
How To: Pick a normal lock
This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.


This video tutorial is for educational purposes only. See how to pick a normal lock with a tension allen wrench and a small screwdriver.
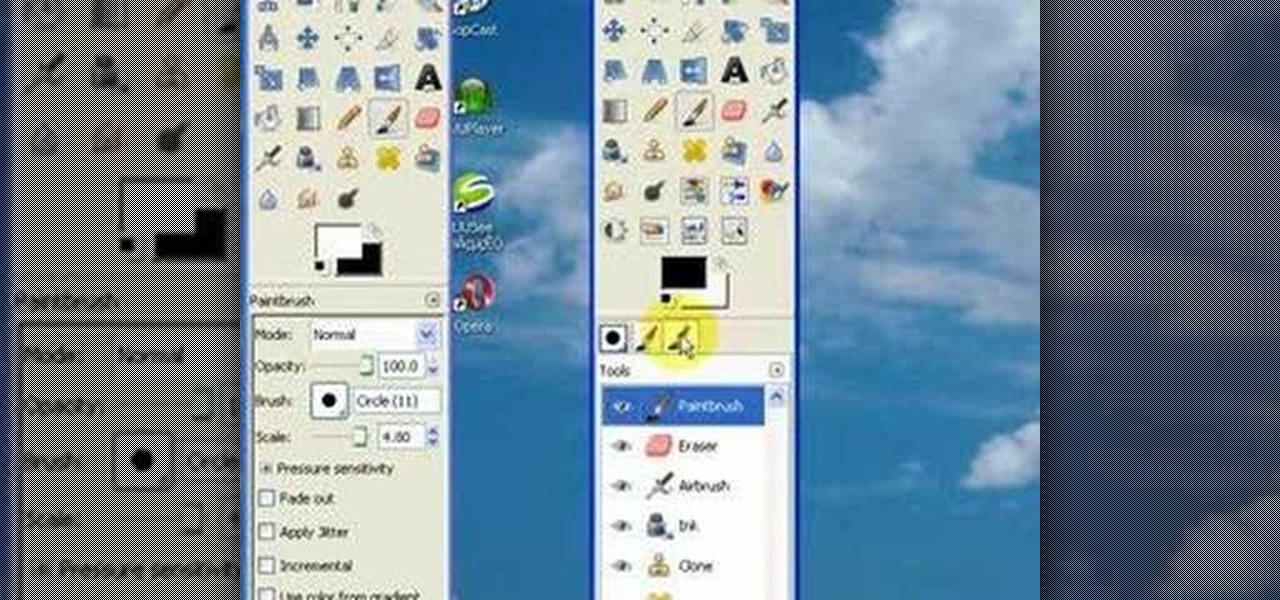
Are there certain tools in GIMP that you use all the time and want easier access to? Or just want to change the default layout? Check out this tutorial and learn how to customize the main toolbar in GIMP to work best for you.

Watch this electronics tutorial video to learn how to enter a secret code and see a lot of interesting info on how your iPhone connects to the network. Field testing your iPhone is easy with the tips in this how-to video.

Watch this helpful electronics tutorial video to learn how to quickly access the Safari address bar on an iPhone. This how-to video, geared primarily toward new iPhone users, will make using quick URLs to browse the internet on an iPhone very easy.
This helpful software tutorial video offers tips on how to keep Firefox bookmarks synced across browsers. The add-on explained in this how-to video will give you access to your Firefox bookmarks no matter what computer you're using.
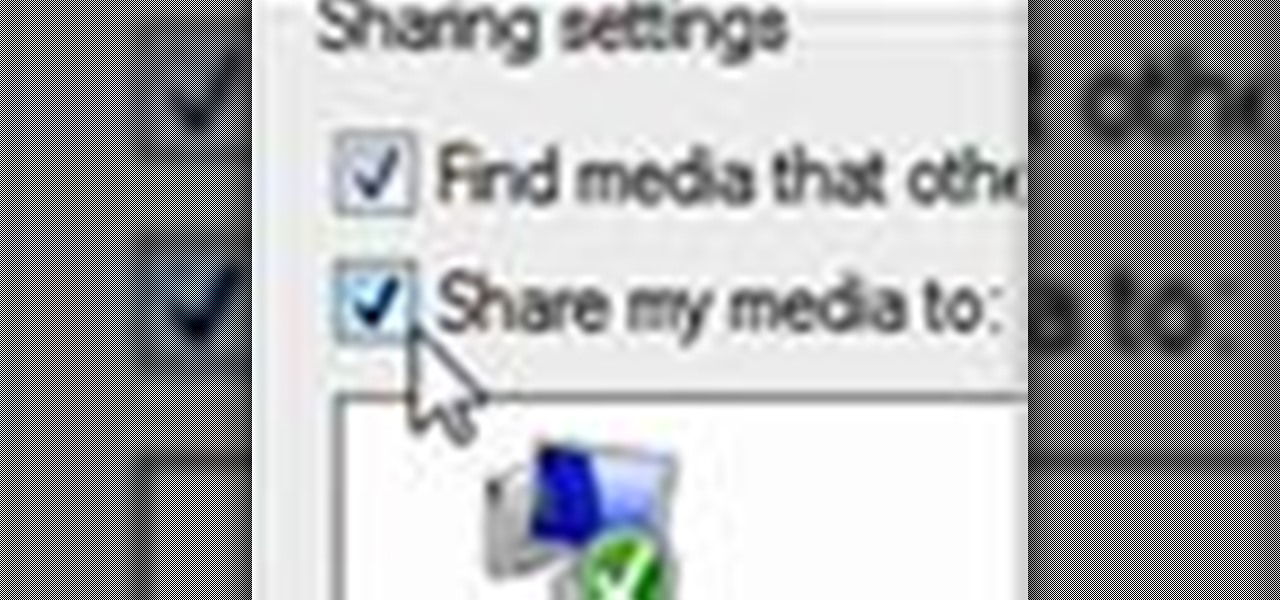
Using Windows Media Player, you can share files among a group of computers and easily access files regardless of where the media is stored. See how to share files in Media Player.

An in depth tutorial on the Sony DSR 250 provided by SPNN Access Staff.

A tutorial on how to "break in" to your Windows machine after you have lost the password. This works in Windows NT, 2000, and XP machines without an encrypted file system. I then show you how to wipe a hard disk to assure no one can gain access to your data once the drive is sold or discarded.

A tutorial showing how to set up a free dynamic DNS address with DynDNS.org and configuring the home router/firewall to forward traffic to your webserver.

Watch this video to learn how to use Google docs. You can view and edit your documents offline, without an active internet connection.

This episode of Take Zer0 discusses the differences between the multi-camera format used in television, and the single-camera setup most often used in film production. Since it's likely that indie filmmakers have access to only one camera, we will explain and offer examples of how to efficiently shoot multiple takes with one camera to convey a single action.

Learn how to con a vending Pepsi machine and access a secret (but benign) debug menu with this hack how-to video. While this hack won't get you any free soda, you might, at the very least, impress your friends with it. For complete instructions for this simple, pushbutton hack, take a look at this instructional video!

Learn how to install a trailer wiring harness in a Hyundai Sonata. This install will also cover Draw-Tite part # 24757. The first step involved is gaining access to your vehicle, the second step is we can hang the hitch on the tie down loop in the center of the vehicle.

If you are going to use your Subaru Forester to tow, carry a cargo carrier that has lights, or if you have accessories that need power, you are going to need to install a T-One vehicle wiring harness. This video will demonstrate the simple installation of the harness on a 2007 Subaru Forester and includes tips showing which panels need to be removed, where to access the needed plugs, and good locations for the wires and module box.
Pages '08 allows you to access the information in your address book and add it to your documents. This is helpful if you are printing envelopes or writing letters.

Don Schechter demonstrates how to capture your footage from your camera to your computer and log it for easy access later on for Final Cut Pro. Logging clips allows you to organize your footage without having to waste hard drive space.

Learn how to fix a squeaky floor in this brief yet informative tutorial. Note: you will need to have access to the floor and floor joists from underneath.

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.

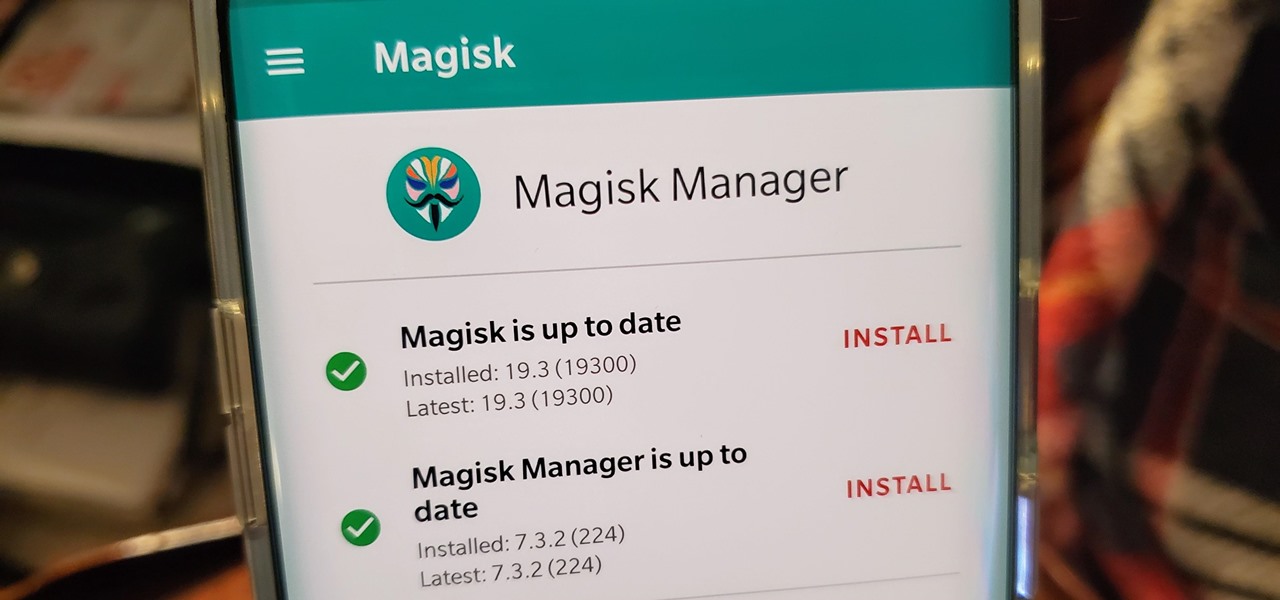
The biggest hurdle to rooting is that it usually requires a computer. Things get complicated when you're trying to use a desktop operating system to exploit a mobile OS, and the connection isn't always reliable. But with the help of Magisk, you can now use one Android phone to root another.

Smartphones are inherently bad for privacy. You've basically got a tracking device in your pocket, pinging off cell towers and locking onto GPS satellites. All the while, tracking cookies, advertising IDs, and usage stats follow you around the internet.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

It is said that the best way to avoid detection when hacking is to leave no trace, and often that means not touching the filesystem at all. But realistically, in most cases, it's impossible not to interact with the filesystem in one way or another. The next best thing to do to throw off any investigators is to change the file attributes to hide activity. We can do this with Metasploit's Timestomp.
OnePlus has purposefully made their devices easy to root so that you can spend less time waiting and more time doing. These phones are a solid choice for anyone looking to dive into the rooting and modding scene. Using the same principles that Google has with the Pixel line, you can always be sure your OnePlus 7 Pro will get first-class treatment from launch day and beyond.
The Pixel 3a came out of nowhere and flexed its muscles to show the industry that you can have a great phone without a hefty price tag. Since Pixel smartphones are first-party devices straight from Google, you can be sure you'll have root access one way or another. For right now the method used to get your Pixel 3a rooted will take a few steps, but they go by real quick.
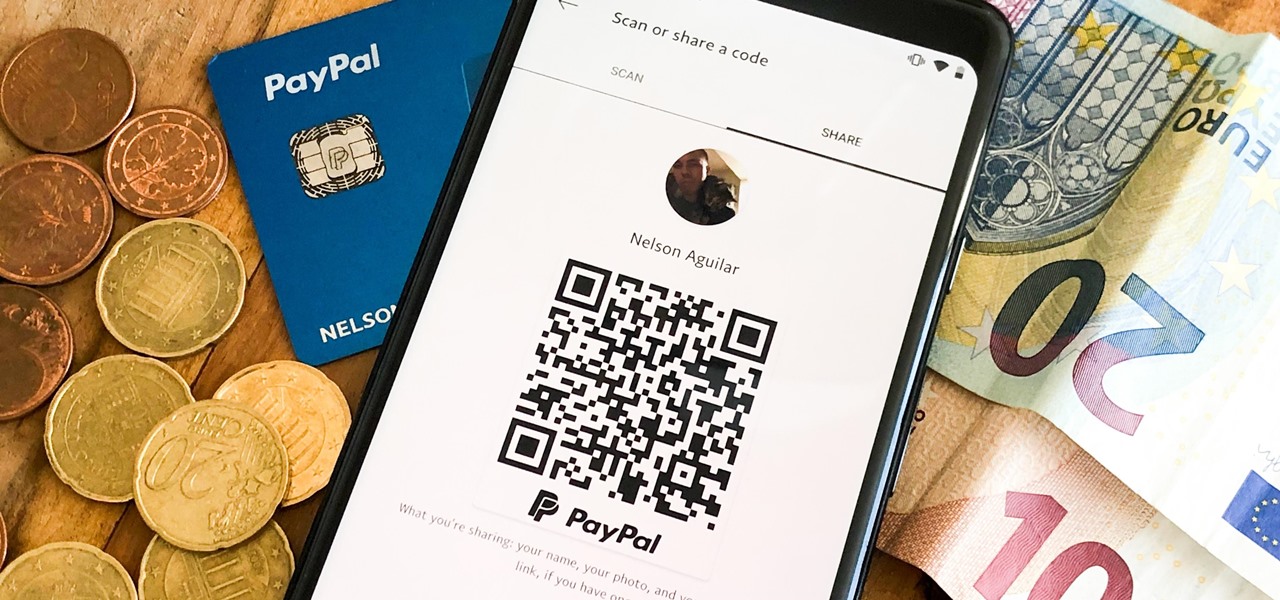
There are many ways to send and receive money on PayPal. You can use an email address, a phone number, or a PayPal.Me link, but if you're standing right next to the person you're trying to pay or get digital cash from, the easiest way, by far, is to use QR codes.
Android's settings menu is actually pretty daunting. There are options for nearly everything, so in the sea of various menus and submenus, it's easy to overlook important privacy and security settings. On Google's Pixel phones in particular, there are 20 such settings that you should double check.

With all the web applications out on the internet today, and especially the ones built and configured by novices, it's easy to find vulnerabilities. Some are more perilous than others, but the consequences of even the slightest breach can be tremendous in the hands of a skilled hacker. Directory traversal is a relatively simple attack but can be used to expose sensitive information on a server.

In 2018, there are more ways than ever to watch your favorite sporting events. You can stream them with a number of services, or you can simply watch it on a TV. Many fans will even watch it at a sports bar. The problem with a sports bar is that you won't be able to hear the game over the sound of dozens of loud bargoers.

Super Bowl LII will bring millions of football and non-football fans together to watch the big game on the big screen. But without a cable subscription, this process can be a little daunting. Luckily, the Google Play Store and the iOS App Store offer a few ways to accomplish this — no cable contract required.
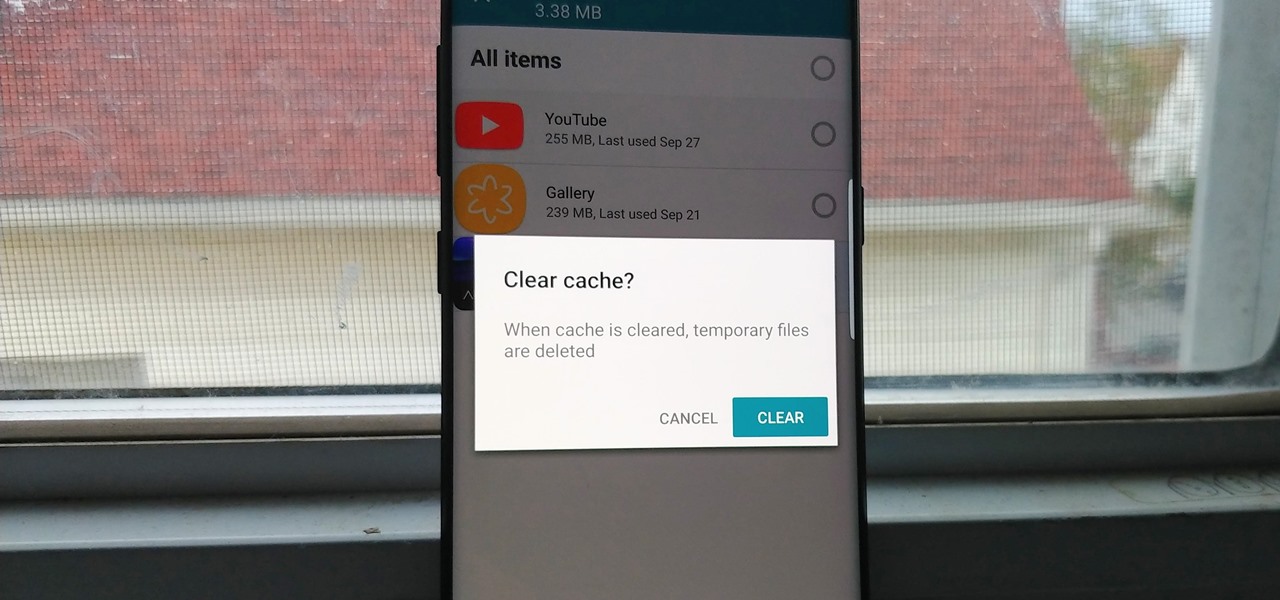
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

After previously learning how to make the material of an object change with the focus of an object, we will build on that knowledge by adding new objects through code. We will accomplish this by creating our bounding box, which in the end is not actually a box, as you will see.
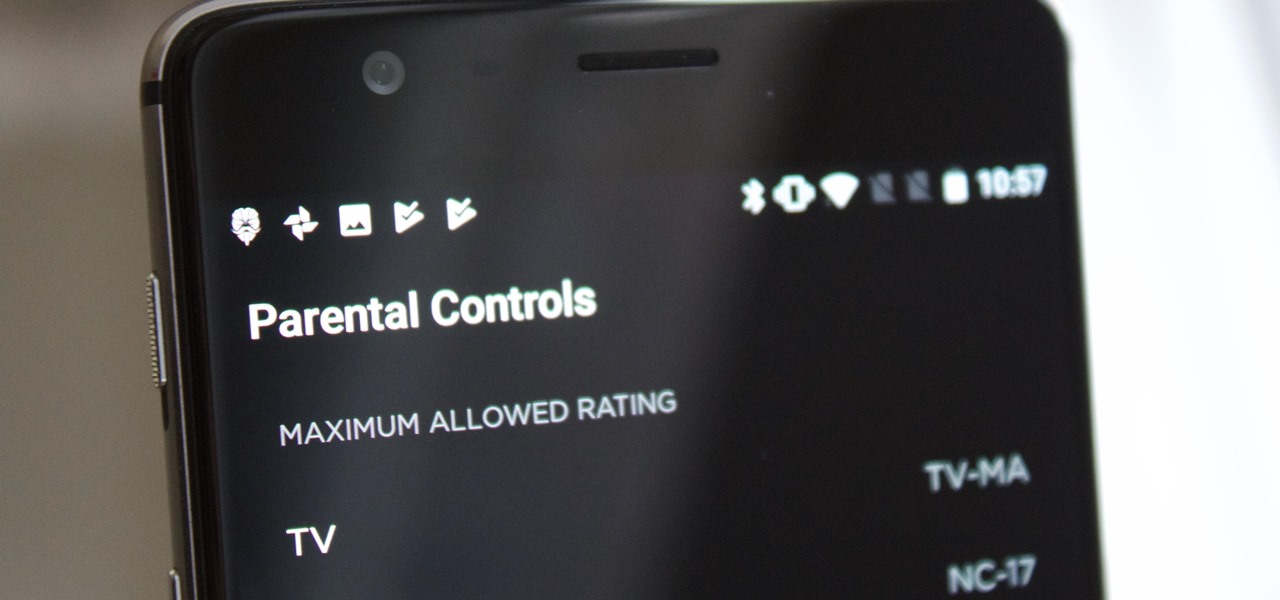
It's no secret that HBO has some ... mature content. Just watch the first five minutes of Game of Thrones. Yeah, I know. What a ride. But here's the thing — HBO has kids content, too, and it's good stuff!

Our smartphones are full of personally-identifiable information. So much of what we do with these devices is tracked and recorded to make our experience more streamlined and personalized. For many users, that's a fair trade — but for privacy-minded folks, it's a raw deal.

GitHub is an extremely popular site that allows developers to store source code and interact with other users about their projects. Anyone can download public, open-source files on GitHub manually or with Git, and anyone can fork off someone's project to expand or improve it into its own project. It's a really great site for programmers, developers, and even inspiring hackers.

The following are 5 pranks you can set up on your friends and family using their shoes. They're quite funny and to prepare these pranks all you really need are a few household items and a couple other things you can get at your local dollar store such as party snaps and party poppers. You'll also need access to your friends' shoes.
If you're all out of prank ideas for April Fool's Day, we've got a few that your Apple-loving friends will enjoy (or hate?). You can have a little bit of fun if you don't have access to their iOS device or Mac, but for the best pranks, you will need access to their devices, even if it's just for a few seconds.

If you have a broken laptop computer, but the hard drive still works, this video will show you how to access and remove your old photos, pictures and files.

One of Android's biggest strengths, when compared to other mobile operating systems is its open file structure. Google introduced a built-in file manager with Marshmallow that provides basic file management, but like with most apps on Android, there are alternatives. Third-party file managers are readily available, providing deeper access and control of all your files.