Mac OS X has finally added a way to use two apps side by side in full screen mode, à la Microsoft's Windows Snap. But since it's only available in 10.11 El Capitan right now, those of us with older systems will have to wait until the El Capitan Public Preview or final build is released later this year.

Anytime you surf the web on your iPad or iPhone, Safari saves which webpages you visit, the information you enter into them, and other types of data. This not only make your internet experience quicker, but it'll also keep track of everything you're doing.

The new iPhone 6 and 6 Plus have bigger displays, and that means more overall screen real estate, something that the new Safari app has taken into account by letting you access desktop versions of mobile websites. Even if you're sporting an older device, you'll still be able to request the desktop version of a site online in the browser.

Continuity is a new feature for iOS 8 and Mac OS X Yosemite which allows users to connect their Apple devices to their Mac in order to access applications, send text messages, receive phone calls, and more while seamlessly switching between devices. Inside Continuity exists a feature called Handoff, which deals specifically with the back and forth use of apps between your device and computer. Draft up an email on your iPad and finish it off on your MacBook Pro. Stare a document in Pages and c...

App switchers are a great way to conveniently access your favorite applications from any screen, but most limit the number of apps you can use. That means that whenever you want to switch over to another app, you have to leave your current one, and either find the one you want in recents, on your home screen, or in your app drawer.

I don't know of a pain greater than of the one felt after cracking the screen of your phone. After I managed to crack my screen, rendered unusable, I immediately began to panic as to how I was going to recover all of the photos, videos, and documents stored on my device. After a few hours of searching, I came upon a thread by Mohamad Sabra that showed exactly how to alleviate my problem.

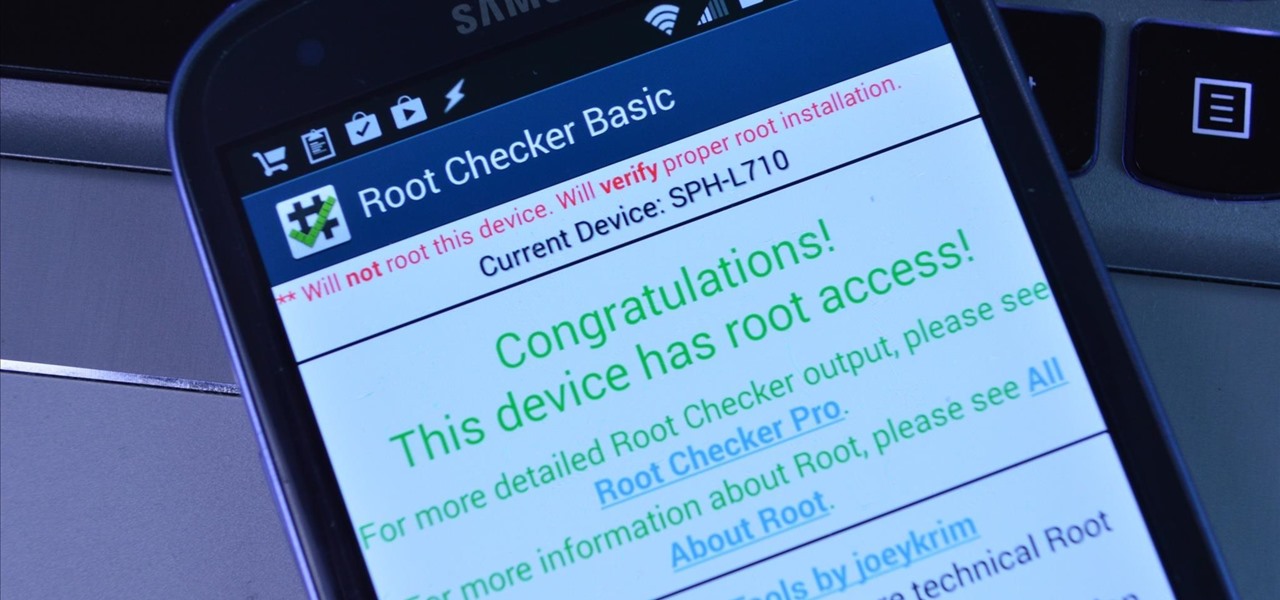
Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.

The Android lock screen interface is an integral part of our everyday use. For those of us who use lock screen security, it functions as a barrier between the sensitive data contained within our smartphones and potential outside access. Even if you don't use a pattern or PIN to secure your phone, you still interact with the lock screen every time you go to use it.

Samsung's Galaxy devices, for all the grief they get about supposed "bloatware", offer quite a few functional features that are not included in stock Android. From "Air Gestures" to a handy "Smart Alert" notification reminder, many of these features are more than just the latest gimmick to pitch in their ads.

Ever use an open hotspot on your Note 3, only to find out that it's severely restricted to what sites you can access? While getting online with free Wi-Fi is great for those who have a limited data plan, when that one site you absolutely need to visit is blocked, you're left frustrated and sent back into the Wi-Fi menu for another access point.

It's not enough for me to just listen to a mindless EDM song that can be retooled as a torturing method for Guantanamo Bay. As an actual fan of music, I yearn for substance and depth. Artists like Morrissey, Kurt Cobain, and John Lennon impacted lives with not only their music, but the subject matter of their songs.

Rooting an Android device used to be a nightmarish labyrinth of .zip files and command prompts, confusing seasoned modding veterans and newbies alike. Thankfully, the process has gotten simpler over the years, with various "one-click" rooting tool kits surfacing and working for nearly every major Android flagship on the market.

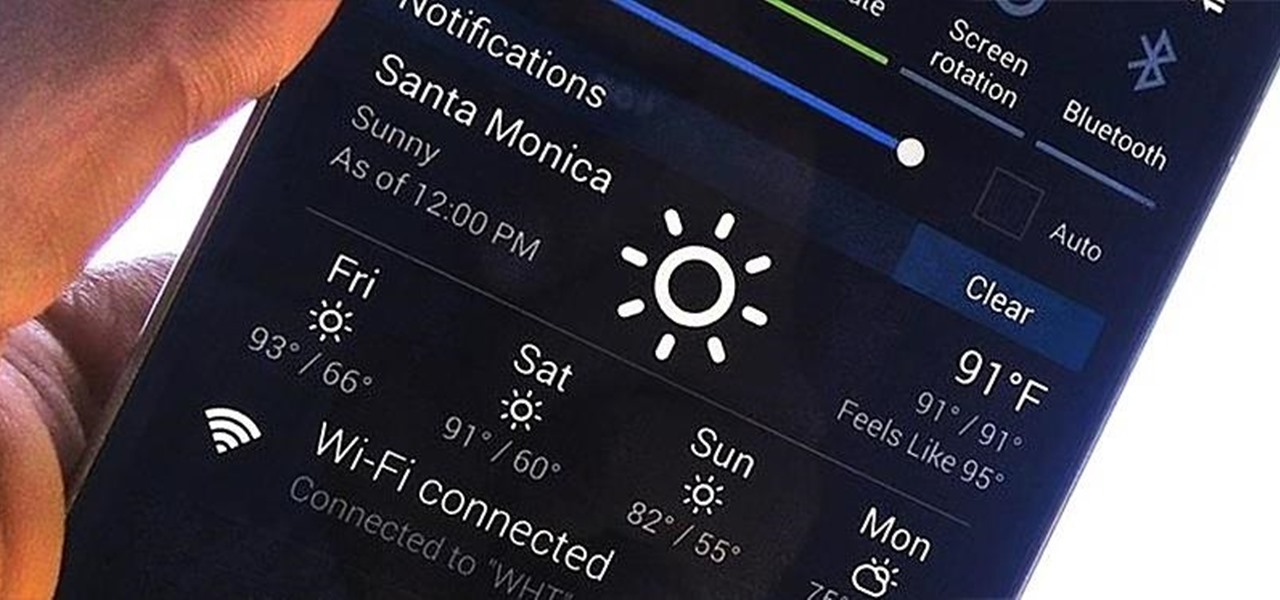
When looking at weather applications and widgets, one major characteristic I look for is efficiency; something that will separate it from the rest of the herd. The stock weather widget looks great on my home screen, but I have to exit whatever app or game I'm in when someone asks me about the weather.

Parents, grandparents, aunts and uncles, and even older siblings have all likely dealt with handing their smartphones over to young children. No matter if they want to play games or watch cartoons or record funny noises, you're handing over a very personal device to those who can mess up what they don't know.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

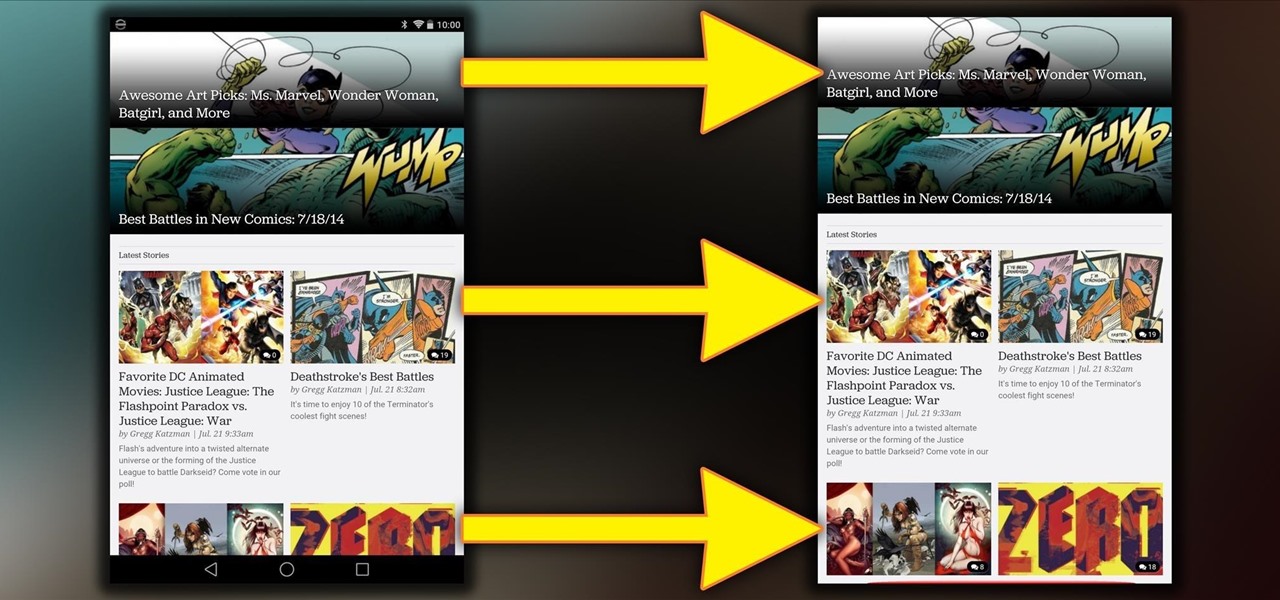
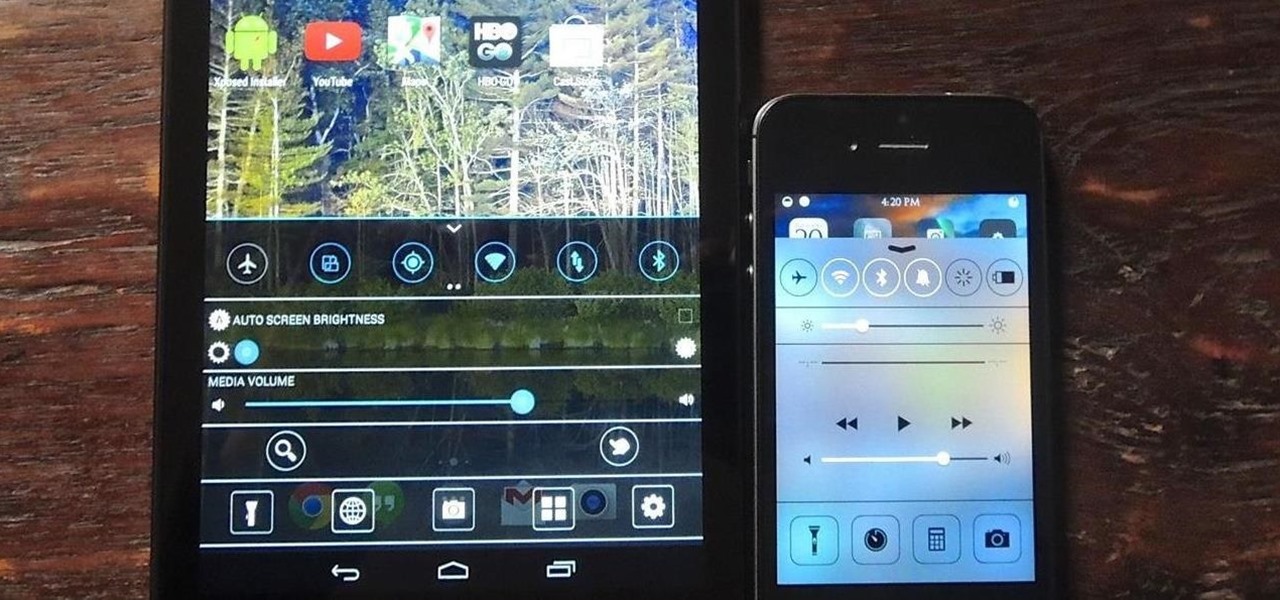
There are two types of tablet users in the world—those who like their quick settings up top, and those who want them on the bottom. I fall into the latter category, and there are a couple of reasons for it.

In direct competition with Pandora, iTunes Radio, and Spotify, Samsung has just launched Milk Music—a strangely named, yet completely free music streaming service for Android.

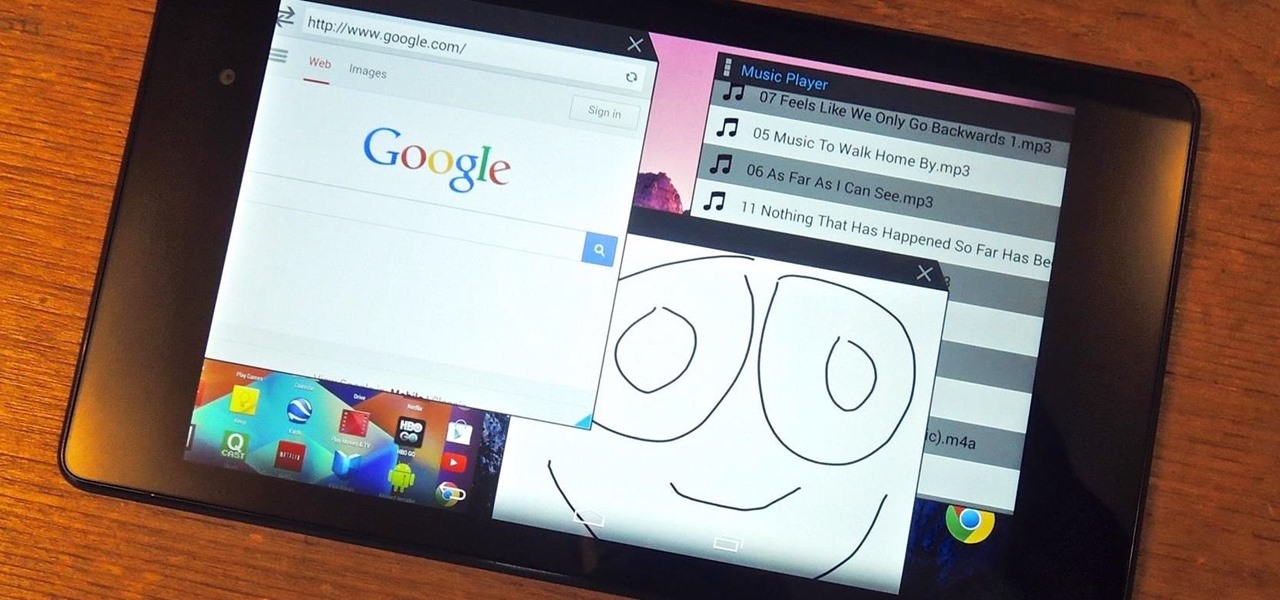
Recently, I offered a guide detailing how to run two separate windows on a Nexus 7 tablets for better multitasking. While extremely useful, that mod was limited to only two windows, and you also needed root access to use it.

Windows 8's interface was met with criticism when it was released, mainly directed at the tiled Start screen, a departure from Windows versions of old. Many felt that this new home screen style was better suited for mobile devices like Microsoft's Surface tablets and Windows Phones.

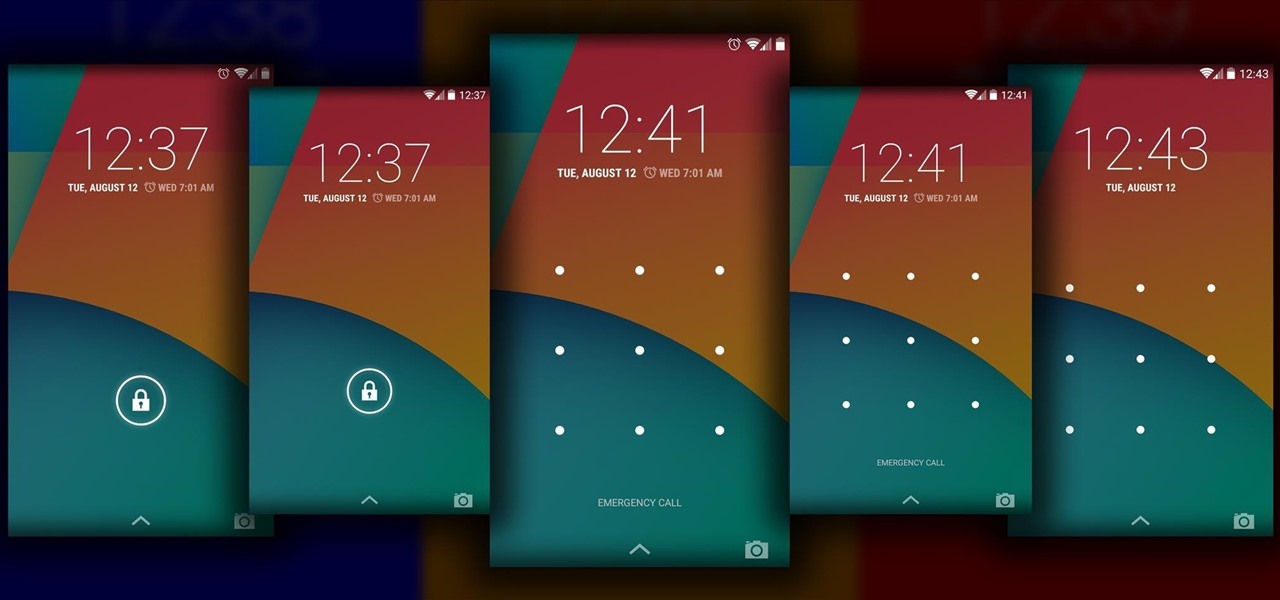
Sometimes it's the little things that make our days better, like finding a dollar in our recently washed jeans or a box of donuts in the lunch room. But your Nexus 7 tablet's lock screen isn't typically one of those things—it's just a lock screen after all.

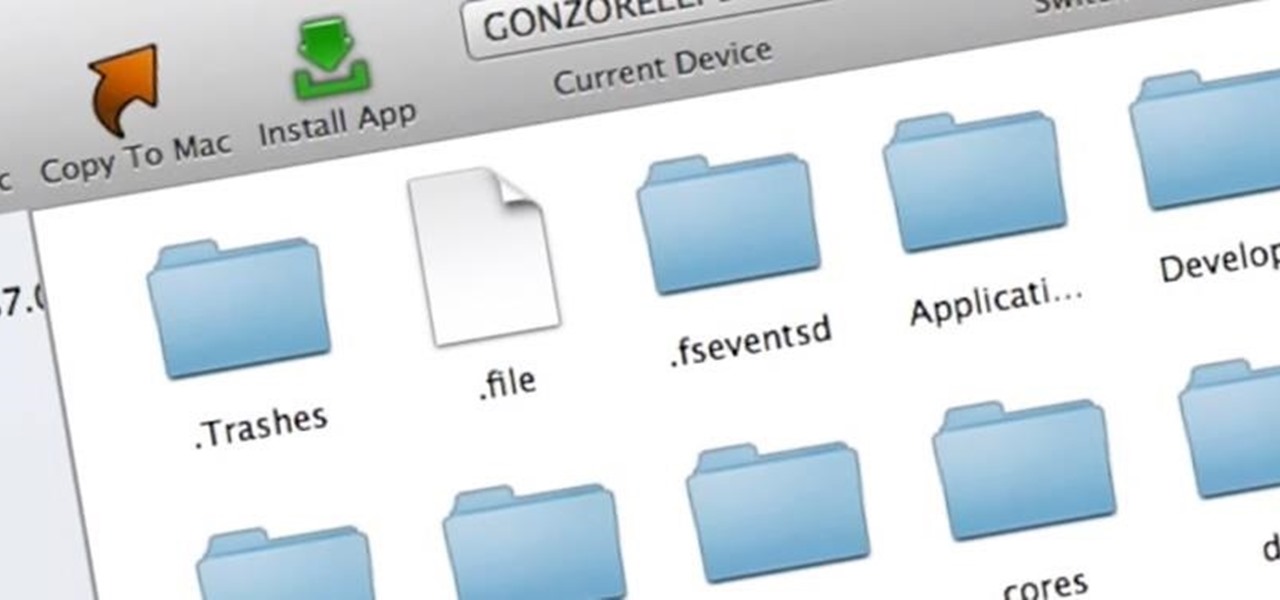
There are a ton of great mods and tweaks available in Cydia, but occasionally there will be one you want to install that hasn't quite made it into one of the main repositories yet. If you're not patient, it can be still be installed by manually placing the .deb file directly onto your device and installing it with iFile.

I could write about a new launcher everyday, because there are so many options out there for Android users, but one of my favorites it Everything Home. You probably have your own favorite, but what if you could actually use two launchers together, taking advantage of each one's awesome features?

Every time Apple releases a new product or software update, people quickly figure out exploits in order to bypass the lock screen without having to type in the passcode. It happened last year in iOS 6, so it's not surprising that it happened again in iOS 7.

You saw our post on the 18 coolest new features of iOS 7, but now that you've had a chance to play around with your updated iPhone, it's time to lock it down.

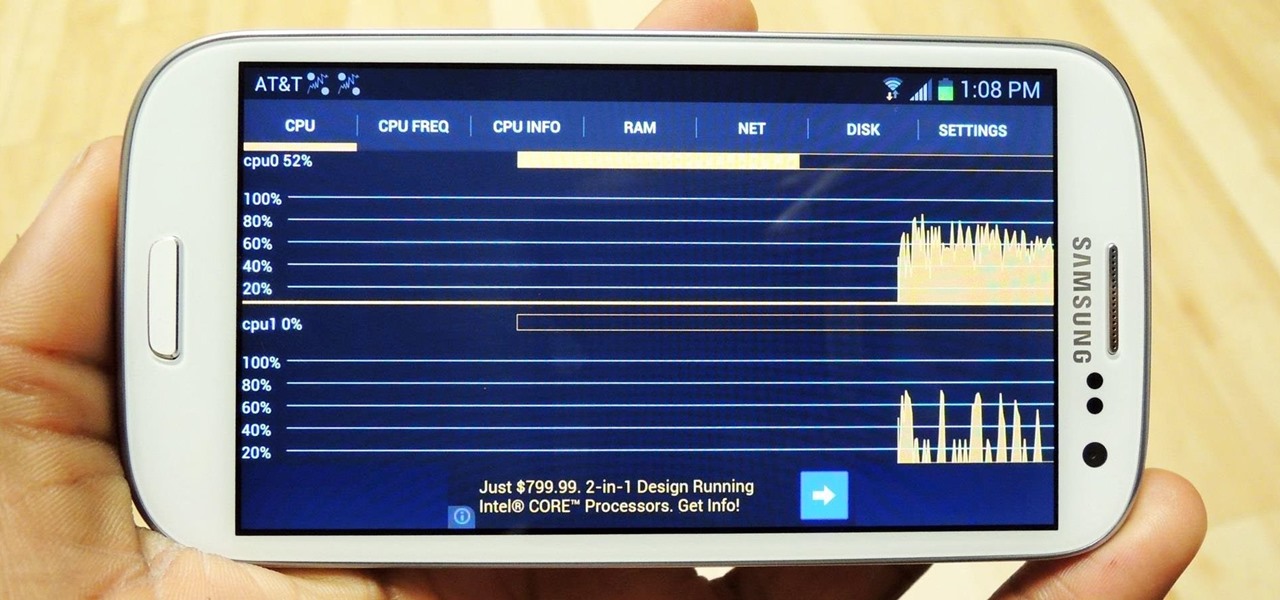
Anyone who uses a computer on a regular basis probably knows how to access the task manager to check system resources and usage stats. However, on a Samsung Galaxy S3 or other Android device, it may not be so obvious. There's no equivalent to Control-Alt-Delete, but it's still fairly easy to monitor running processes and battery usage.

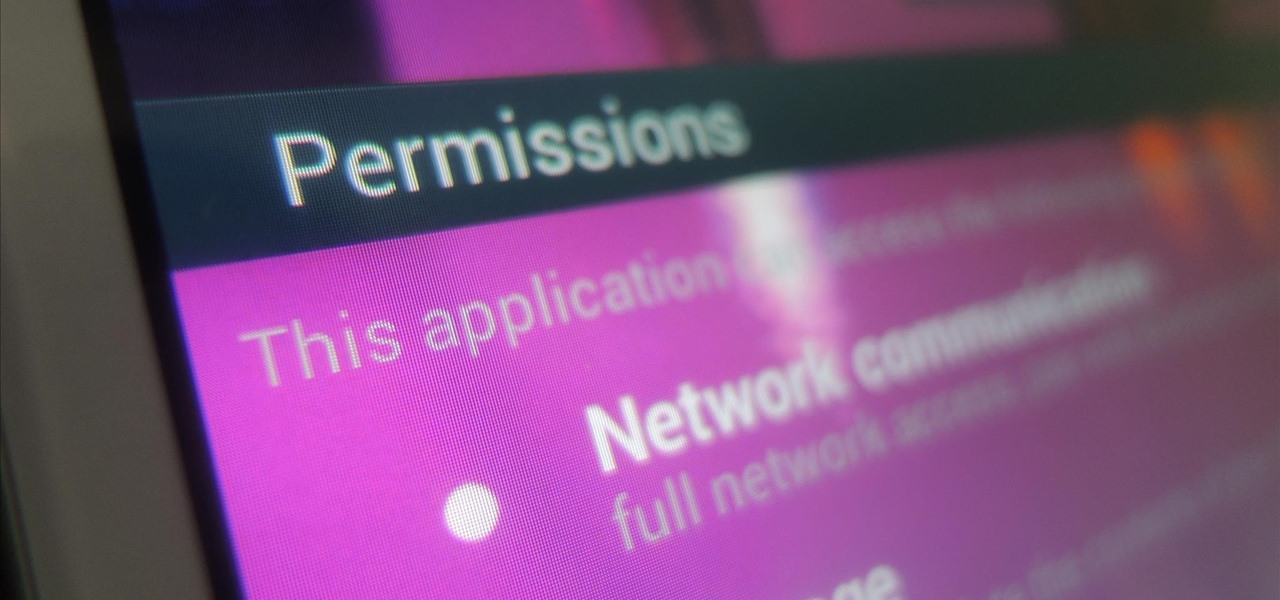
While we're usually responsible for leaking our own private information through mediums like Facebook, there are other times when we mistakenly and unwillingly allow certain applications to scour through our personal data. Some apps may have enabled permissions for internet access, thus allowing it to share said data with its external servers.

The transition from an iPhone to a Samsung Galaxy Note 2 or other Android device can be a tough one. A vastly different operating system and the ability to customize anything and everything might be too much for some people. Taking in all that new, while having to let go of the old, can be as daunting as climbing Mount Everest.

Running multiple applications at the same time is one of the Samsung Galaxy S3's and S4's biggest advantages over Apple devices, and it's a fact that Samsung certainly harps on constantly in their well-targeted commercials.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

What is your Samsung Galaxy Note 2 running? More than likely, you're still rocking Jelly Bean 4.1.2, which is already pretty outdated. My grandma uses 4.1.2.

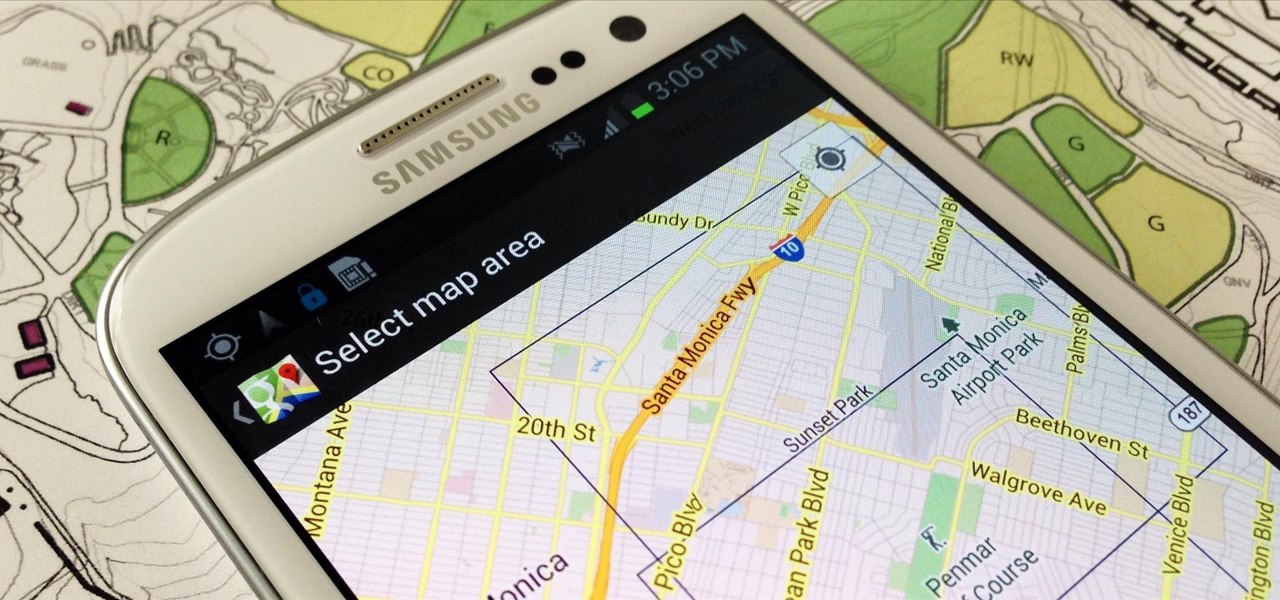
When you have to take four different freeways to go twelve miles, Google Maps becomes a very close and dear friend—especially in Los Angeles. Without my trusty Samsung Galaxy S3, I seriously don't know if I could make it back home half of the time. Of course, you'd probably get better directions using a Garmin, TomTom, or other GPS device, but when you already have a smartphone like the GS3, dedicated GPS units become nothing more than a luxury item.

Welcome back, my fledgling hackers! There's an evil dictator hellbent on destroying the world, and in one of our last hacks, we successfully compromised his computer and saved the world from nuclear annihilation. Then, we covered our tracks so no one would know what we did, and developed a hack to capture screenshots of his computer periodically so we could track of what he was up to next.

Gaining remote access to a phone isn't only for super hackers and spies. There are plenty of times when the average smartphone user would want to have remote access to their device.

Having trouble getting a strong Wi-Fi signal on your Samsung Galaxy S3? Does the signal drop out on you when changing rooms? Frustrating, isn't it?

The U.S. Postal Service has been in trouble for quite some time. With more and more people choosing to go digital to take care of bills, legal documents, and pretty much all other forms of correspondence, they haven't exactly kept up with the times. I mean, let's be honest—when was the last time you sent snail mail?

Even though iOS 6.1 was only released a couple of weeks ago, hackers released evasi0n a couple days after. Evasi0n, the only iPhone 5 jailbreak currently on the market, is the most popular jailbreak in history—with nearly 7 million iOS devices already hacked in the mere four days after its release. Well, now it seems that iOS 6.1 is being taken advantage of again, this time with a simple exploit figured out by YouTube user S1riOS6, which lets you bypass the lock screen on an iPhone running iO...

There is nothing more irritating than having a nice jam session interrupted by an ad selling B vitamins, and that's exactly what Spotify does to you if you don't pay up.

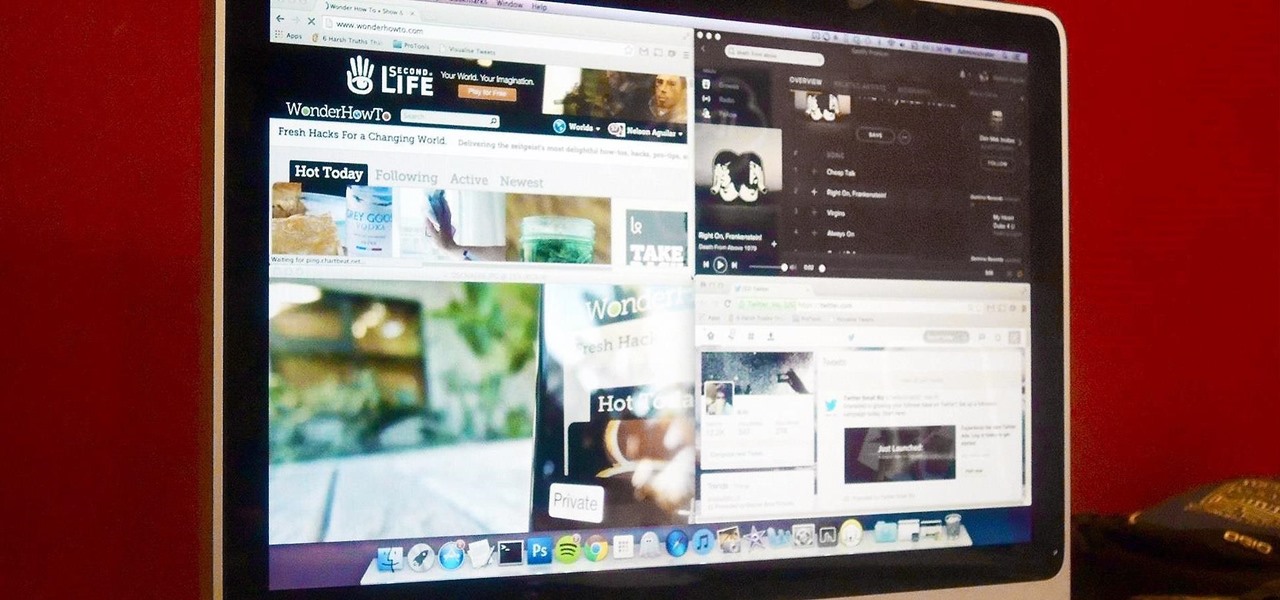
Using a second monitor is great for multitasking, especially if you tend to max out your computer's brain power on tons of simultaneously running apps that you want to see, well, simultaneously. That second screen becomes more like a lifesaver.

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...