In this video we learn how to disassemble a T-Mobile G1 HTC phone for repair. First you want to make sure to wear an ESD wrist strap and make sure it's secure around your wrist. Then remove the battery from the device. Next unfasten the screws from the back of the housing on the G1. Then separate the housing from the device and then the speaker from the housing. Next unplug the UMTS cable and the GPS coaxial cable. Then remove the UMTS board and GPS boards from the device. Then disconnect the...

This video demonstrates how you can tell if someone is lying using visual accessing cues. This is a sample video of Kelley Moore teaching for a breakthrough collaborative application. She uses basic psychology terms to aid in understanding when someone lies. A sample visual cue for lying is to notice the eyes. If someone is lying, their eyes would twitch or unconsciously shift to the left side. If you follow the steps in this video, you'll be able to notice when someone is lying to you.
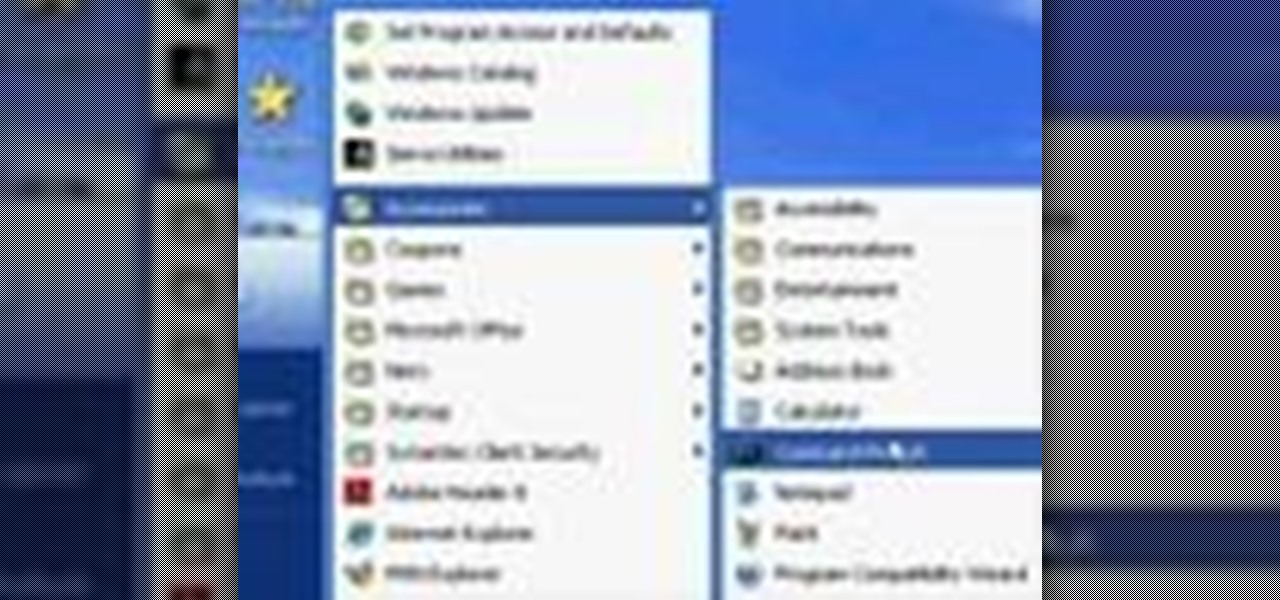
You want to use the websites you want to use, regardless of any school blocks or other hindrances, so how? This video tells us by using the IP addresses of your favorite sites. To find this IP address, at your home, or an other unblocked location, in your start menu, you must access Programs, then Accessories, then Command Prompt. When the window pops up, then type in "Ping http://www.myspace.com" without the quotations, for instance. Write down, then, the string of numbers that appears, whic...
This video is about creating a group on Facebook. Groups on Facebook join friends and people with similar interests. Go to the dialog box and choose groups, create new. You then bring up the form. Choose a name and describe the name. Scroll down and choose the group type. Click create group. You can also add a photo of the group. Scroll down and choose enable photo, video or links. Then you decide who has the responsibility for making changes to the group-members or an administrator. Decide w...

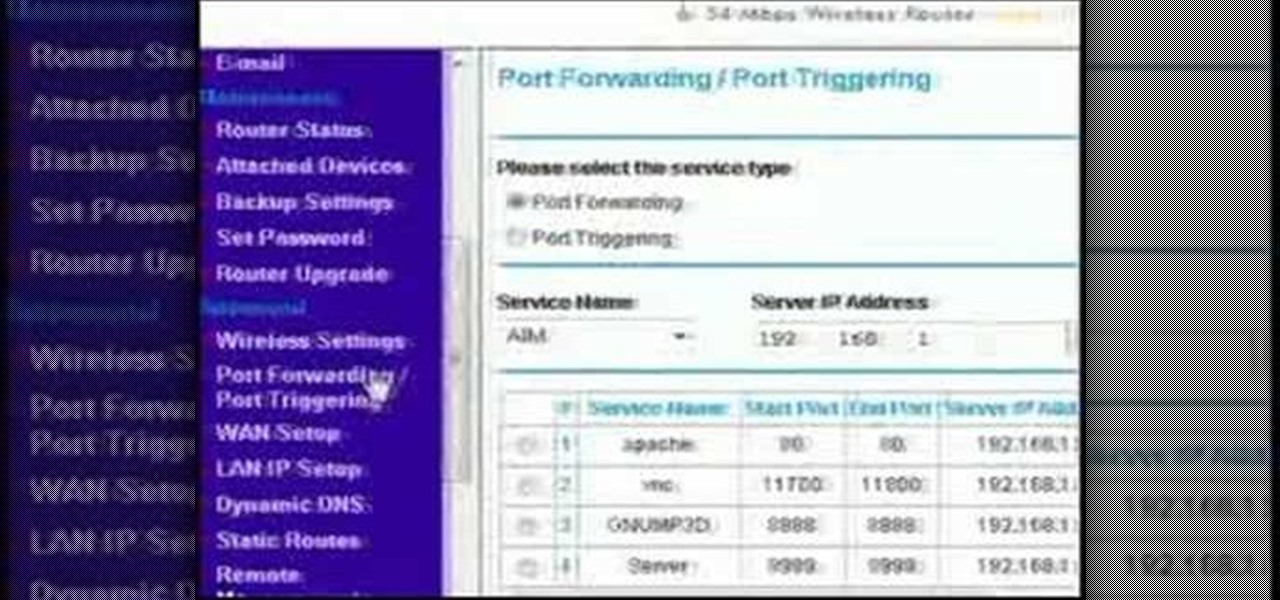
This simple video tutorial explains how to use Airport Utility to configure your Airport Extreme so you can access your Apple computer remotely for file and screen sharing. It explains how to setup DHCP IP reservations and port forwarding using Manual Setup option of the Airport Utility. Considering that the tutorial becomes a little bit technical during the second part, this tutorial is aimed at users who already have at least some knowledge and/or experience setting up a network. Absolute b...

Don’t you just hate it when you try to go on a website while you’re at work—and find out your boss has blocked it? Here’s how to thwart The Man. With these tips, you'll be able to check your facebook or myspace at work (or whatever sites your employer may be blocked). All you need is access to google. Did you know? According to one survey, 78% of employers block employee access to pornography, 47% block gambling sites, 20% block shopping and auction sites, and 4% block news sites.

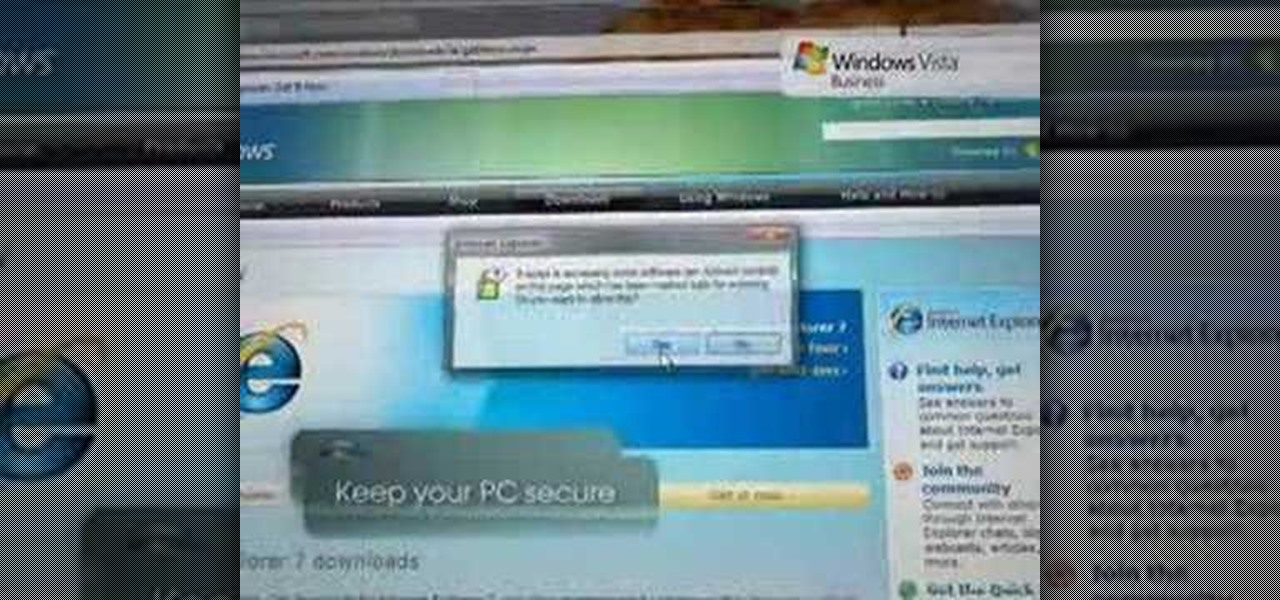
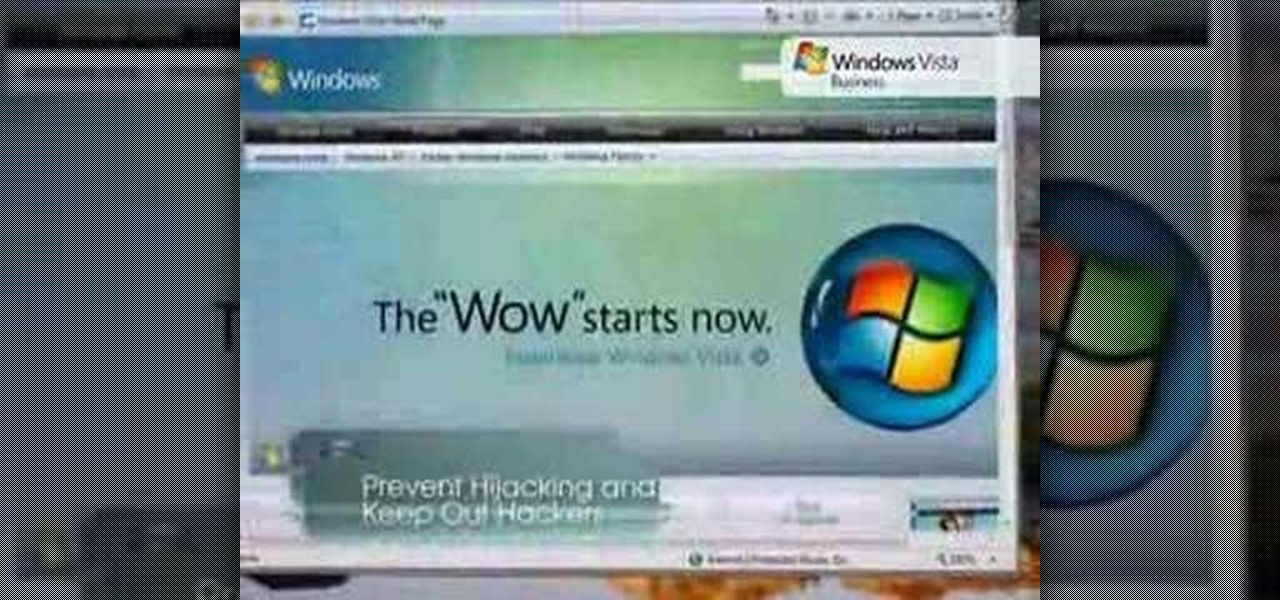
Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

Web browsers such as Windows Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Microsoft Internet Explorer 7 has several new features that make using the web easier and safer than ev...

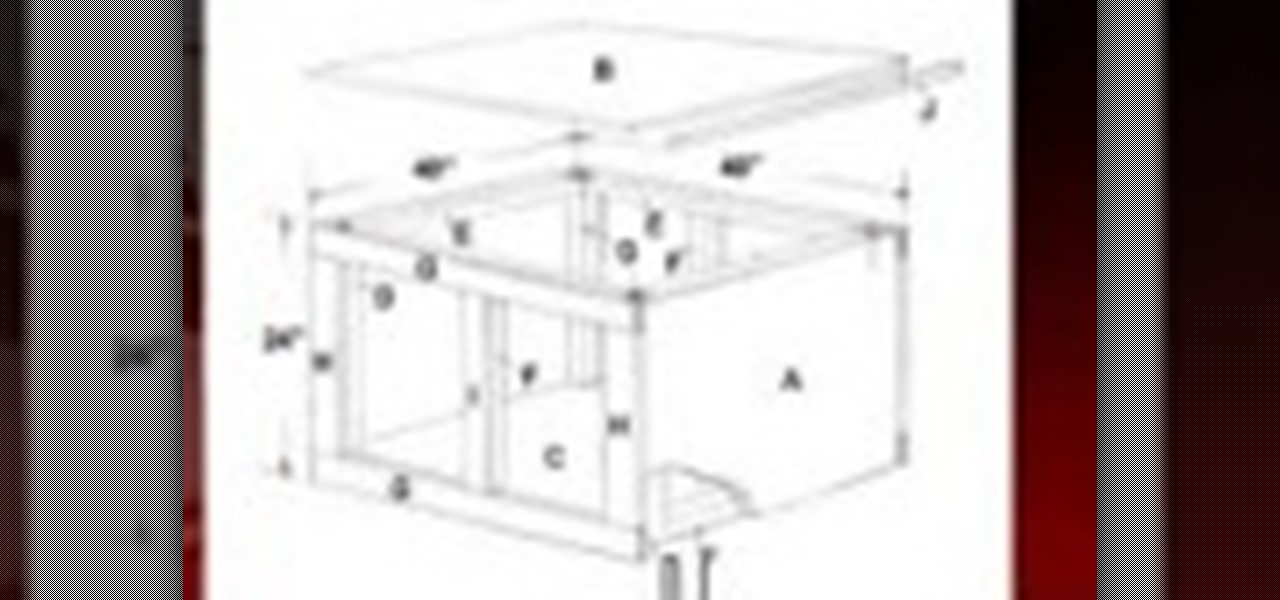
So many bench-top style tools are available today it's easy to accumulate several, including table saws, jointers, sanders, scroll saws, planers and others. With either purchased or shop-made individual stands, the tools can take up a lot of room. In this video tutorial, you'll learn to build a roll-around tool cabinet that can easily be rolled out for access to a variety of tools placed on top. It features a large bench top with locking rollers, and a huge storage cabinet beneath, which prov...

In this video tutorial, Chris Pels will show how to determine what capabilities a user’s browser has when viewing pages in an ASP.NET web site. First, learn how to access an instance of the HttpBrowserCapabilities object from the ASP.NET Request object associated with the web page request. Next, see the different information available in the HttpBrowserCapabilities object such as the type of browser and whether the user’s browser supports JavaScript and Cookies. Then see an example of how to ...

Systm is the Do It Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. We will help you avoid pitfalls and get your project up and running fast.

In this ten-step video tutorial, you'll learn how to quickly copy keys using a camera, printer and Dremel tool. With this ten-step process you'll learn the necessary steps to copy almost any key... even if you only have access to it for a brief period of time.

This is a great solution if you need to get something off your computer, but you are not home. Want access to your files stored at home? How about hosting a home web server? Static IPs are expensive, if you can even get one. We set up Dynamic DNS instead!

This video discusses how to bypass your router to access your server. In the search window type in CMD to open up a command prompt. Then type in ipconfig to bring up the ip configuration. You want to look for the ip address for the default gateway and the one for your computer. They should both start with 192.168. Once you find them open up internet explorer and type in the ip address for your default gateway and it should then prompt you for a user name and password. Log in and look for a po...

This video teaches how to change Windows 7 accessibility options. Choose Start, Control panel. This opens the Control Panel window. Choose Ease of Access in the control panel window. This opens Ease of Access window. Inside the Ease of Access window, there are various links that allows you to set various accessibility options in windows 7. You can use these settings for options like "Optimizing Visual Display", "Replace sounds with visual cues" and you also have settings to choose how the way...

One day, your car may break down and you won't be able to afford to hire a mechanic, so what do you do... you look on the web for some how-to vehicle repair videos and become your own car mechanic, that's what. You don't need any advanced training to perform repairs and simple maintenance on your automobile, but you may need a few tools. Invest in the basic tools and you'll be prepared for just about any car malfunction you can think of. These tutorials will help get you on your way, as long ...

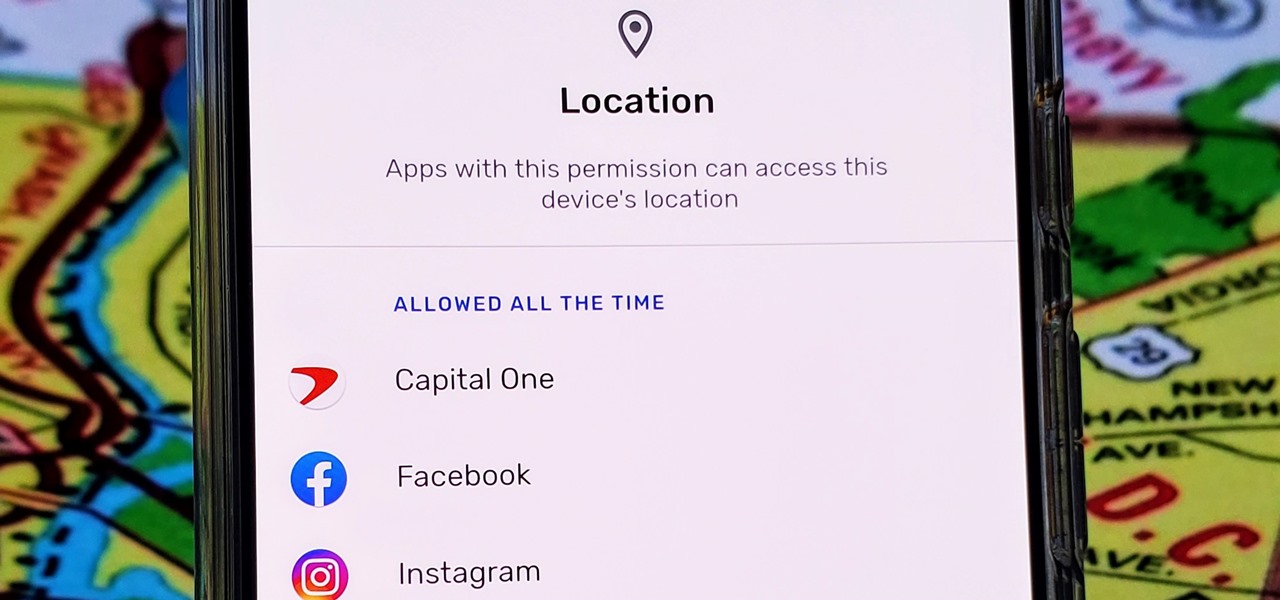
With Android 10, there are now three options when an app asks to access your location: Allow, Deny, and Allow While In Use. That last one prevents apps from seeing your location unless you're actively using them, and it's the default now. But when you first update, most of your apps will still be allowed to access your location in the background — at least, until you do something about it.

After dipping its toes into the AR cloud arena last year, Ubiquity6 is now jumping in with both feet this year.

There's definitely some malware-ridden apps on the Play Store. When it comes to the third-party apps you've connected to your Google Fit account, some have a crazy amount of permissions they have no business accessing. For example, you probably don't want a heart monitor app having access to your personal location data.

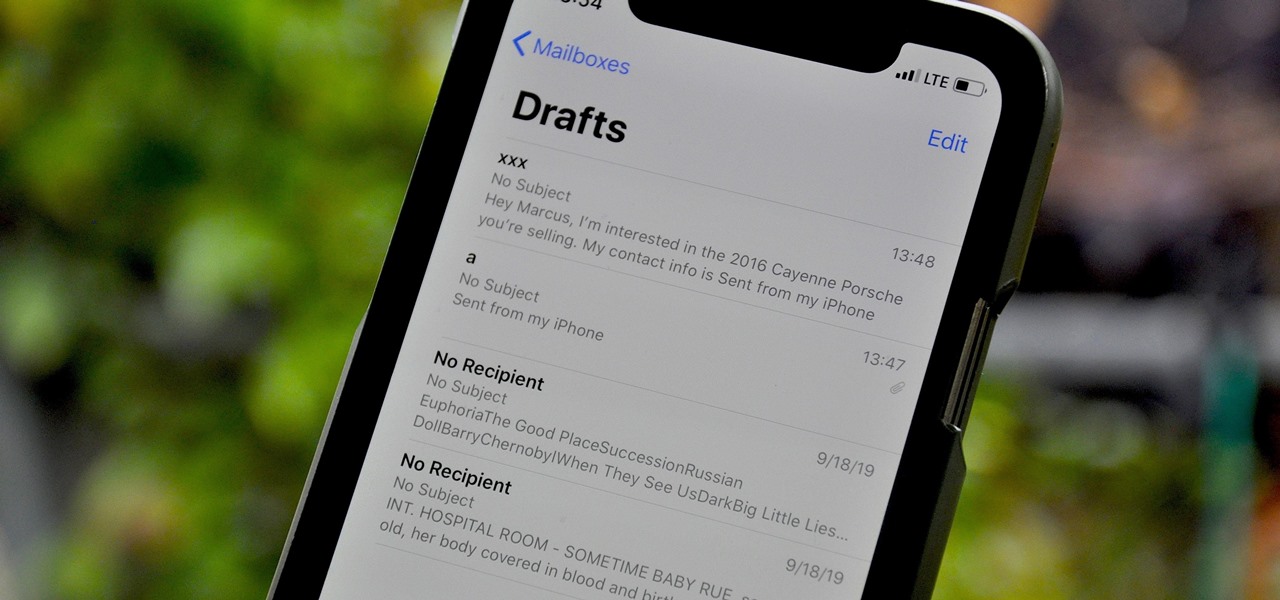
All of your partially written, unsent emails live in your "Drafts" folders, in limbo until the day they are sent off or deleted. In Apple's Mail for iPhone, you can access all drafts from all accounts in a combined "All Drafts" folder from the app's main Mailboxes list — but only if you added it manually. But there's an even better way to access all of your drafts in Apple Mail in iOS; it's just not obvious.

One of the best things about Android is the ability to customize every aspect of your device to make it your own. However, unless you have prior knowledge or experience with every single setting available to you, you might have missed a few critical features without even knowing it. Some settings are easy to find, while others might be tucked away in another menu of their own.

Two-factor authentication (also known as 2FA) adds a necessary additional layer of security to your username and password in many important apps. On Instagram, 2FA requires you to confirm it's you attempting to log in, with a special code sent to you via text message. Enter the code and you're in ... but what happens when you need to log in and don't have access to your phone?

Players of Pokémon GO on Android now have a reason to turn on AR mode with the release of AR+ support via ARCore.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

Just nine days after the official release of iOS 11.2, Apple has released iOS 11.2.1. The update initially seems to have been seeded to only a handful of users and is intended to fix bugs in 11.2.

SSH is a powerful tool with more uses than simply logging into a server. This protocol, which stands for Secure Shell, provides X11 forwarding, port forwarding, secure file transfer, and more. Using SSH port forwarding on a compromised host with access to a restricted network can allow an attacker to access hosts within the restricted network or pivot into the network.

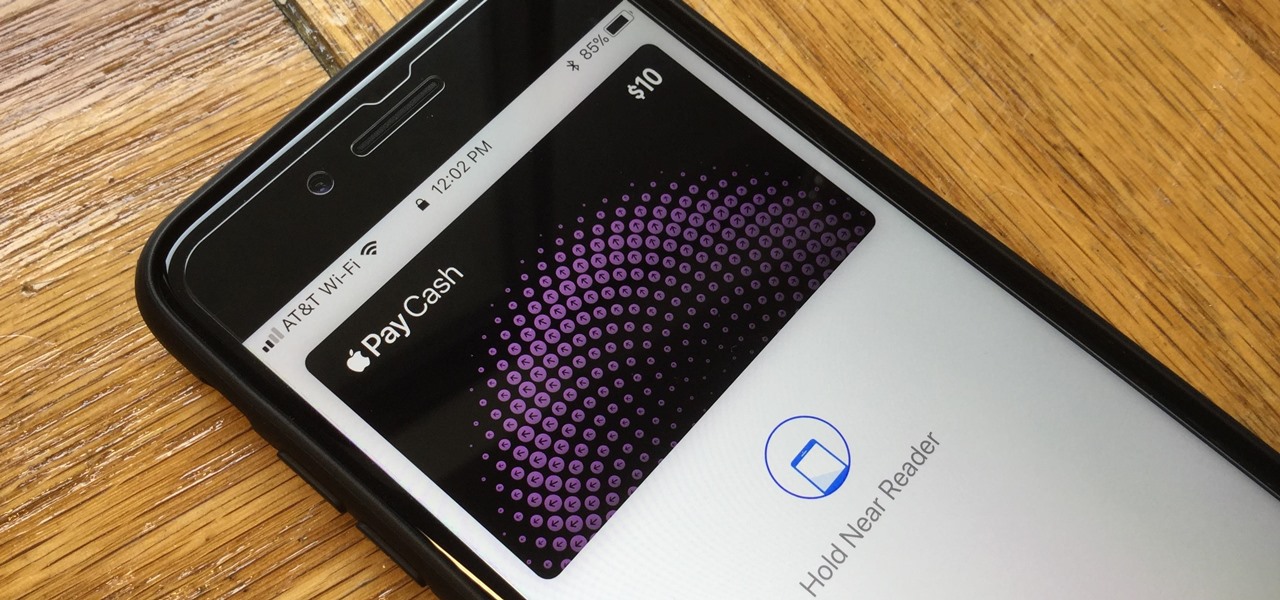
With Apple Pay Cash in iOS 11.2, your iPhone potentially becomes the only form of payment you need. Whether you're sending money to a friend via iMessage or paying for your groceries, you can use Apple Pay Cash to complete those transactions. It makes sense, then, that Apple would allow you to add your Apple Pay Cash card to the lock screen, for quick access wherever you are.

The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

After recently being in the news for collecting PII (personally identifiable information) for analytics and after-sales support, OnePlus has another security problem. An individual going by the name Elliot Alderson discovered an app in OnePlus devices that can enable root access with one command.

As smartphone users, we live in dangerous times. The value of phones continues to rise, making them prime targets for thieves. In 2015, the FCC estimated that one million phones are stolen each year, and with several devices starting to hit the $1,000 mark now, these numbers are sure to rise. But what do you do if you fall victim to phone theft?

Gestures are a big deal on an iPhone X, XS, XS Max, XR, 11, 11 Pro, and 11 Pro Max. Without a Home button on Apple's super-premium smartphones, several actions had to be mapped to gestures instead, which impacts other areas of the system such as the Control Center.

About a year ago, a certain watershed mobile augmented reality game based on a familiar video game franchise was released into the wild. Today, a number of imitators and emulators have introduced their own location-based games with hopes of similar success.

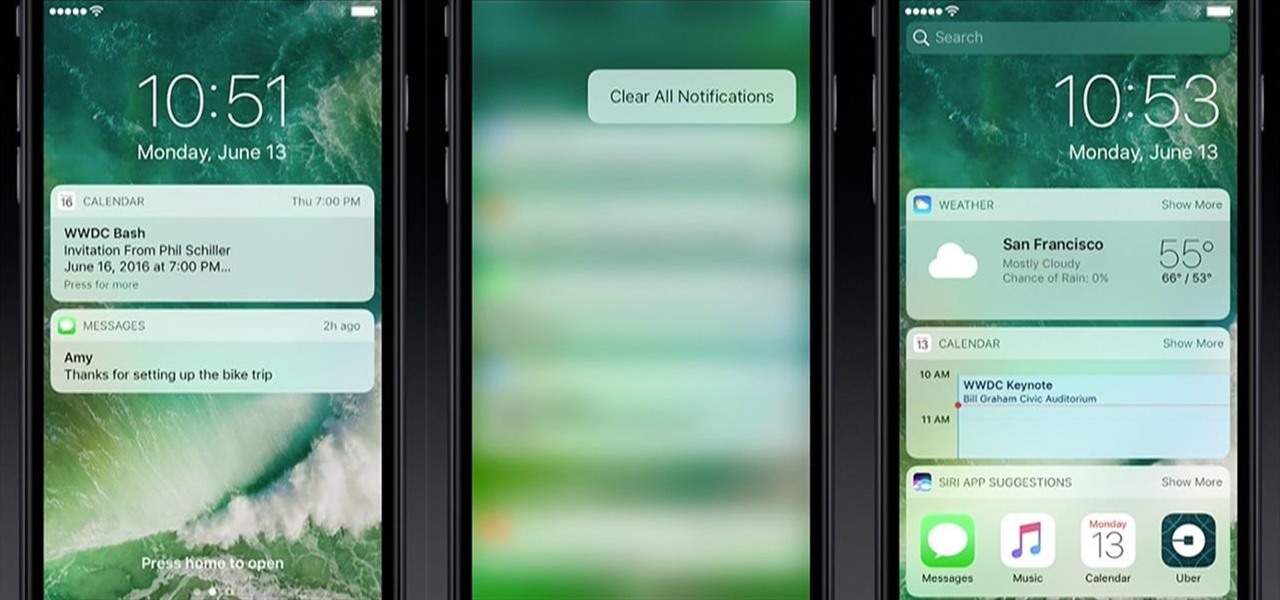
Your iPhone's lock screen is about to get a major upgrade in iOS 10, as shown off by Apple at WWDC '16, and it will make dealing with notifications and apps a breeze. The new lock screen has been fully redesigned to give users better and faster interaction with the apps they need. It's also snappier and more aesthetically pleasing with notifications no longer darkening the wallpaper.

You've probably heard the old joke about how Ford is an acronym for "Found on Road Dead." Well, the Detroit automaker on Monday announced a new and much better way to help you find your parked vehicle, as well as a whole host of other features—just use your smartphone.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

In this tutorial I am going to show you how to change some file metadata, this could be very useful if you want to edit or access a file and remove any evidence of your changes.

With as much creativity and freedom that we have on Android, it feels a little underwhelming that the only gesture we can perform on the status bar is a downward swipe to expose the notification tray or quick settings. Maybe this is a field for Android to expand on in the future, but until that day, third-party developers are exploring this now.

You would think that with each major iOS update, there'd be fewer ways to bypass the lock screen. Unfortunately, Apple's developers have consistently failed every year since 2013 in this department, leaving open lock screen exploits for iOS 7, iOS 8, and now the latest iOS version, iOS 9, with each exploit being discovered within days of the OS release.

In this day and age, maintaining your privacy is a perpetual battle, and doing so with an internet-connected device like your smartphone is even more of a struggle. Every website you visit, every app you install, every message you send, and every call you make is a potential vulnerability that could expose you to prying eyes.