjust the mouse cursor size on a Macintosh computer, so that it is easier to see and locate. The cursor can be adjusted to your liking by accessing the "Universal Access" preferences window and then by selecting the "Mouse & Trackpad" option. Near the bottom of the control panel, you will be able to find a slidable bar that can adjust the cursor size to be smaller or larger, as needed. This option can help make the mouse cursor easier to see against a difficult desktop backgroun...

In this video tutorial, viewers learn how to use the Filter Key features on a Windows 7 computer. Begin by opening Control Panel and select Ease of Access. Under the Ease of Access Center, click on Change how your keyboard works and click on Set up Filter Keys, at the bottom of the window. Now check the box beside Turn on Filter Keys. Users are provided with several options for he Filter Keys such as: turn off the Filter key wen Shift is held or 8 seconds, display a warning message when turni...

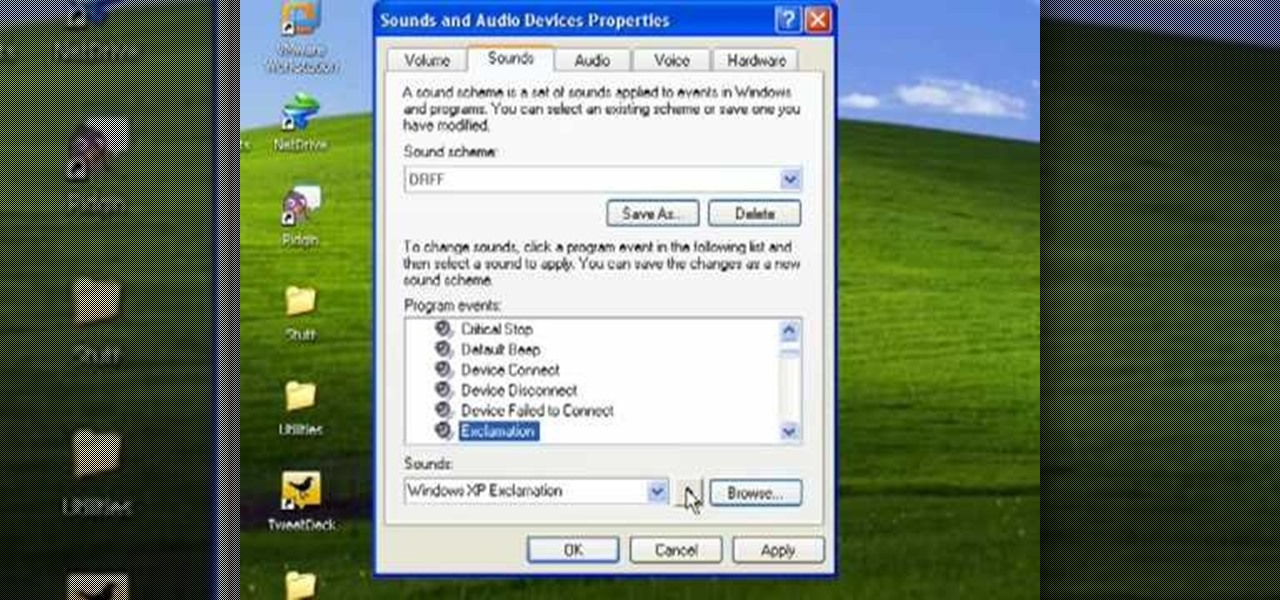
Butterscotch is here to help you create a sound profile in Windows. First, go to "start", then click "settings", and then "control panel". When the "control panel" menu comes up go to and double click on "Sounds and Audio devices". Once you have that window up, click on the "sounds" tab. After doing so you'll see a menu called "program events" which is all the sounds that Windows uses. You can highlight one of the titles and click the play button on the bottom to preview the sound. But in thi...

In this Computers & Programming video tutorial you will learn how to use the Remote Desktop feature within Windows XP. This application will enable you to access your home computer from office using the internet. This application is really very easy and simple to use. You have to ensure 3 things for this to work. Ensure that the computer on which your files reside that you want to access has all the components of XP installed. This is the host. The computer that you want to use to access the ...

Stuck with the gadgets in Windows 7? Need a little bit of help from an expert? Then this video is for you! In this video you will learn how to add, remove, and edit different gadgets. Did you know you can drag a gadget to your desktop for easier access? This short video will have you using gadgets like a pro in less than a minute and a half! There is also a gadget bar included in Windows 7 for an organized easy way to access your gadgets. If you feel the gadgets you have are not good enough f...

This video tutorial gives you a way to access websites that you can not normally access because of a web block or filter. What you need to do is click on the ‘Start’ button and then click on ‘Run’. In the small window, type in ‘cmd.exe’; this then opens a black window. Then type in ‘ping’ and the website; this gives you an address that you type in directly to your web browser, granting you access to a normally blocked website. This comes in very handy when you are in such locations like schoo...

This video shows you how to easily access the hidden Motorola Droid menu and how to improve call quality. The first thing you have to do is dial and call: ##7764726 . Then, type in the SPC Password, which usually is 000000 (six 0s) and hit OK. Next, click 04.Vocode in the popped up menu and choose either EVRC or EVRC-B for the highest call quality. Tap apply. Please note that better call quality requires more battery, so the battery will go down easier. That's it! Good Luck!

Can't wait until you get home to get onto MySpace? This video gives step by step instructions on how to try and unblock MySpace while you are at school or on a server that does not allow access to the site. This video does not have narration, but has written instructions on how to get around blocked sites with out using a proxy server. However, you have to have access to the system 32 files for this tutorial to work, and accessing these files does go against a lot of network policies.

Want quick access to your voicemail using your BlackBerry device? Instant voicemail access is available on the BlackBerry device. But how? Best Buy has answers. The Best Buy Mobile team explains how to quickly dial your voicemail on a BlackBerry by using the shortcut of holding down the "1" key.

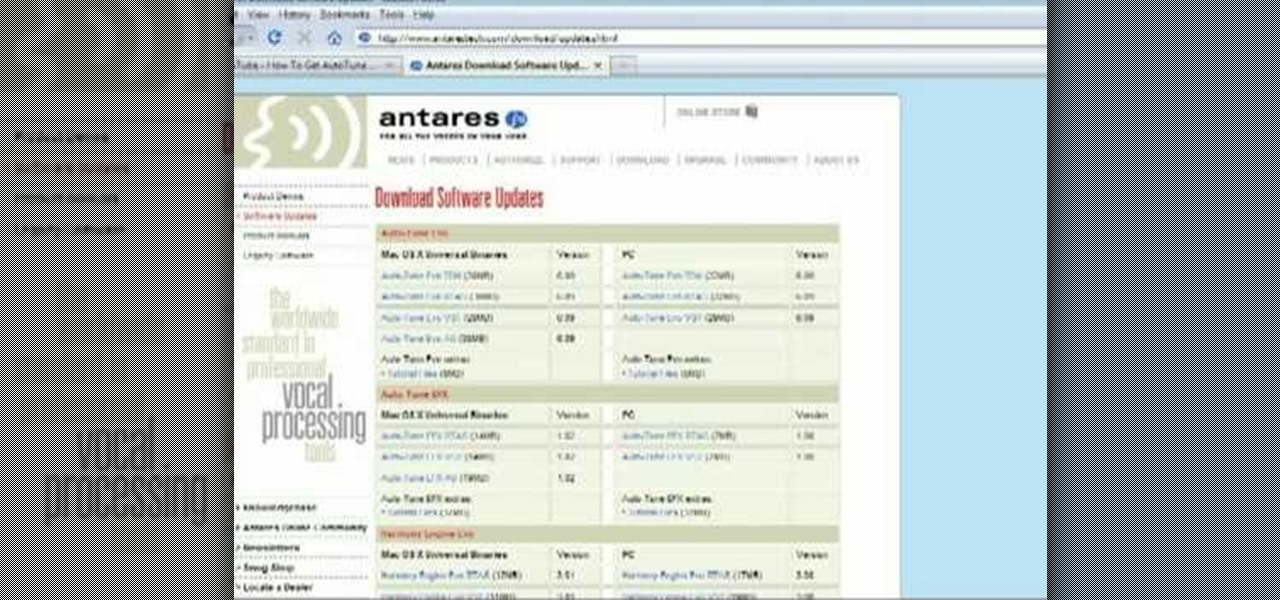
Access auto tune for your Audacity recording software with help from this video tutorial. Step-by-step instructions are gone over, and the following links will be needed:

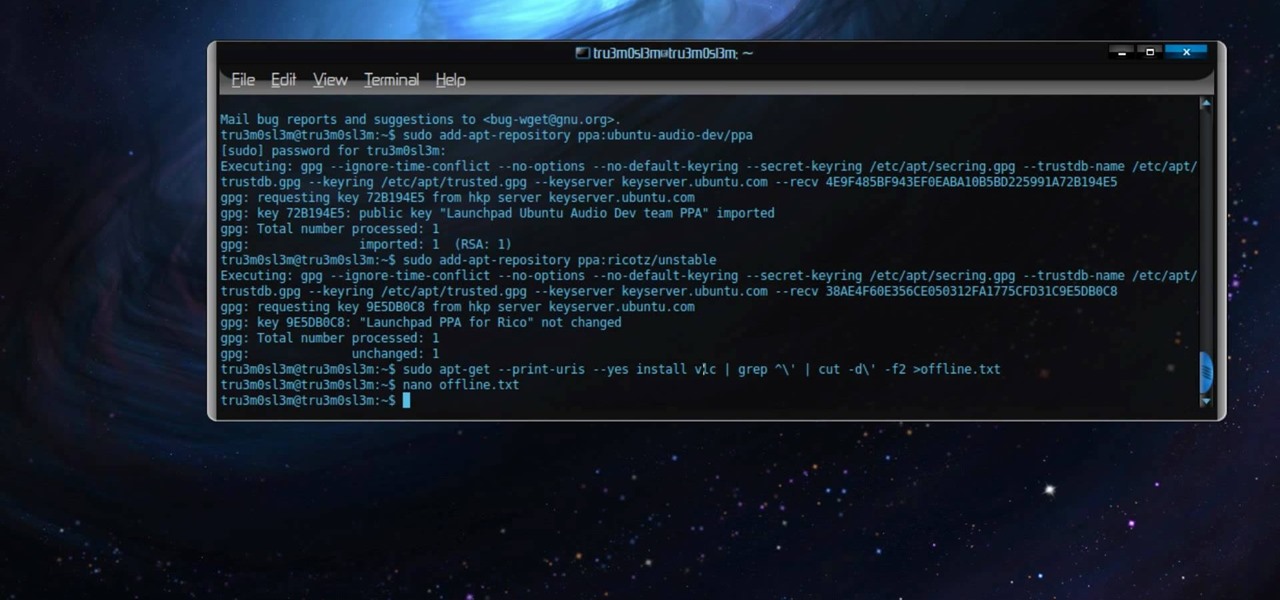
Permanent access to the internet might not always be possible for you and your Linux system, and this computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to offline package install and update on Ubuntu Linux.

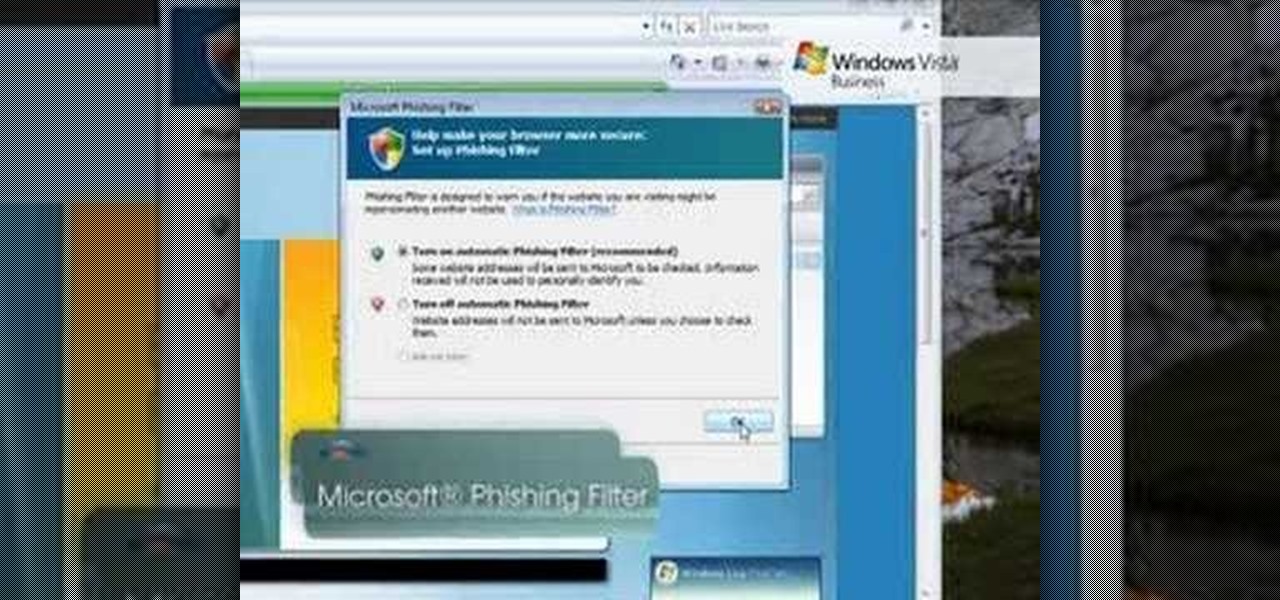
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

Starting with Android 9 and 10, Google made privacy and security the main priorities for Android updates. Both versions brought numerous changes to help erase the notion that Android isn't safe, but Android 11 might even have them beat.

It wasn't too long ago that the power menu for stock Android didn't offer much beyond turning the device off, but Google has steadily added more functions, like capturing screenshots and provisioning access to emergency information.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

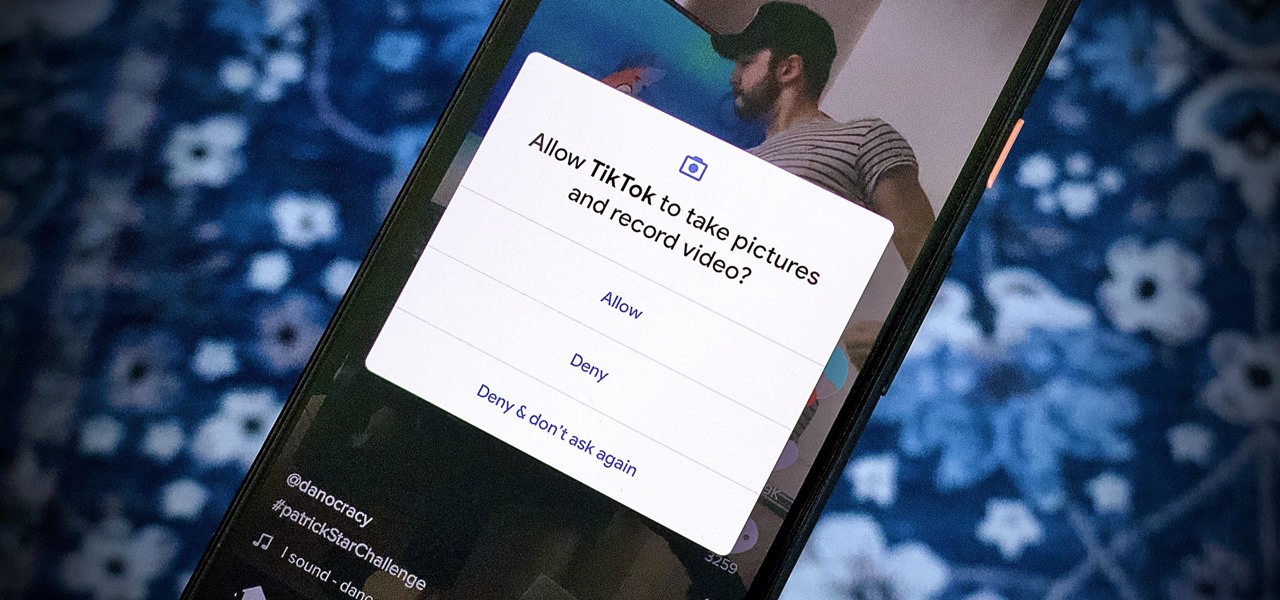
We're thinking more and more about our digital privacy these days. When we first started using smartphones, we'd download apps with reckless abandon, allowing permissions lists as long as novels in order to play free games. Now, we know that apps have access to things like our cameras and microphones, even when they shouldn't. Luckily, taking away these permissions is easy.

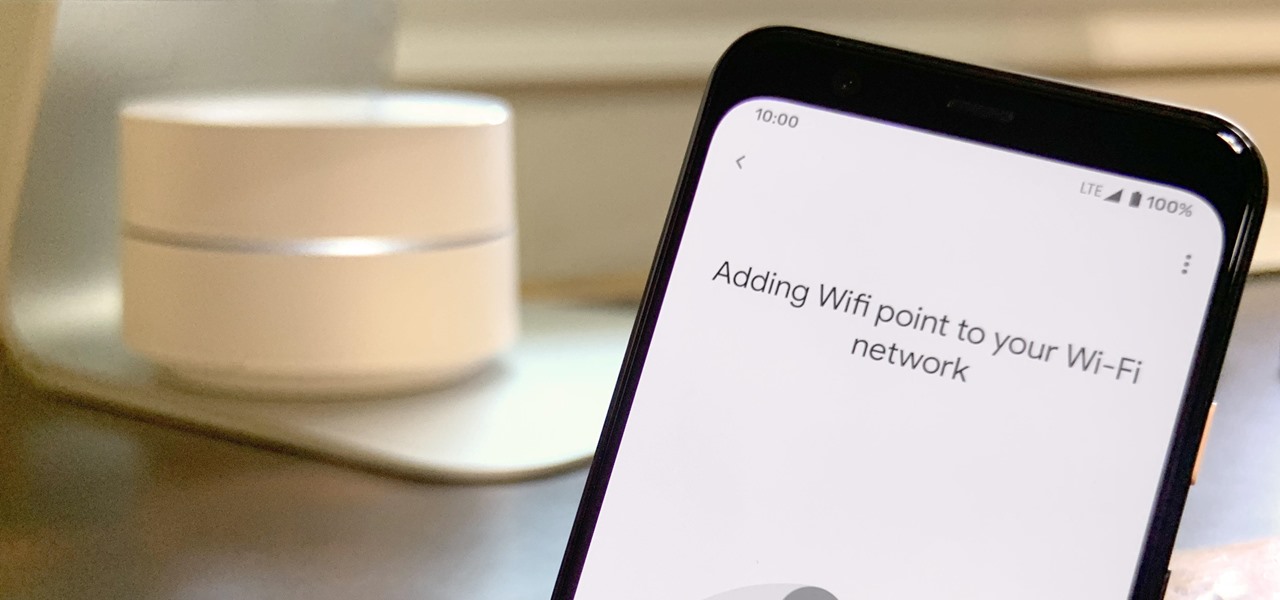
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

The camera system on the iPhone has never been better. Apple's iPhone 11, 11 Pro, and 11 Pro Max sport some of the best shooters on the market. But no level of quality makes up for the fact that shady apps can access your cameras for nefarious reasons. You can take control of the situation, however, and block any app you want from using your rear and front-facing cameras.

Whether we like it or not, our personal information and smartphones are tied together at the hip. The former needs the latter to deliver a personalized experience that matches our individual needs. This personal data, however, makes your phone a prime target for thieves of all sorts to turn your privacy into illicit profit.

Shopping wasn't always this easy. Now, in a matter of minutes, you can order your groceries for the week, send your cracked phone in for repairs, get your holiday shopping done, and have everything delivered to your front door in just a few days — without ever having to leave your home. Online shopping is convenient, comfortable, and a blessing ... right? Well, it can also be a headache.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

While iOS 12 is arguably the best iteration of Apple's mobile operating system yet, one major fault so far is security. On Sept. 26, Videosdebarraquito discovered a passcode bypass that gave access to contacts and photos from the lock screen. Apple has since patched that security flaw, but Videosdebarraquito has discovered a new one that affects all iPhones running iOS 12.1 and 12.1.1 beta.

In iOS, the Control Center is an easy way to toggle settings such as Wi-Fi, Do Not Disturb, and Low Power Mode. Its Android counterpart is called "Quick Settings," which provides much of the same functionality with a few bonuses. If you're curious about how this toggle menu works or miss having it before you made the switch from Android, you can test it out on your iPhone right now.

When BlackBerry made the move to Android OS, they were aware of the limitations it presented. Unlike with BB10, they didn't create the operating system and would have to deal with the vulnerabilities already included. As a result, they added numerous security enhancements, and at the heart of this is DTEK.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.