How To: Use Safari as an RSS reader
RSS news feeds can be used to easily access news stories, blogs and podcasts. Watch this video and learn to read RSS feeds in Safari.


RSS news feeds can be used to easily access news stories, blogs and podcasts. Watch this video and learn to read RSS feeds in Safari.

This is an NLP Practitioner lesson on detecting eye movements in people to see if they are lying. The coordinates are labeled as below.

A tutorial on using LogMeIn.com to set up remote computing on your computer so that you can always access your computer from anywhere with the Internet.

Need internet access and you don't have a login? Hack into a private or controlled network with this tutorial. Thefixed.org also shows you how to build a smoke bomb!

In this tutorial, Bert shows you how to make a realistic 3D looking wine bottle, complete with label. This uses the 3D part of Illustrator and is great for those of you without access or time to use an actual 3D software package.

Don Schechter explains how to capture your footage from your camera to your computer and log it for easy access later on. You can use Adobe Premiere to capture your movie, but you can not forget to put your tape in your camera.

Are you looking to upgrade from that clunky dial-up connection to high-speed Internet access? Find out who comes out on top when DSL and cable go head-to-head.
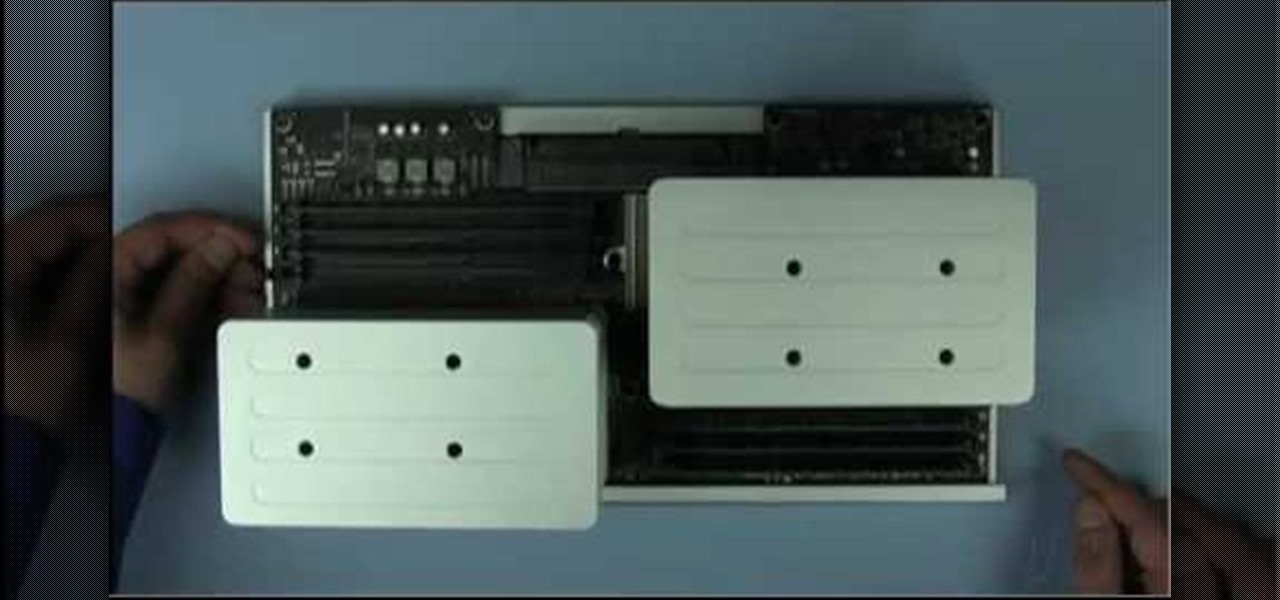
MacOSG demonstrates how to install memory in a 2009 Mac Pro. When performing this upgrade, be sure to take precautions for static by discharging static electricity before beginning. Shut down, unplug and place the Mac Pro on a static-free surface. To access the memory, you need to open the side access door by lifting the latch located on the rear of the Mac until it locks in the open position. You can then the door forward and then remove from the body. The memory is attached to the processor...

Right out of the box, iPhone is incredibly easy to use. If you want to get the most out of every feature, you’ve come to the right place. This video tutorial straight from Apple will teach you how to customize the Home Screen on the Apple iPhone 3G. The iPhone redefines what a mobile phone can do.

Learn how to build a remote controlled beer keg. Not only can you deliver beer to friends, but you can control the drinker's access to it. It's sort of like a remote control bartender!
There's a handy new feature in Windows 7 called the Ease of Access Center, which brings together settings and programs that can make your PC easier to use. This is where you get quick access to programs like Magnifier, Narrator, On-Screen Keyboard and more. Learn about the accessibility.

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

You can get an expensive ticket for driving with a busted tail light. But that's not all. Driving with a faulty brake light can be dangerous. Replacing the bulb is a simple task that takes only a few minutes.

Researching genealogy takes a little enterprise and the skills of a master sleuth.. Watch this video to learn how to research your genealogy and family tree.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

SEO is the name of the game. If you want your business or brand to succeed, ranking on the front page of Google is a boon. Getting to the front page of search engines takes work, but it's not impossible when you master SEO best practices.

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.
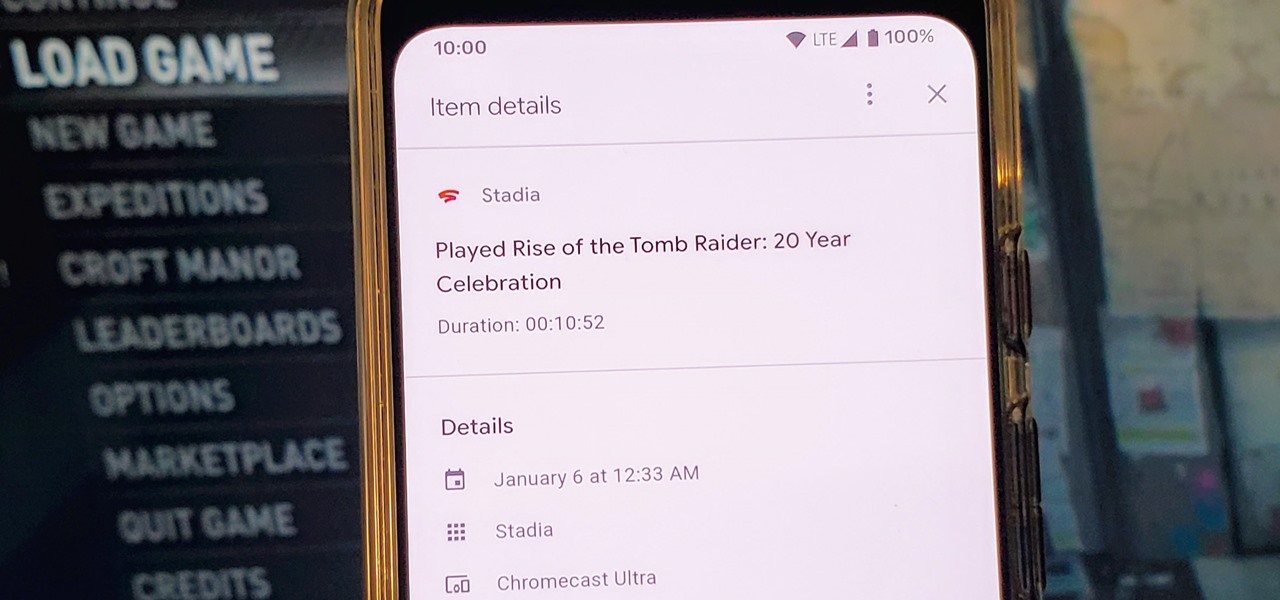
Since Stadia is an early access game streaming platform, Google is still working on bringing big things to the table. You can expect wireless Stadia controller support for many more devices, high-quality 4K gaming on all Chrome web browsers, and more Google Assistant features. They also managed to silently sneak in a way to keep track of your Stadia gaming sessions too, which is pretty handy.

You're reading this so you're probably already safely huddled up in your house or apartment, watching as the entire planet grapples with the unfolding coronavirus health crisis. But unlike some others, you're lucky enough to already have a couple of weeks of supplies and now it's just about what you can do to entertain yourself and your family as you weather the current situation.

Privilege escalation is one of the essential skills a hacker can have and often separates the newbies from the pros. With a continually changing landscape and a plethora of exploits out there, it can be a problematic aspect of any attack. Luckily, some tools can help expedite the process. Linux Exploit Suggester is just one of many to help you get root.

The biggest new feature in Android 10 is the system-wide dark mode. Both Samsung and Google phones have it, so third-party support is everywhere. The only problem is OnePlus forgot to include a way to quickly toggle dark mode on and off.

As we predicted this time last year, Magic Leap is finally moving from consumer entertainment hype to making a firm commitment to enterprise customers.
The Pixel 4 is one of the most talked-about phones of 2019, so you know there will be lots of third-party developer support. Mods are already popping up, so you'll want to get Magisk installed as soon as possible to get root access. The current method used to gain root is the quickest way yet, thanks to the recent TWRP custom recovery support for the Pixel 4.

While MacOS computers have been spared from some of the most famous malware attacks, there is no shortage of malicious programs written for them. To keep your computer safe from some of the most common types of malware, we'll check out two free tools. These tools can automatically detect ransomware encrypting your files and watch for unauthorized access to your microphone and camera.

Apple has seemingly always made it a priority to show how much it cares about user security and privacy — enough that it has a page dedicated to it, proclaiming that "privacy is a fundamental human right." It's true that there are few issues more important than user privacy when it comes to technology, and Apple only makes things better in iOS 13.

I go back and forth between two home screen apps: Nova Launcher and Action Launcher. While I prefer the aesthetics of Nova, I like Action's Quickpage feature since it puts some of my favorite apps just a swipe away. But now, I've found a way to replicate this feature on Nova (or any other launcher), and it works even better.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

It's been proven that hackers can manipulate your screen with fake taps through specific exploits, so they can potentially hit the "Grant" button when you get a superuser request. This is the last thing you'd want to happen since the malicious app from that point forward has full system privileges. Luckily, using a fingerprint to lock your superuser requests can prevent this.
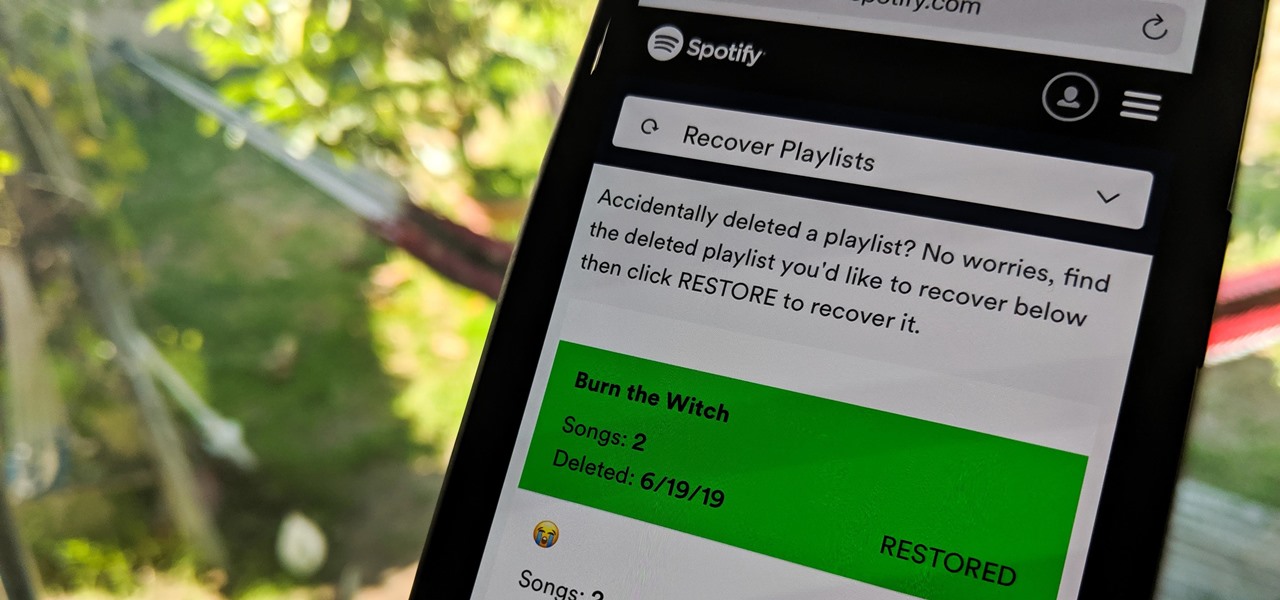
Absentmindedly or accidentally deleting your favorite Spotify playlist — which you spent hours or even days meticulously crafting — may seem devastating because there's no obvious way to bring it back. However, there is a hidden setting in the popular streaming service that can help you recover deleted playlists — you just need to know where to look.
Android 10 goes all-in on gesture navigation. Unlike Android 9, all three buttons which made up the navigation bar are replaced with gestures, with the biggest change being the back button. The problem is this same gesture is already used within apps to access the side menu, so in Android Q, this has been changed.

If you're ever faced with a situation of handing over your iPhone to law enforcement (or getting it taken forcibly), whether by the police, feds, or court system, there are things you can do to prevent them from getting access to all that potentially self-incriminating data. And it takes less than a second.
Call Screen is one of best features on Pixel phones. With one button, you can screen calls using Google Assistant and avoid pesky spam callers. However, after the call, there is seemingly no way to access the transcripts for future review. Fortunately, there is a way, but it is tucked away.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

If you're on iOS 11.4.1 or iOS 12 and go more than an hour without unlocking your iPhone, an "Unlock iPhone to Use Accessories" message will appear whenever you connect your iPhone to a computer or other device that tries to use the Lightning cable's data lines. This is to protect you, but it can be annoying if you have no reason to believe that law enforcement or criminals will have access to your iPhone.

There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.
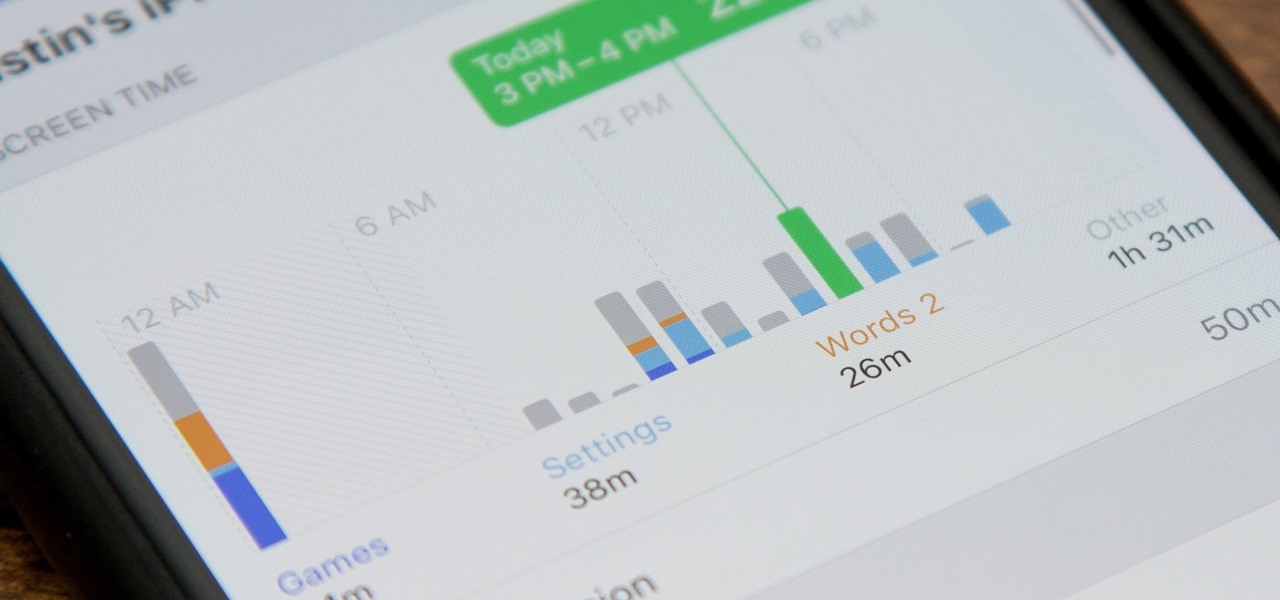
Apple's digital health initiative in iOS 12 includes Screen Time, a settings menu that shows you how much time you spend playing games, reading news, and whatever else it is you do. This menu also lets you schedule downtime away from your iPhone, set time limits for your apps, and more. While this is all great, it's hidden inside the Settings app — but there's a faster way to access this data.
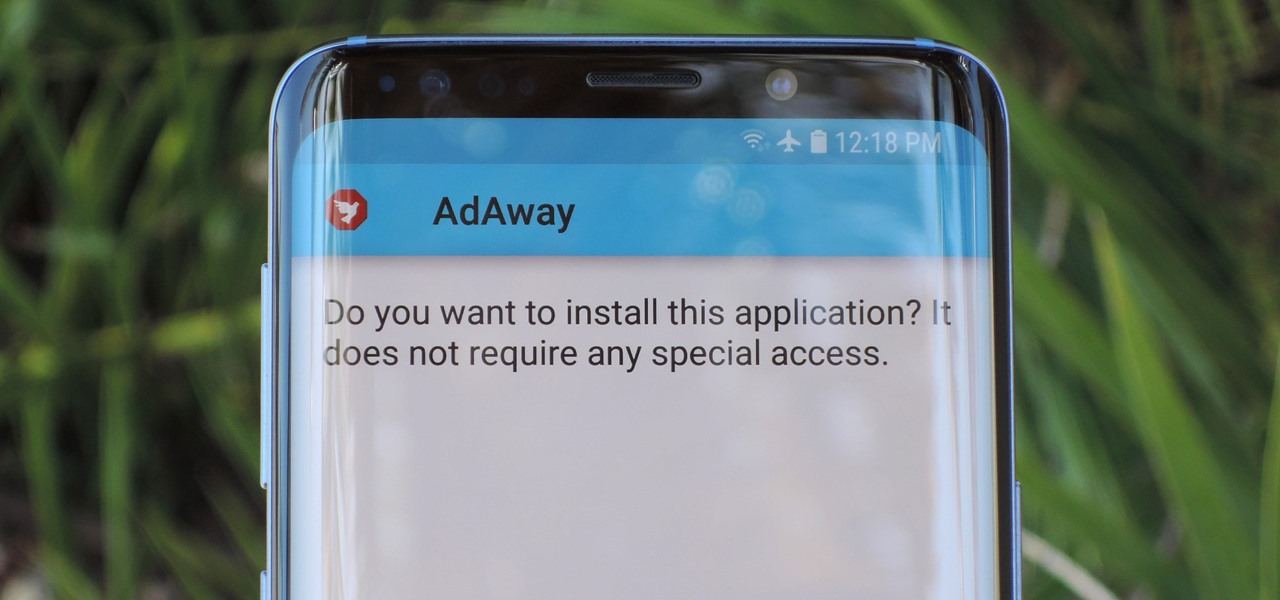
Starting with Android 8.0 Oreo, the process of sideloading apps has changed dramatically. Google removed the old "Unknown Sources" setting and replaced it with a permission that you have to grant to individual apps. It's really an interesting security feature.

HTC is entering the augmented reality market through the back door by giving developers access to the stereo front-facing cameras on the Vive and Vive Pro VR headsets.
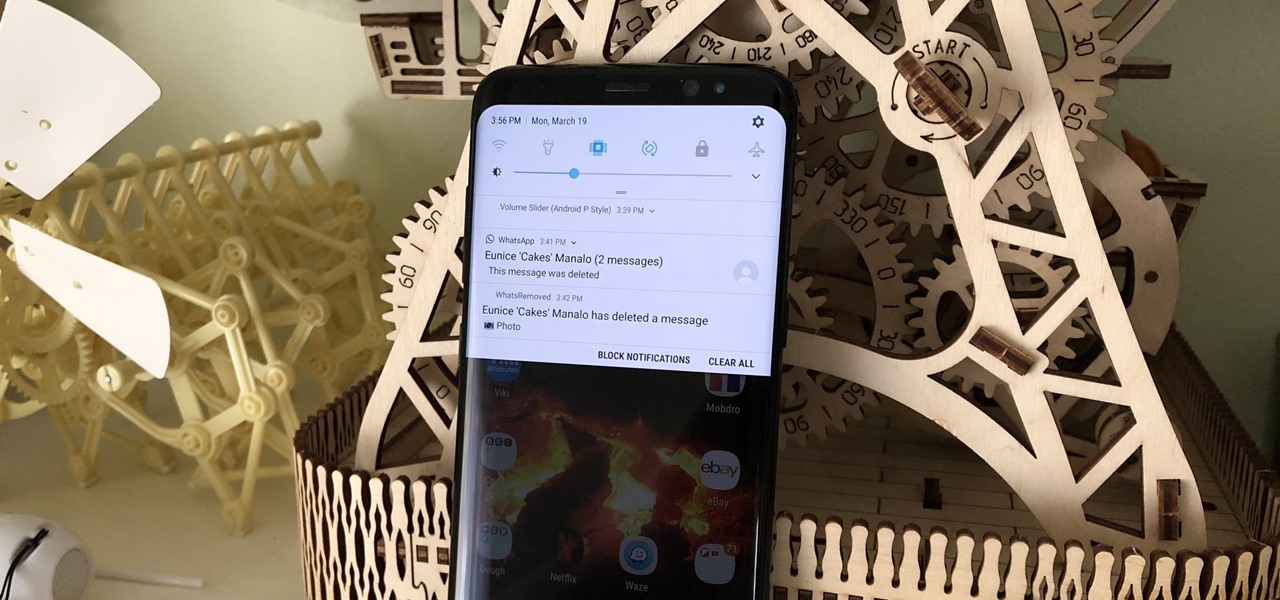
To help keep potential drama at bay, WhatsApp lets you delete questionable messages before the other person even sees them. If you're on the receiving end and you're curious about the deleted text, however, there's an Android app that lets you view erased messages.