Backdoors are convenient to leave behind once you've already found a way into a server, and they can come in handy for a variety of reasons. They're good for developers who want a quick way into machines they're working on, or for systems administrators who want similar access. Of course, backdoors are also a hacker's best friend, and can be added in a variety of ways. One good tool for doing this is Weevely, which uses a snippet of PHP code.

You're only as smart as your communication skills allow you to be, as other people will simply never know your inner genius if you can't effectively express yourself. Regardless of the medium—be it a Facebook post or even a simple text message—this fact remains true.
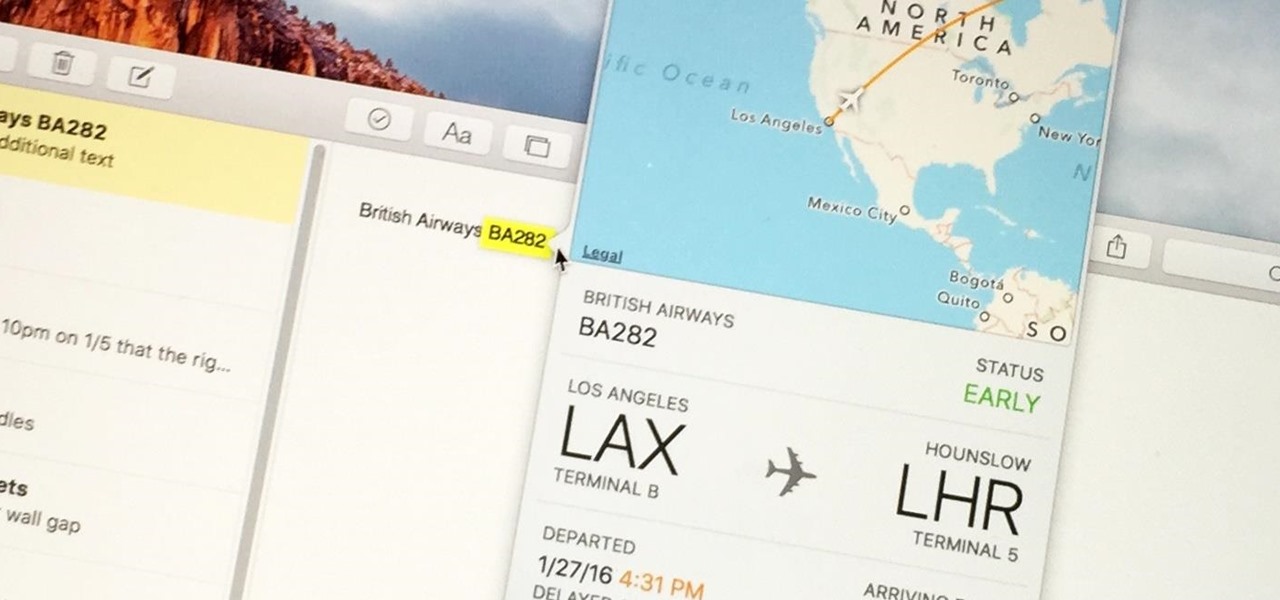
Turns out, you no longer need third-party flight tracking apps to get information on yours or others' flights—your iPhone and Mac can now give you flight details right from your Mail, Notes, and Messages apps.

Welcome back, my tenderfoot hackers! Recently, Microsoft released a new patch (September 8, 2015) to close another vulnerability in their Windows Vista, 7, 8, and 8.1 operating systems. The vulnerability in question (MS15-100) enabled an attacker to gain remote access to any of these systems using a well-crafted Media Center link (MCL) file.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

Whether it's the start, middle, or end of summer, it's prime-time grilling season. If you find yourself without a grill, however, it may seem as if half your summer plans of swimming by the pool while stuffing hot dogs in your face could be ruined.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Apple definitely wasn't first to the widget game, but any iPhone running iOS 8 or higher can add widgets to their Today View found via a swipe down from the top of the screen when on the home screen or in any app. There's even access to widgets on the lock screen via the same swipe down on iOS 8 and iOS 9 (on iOS 10, iOS 11, and iOS 12, all you have to do is swipe right on the lock screen).

Welcome back, my tenderfoot hackers! Not too long ago, I showed how to find various online devices using Shodan. As you remember, Shodan is a different type of search engine. Instead of indexing the content of websites, it pulls the banner of web servers on all types of online devices and then indexes the content of those banners.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

Chopsticks are very easily reusable, yet they always get thrown away. You use them when you get Chinese takeout, then toss them out without even a backwards glance.

Everyone in the world uses tablets these days, so it's no wonder that the Samsung Galaxy Tab has different languages built right in. To change your language on the Android tablet, all you need to do is navigate to the Settings menu.

In this video, we learn how to make iPhone ringtones for free with iTunes. First, open up iTunes and open up the song you want to make a ringtone out of. After this, right click and click "create an aac version". It will start to convert, then once that's done right click on the new song and click "get info". Now you can adjust the start and end time of the song, depending on what you want your tone to be. When finished, click "ok", then create an aac version of this new song. Delete the firs...

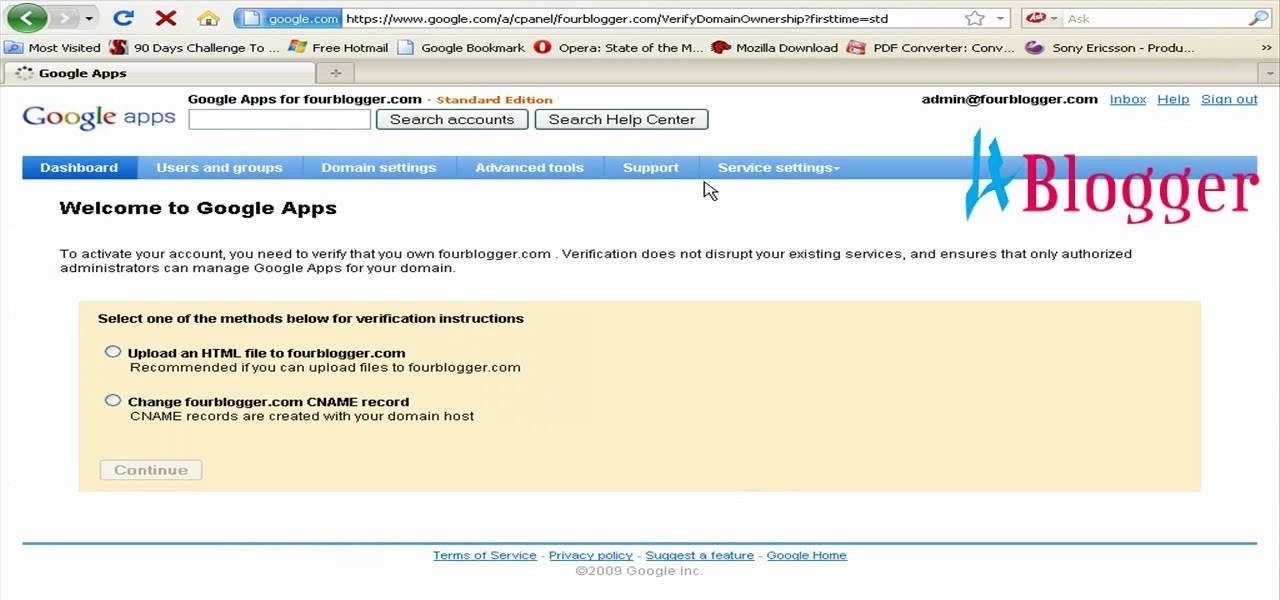
You can create the Google apps email like Gmail for your domain. So to do this first you need to go to the google.com/a and click on the standard in "other Google apps editions". Now click on "get started". Now select "administrator: I own..." and enter your domain name and click get started. Now on next page create your account by filling all the fields and click continue and now fill the info of your administrator account and click I accept button. Now next step is for the verification of y...

This video tutorial from xTheEnforcerx1 shows how to import custom SMS tones to your iPhone 3G using SSH.

If you want to run multiple windows operating systems at the same time you first need a Windows computer, the installation disk for the operating system you want to run, and Windows Virtual PC 2007. To install this, first type in Virtual PC 2007 to Google, go to the Microsoft link and download and install the program. Now, open the Virtual PC and click next on the wizard. Name your hard disk and click next until you choose where you want this at. Now your virtual hard drive is created. Now, p...

TubeTutorials teaches viewers how to legally put free ring tones on their iPhone 3GS! First, go to start menu and click on computer. Click on organize, layout and make sure menu bar is checked. Click on tools and go to folder option go on view and uncheck 'hide extensions for known file types' and click 'apply'. Now open iTunes and pick a song you want. First, right click the song click get info. Go to options and click start time and stop time. Copy the stop time and change the stop time and...

Craig Madox from TubeTutorials shows how to create and put ringtones on your iPhone 3G. If you already own the song, you shouldn't have to pay for it again as a ringtone!

This video is about how to download torrent files. The first thing that you will have to do is to open your uTorrent. After opening your uTorrent, open your browser and browse torrent sites that suit you best. Once you have found the site that you like, search for torrent files that you are interested in. Once the results have been displayed, refer to the number of seeds since this increases the download speed. Once you have found the largest number of seeds, click on the title of the file. A...

gjtfreak demonstrates a new free tip for the iPhone 3G on how to get free ringtones on a Windows Vista environment in this video. Firstly go into the start menu open control panel option and from that open folder option. Click on view and find a box that says hide extensions for known file types and unclick that box click apply and then OK. Secondly open up iTunes and pick the song you want to use and go into the preferences column at the top left of the iTunes window. Make sure that the ring...

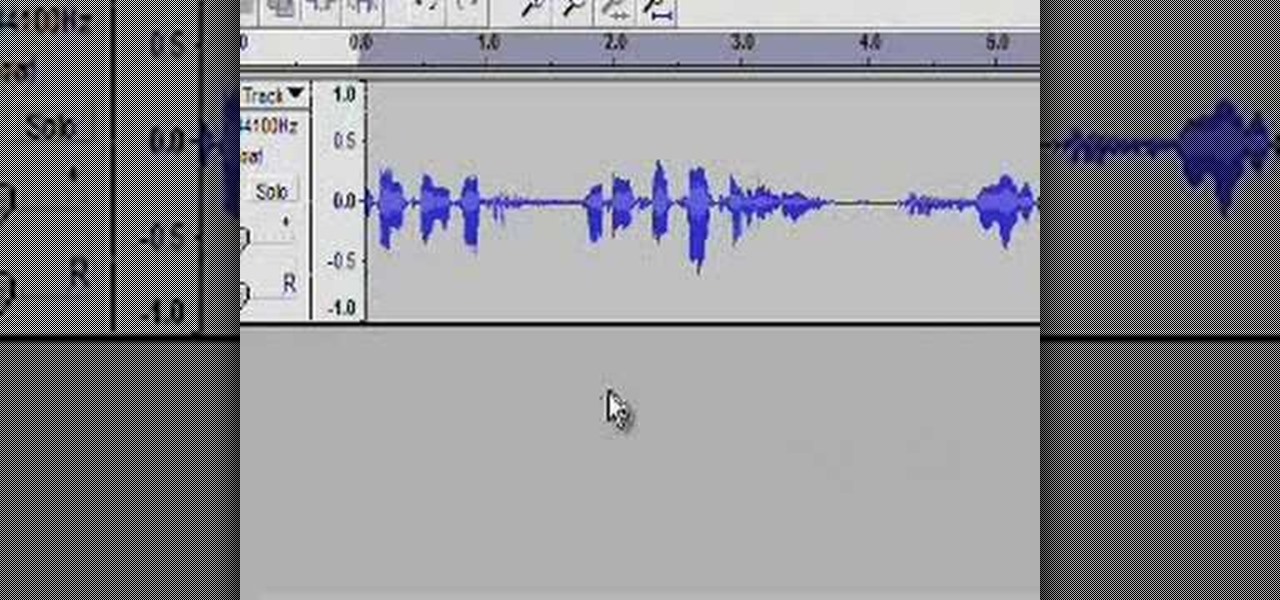
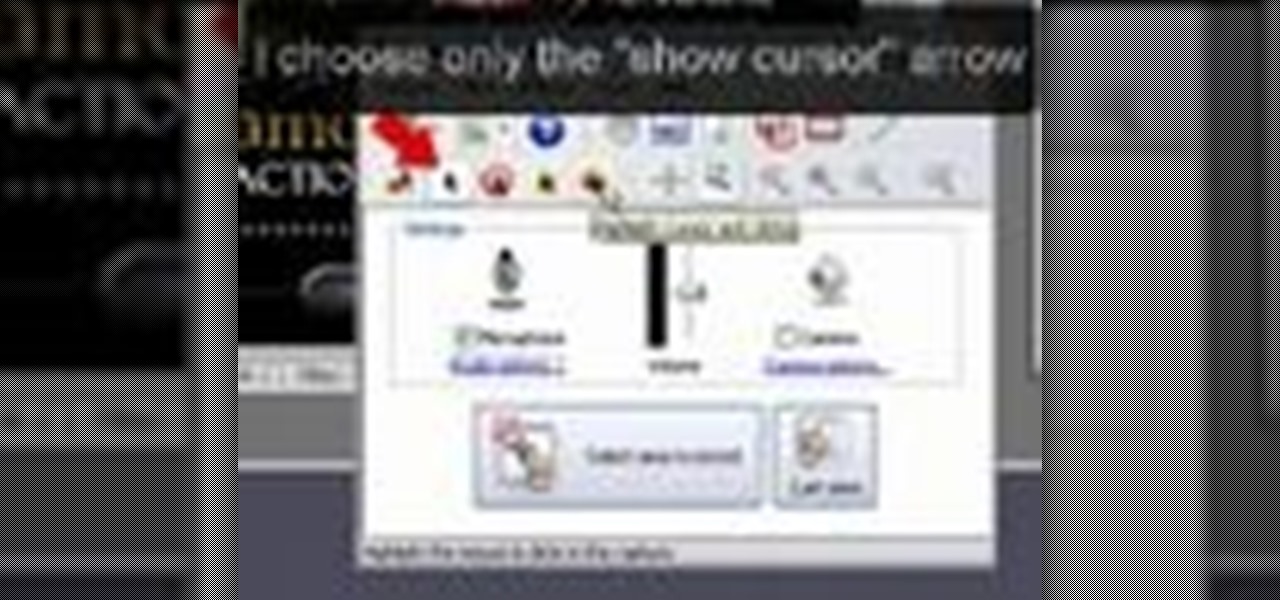
RabbidHedgeHog shows viewers how to easily make a podcast. This features how to make the podcast with the program Audacity. First open your internet browser and go to Audacity. Scroll down to download Audacity 1. 2. 6, save the file, Install and download the program. Now, open up Audacity which is basically a recorder. Connect your microphone which will allow you to record. Click edit, preference, find microphone and select the device you will use. Now, record your podcast by clicking the red...

In this video, learn how to install Install0us 2.5 on your iPhone. This can only be installed on a jailbroken iPhone. Directions, tips, tricks, and tourbleshooting advice from videomaker, grandhustler are listed below.

CC, which stands for "carbon copy", is a familiar phrase in email, but can also be used in business letters and legal documents. This can be especially useful for letters you want to spend up a company or organizational chain, letting each recipient know exactly who else received the same document.

Having problems with your anti-virus software on Windows? Learn how to remove the fake virus protector Personal Antivirus! Personal Anti-Virus is NOT a legitimate anit-virus software and will use spyware to steal info from your computer. Personal Anti-Virus is hard to get rid of and is totally annoying. To get rid of it, you don't have to download anything.

Want to control a friend's cell phone remotely and make "free" calls from it? In this hack how-to video, you'll learn how to hack Bluetooth-enabled cell phones with your Sony Ericsson or Nokia phone and the Super Bluetooth Hack—or "BT Info"—, a free program easily found through Google. Once installed, Super Bluetooth Hack will enable you to control your friends' cell phones remotely.

Photoshop Mama is here to make all your software tutorials you want to post on YouTube so much better! She shares info on the products and where to get them and also covers how shes produce vids and specifically her post production procedure for saving vids for upload to YouTube.

This Photoshop video series is going to explain how to create a chiaroscuro lighting effect on an image. This art form was made famous by the Italian artist Rembrandt. Part one covers the origin of terms and how to create chiaroscuro dramatic lighting. Part two has instructions for downloading the image, and some very basic workspace and preferences instructions for beginners. Part three covers Duplicate Image, File Info, File Size, Eyedropper Sample, Doc Status Bar, Panels/Palettes. Part fou...

She thinks just because you're related that your closet is her closet; and if she ever gives your things back, they're never washed. If it's time to stop your sister from being a closet bandit, check out this video. This tutorial is full of tips for gettinf rid of that pesky sibling and keeping your clothes all to yourself.

Striking up a conversation with a group of people you don't know can be an intimidating task. Come prepared with some interesting comments and ideas and you will be able to make new friends out of any crowd.

It's easy to find yourself drowning in a pile of papers and nick-nacks if you're not armed with a good organization system. By taking the time to set up a system where everything is condensed and has a place you'll find it much easier to keep it that way.

Everyone benefits from positive coping strategies when dealing with divorce – learn how. Step 1: Stay in touch with both parents

With each update, Chromebooks are slowly becoming the Android tablet we always wanted. They already run your favorite Android apps and recently added a multitasking feature introduced to Android smartphones a few years ago: picture-in-picture mode.

Apple released iOS 13.5 for iPhone on Wednesday, May 20. The update came just two days after the company seeded beta testers iOS 13.5's GM (golden master), the build everyone would get if all went well. While only available to beta testers, the GM is the same software as iOS 13.5's stable release.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.