I've been a Sprint customer for a long time. Normally, Sprint (flagship) phones come with some useful apps, such as Sprint TV, Sprint Zone (for payments, updating PRLs, and account information), and NBA Game Time. In other words, relatively free of bloat.
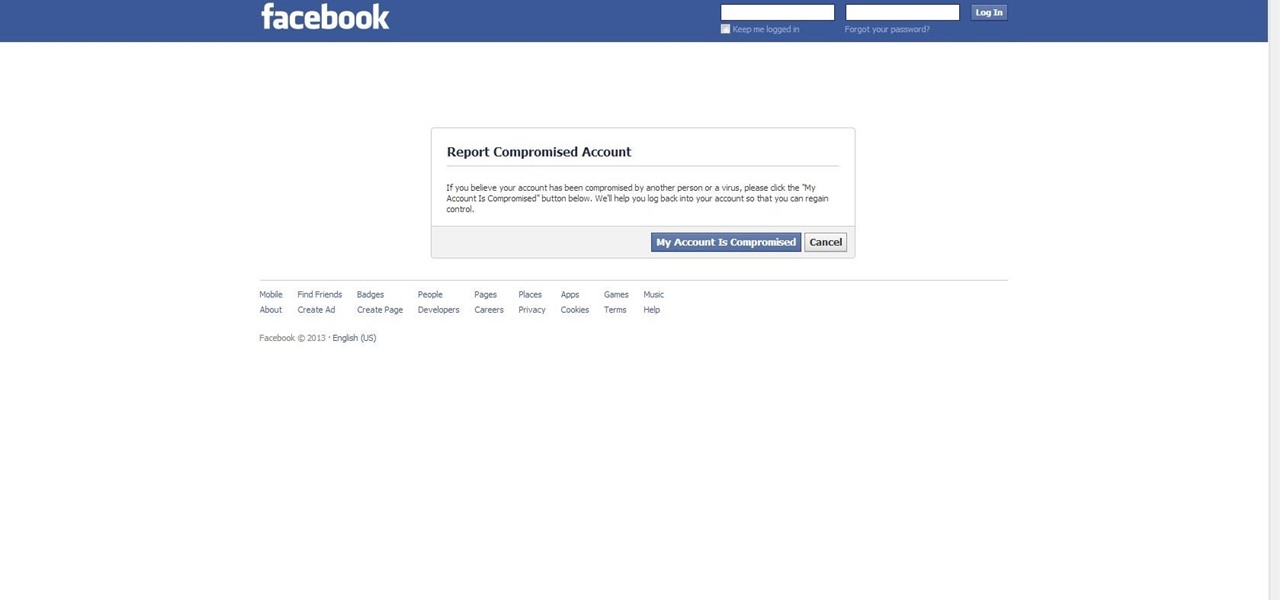
If your facebook account was hacked by someone and you really want it back this tutorial would help you get it back.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

The rumors are flying everywhere about the Samsung Galaxy Note 2 getting updated to Jelly Bean 4.2, but as of now, we have no freakin' idea when. Among all of the features sported in the update, Photo Sphere is one of the more popular, allowing you to snap incredible and immersive 360 degree photographs. So, until that update comes, you're probably still marooned with Jelly Bean 4.1.2 on your Note 2, and that means no Photo Sphere camera.
In this Windows 8 Tutorial you will learn how to disable automatic maintenance. Their are really two situations I can think of when you would want to disable automatic maintenance in Windows 8. The first being if your Windows 8 computer came with a Solid State Disk then you will probably want to disable automatic maintenance. The reason being is that a solid state disk does no benefit from defrags and the automatic maintenance automatically defrags your hard drive and this will take away from...

Newsletters, subscriptions, and receipts are all necessary evils that come along with online services and shopping, and they take up a significant amount of space in a lot of people's inboxes. If you've ever signed up for an account on a website, chances are you've gotten an email from them.

You know that guy who does the cheesy card trick to get the attention of all the girls at the party? Well, we kinda hate that guy don't we? But, if we could be that guy, it might not be so bad.

These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected.

Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

When it comes to your smartphone, you don't have to be a cheater to want a little privacy. I don't even like people playing Temple Run on my mobile because I don't want anyone beating the achievements I've been working on getting myself.

I'm all about safety in my life. I even put on safety goggles when someone opens a bottle of champagne—high life problems. But when it comes to driving, you have to be double safe, because the other drivers on the road may not have your safety in mind.

As most everyone knows, Android and Apple don't get along so well. Even the users don't get along well, with Android and iPhone users constantly berating and insulting each other online—any chance they get. I should know, since I was one of them, but I'm now rare breed who's learned to appreciate both. People just need to realize that they have their own unique strengths—Android with its customization and Apple with its simplicity.

Humans are able to produce a wide variety of sounds in part because they have descended voice boxes that makes room for longer vocal tracts.

This tutorial is for those who are new to Windows 8.

While websites may run smoothly without any noticeable vulnerabilities, there's always the looming threat that any background weakness in the site can be exploited by hackers. Once a site is compromised, it can be difficult to get it fixed without the proper help. Google has recently launched a new series entitled "Webmasters help for hacked sites”, which teaches web developers and site owners how to avoid getting hacked and how to recover their website if it gets compromised in any way.

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

My obsession with Siri is well documented, and after I jailbroke my iPhone 4 recently, I thought I would finally be able to rekindle our imaginary love. But, when I downloaded the Siri Port, I found that the app was buggy and super slow.

This video demonstrates how to calculate shipping costs with UPS. UPS provides an easy-to-use online calculator to help customers accurately estimate shipping costs. By following a few simple steps, this tool can help customers control their shipping costs and avoid confusion during the billing process.

Warm water is an essential part of life that we sometimes tend to take for granted. Over one billion people, or roughly one-seventh of the world's population, have no access to hot water.

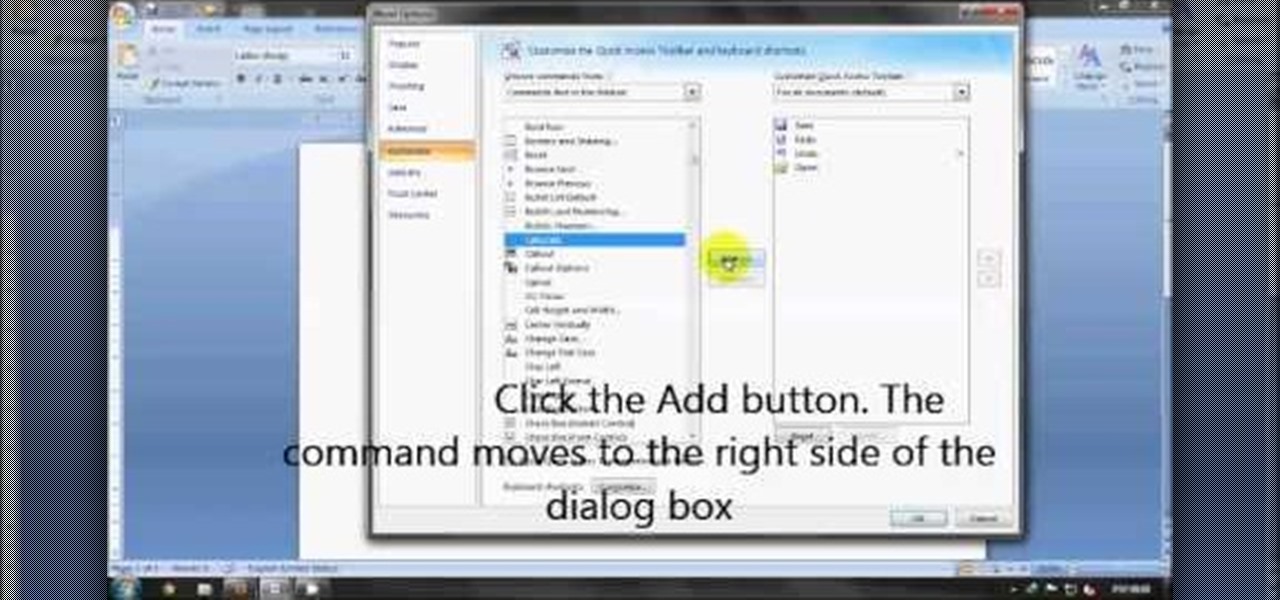
Step 1: Calculating Expression in MS Word Step 2:

There's nothing more inherently awesome than looking up into the stars and wondering WTF is really out there. Outer space is one of those rare items that a Google search cannot provide all of the answers for.

Polaroid photographs have a charming old-fashioned feel to them, evoking nostalgic memories of past days. My younger sister used to carry her Polaroid camera everywhere she went, transforming even the most trite moments into something wonderful.

Playlists are a great way to organize and share groups of videos on YouTube. Playlists can consist of your videos, someone else's videos, or a combination of the two.

Got a Samsung tablet with an S Pen stylus? Then you might be one of the many people irked about having to manually choose a different keyboard layout after pulling the S Pen out of the device. For instance, if you have a Samsung Galaxy Note I or Note II, when you pull the S Pen out, the keyboard layout stays the same. But if you'd like it to switch to a different keyboard, say, from the stock Samsung keyboard to something like SwiftKey, then you're out of luck.

Sharing screens is a great way to showcase projects, photos, or videos without having to download and upload those files on the other devices. This is made easy with AllSharePlus. You can download the AllSharePlay application for your Samsung Galaxy S III or Tab 2 right here. If you would like to download it for sharing on your laptop, you can visit the Samsung website. For now, the desktop app is only compatible with Windows XP or Windows 7 and the devices shown above. Nevertheless, it is gr...

LEGO has not attempted a blimp, zeppelin, or similar airship since 1999, the 5956 Expedition Balloon which used highly specialized parts. This is unfortunate as these vessels are well and truly part of the pulpy adventure and steampunk scene.

As dedicated bicyclists are well aware, riding can be very dangerous. Now that daylights savings time has ended in the United States, darkness appears quicker, and the night is especially dangerous for cyclists because of the low visibility that drivers have. Not only is darkness a danger, but also fog, blizzards, and heavy rain—all wreaking havoc on the vision. To combat this, bikers attach reflectors: clear front reflectors, red rear reflectors, amber pedal reflectors, and clear side reflec...

It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

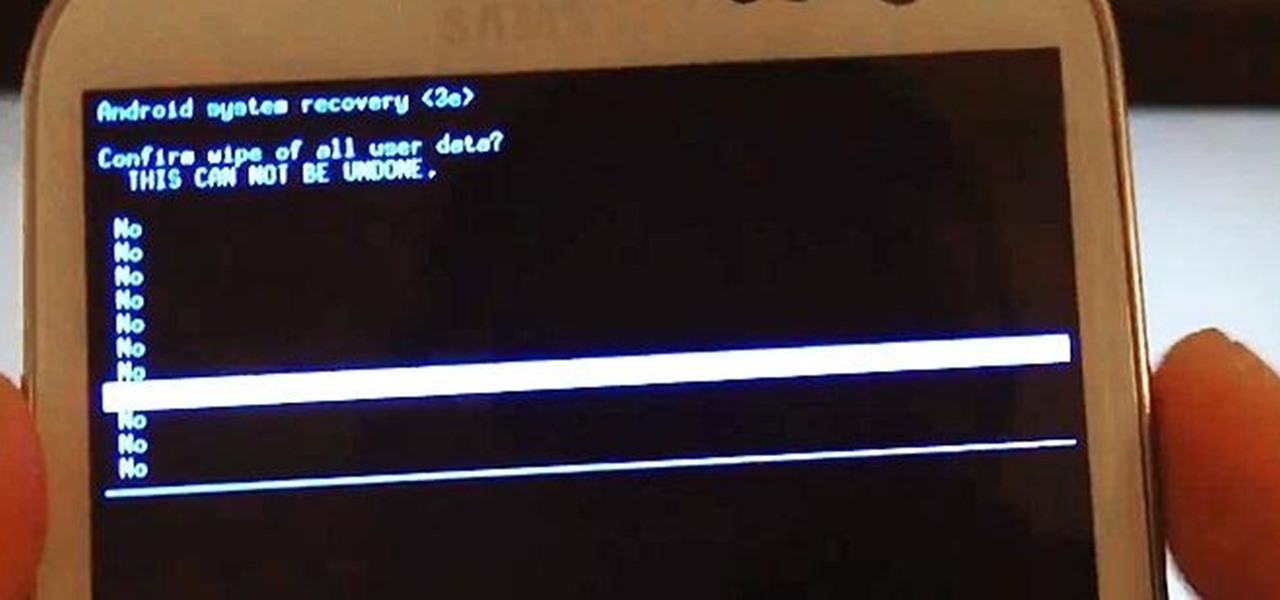
Erasing everything off of your phone and starting anew is a pretty drastic step to take for a little glitch. For most people, system restoring is a last resort option, but there are a few reasons to want or need to restore your device to factory settings.

Configuring user accounts is extremely important for those with a family shared computer or anyone using a work computer. Assigning different accounts with their own distinctive accessibility, customizations, and applications is the best way to manage a computer with multiple users.

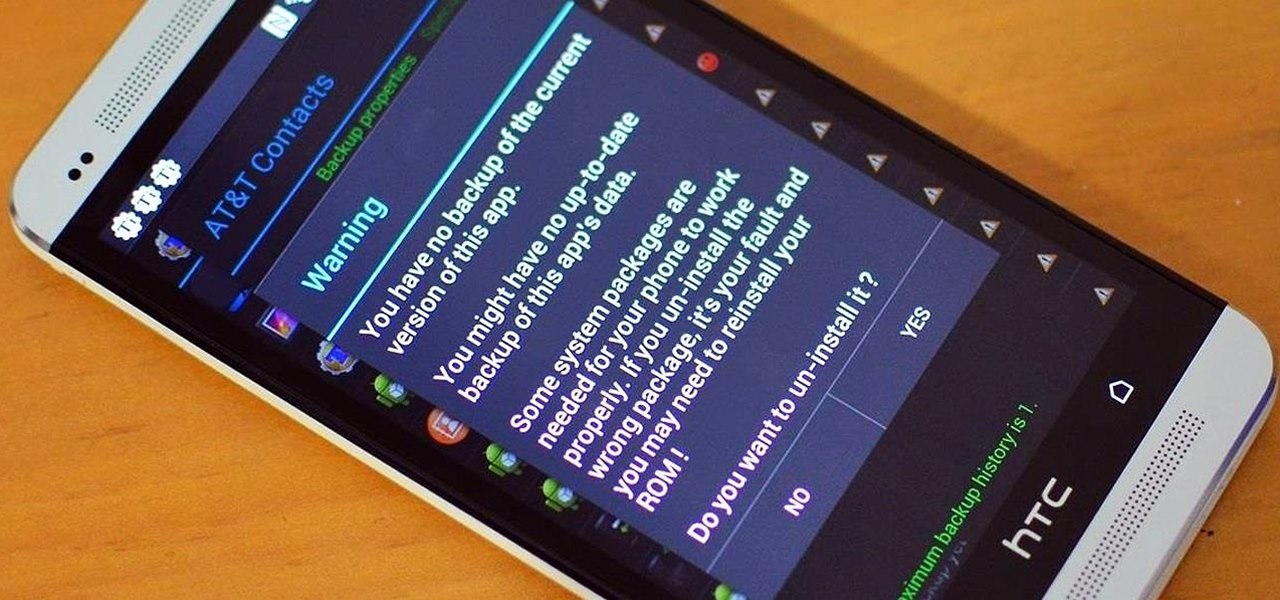
Rooting your device gives you all-powerful administrative access to your phone and its system settings. Of course, with such power comes great responsibility, and sometimes that responsibility becomes to burdensome or just plain unnecessary.

Still have an old tape deck installed in your car? This nifty hack lets you upgrade to the digital age without sacrificing your love for cassettes. There's nothing wrong with some low-fidelity tunes in your car every now and then, but if you want to listen to the tunes on your iPod or smartphone too, it's a lot easier (and cheaper) than buying a new in-dash player that supports line-in connections. Just add some wireless capabilities to you tape deck! All you need is a cheap cassette adapter,...

A hidden feature residing in Mac OS X Mountain Lion is the ability to view and also reply to your friend's tweets through the Contacts application, previously known as Address Book. The only way to do this, though, is to provide your Twitter account login data to the Contacts app. To integrate your Twitter, just go to System Preferences, then click on Mail, Contacts & Calendars and choose Twitter. Put in your Twitter login information and then click on Update Contacts. Twitter will use your e...

There are plenty of ways to take double exposure photos, even if all you have is your cell phone. If you have access to a darkroom (or Photoshop), you can do it by stacking negatives. But if you have the right kind of DSLR, you can do it right from your camera by using the multiple exposure setting.

Want to know when you have a visitor, even if you're not home? You could always set up a security system and live-stream it with your iPhone. But if you don't have a spare iPhone, or just don't want to go to the trouble, this simple hack will add text message alerts to your doorbell so that it lets you know when someone's there.

Windows users have been getting a lot of bad news about their security lately. First, we found out that passwords in Windows 7 and 8 can easily be exploited if password hints are enabled, and now, Russian password-cracking software developer Elcomsoft has found another huge vulnerability.

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Have a PC but hate Windows? Maybe you've just heard a ton about the new Mountain Lion OS X and want to see if it lives up to expectations. Either way, you can install Mountain Lion on your Intel-based PC in a few easy steps. All you need is a copy of the OS X and an 8 GB USB flash drive. The first step is getting Mountain Lion onto the flash drive. You'll need to format the drive with one partition as Mac OS Extended, Journaled and select Master Boot Record under options so that it's able to ...