
News: Ex-Magic Leap Employee Files Lawsuit Alleging Shady Hiring Practices
The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.


The legal travails of Magic Leap appear to have no end in sight, as a lawsuit filed by an ex-employee further threatens to dampen the startup's 2018 launch.
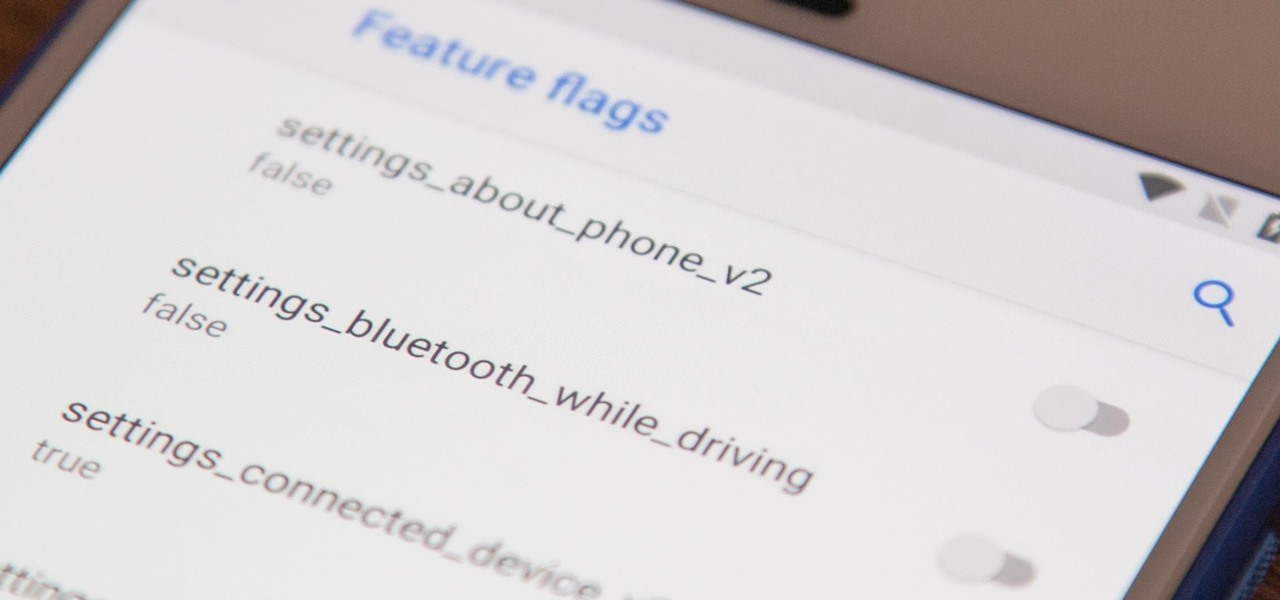
There's a new secret settings menu hiding in Android 9.0 Pie that offers Chrome-style "flags" to the overall operating system. Since it's currently the first Developer Preview and Public Beta versions, it's possible that this menu could disappear entirely when the stable version finally gets released, but it could also persist in its current hidden state where you have to unlock it.
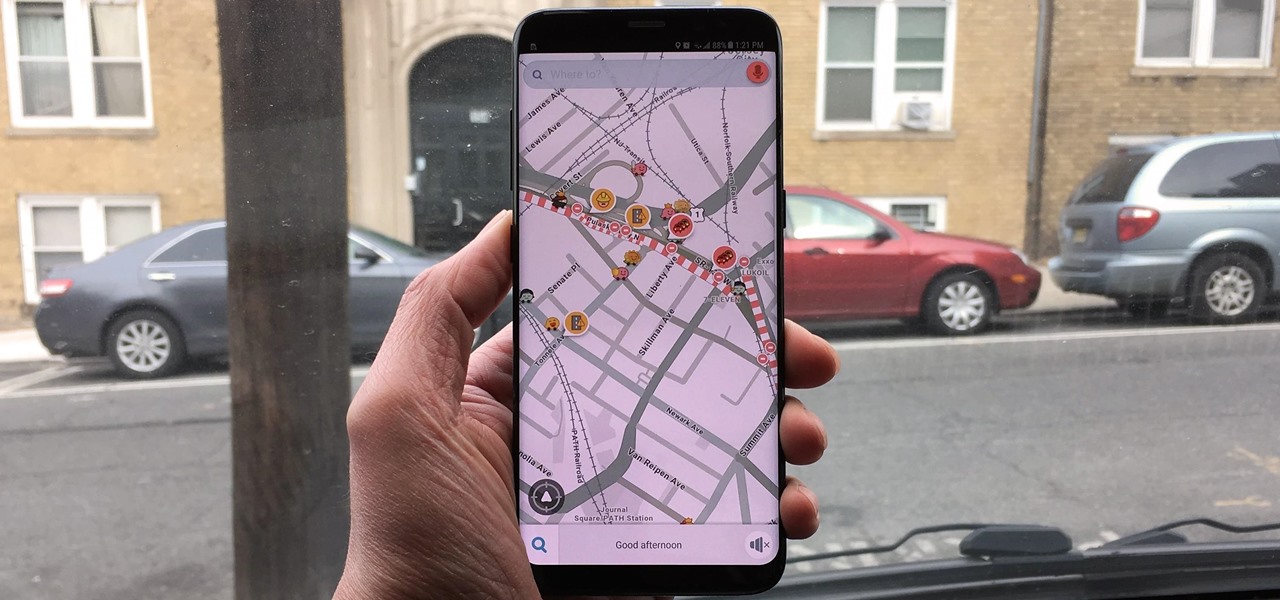
Because it sources a majority of its vital data from actual drivers on the road, Waze is easily one of the best navigation apps to use if you prioritize safety. Benefits such as crowd-sourced traffic data, police trap locations, and road work avoidance, when combined, help you anticipate traffic conditions with unprecedented accuracy and make adjustments accordingly.

It's tough to keep pace with Apple lately. As expected, only one day after the public release of iOS 11.2.5, the company released iOS 11.3 to developers. A day after that, Apple pushed it out to public beta testers, too. With new Animoji, more transparent battery information, Apple Music receiving music videos, and more, this update is the one to watch out for.
Google just rolled out a revolutionary feature to its Pixel devices — Google Lens. Previously, Lens had only been available in the Photos app, but now, whenever you want to learn about something in the real world, you can just bring up Google Assistant, turn on the camera, then let Google's famous AI analyze the scene.
It couldn't be any easier to remove apps from your iPhone — simply do a long-press on the app's icon, then tap on the delete button once it pops up. However, when it comes to removing unwanted tweaks and apps from a jailbroken iPhone, the process is often a little more involved.

The ride-sharing firm Lyft and Faraday Future, a troubled electric carmaker and potential Tesla competitor, have quietly appointed new top executives, but like the rest of the industry, they struggle to find talent for their driverless programs.

BMW seeks to hire 2,000 engineers for its driverless program ahead of the launch of its iNext Level 3 model in 2021, a source close to the company told Driverless.

We are totally buggin' about Pinterest's update to their Lens. I know, I had to.

Uber has lost market share to Lyft, its main competitor. Uber's US market share dropped from 84% to 77% between January and the end of May this year, and the ride-sharing company has continued to run into legal, public-image, and internal trouble. Lyft, on the other hand, has been growing.

Uber's legal team may have finally sold their engineering golden boy down the river as their war with Waymo continues. Anthony Levandowski isn't your average sacrificial lamb either — given the alleged stealing and all that — but Uber seems set on distancing themselves from this whole fiasco as fast as they can.

Engineer Anthony Levandowski has officially been kicked off Uber's driverless program by a judge as the company's legal war with Waymo continues.

Firefox Focus has been out for iOS for a while now, so it's about time Mozilla began porting the app over to Android. It's an amazingly private browser that protects you from trackers and ads when you're surfing the web. It blocks a wide range of online trackers, erases your browsing history, hides passwords, and deletes cookies. This essentially means ads won't be able to follow you around, in the sense that you won't see ads related to your last ten searches on Google.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.
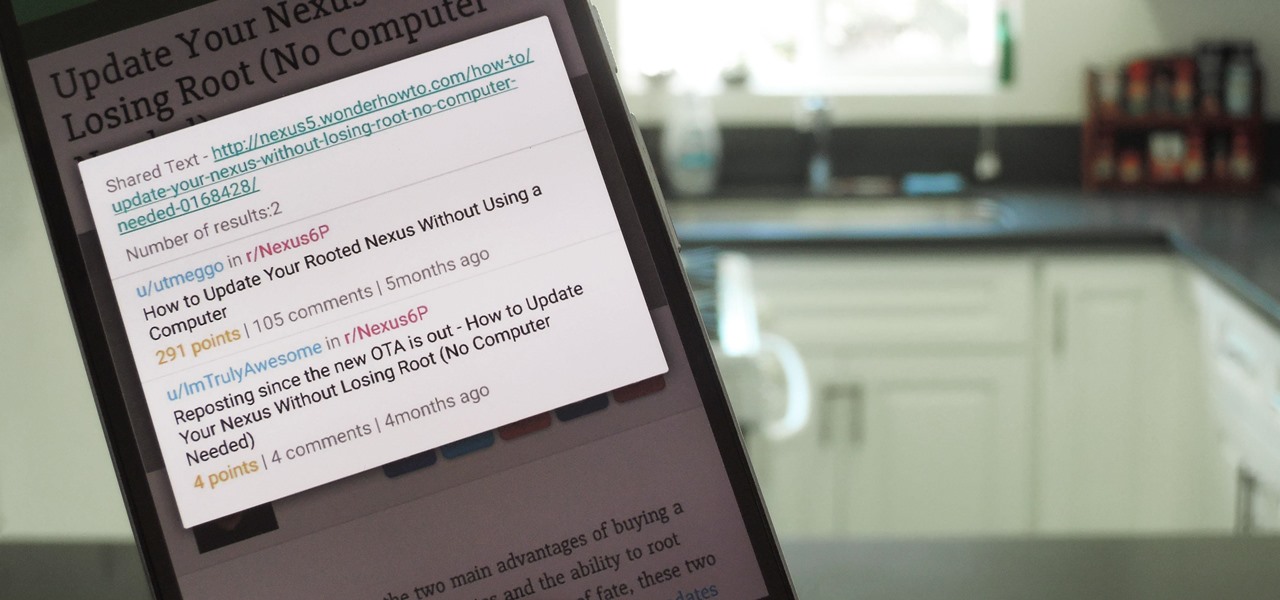
When you want to read product reviews, you go to Amazon—regardless of whether or not you intend on buying the product from their website. By the same sense, when you want to read discussions about certain topics you come across on the internet, there's no better place than Reddit.

The biggest corporation we know today is called Google, I bet you've heard of it yeah? How Google Tracks You:

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Starting with the release of Android Lollipop, the process of installing the Xposed Framework got a bit more complicated. Not only are there separate installers for each Android version, but now, you also need to know exactly what type of processor is in your device to make sure you're downloading the right files. In fact, CPU architecture is becoming a factor in more and more scenarios these days, including certain sideloaded app updates and, of course, custom ROMs.

Before we dive into the world of frustration, I first would like to thank whoever of the admins and mods made the folder for Raspberry Pi in the How-To's, thank you. Now with that outta the way, this article is about Metasploit on Raspberry Pi (hence the title). I should say that I ran into a error, but I think I figured what the problem is. First of all this is not on Kali Linux, but on a regular Linux OS. With that said let's open up a terminal and begin.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.
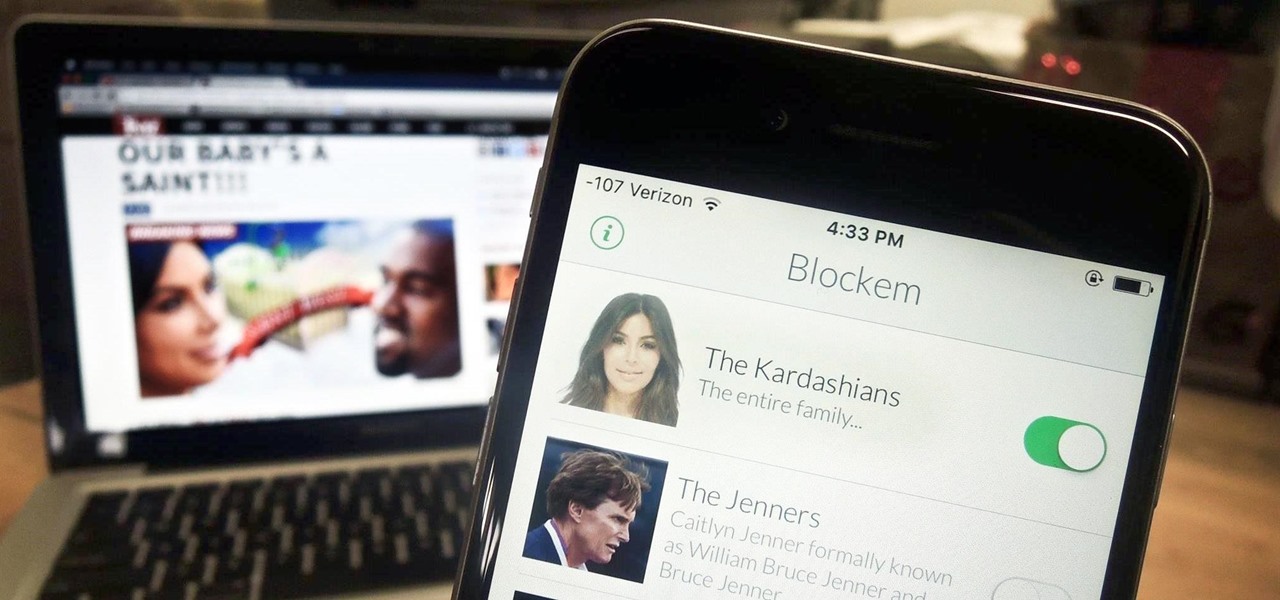
Kim Kardashian and Kanye West have fittingly named their second child "Saint," but I'm sure you don't care about that—and neither do I. Unfortunately, regardless of our pop culture interests, we're forced to know these types of stupid facts because the internet is so densely populated with Kardashian-related content that it's impossible to avoid. It's enough to make you puke.

This is My Review of the Electric Hair Brush Straightener LCD Iron Brush. I have had a Bad Experience please Watch this Video for more info!

As you all know, Anonymous have declared cyber war on ISIS and have already proven what they are capable of and whats to come.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

We are most certainly not machines. We all need some downtime every once in a while to set our sanity scales back in balance, which in turn, makes us more productive workers. This is a premise that several forward-thinking employers fully understand, but these types of companies are few and far between in corporate America.

It's no secret that exercise is good for you, but you may be surprised to know that a good workout can actually boost your memory, too. They key to giving your body and your brain muscles a good workout is by adding more weight and pushing hard for an extra 20 minutes.

As the developer behind the most popular root methods for hundreds of Android devices, Chainfire knows the ins and outs of Android root procedures. But this doesn't mean he's infallible—occasionally, some of his root utilities can cause minor bugs.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

Welcome back, my greenhorn hackers! Before we attempt to exploit any target, it is wise to do proper reconnaissance. Without doing reconnaissance, you will likely be wasting your time and energy as well as risking your freedom. In previous guides, I have demonstrated multiple ways to perform reconnaissance including passive recon with Netcraft, active recon with Nmap or hping3, recon by exploiting DNS or SNMP, and many others.

When Android 5.0 rolls out to the Nexus 5, several changes and new features will come along with it. The over-the-air update is already rolling out, and if you don't want to wait, you can get it right now.

Last year, Todd Blatt ran a Kickstarter campaign to make 3D-printed accessories for Google Glass, and has turned it into a company: GlassKap.
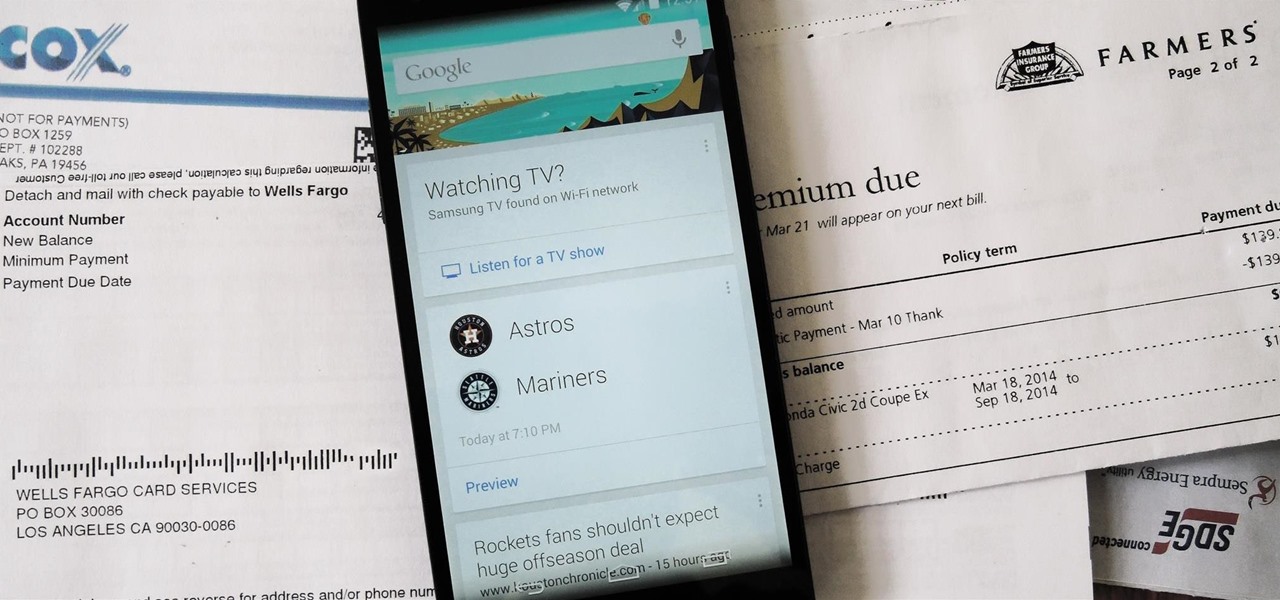
Google is widely renowned for its mastery in using data to tailor specific search results and ads. Their Android and iOS search apps put this ability to use in finding the most relevant pages for your query, and their desktop site is the most-used search engine on the web as a result of it.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Samsung released a teaser video today, touting its next flagship Galaxy device, presumably the Galaxy S5. With an official announcement expected on Monday at Mobile World Congress, this video should serve as a final teaser before the big day.

Sometimes, you just don't want to hit the Power button to turn your screen off. In the current age of touchscreens, you've got to wonder why we even have physical keys anymore.
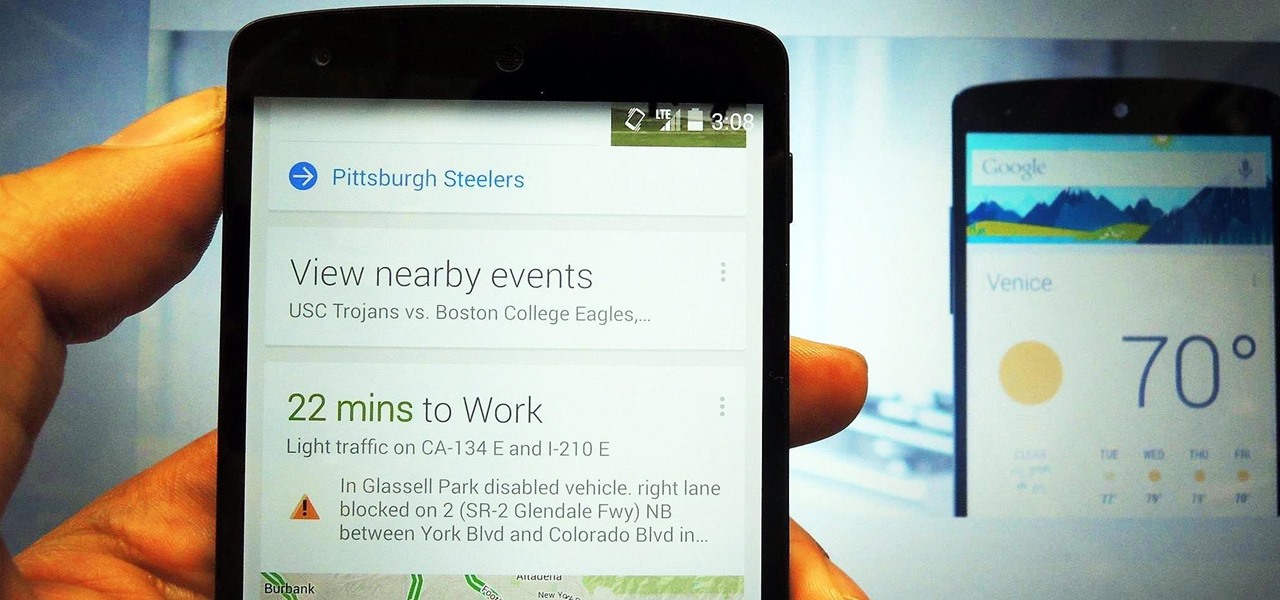
The launch of Android 4.1 Jelly Bean was also the launch of Google Now, a service that was supposed to one-up Siri, the resident personal assistant for iOS devices. Google Now offered enticing features, but its launch went unnoticed by a great many Android users.
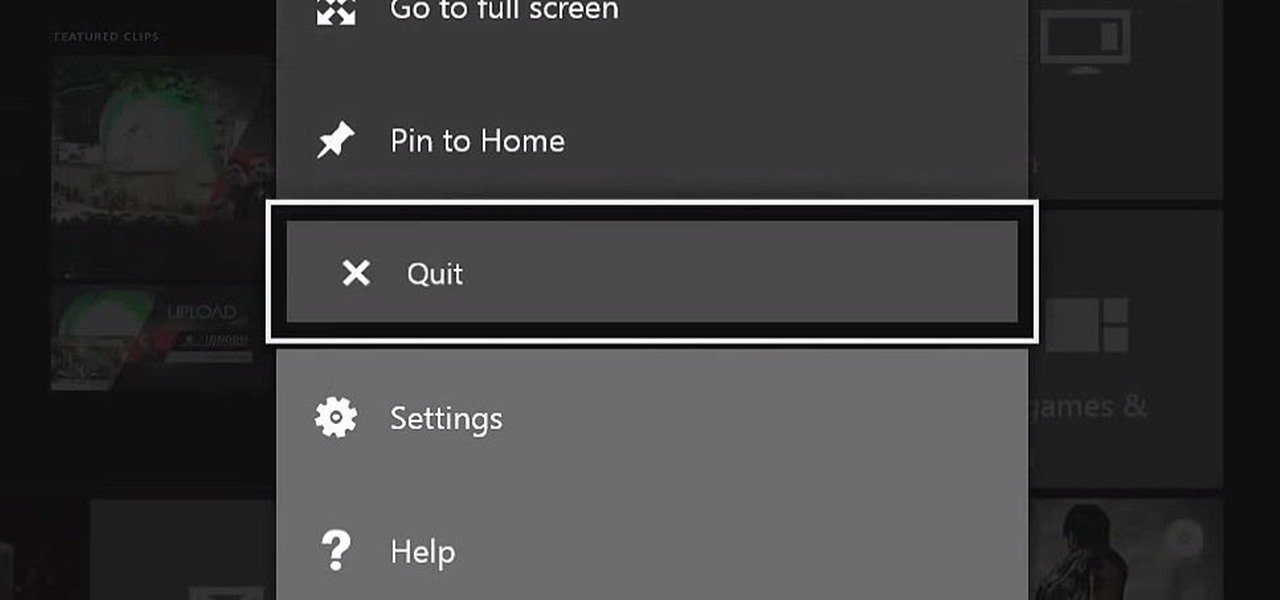
The Xbox One is pinning its success on the fact that is much more than just a video game console. Microsoft is looking for the Xbox One to become the centerpiece for family entertainment, which is why they included features like multitasking, TV controls, and apps.
Thousands of history files, cookies, other unwanted files stored in your system as logs and other formats. To manually check each one is difficult. New computers are too fast by processor behavior, after some times of working it comes to slow performance.

This step-by-step tutorial will show you how to install Mac OS on Windows 7 on Virtual Box. Video: .
